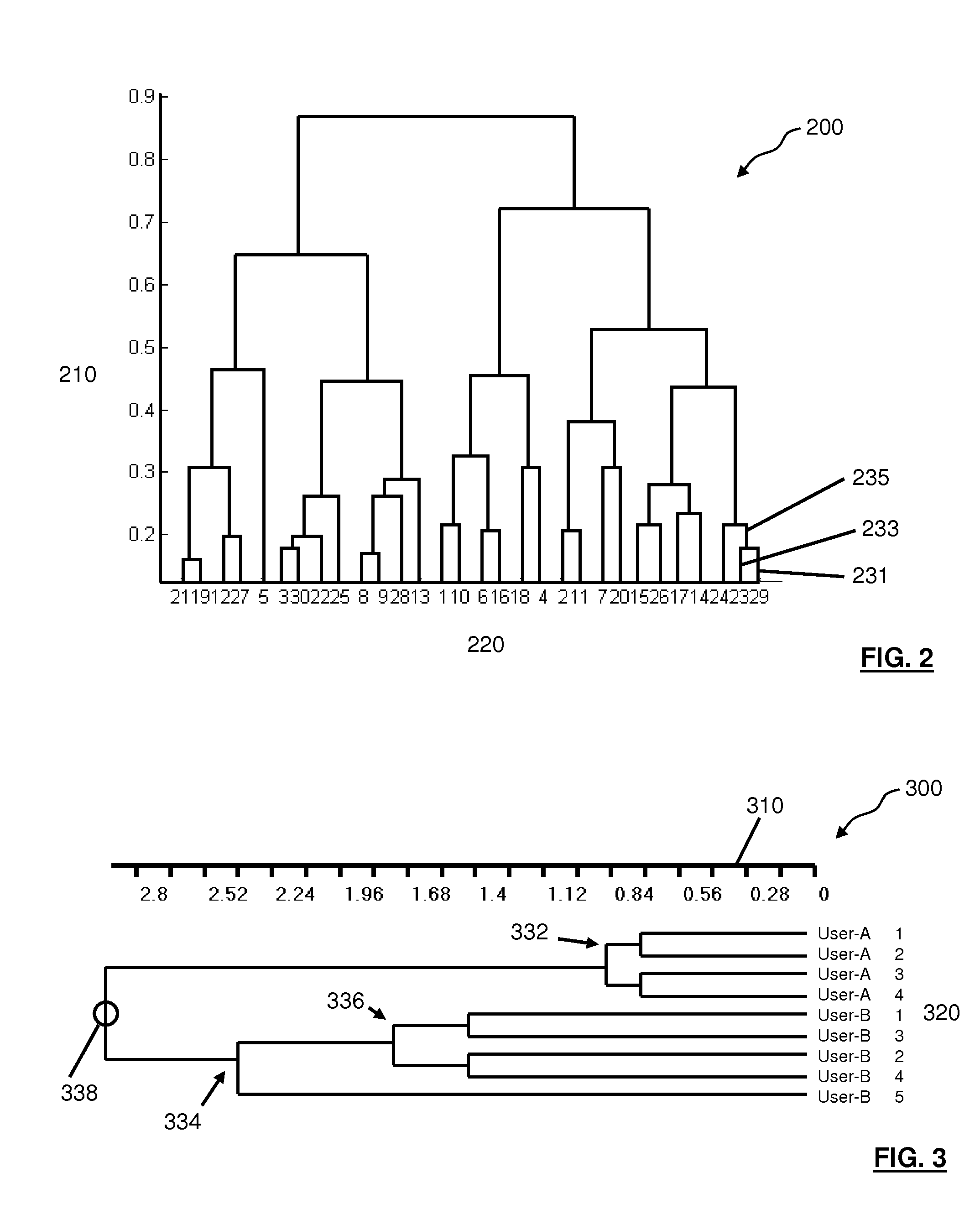
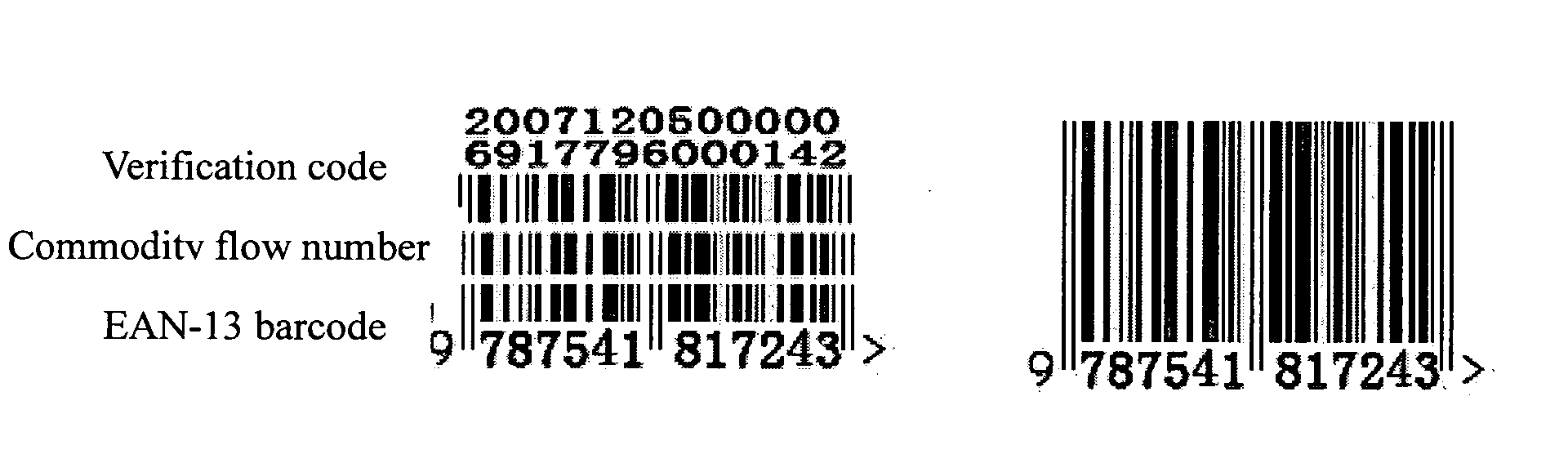Patents
Literature
280 results about "Machine identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Machine identity is the application of familiar privileged access management (PAM) concepts including identity, authentication, RBAC, least-privilege, auditing, etc. to non-human network entities (processes, services, containers and hosts).
Smart card for recording identification, and operational, service and maintenance transactions
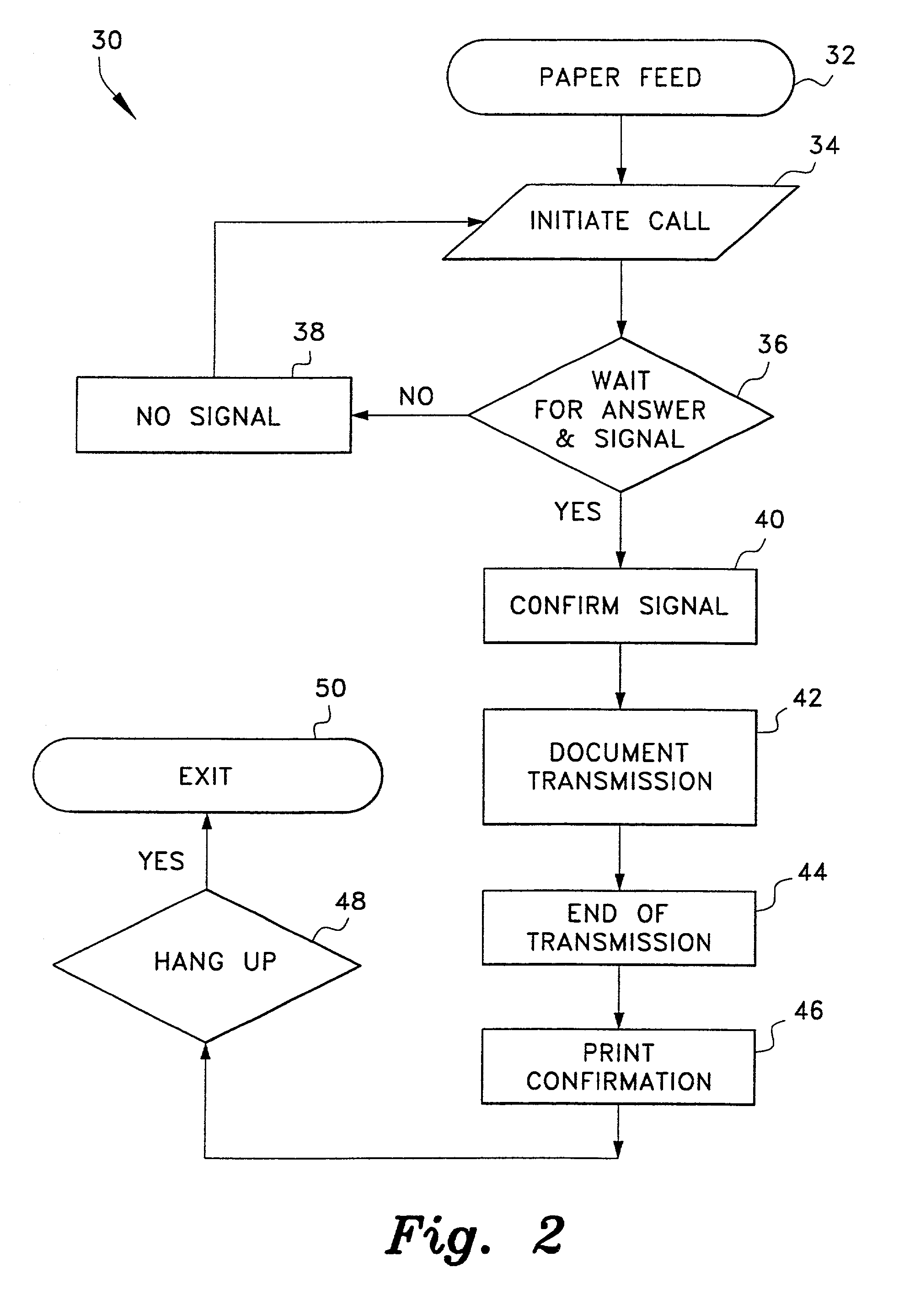
InactiveUS6557752B1Registering/indicating working of vehiclesRegistering/indicating working of machinesTelecommunications linkCommunication link
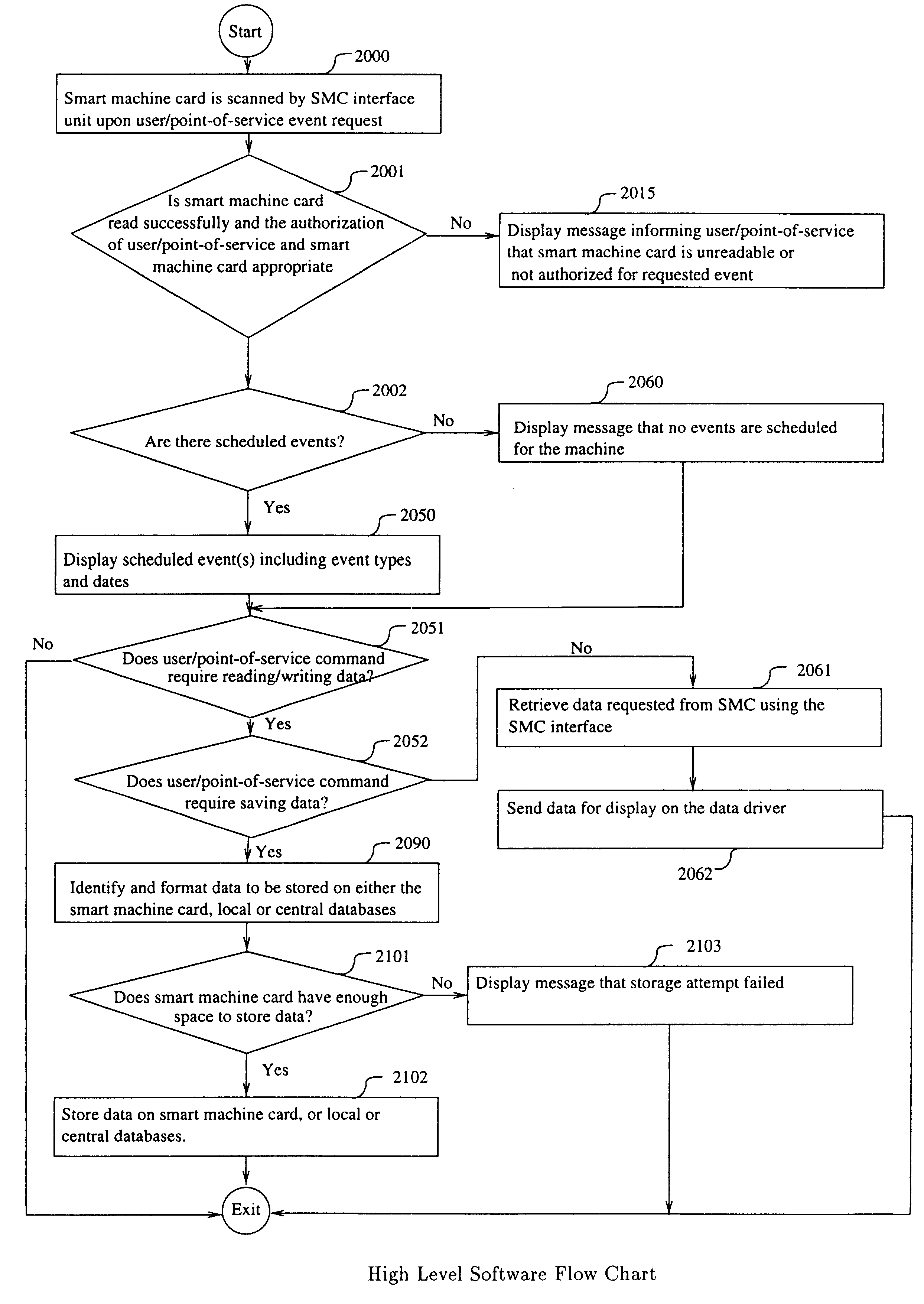
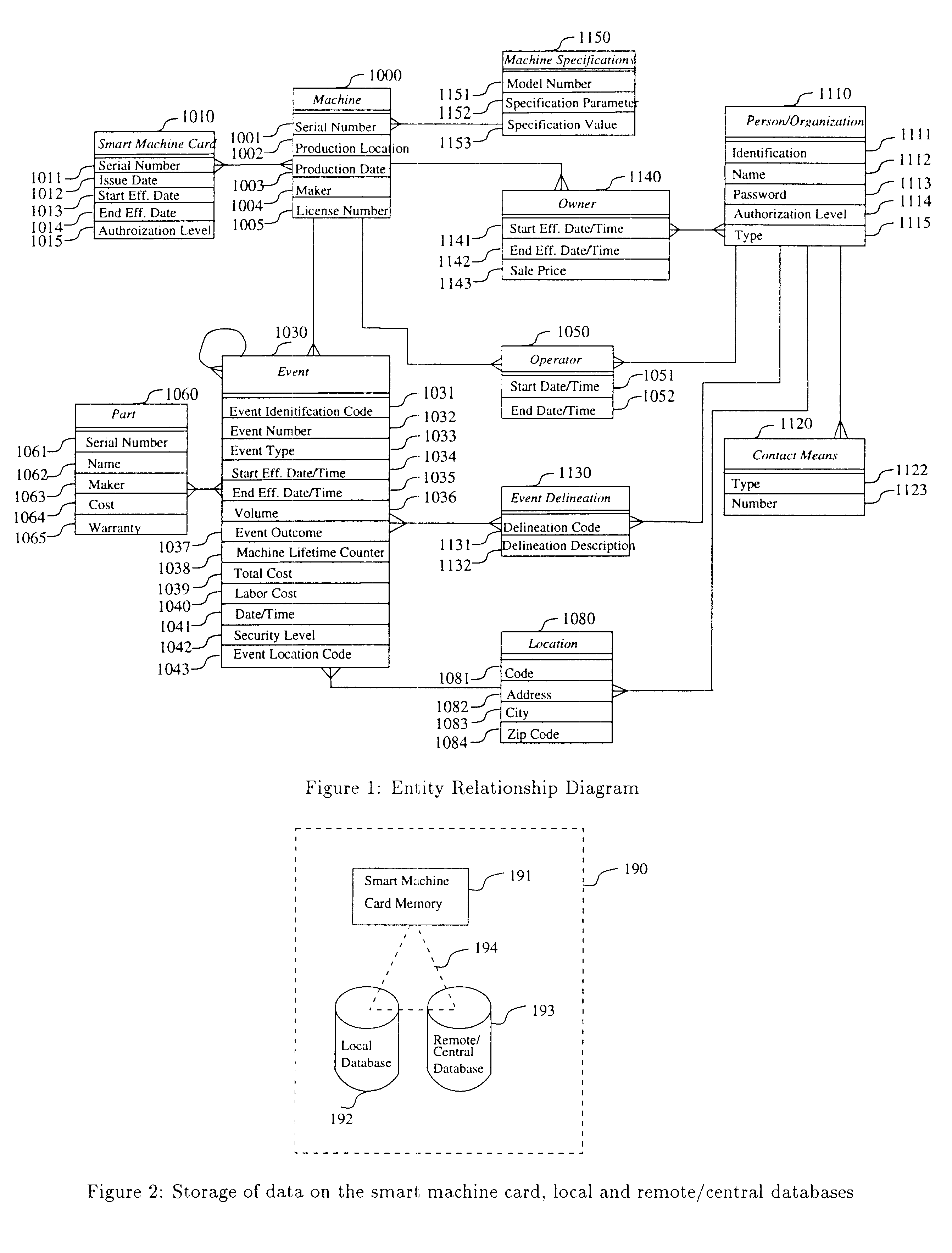
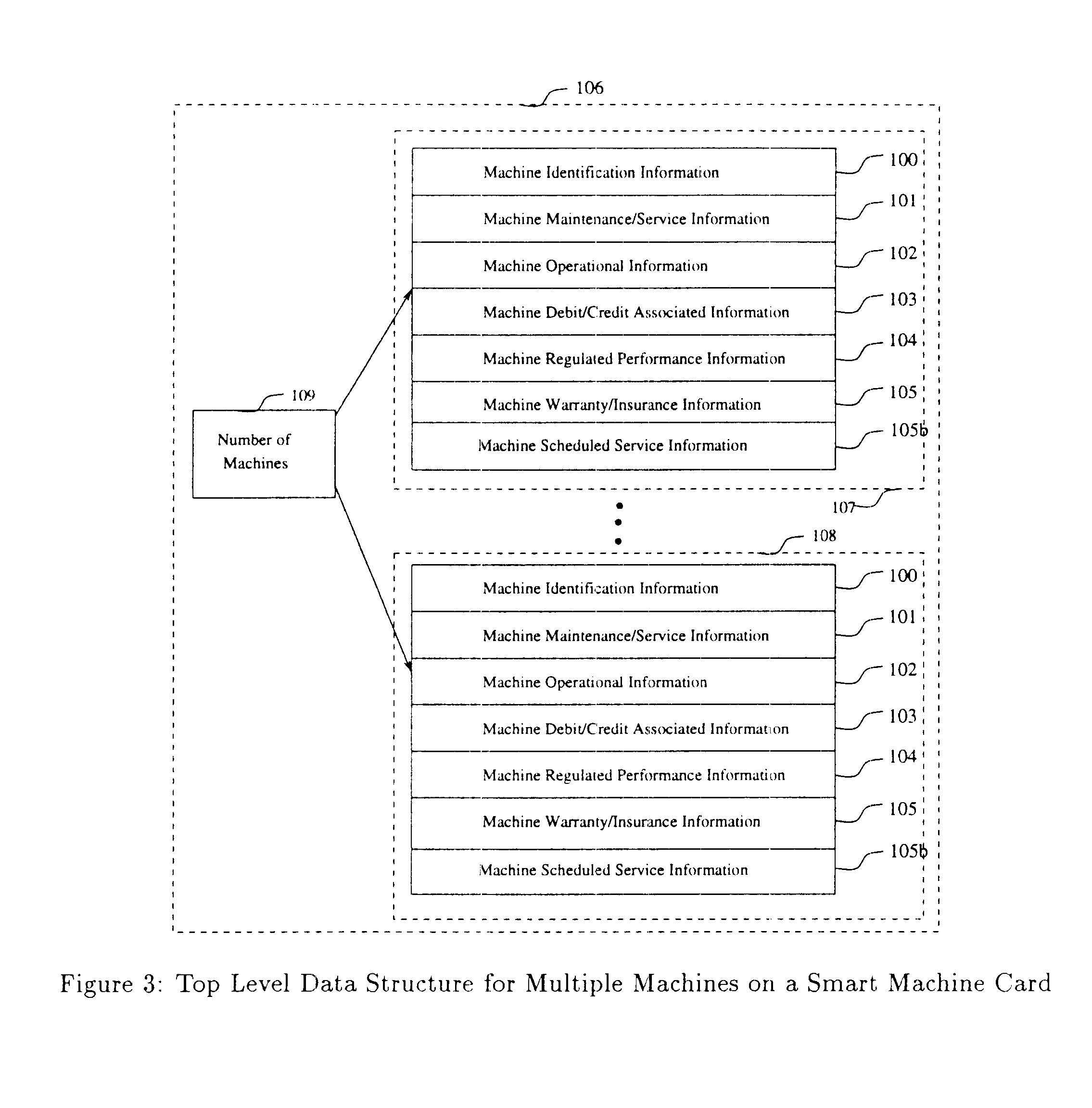
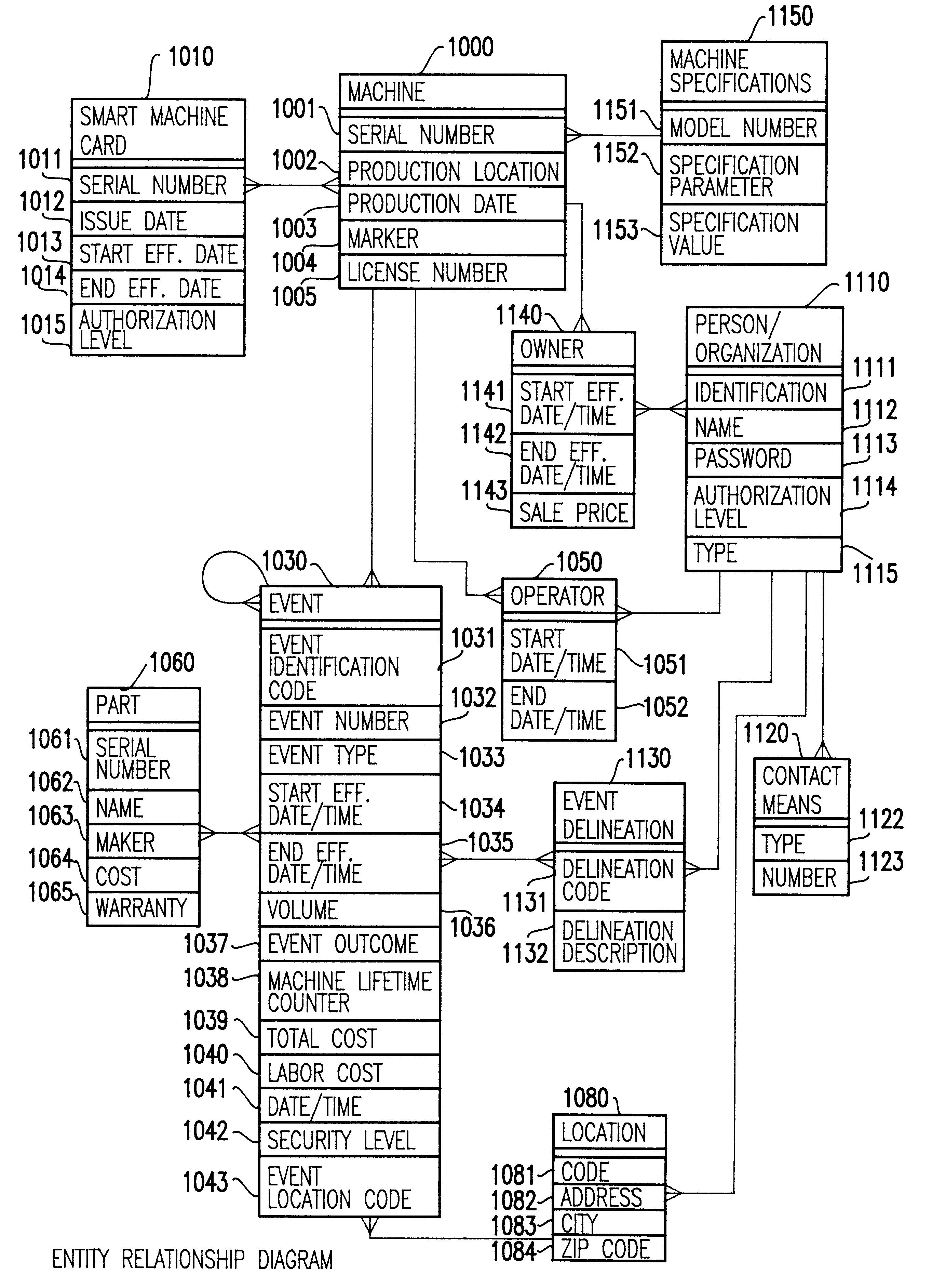
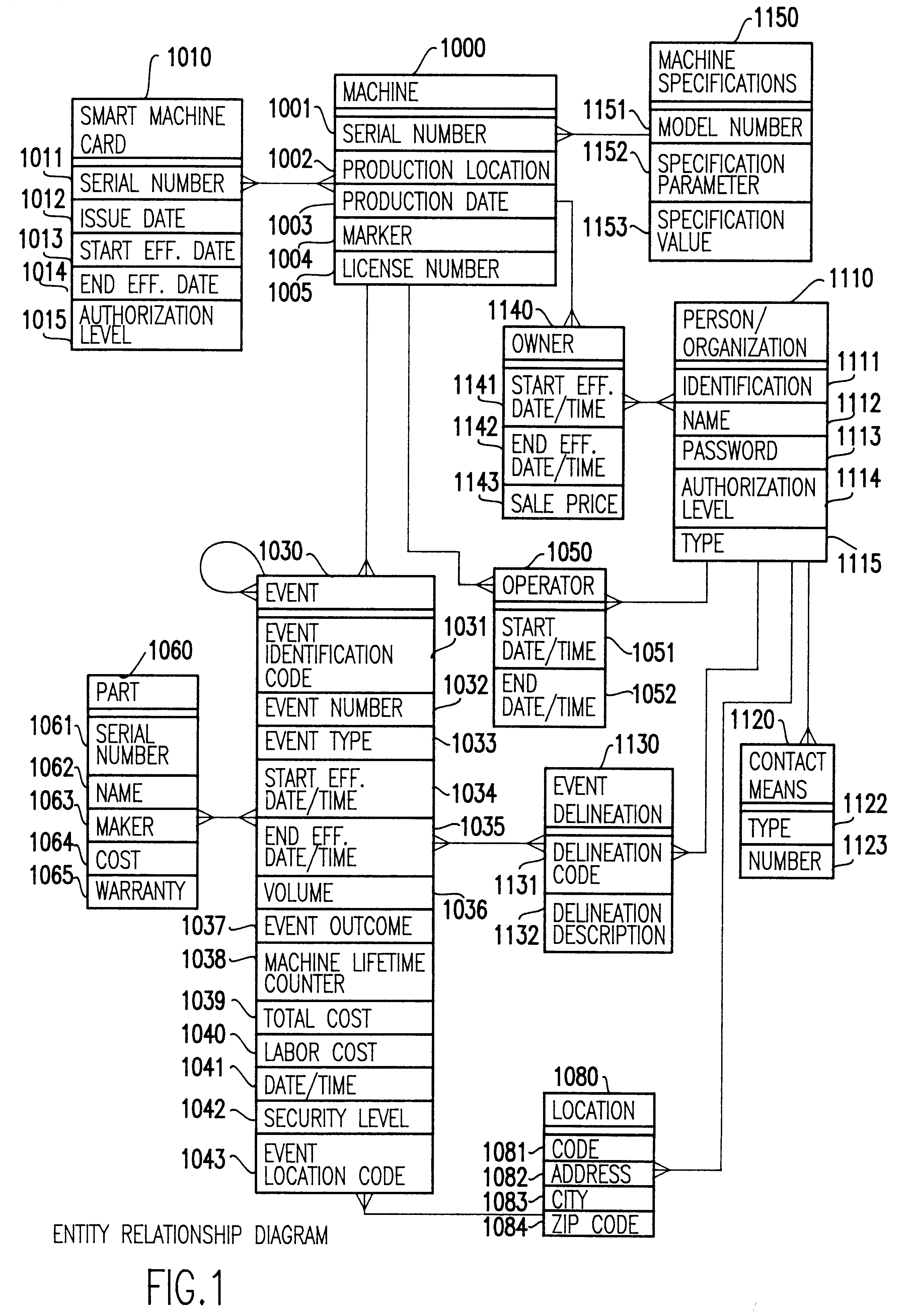
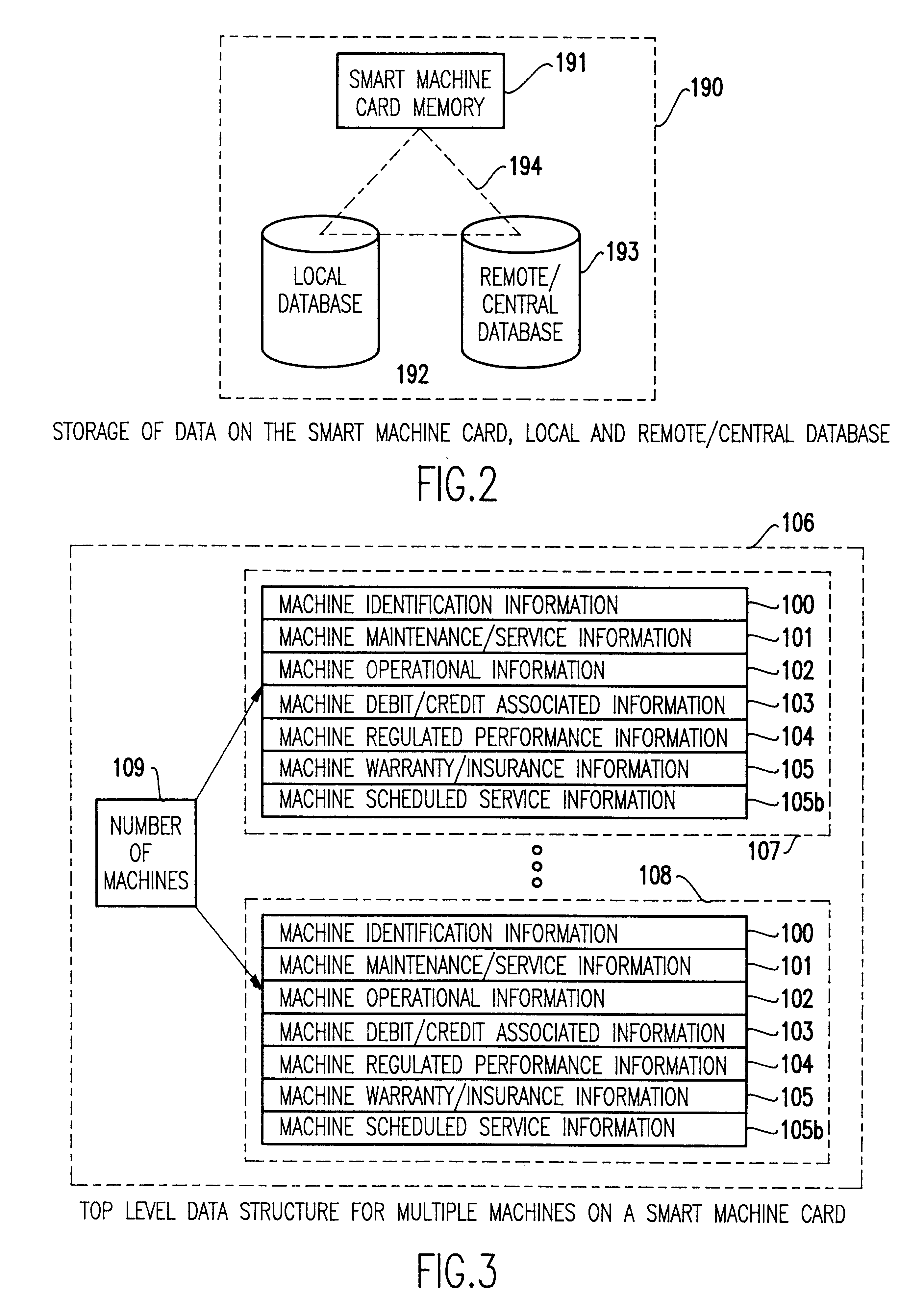
A computerized "smart card" which has a read / write memory and formatted data storage blocks is used to track the life history of one or more associated machine(s) (e.g., vehicles, medical instrumentation and apparatus, business and copying machines, etc.). The smart card can store a variety of information including machine identification, hardware / software specifications, debit / credit, regulated performance, warranty / insurance, maintenance / service and operational transactions that might impact the hardware, software or the intended operation or performance of the machine. The smart card will be equipped to interact with any of a plurality of autonomous reader / writer smart card units and computer-based reader / writer smart card units that may be equipped to interact with any of the plurality of computer databases through the utilization of land or wireless communications links. Preferably, each smart card will be associated with one or more specific machines at the time of sale of the machines, and will be periodically updated at each transaction (e.g., repair, scheduled maintenance, transfer of title, etc.) using reader / writer units operated by service technicians, repair shops, insurance agents, or the like. Thus, upon transfer of title of the machine, the smart card will also be transferred to provide the new owner with a complete life history for the machine. The stored life history can be used for valuation, maintenance scheduling, problem trouble shooting, and other applications. In the case of a single card being associated with a group of machines (e.g., a company with a fleet of cars, trucks or buses, or a company with several photocopiers, etc.), the card can also be used to track the scheduled replacement of individual machines within the group. Provisions are also made to associate new cards with existing machines to track the future life history of a particular machine.
Owner:Q INT
Method for using a smart card for recording operations, service and maintenance transactions and determining compliance of regulatory and other scheduled events
InactiveUS6170742B1Specific performanceRegistering/indicating working of vehiclesRegistering/indicating working of machinesTelecommunications linkSmart card
A computerized "smart card" which has a read / write memory and formatted data storage blocks is used to track the life history of one or more associated machine(s) (e.g., vehicles, medical instrumentation and apparatus, business and copying machines, etc.). The smart card can store a variety of information including machine identification, hardware / software specifications, debit / credit, regulated performance, warranty / insurance, maintenance / service and operational transactions that might impact the hardware, software or the intended operation or performance of the machine. The smart card will be equipped to interact with any of a plurality of autonomous reader / writer smart card units and computer-based reader / writer smart card units that may be equipped to interact with any of the plurality of computer databases through the utilization of land or wireless communications links. Preferably, each smart card will be associated with one or more specific machines at the time of sale of the machines, and will be periodically updated at each transaction (e.g., repair, scheduled maintenance, transfer of title, etc.) using reader / writer units operated by service technicians, repair shops, insurance agents, or the like. The stored life history can be used for valuation, maintenance scheduling, problem trouble shooting, and other applications.
Owner:Q INT
Account sharing detection
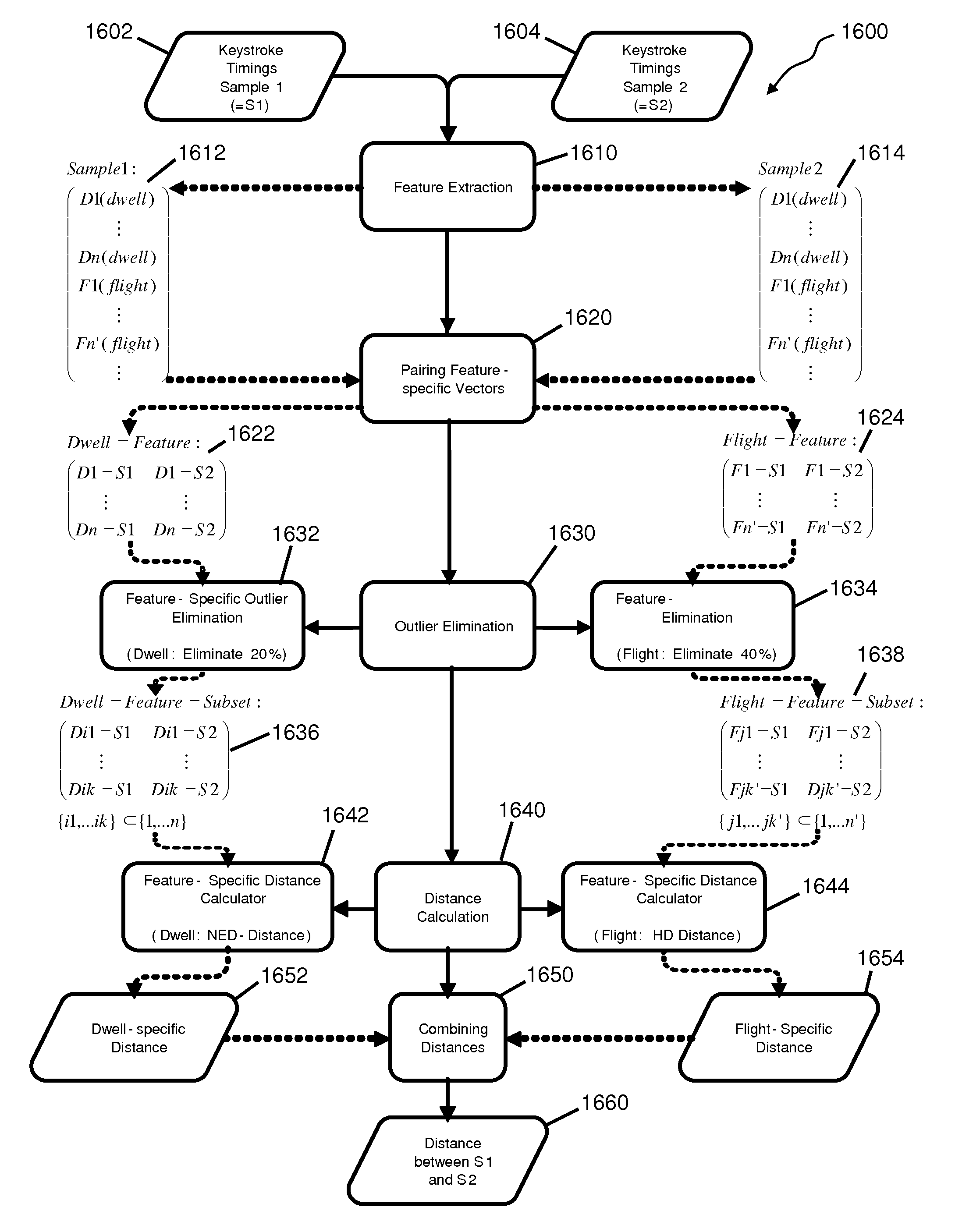
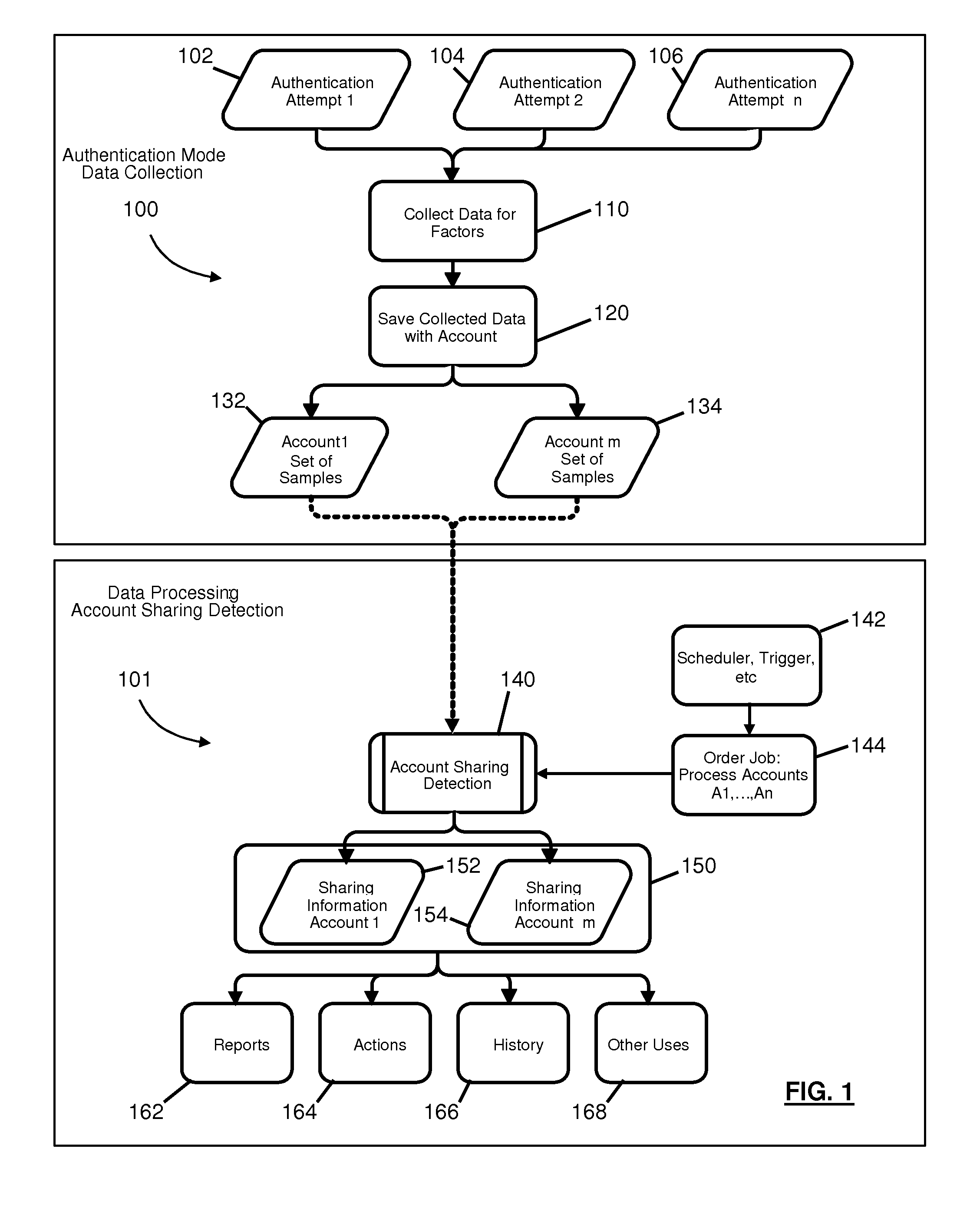
Apparatus and methods are described for detecting sharing of electronic or online accounts based on grouping of data samples that include keyboard input timing factors and optionally secondary factors. The data samples can be received from various computers having various keyboards of a certain type and may be input by more than one user. The data samples are grouped based on distances and ratios of mathematical combinations of distances between input timing of key events such as dwell and flight time, as well as optionally based on at least one secondary factor related to the keyboard input timing factors. Example secondary factors include a time of day of the input; and / or a machine identification, location, and IP address of the computer used to input the sample.
Owner:CONCENTRIX SREV INC
Post-processing system and method for correcting machine recognized text
InactiveUS7092567B2Special data processing applicationsCharacter recognitionAmbiguityOptical character recognition
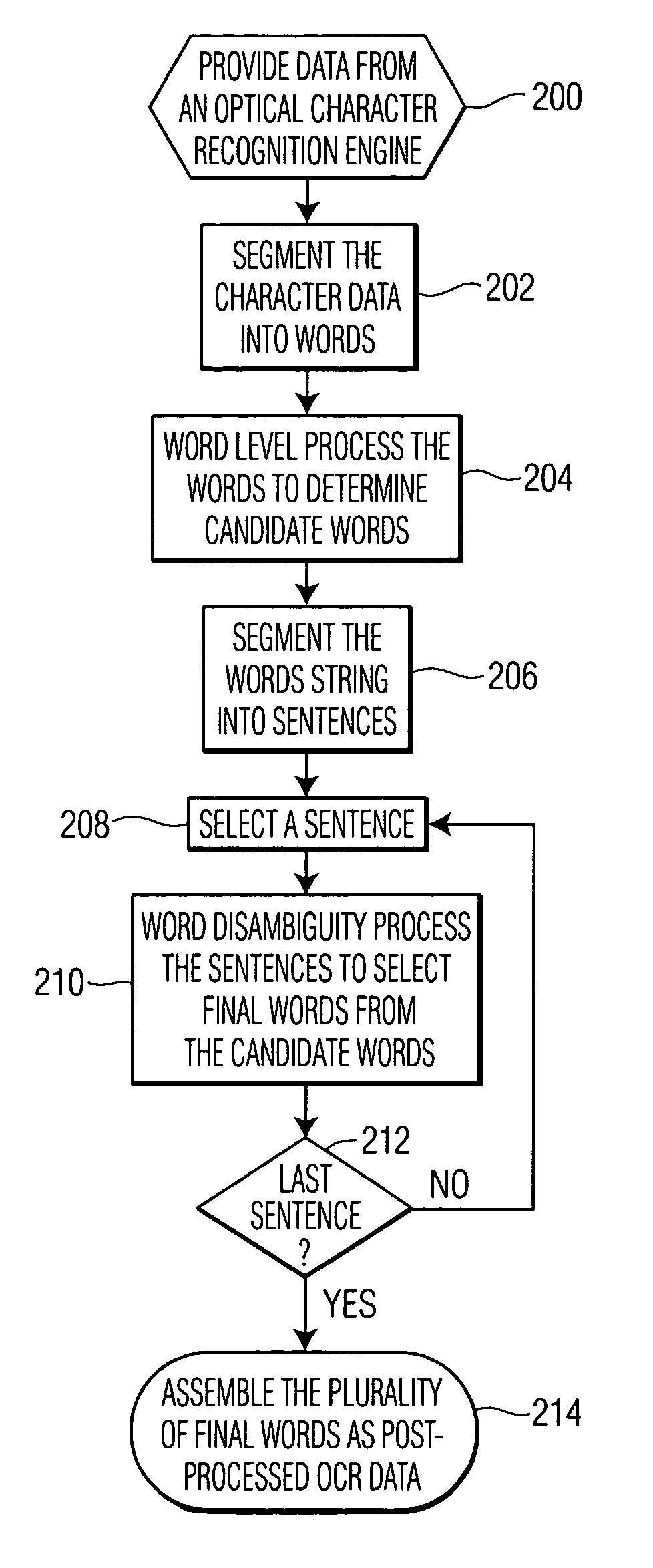
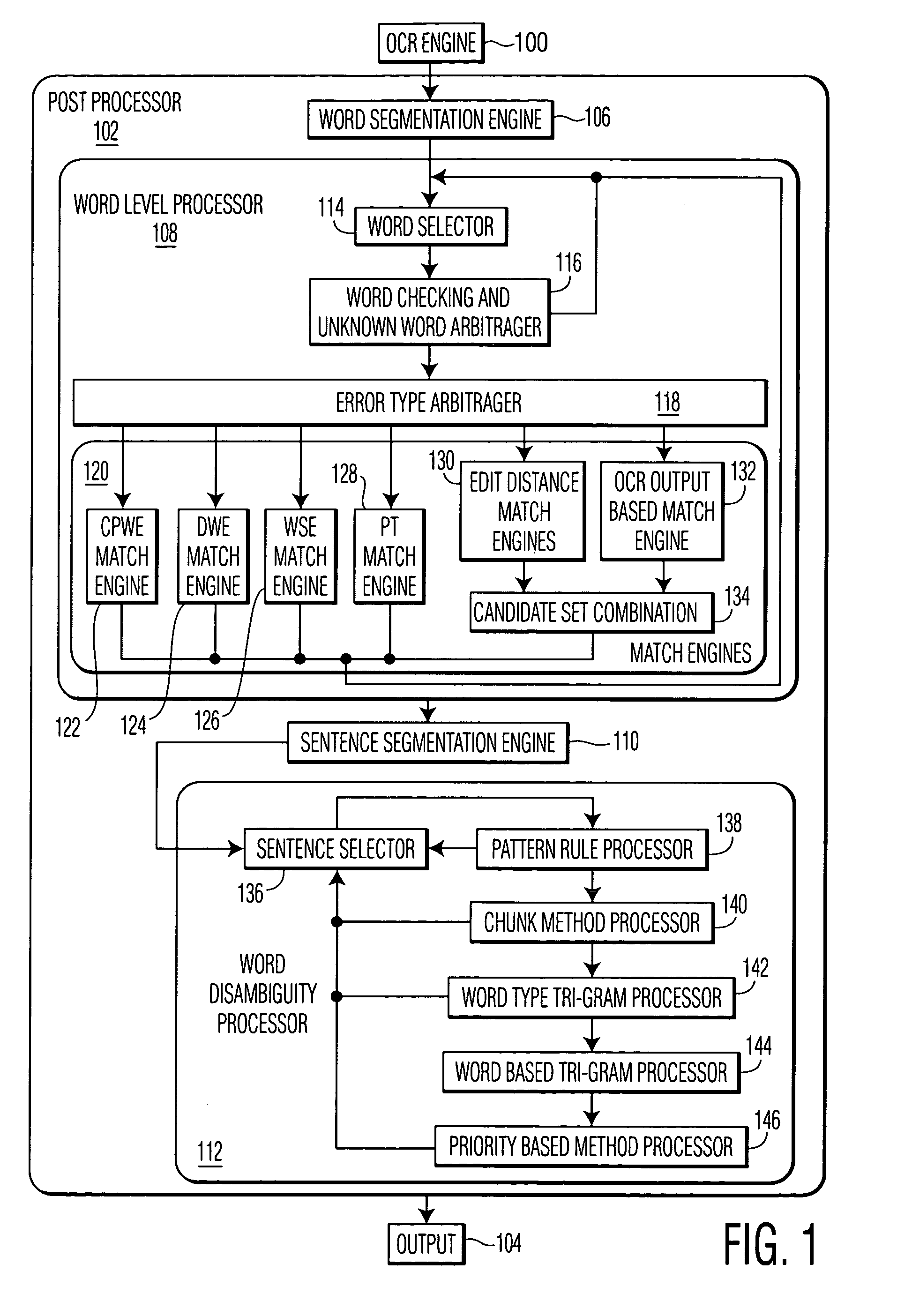
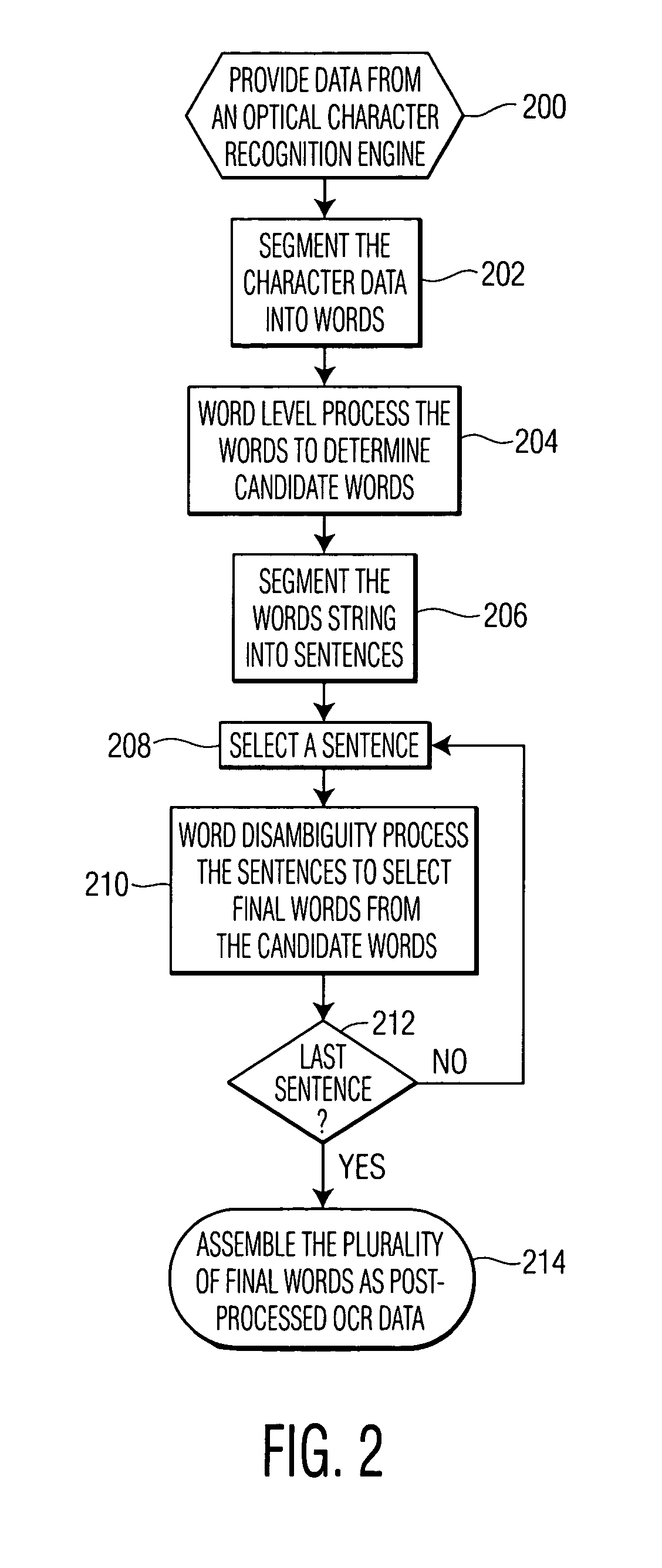
A method of post-processing character data from an optical character recognition (OCR) engine and apparatus to perform the method. This exemplary method includes segmenting the character data into a set of initial words. The set of initial words is word level processed to determine at least one candidate word corresponding to each initial word. The set of initial words is segmented into a set of sentences. Each sentence in the set of sentences includes a plurality of initial words and candidate words corresponding to the initial words. A sentence is selected from the set of sentences. The selected sentence is word disambiguity processed to determine a plurality of final words. A final word is selected from the at least one candidate word corresponding to a matching initial word. The plurality of final words is then assembled as post-processed OCR data.
Owner:PANASONIC CORP
Intelligent bag
InactiveCN105430767APrecise Indoor PositioningDynamic correction positioningCyclesPursesSelf maintenanceAutomatic control
The invention discloses an intelligent bag. The intelligent bag comprises a portable bag, a power source, an intelligent sensor, a network layer, a microprocessor, a man-machine interaction apparatus and an application layer. The intelligent bag is reasonably and effectively integrated with a series of technologies such as navigation positioning, block chains, electronic sensing, data networks, artificial intelligence, distributed calculation, automatic control, machine identification, mobile computation, man-machine interaction and the like and is embedded into a portable terminal so as to improve trip experience of people. An intelligent bag user, as a manager, a supervisor and a user of a peer-to-peer network system in a wireless Ad-hoc network, can perform self-disposition, self-maintenance, self-learning and self-production so that a decentralized self-growing trip database can be constructed. Hopefully, the intelligent bag can be a terminal member of the internet of things of an intelligent city traffic system.
Owner:罗轶
Methods for machine detection of al least one aspect of an object, methods for machine identification of a person, and methods of forming electronic systems
The invention includes electronic systems comprising Si / Ge substrates. The electronic systems can include data storage devices and / or logic devices having active regions extending into a crystalline Si / Ge material. An entirety of the portion of an active region within the crystalline Si / Ge material can be within a single crystal of the material. The assemblies can be utilized for detecting properties of objects, and in particular aspects can be incorporated into assemblies utilized for identifying persons. The assemblies can be fabricated over a range of versatile substrates, including, for example, glass, alumina or metal.
Owner:ROUND ROCK RES LLC
Methods and arrangements for sensing identification information from objects
ActiveUS20130048722A1Increase check-out speedImprove accuracyCash registersVisual presentationComputer graphics (images)Barcode
In one arrangement, retail product packaging is digitally watermarked over most of its extent to allow machine identification by one or more inexpensive cameras at retail checkouts. Such a system also considers image fingerprints, product configuration, barcodes and other available information in identifying products. Imagery captured by conventional or plenoptic cameras is processed to derive several perspective-transformed views, which are provided to the identification system—increasing throughput by minimizing the need to manually reposition items for identification. Crinkles and other deformations in product packaging are optically sensed, allowing the surface to be virtually flattened to aid identification. A marked conveyor belt at the checkout station increases speed and accuracy, and provides other benefits to both shoppers and sellers. A great variety of other features are also detailed.
Owner:DIGIMARC CORP
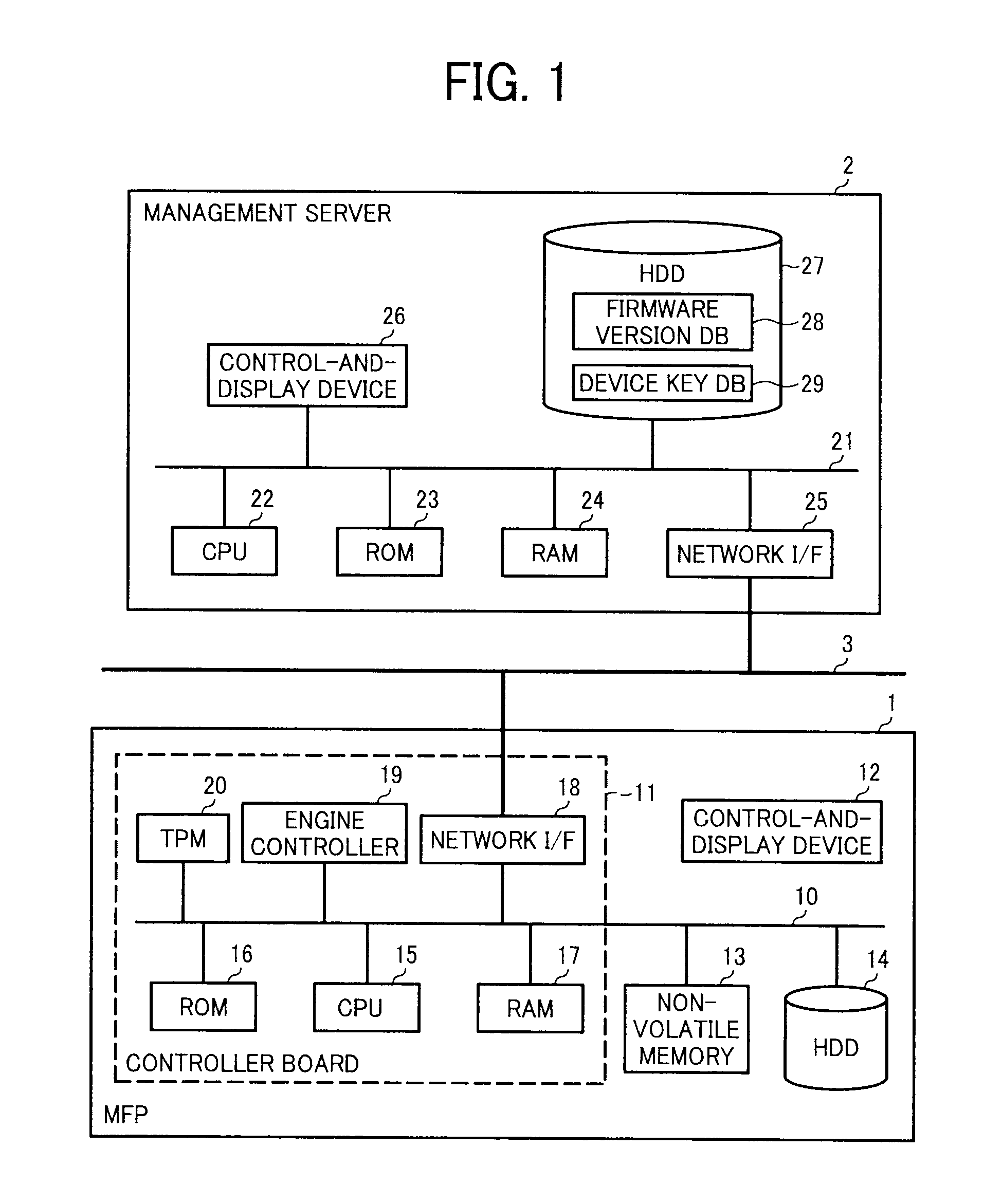
Machine, machine management apparatus, system, and method, and recording medium
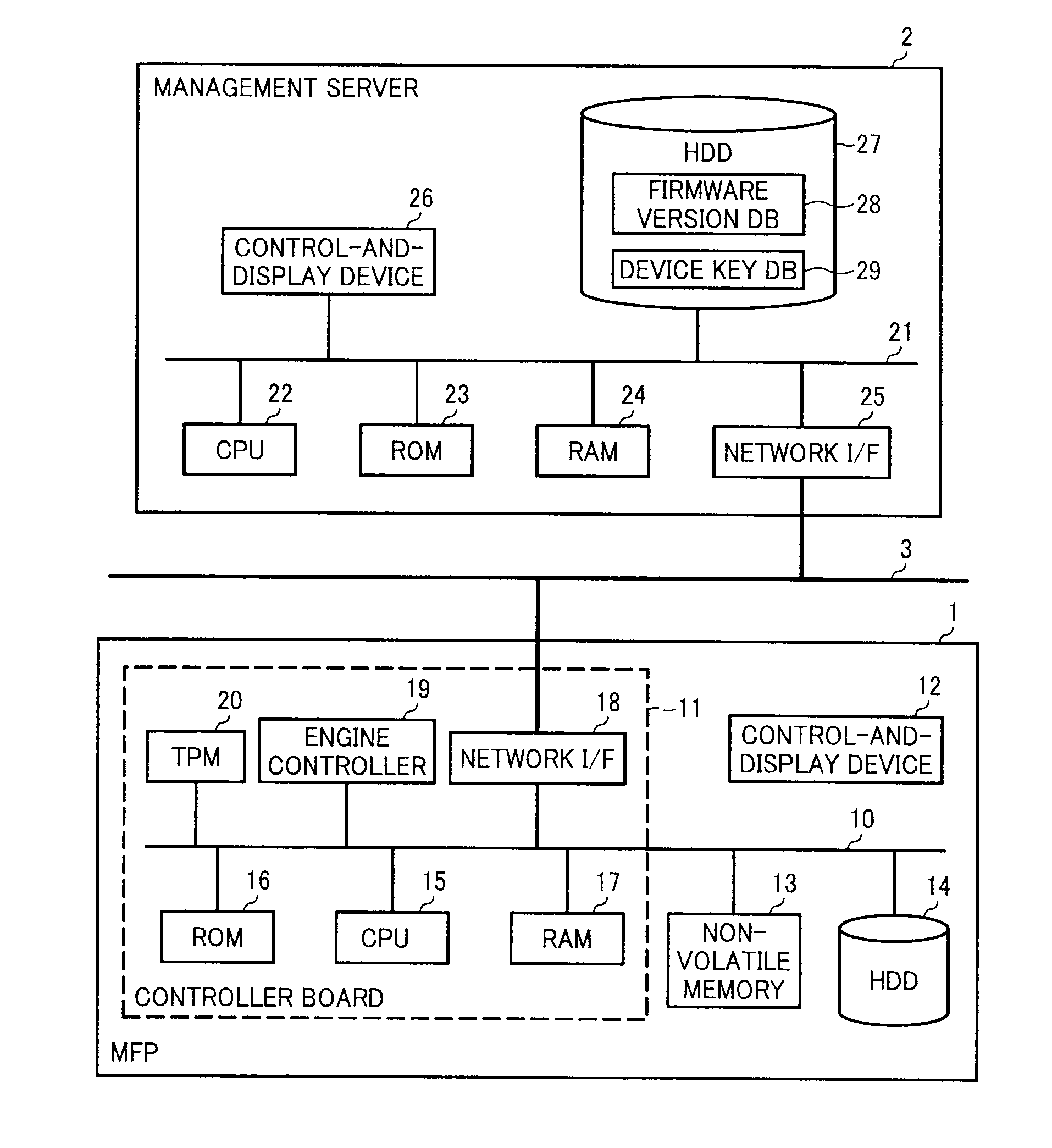
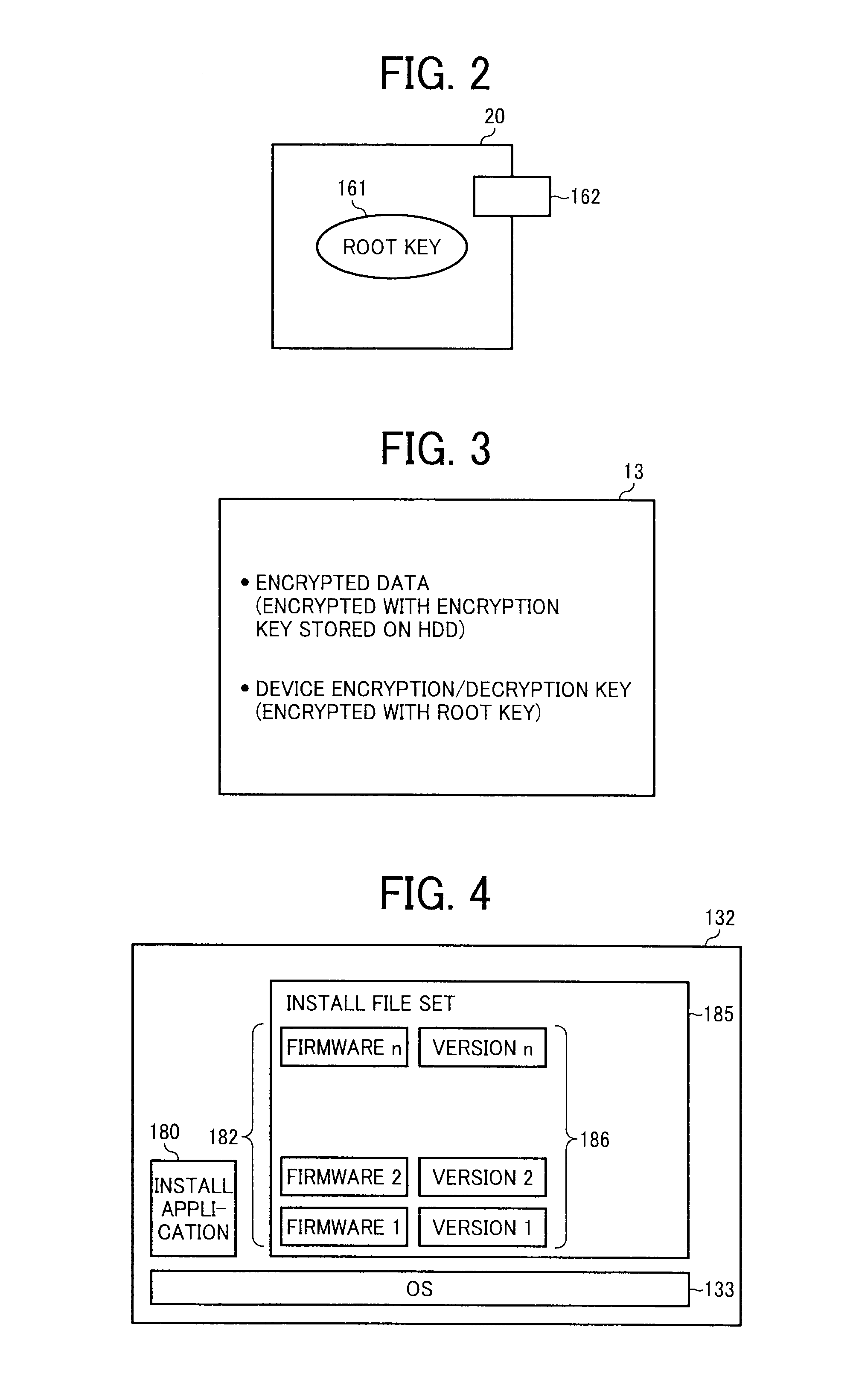
A machine management method includes installing software in a machine including a security device that holds a secret key unextractable from the security device and a public key extractable from the security device, encrypts input data with the public key, and decrypts the input data with the secret key; storing machine identification information of the machine in association with software identification information of the software installed in the machine in an external management apparatus; creating a device-encryption key to encrypt data stored on a first storage device of the machine; storing a device-encryption-key BLOB obtained by encrypting the device-encryption key with the public key on a second storage device of the machine; and storing the device-encryption key in association with the machine identification information in the external management apparatus.
Owner:RICOH KK
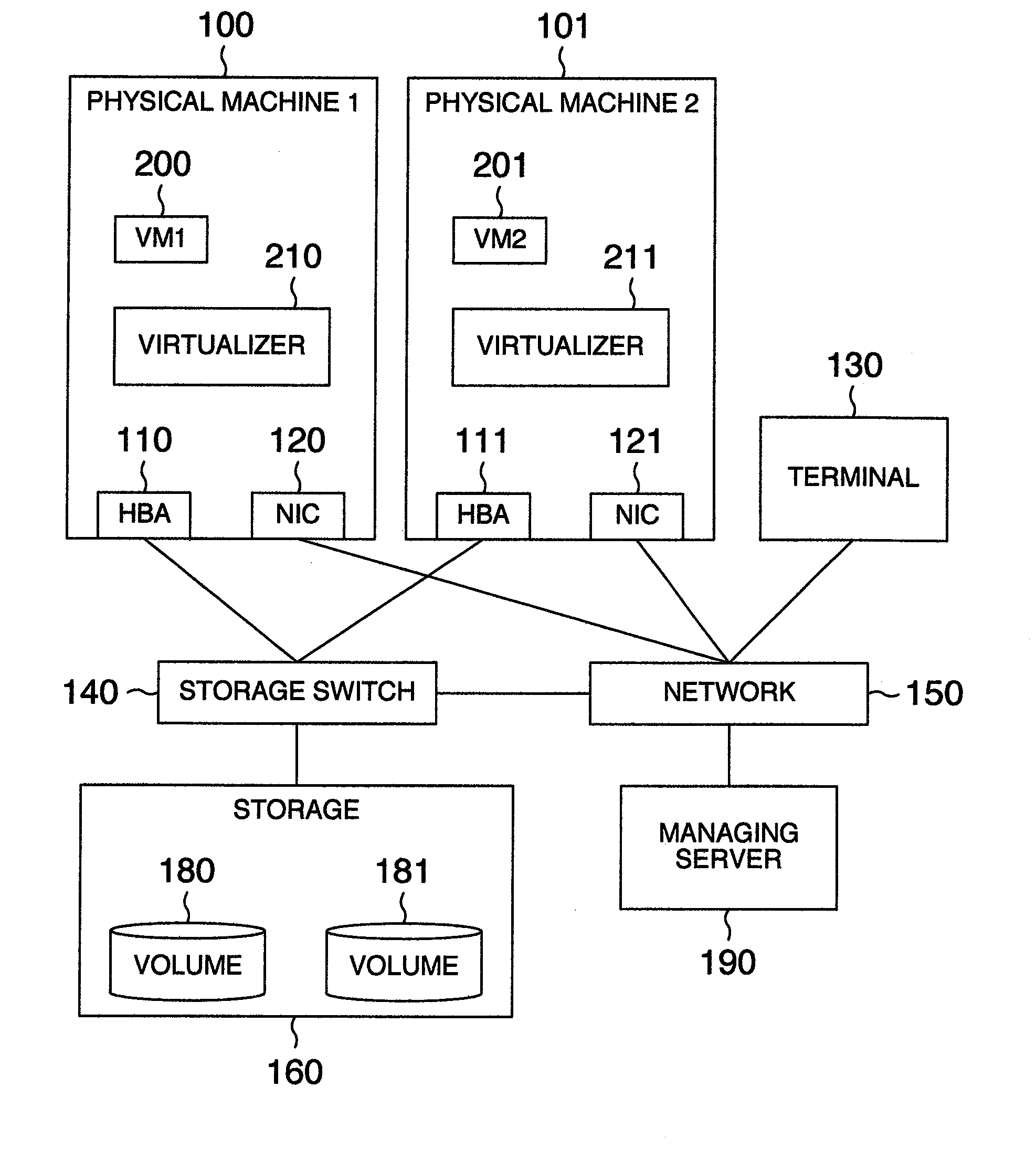
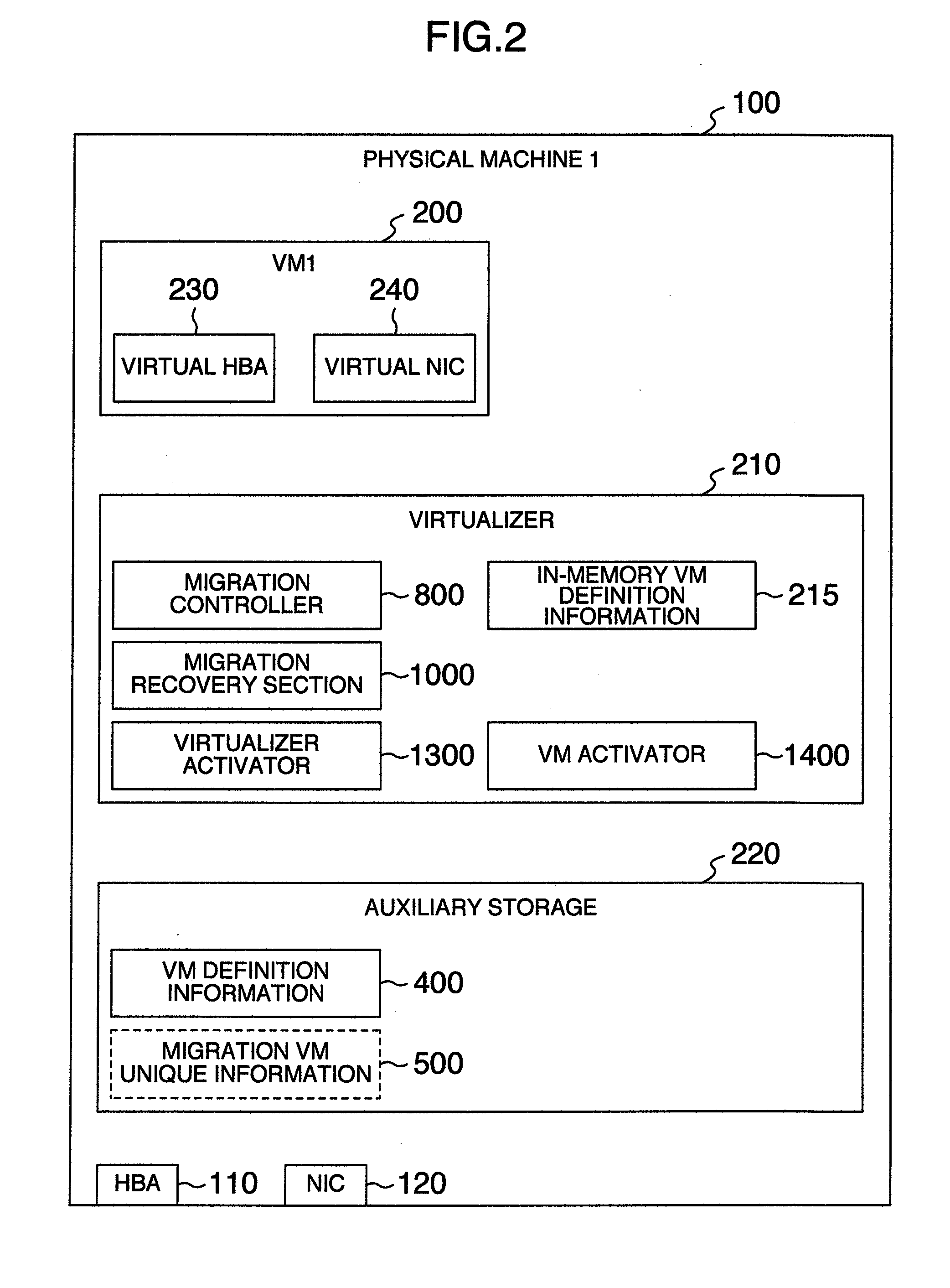
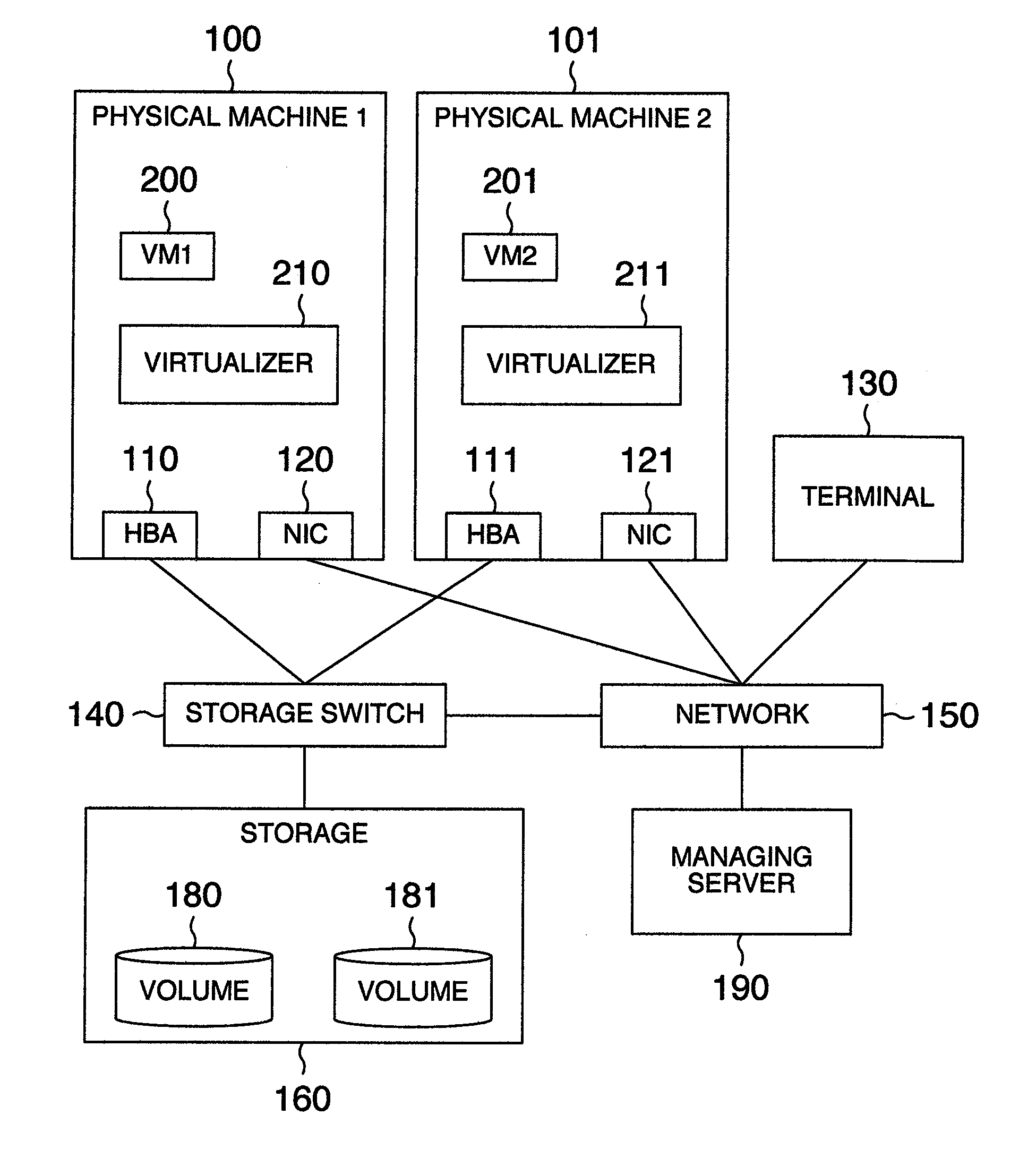
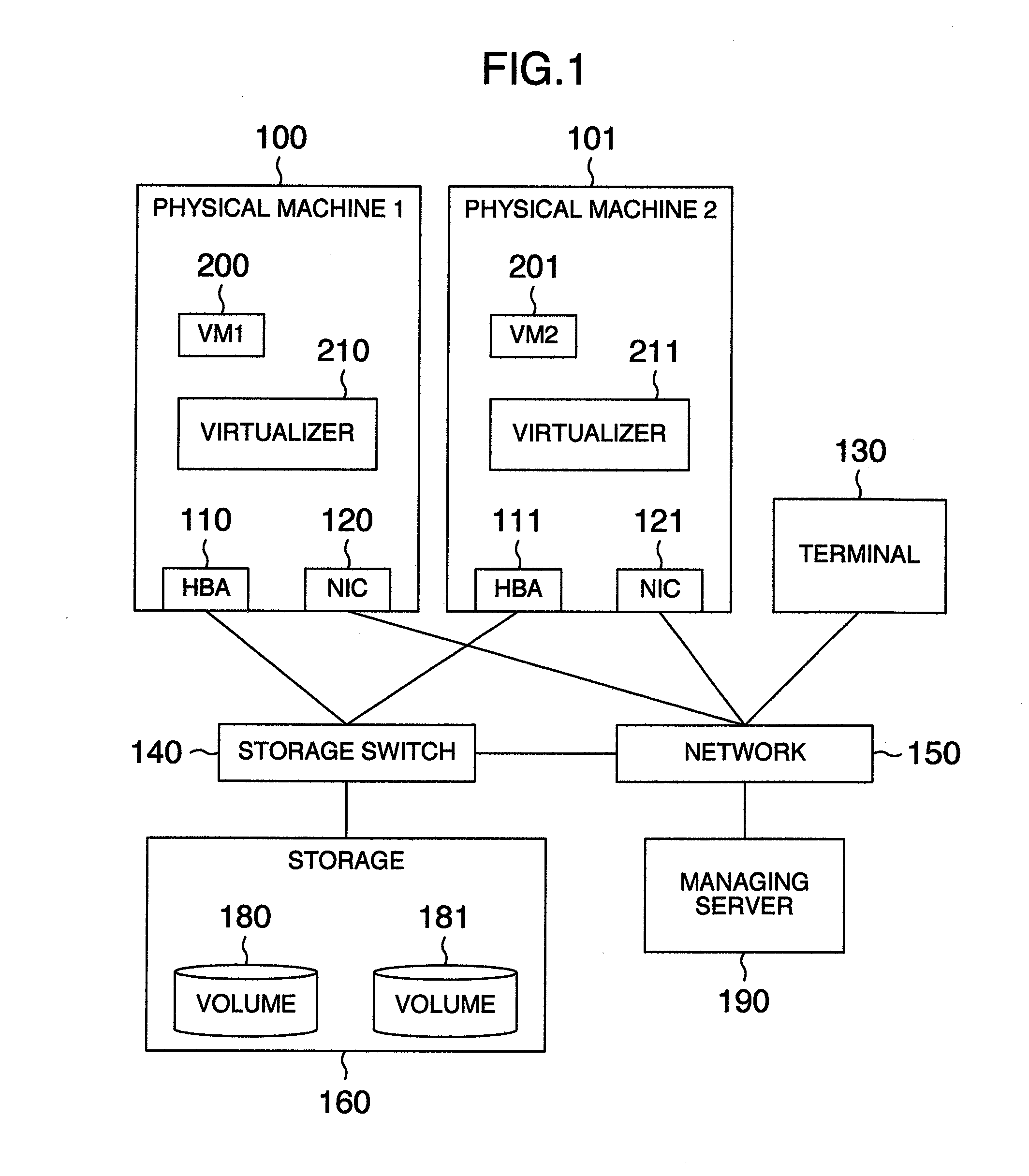
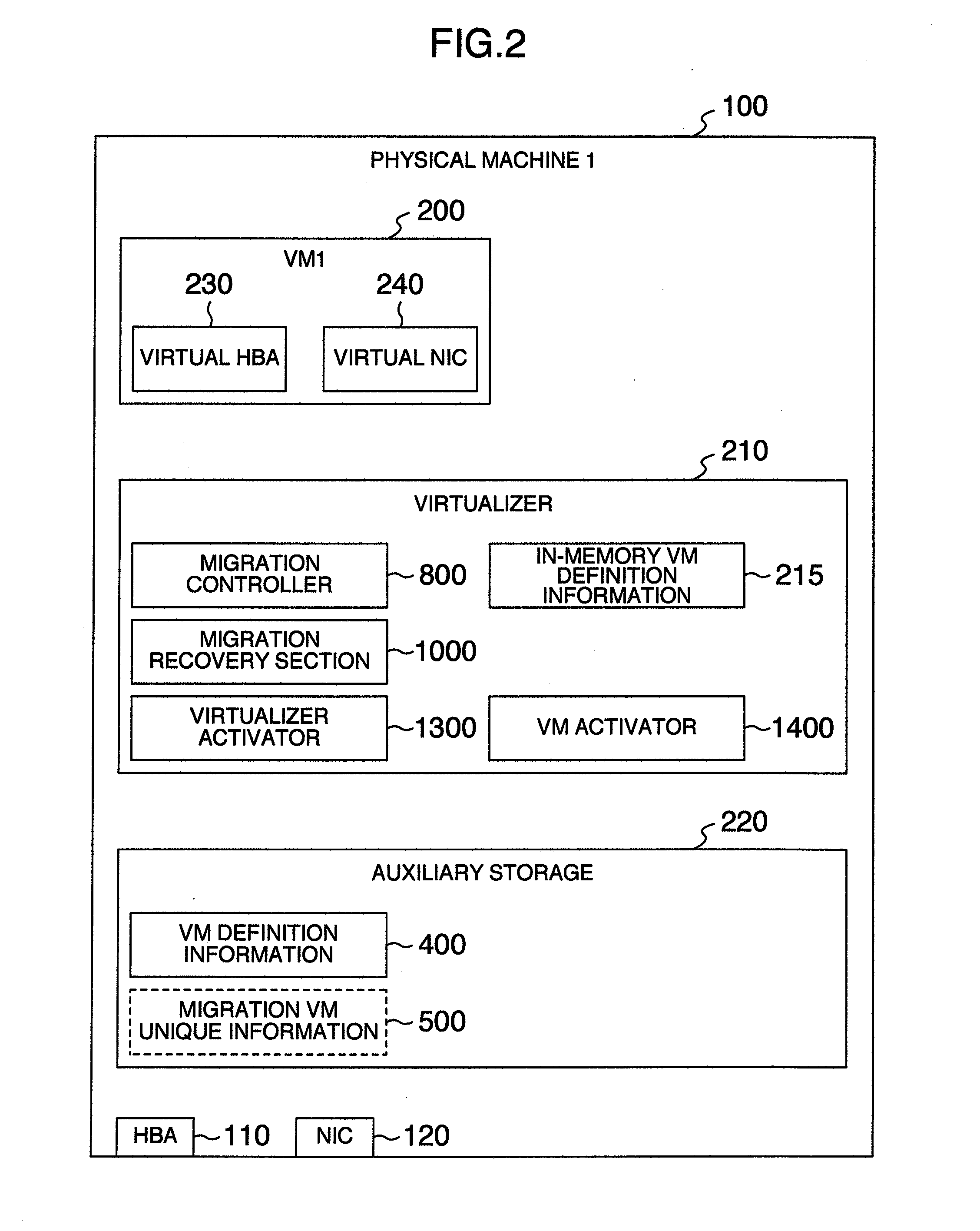
Virtual machine migration managing method, computer using the method, virtualizer using the method and computer system using the method
ActiveUS20110131576A1Without deteriorating securityAppropriate settingSoftware simulation/interpretation/emulationMemory systemsComputerized systemComputer science
In a system including a plurality of physical machines to execute virtual machines (VM1, VM2), migration virtual machine information and definition information are saved in a physical machine executing a virtual machine (VM1) to be migrated and a storage of a physical machine as a migration destination. During the migration of the virtual machine, machine identification information of a migration partner, unique information assigned to the virtual machine, and information indicating whether the physical machine executing the processing is a migration-source or migration-destination physical machine are saved in a migration information storage area. A migration recovery section examines information stored in a definition information storage area and a migration information storage area to determine a recovery procedure to restore the virtual machine.
Owner:HITACHI LTD
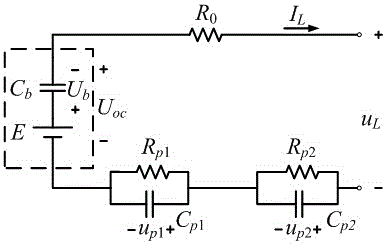
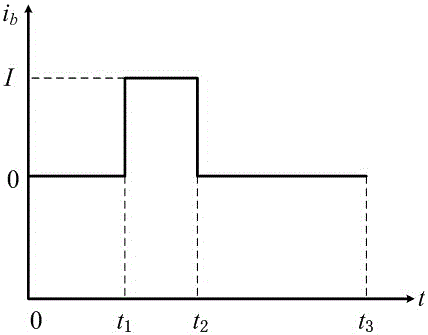
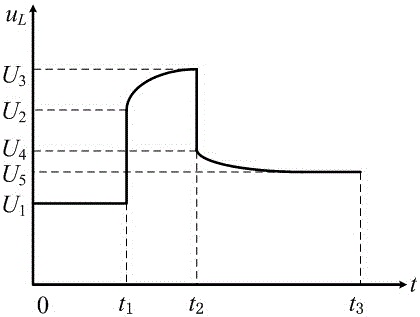
Battery SOC (state of charge) estimation method by utilizing vehicle-mounted charging machine identification battery parameter
InactiveCN105068008AOvercome the impact of estimation accuracyEasy to operateElectrical testingElectrical batteryEstimation methods
The invention relates to a battery SOC (state of charge) estimation method by utilizing a vehicle-mounted charging machine identification battery parameter. A battery model parameter is identifies through a pulse experiment which is performed by an electric automobile vehicle-mounted bidirectional charging machine on a battery, the battery capacity is recalibrated by utilizing the bidirectional charging machine to perform deep charging and discharging on the battery, extended Kalman filtering is performed then according to an updated battery parameter to estimate a state of charge (SOC) of the battery, and then an influence of a battery parameter changed, which is caused by aging, on battery SOC estimation precision is overcome. A changing battery parameter can be effectively tracked, and a selection of initial data is not depended on; the battery parameter is identified through charging and discharging which are performed by the vehicle-mounted bidirectional charging machine on the battery, and an advantage that an electric automobile is provided with a power electronic conversion device is fully used; in the whole parameter identification process, an electric energy released by the battery is grid-connected in a feedback manner, and energy loss is small; and the method is simple and practicable, and tedious operation that a traditional off-line identification battery parameter method needs to detach a battery box is prevented.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
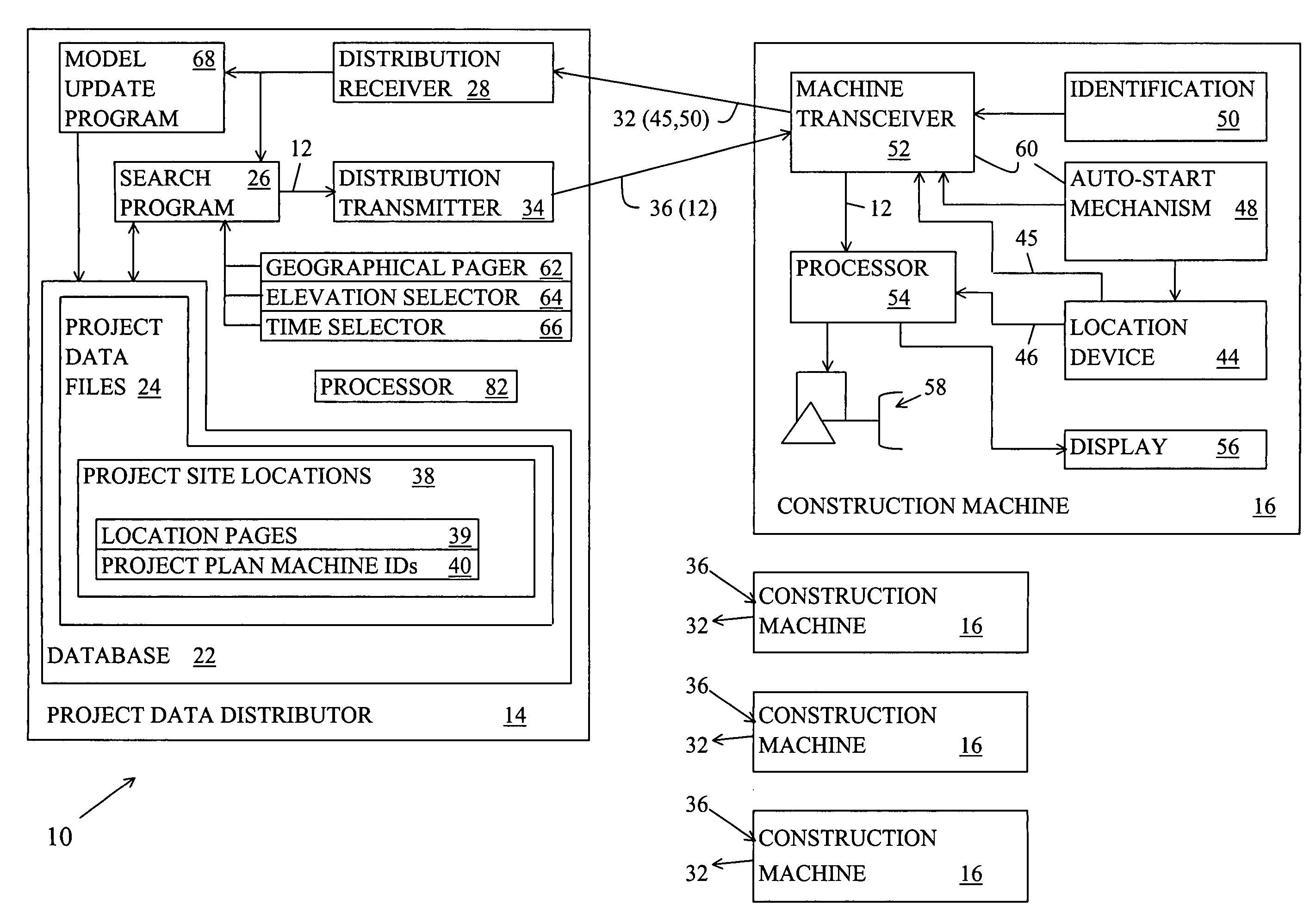
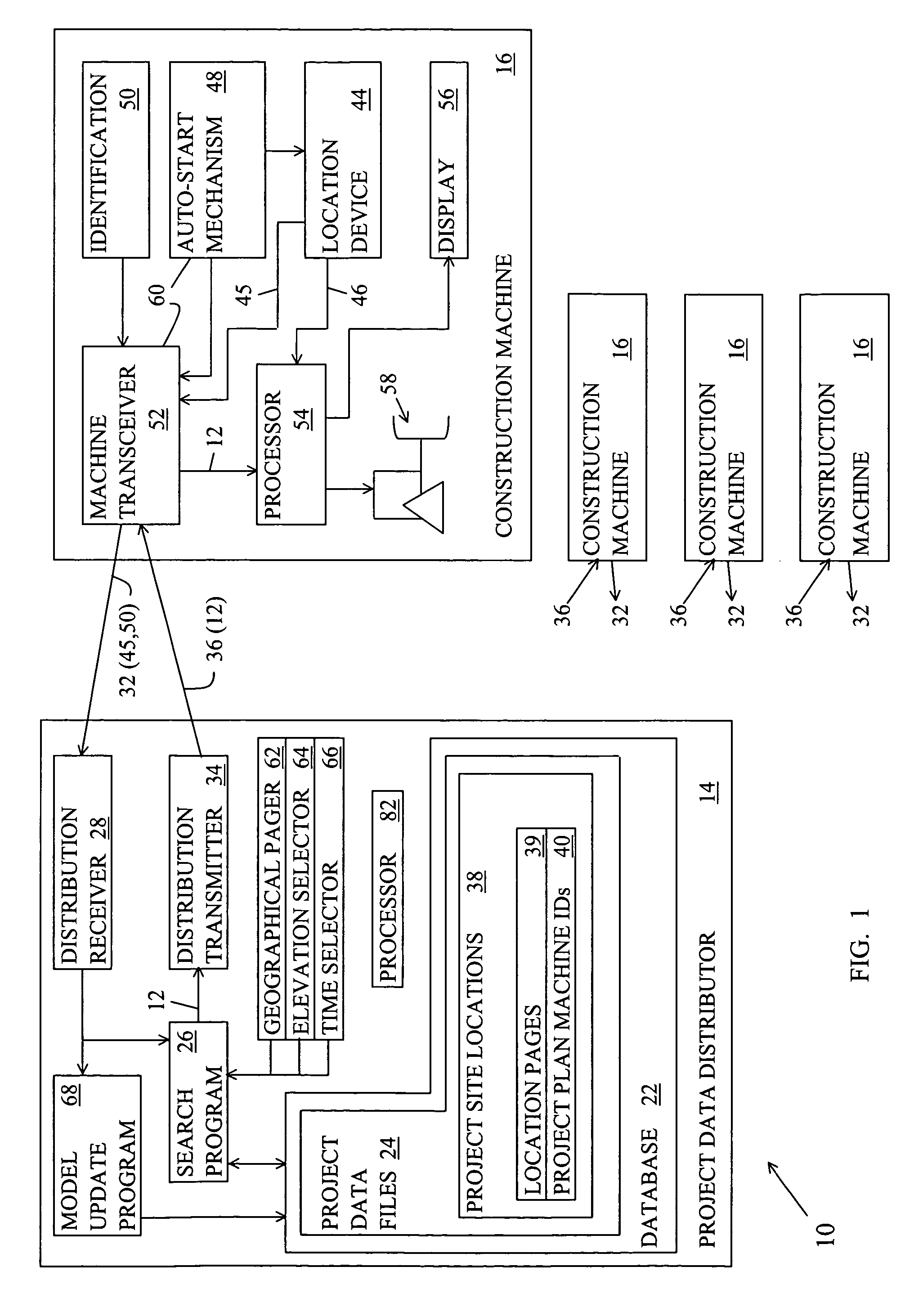
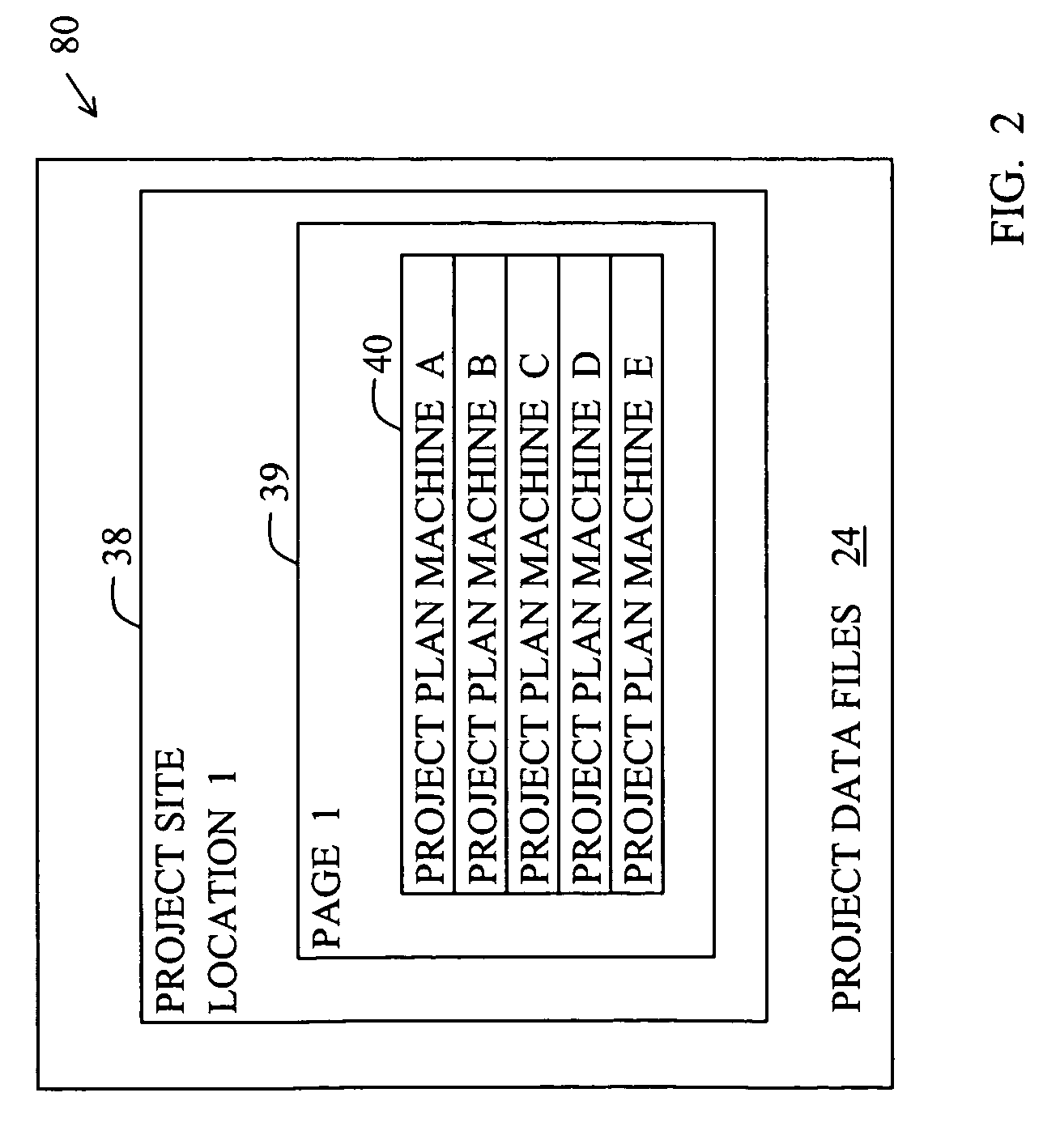
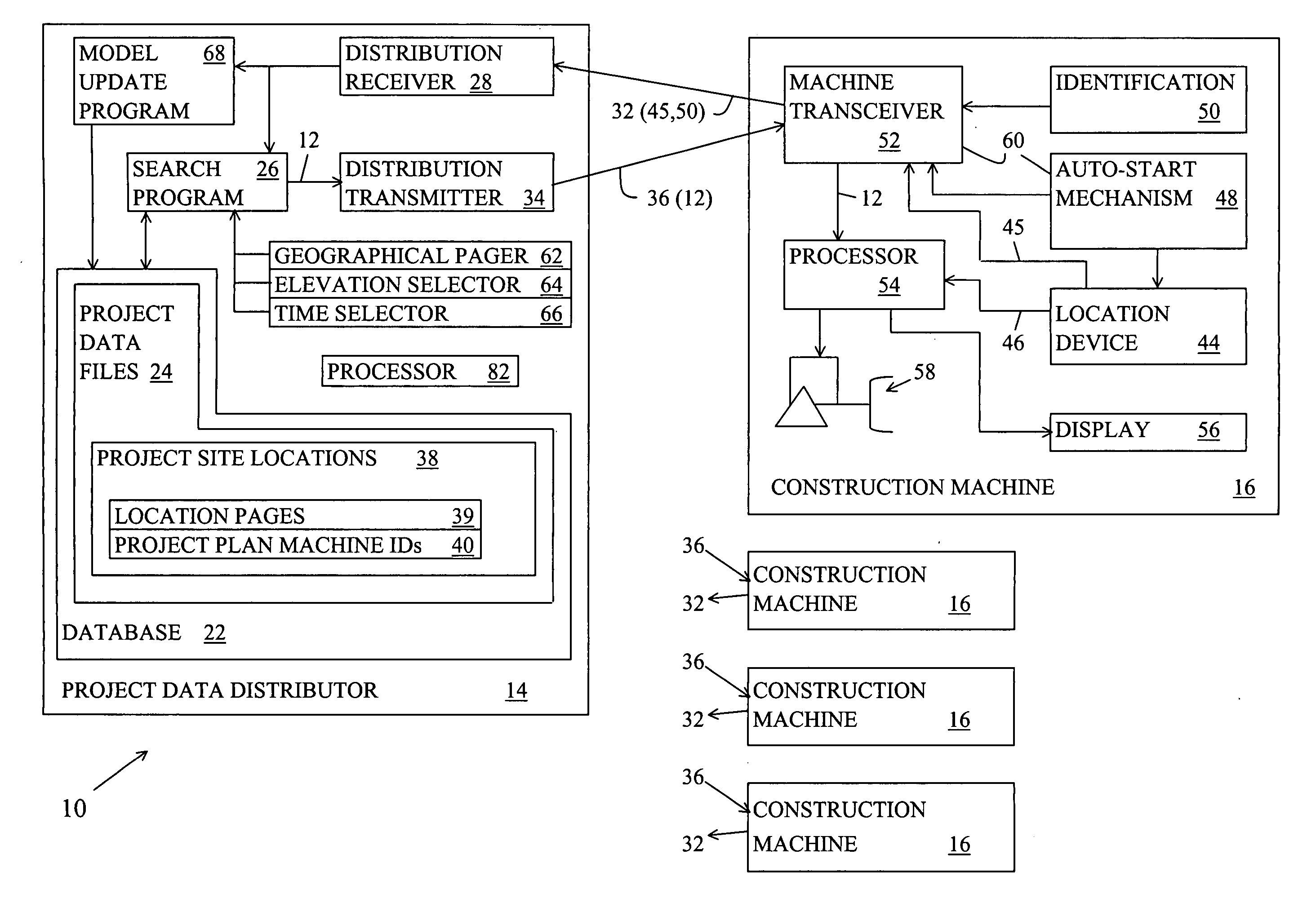
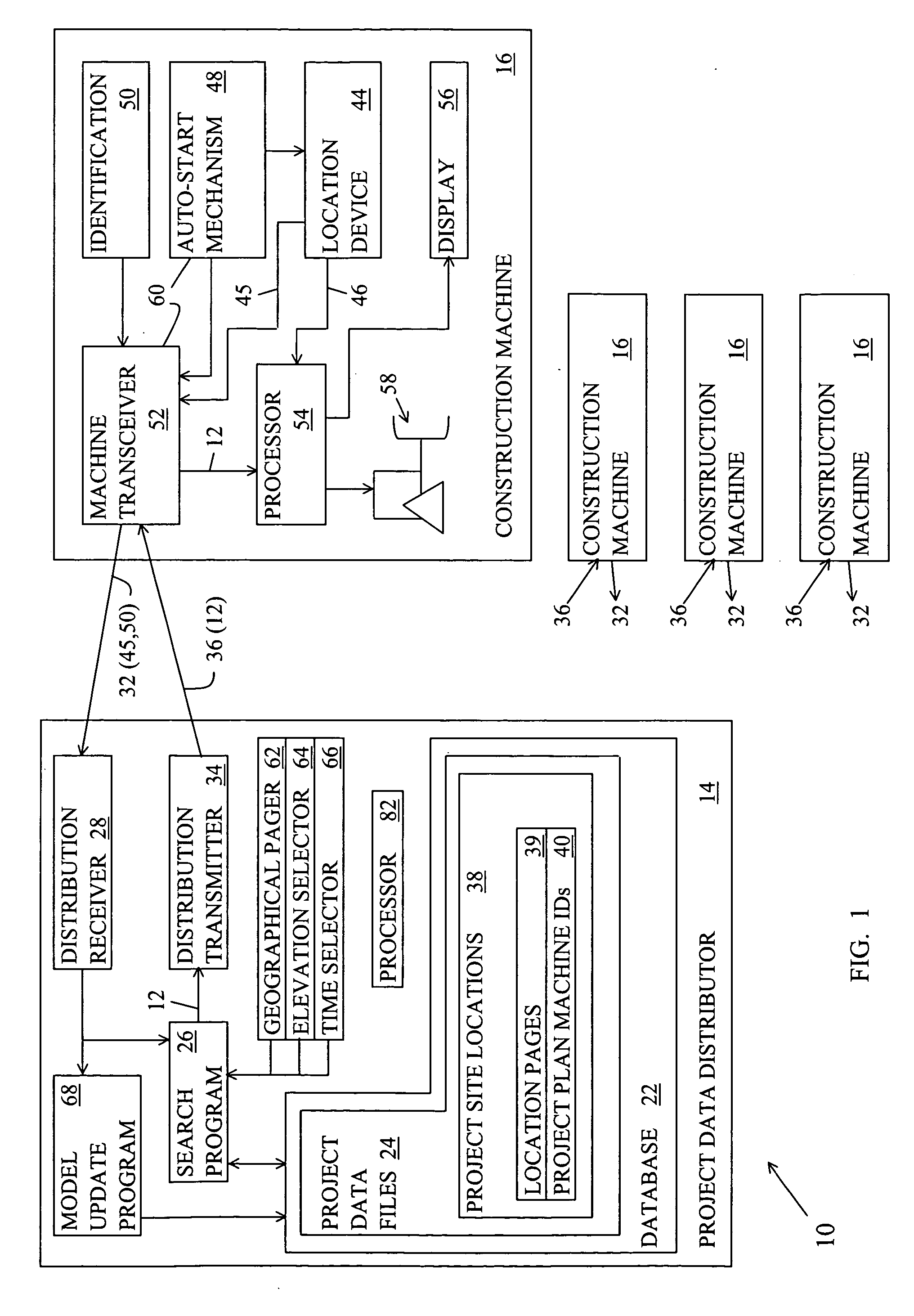
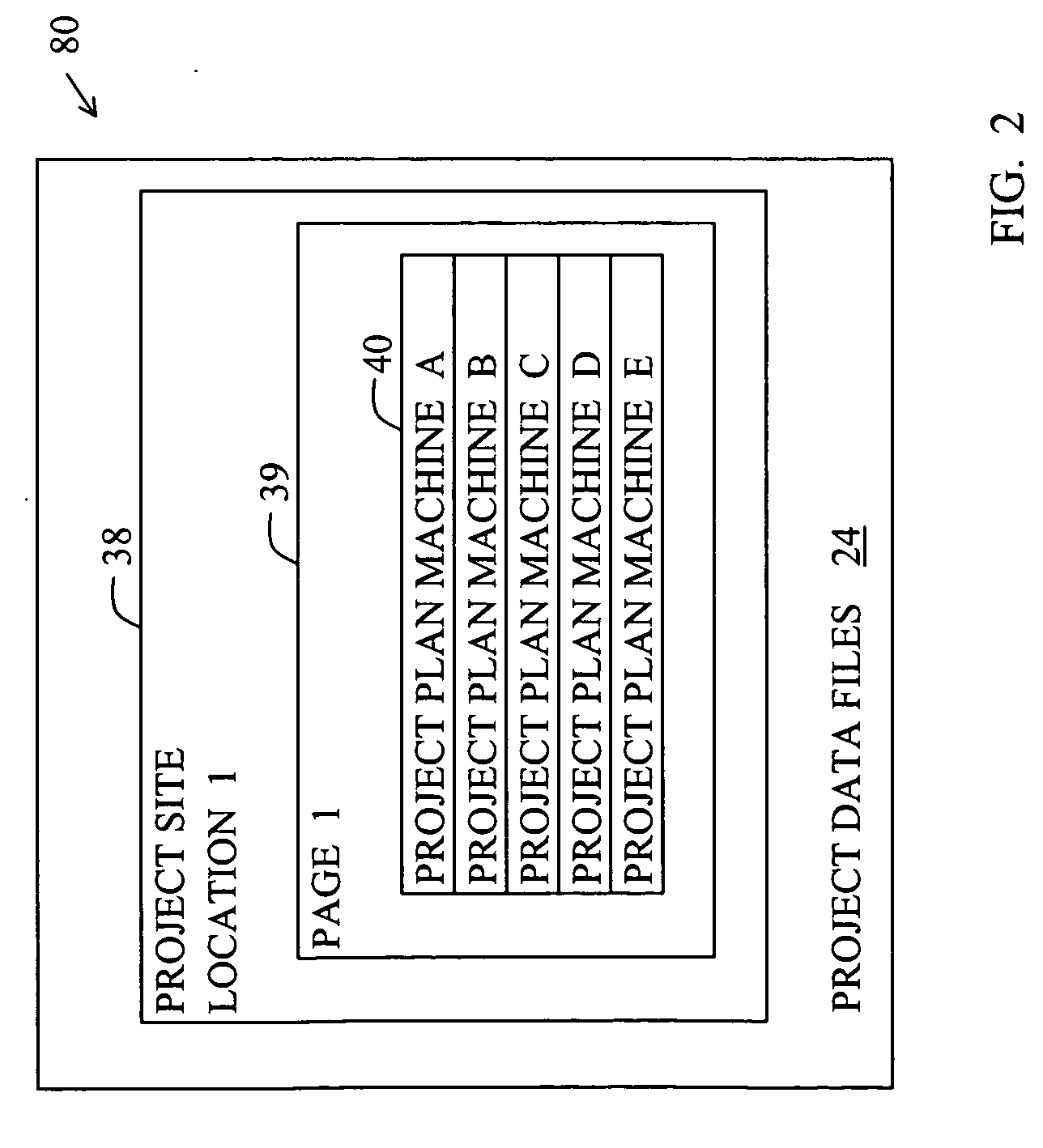
Location-centric project data delivery system for construction
ActiveUS7681192B2Automatic deliveryResourcesSpecific program execution arrangementsProgram planningData file
A project data delivery apparatus for automatically delivering project data files to a construction machine based on the geographical location and identification of the construction machine. The apparatus includes a project data distributor for storing, maintaining and transmitting project data files that are associated with project site locations and project plan machine identifications.
Owner:CATERPILLAR TRIMBLE CONTROL TECH
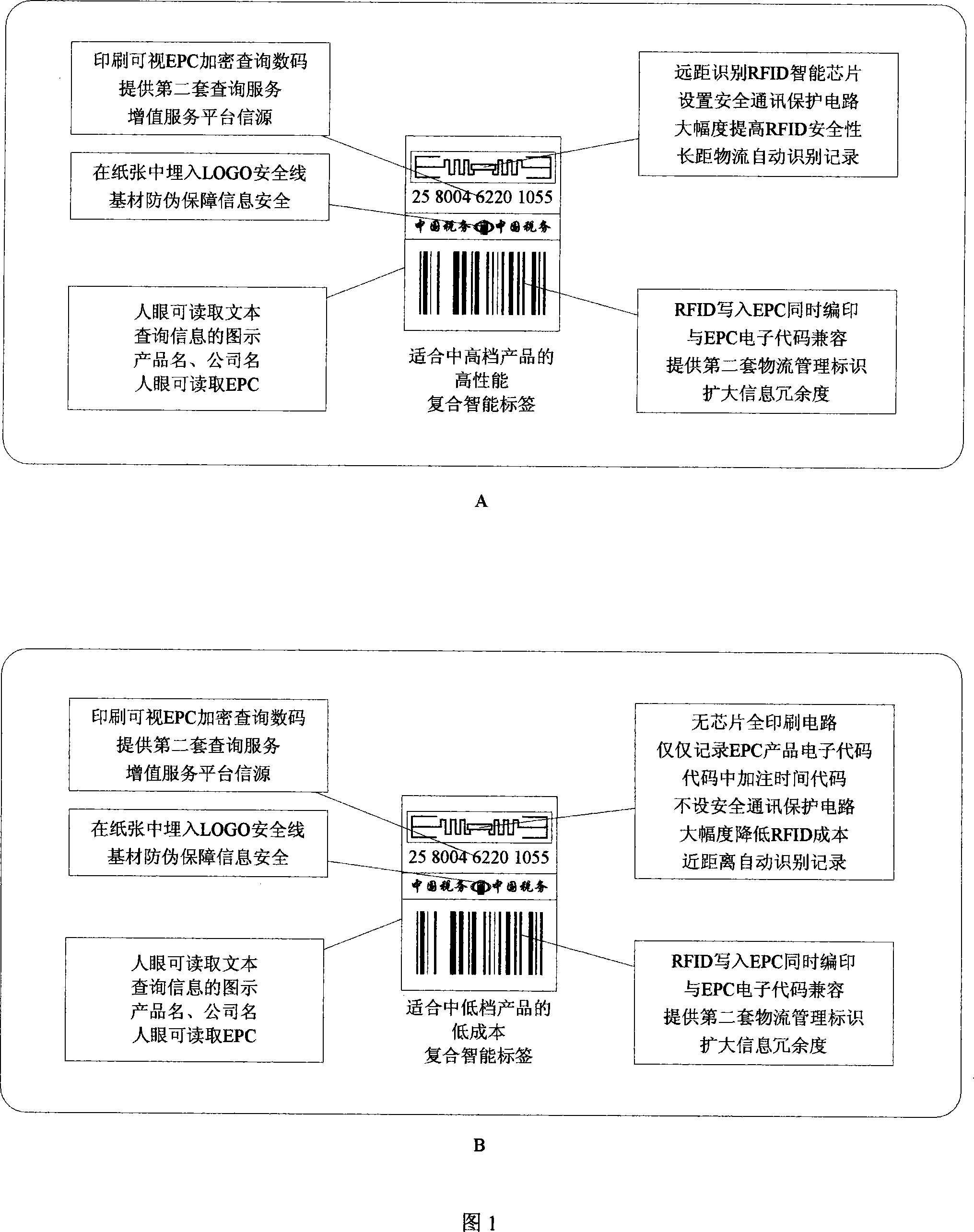
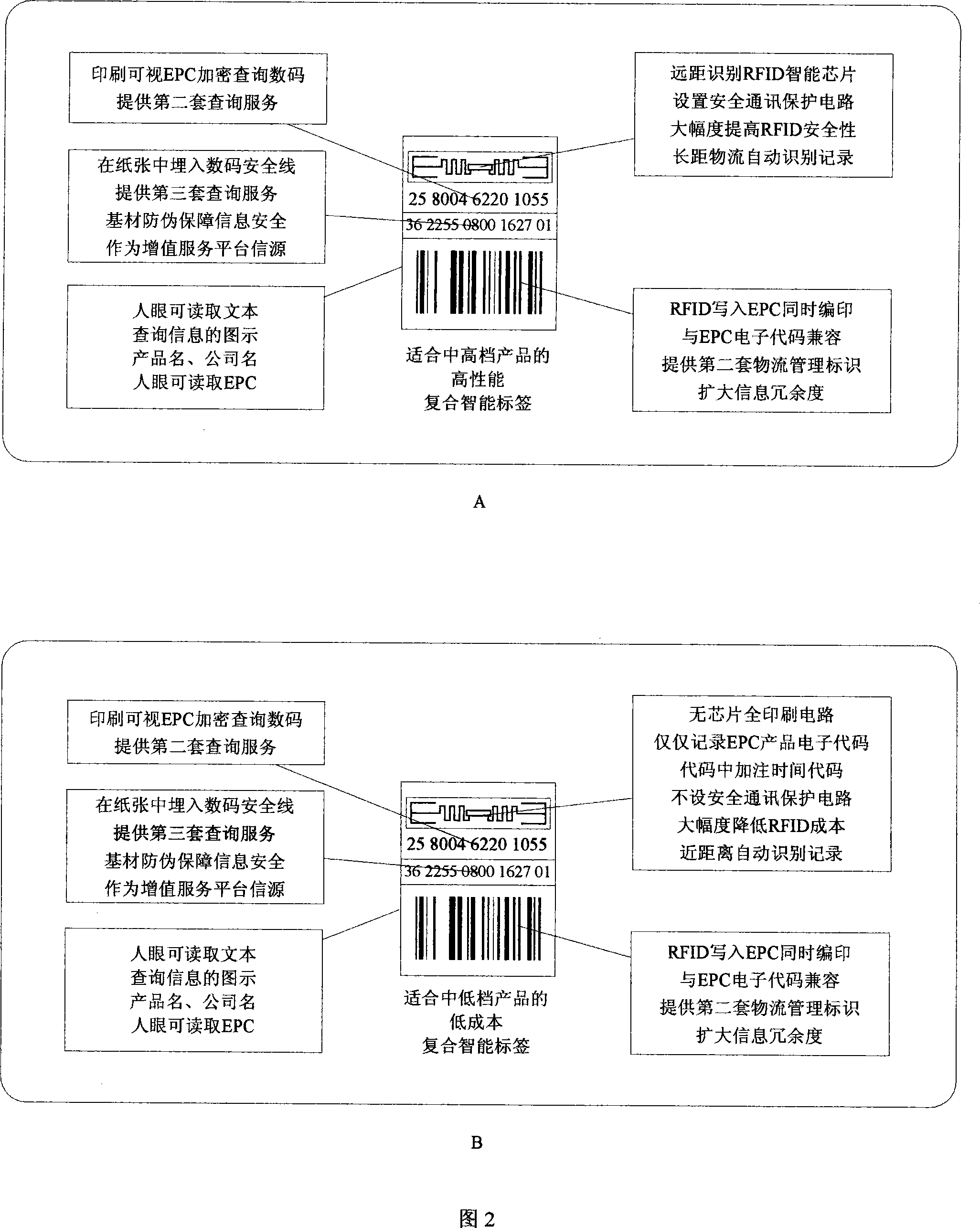
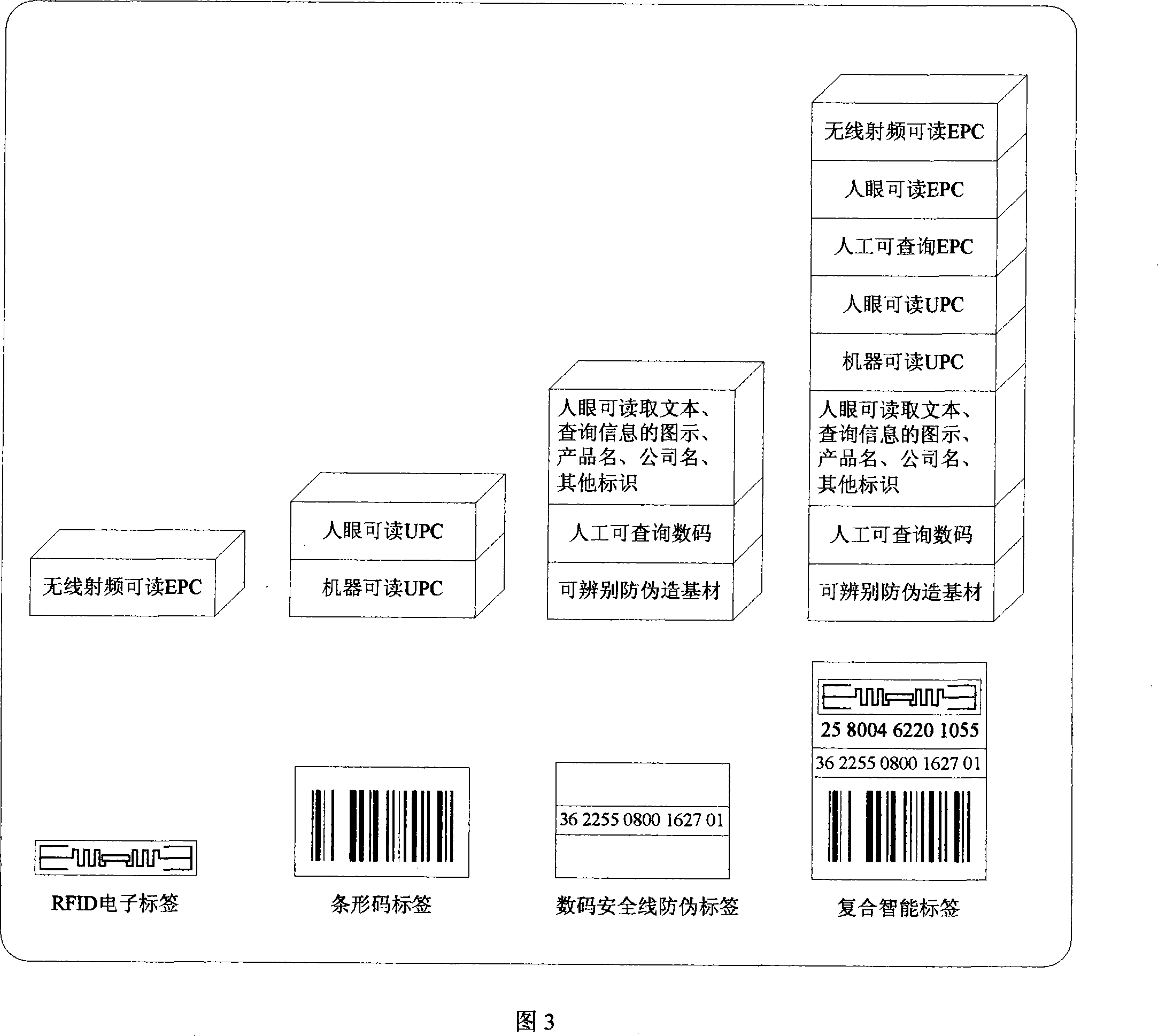
A coding and preparation method for the multiple cross-validation of RFID compounding labels and its system
InactiveCN101216897AImprove securityAvoid security breachesDigitally marking record carriersPaper/cardboard articlesPlaintextThe Internet
The invention relates to a method for encoding and manufacturing a multi-interactive authentication RFID compound intelligent tag, as well as a system thereof. An EPC product electronic code which is provided with a time code and is randomly corresponding to a sequence code is prepared as a storage code of a non-chip RFID, a surface acoustic wave RFID or a powder RFID chip; the code is converted to a plaintext code via encryption and is printed on a tag for covering; the plaintext code is converted to a bar code and printed on the tag; a digital safe line production tag is used to carry out the pre-chopping treatment of the tag, so as to prevent the transfer; numbers on the safe line are identified by photography; EPC codes, passwords, bar codes and the safe line digital codes are stored correspondingly; a tag anti-counterfeit system, a bar code scanning system and a radio frequency identification system are all connected with the Internet of Things; thus the same product information and logistics path information can be accessed through the EPC Internet of Things regardless of using radio frequency identification, man-made identification or machine identification. The invention can greatly reduce the tag cost, improve the safety, and expand the information redundancy and the application adaptability.
Owner:SICHUAN ZHENGDAOTIANHE INFORMATION TECH
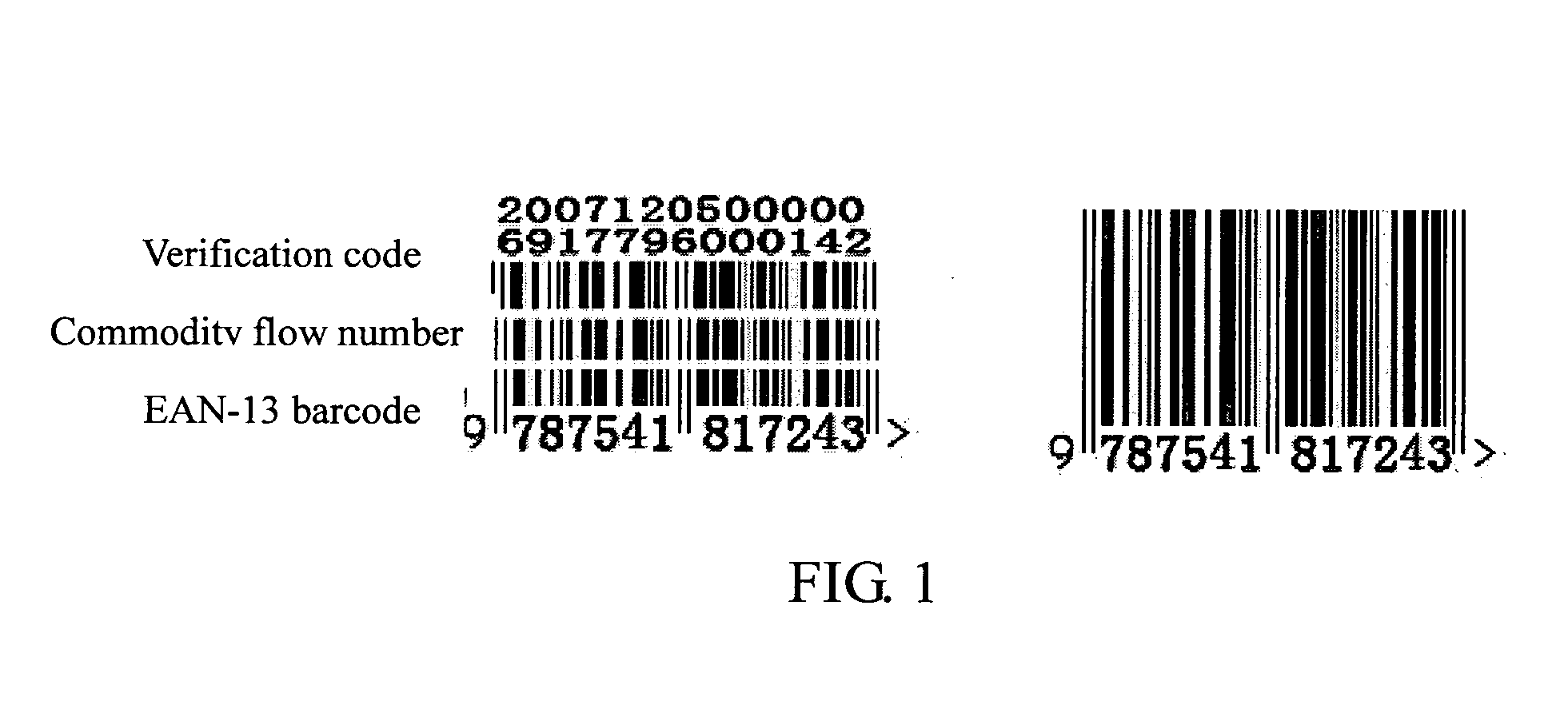
3-in-1 barcode for identifying commodity
InactiveUS20100258641A1Easy to identifyEasy to counterfeitResourcesRecord carriers used with machinesBarcodeComputer science
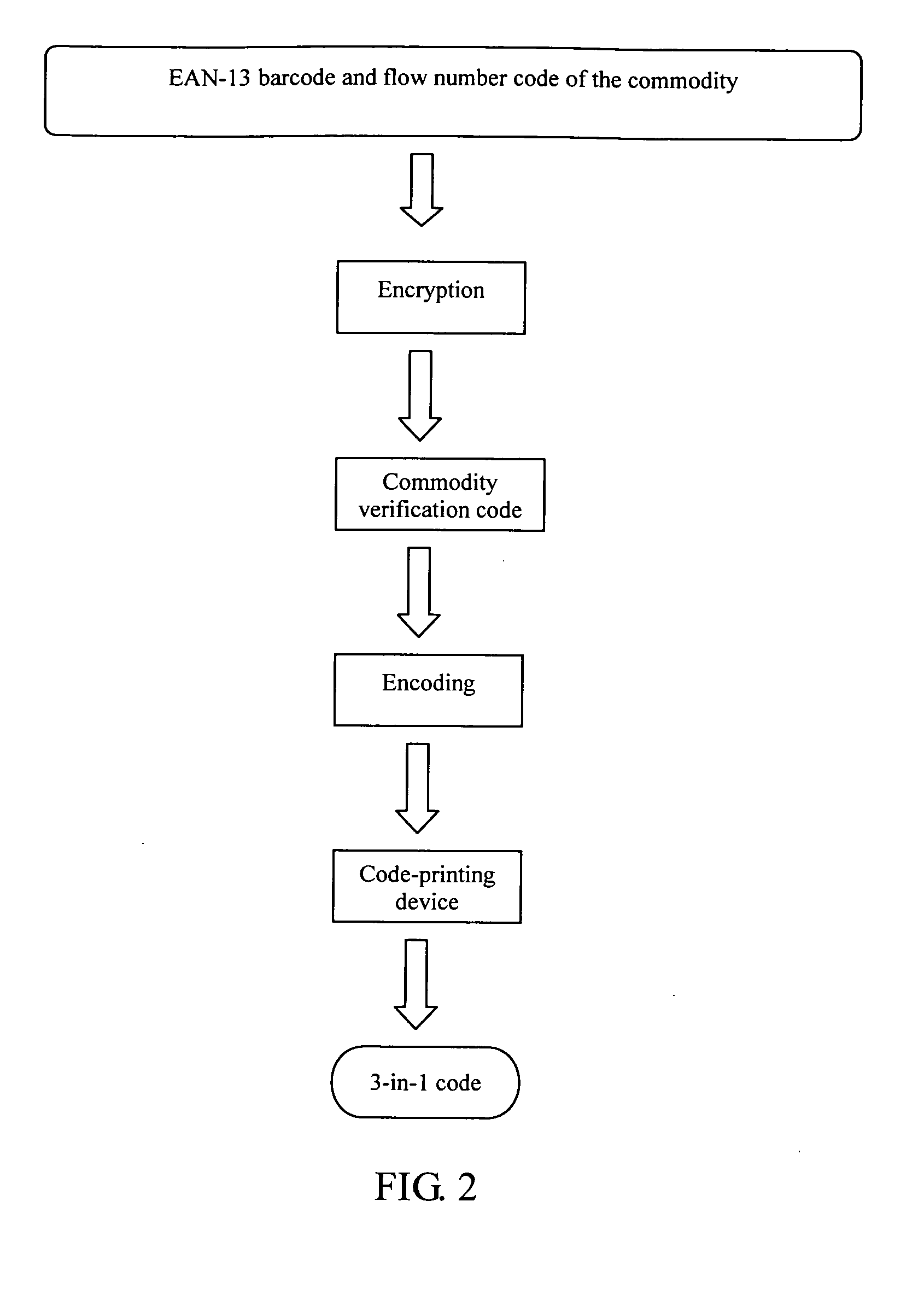
A 3-in-1 barcode for identifying a commodity, involving a commercial cipher technology, is implemented through the following steps: acquiring a first and second group of data in the form of 13-digit decimal number that are input into a computer for being processed; determining whether the first group of data satisfies an EAN-13 encoding principle or not, and whether the second group of data satisfies an commodity flow number encoding principle or not, if yes, proceeding to the next step, otherwise, generating an error prompt; performing an encryption operation on the first group of data satisfying the EAN-13 encoding principle and the second group of data satisfying the commodity flow number encoding principle through a commercial cipher algorithm, and generating a 13-digit decimal verification code data; dividing the first group of data, the second group of data, and the verification code data into three rows by the computer; and storing and printing the 3-in-1 barcode divided into three rows by the computer, for machine identification. The advantage of the present invention lies in that the 3-in-1 barcode has a plain part and a cipher part, which is easily identified by both the users and consumers, and cannot be easily counterfeited and forged.
Owner:YU ZHI
Identification method for network access equipment and implementation system for identification method
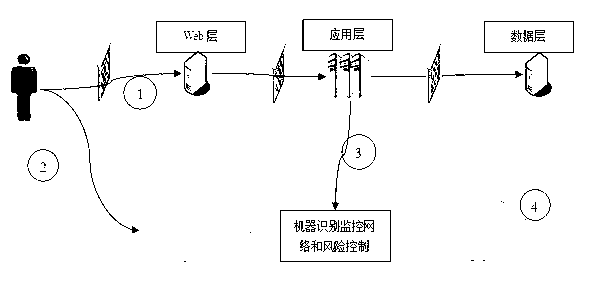
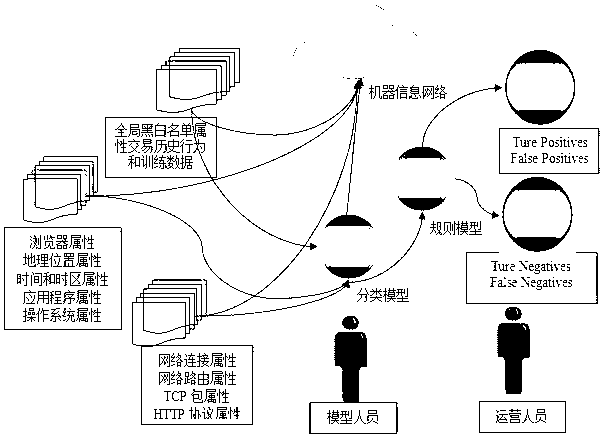
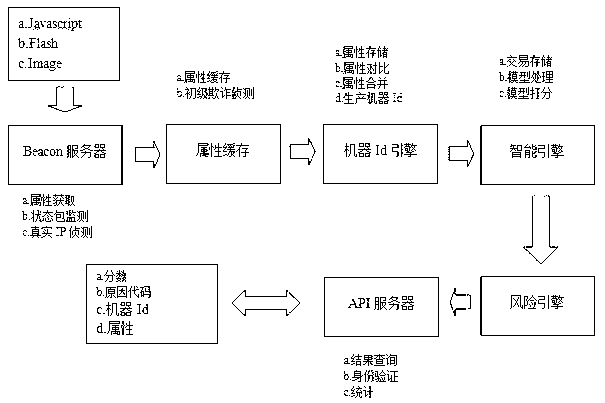
InactiveCN102710770AAccurate discriminationDiscrimination ability, unique identification is accurateTransmissionWeb serviceVia device
The invention discloses an identification method for network access equipment and an implementation system for the identification method. The method comprises the following steps that: a user is connected with and accesses a web service layer through the network access equipment, and software embedded into an application program page of a client acquires information about the network access equipment of the user, wherein the information comprises an equipment attribute, a state packet, a real Internet protocol (IP) address and a user behavior attribute; the network access equipment is connected with an established equipment fingerprint database, and performs retrieval to identify whether the network access equipment exists or not; the user enters an application layer for access or a specific transaction function, and a cloud computing cluster-based equipment fingerprint management platform integrates a machine identification and monitoring network and risk control, performs uniqueness identification on the network access equipment according to the network attribute of the equipment, and judges whether the network access equipment has an unconscious change or a conscious deceptive behavior or not; and the operation of the user over the network access equipment is identified and recorded, and a result is stored in the equipment fingerprint database. According to the technical scheme, the functions of network access equipment query, risk early warning, equipment tracking and the like are provided for the user by fully utilizing the network attribute and the high computing and judgment capability of a cloud computing cluster, roles of two parties of a transaction can be accurately identified, and the credibility of the transaction can be quickly judged, so that the safety of the transaction is improved.
Owner:JIANGSU PAYEGIS TECH CO LTD
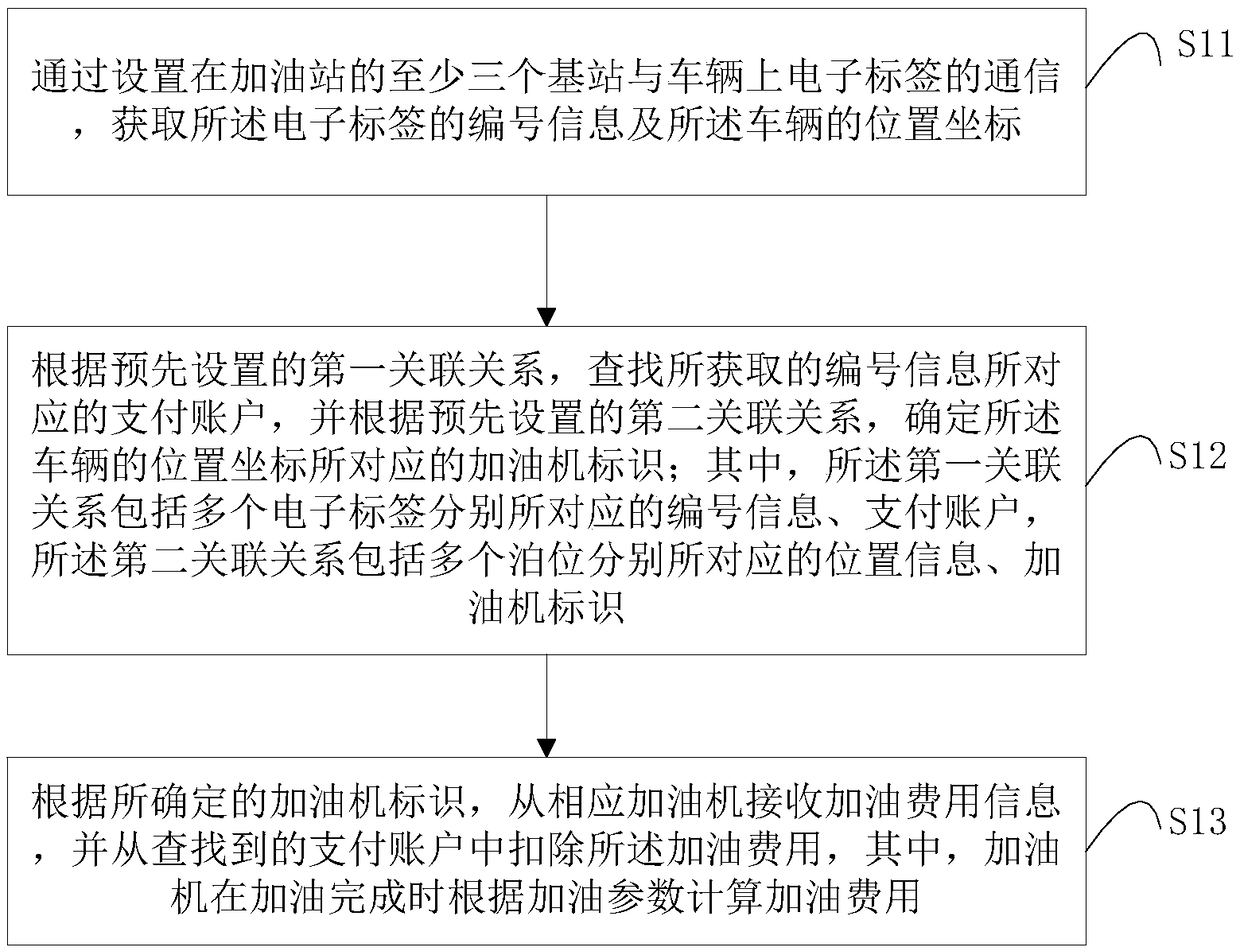
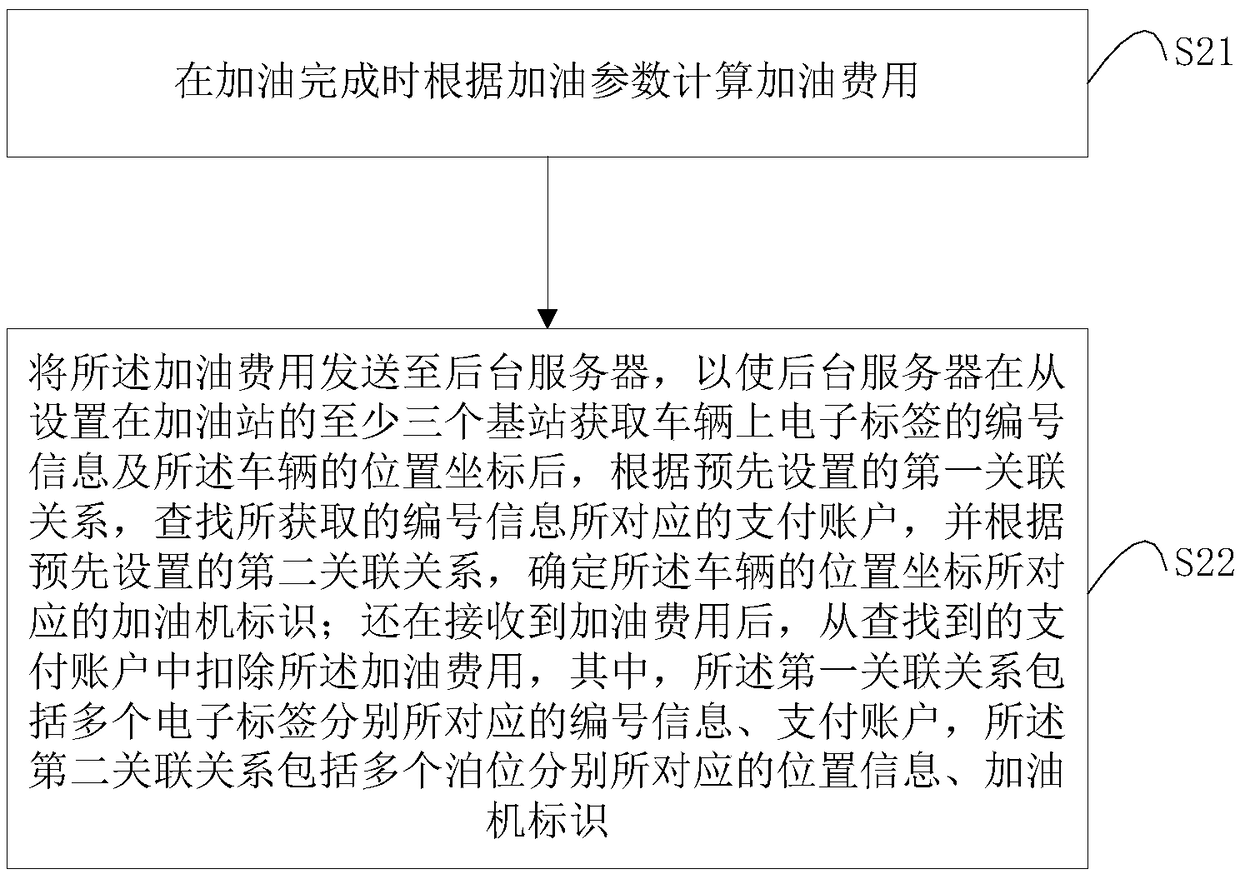
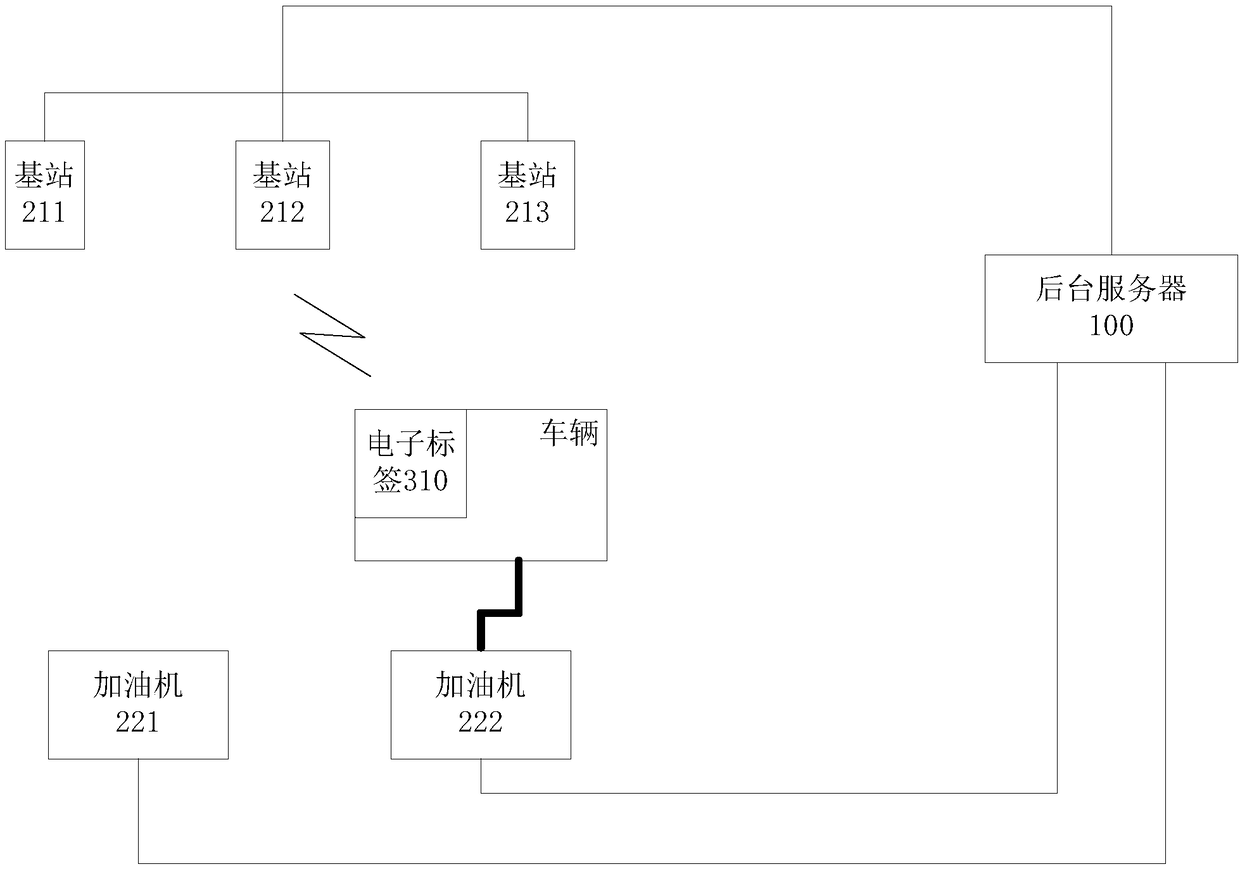
Self-service refueling method and system and refueling machine
InactiveCN108615301AImprove experienceImprove refueling efficiencyPayment architectureApparatus for dispensing fluids/granular materialsPaymentSimulation
The invention relates to a self-service refueling method and system and a refueling machine. The self-service refueling method includes: acquiring serial number of an electronic tag and position coordinates of a vehicle through communication between at least three base stations of a gas station and the electronic tag of the vehicle; according to a preset first association relation, searching a payment account corresponding to the acquired serial number information, and determining identification of a refueling machine corresponding to the position coordinates of the vehicle according to a preset second association relation, wherein the first association relation includes serial number information and payment accounts corresponding to multiple electronic tags, and the second association relation includes position information and refueling machine identifications corresponding to multiple parking positions; according to the determined refueling machine identification, receiving refuelingcost information from the corresponding refueling machine, and deducting the refueling cost from the searched payment account. By implementation of the technical scheme, the whole refueling process is completed without participation of vehicle owners, and great user experience and high refueling efficiency are realized.
Owner:SHENZHEN GENVICT TECH
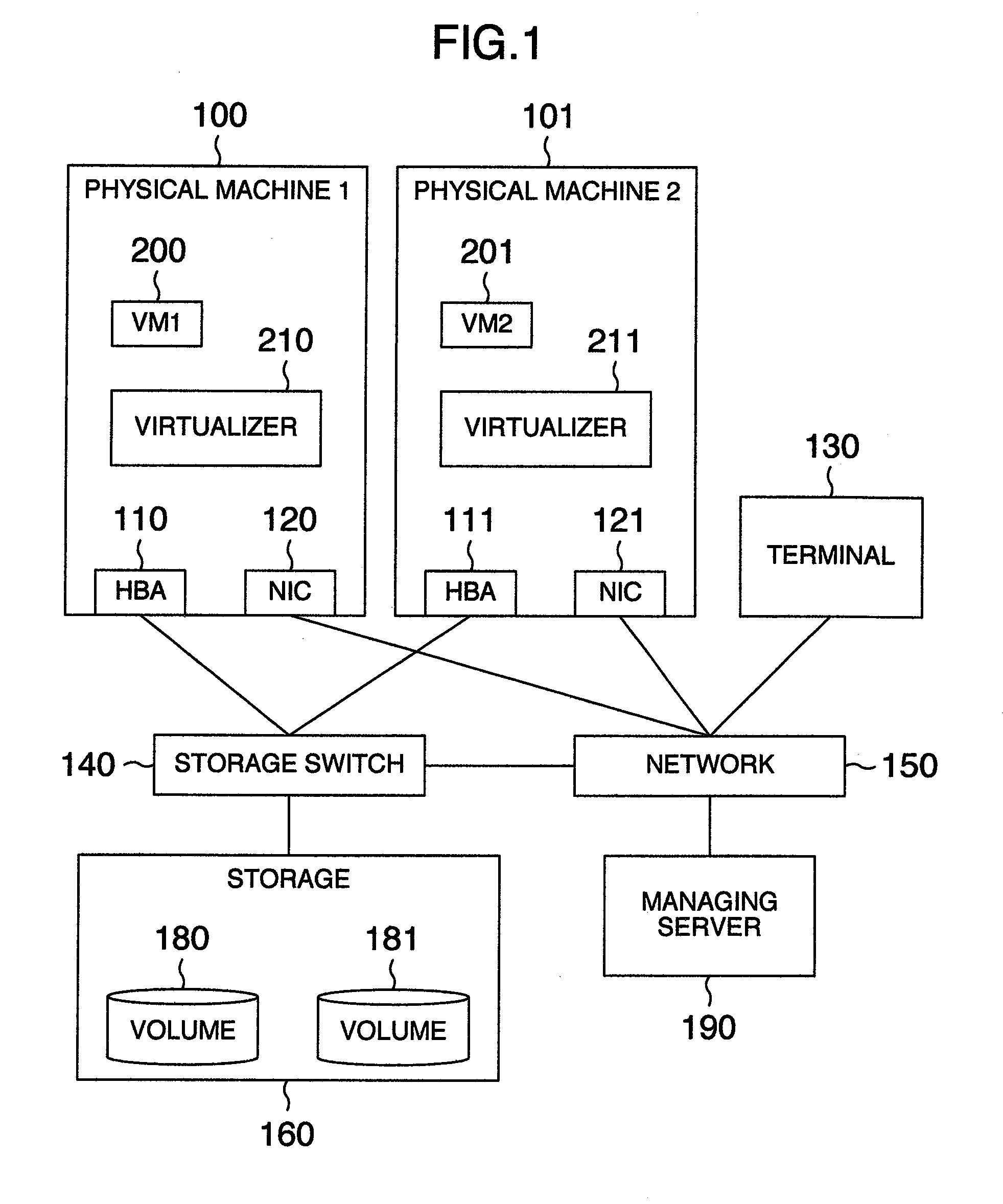
Virtual machine migration managing method, computer using the method, virtualizer using the method and computer system using the method
ActiveUS20120180051A1Without deteriorating securityAppropriate settingSoftware simulation/interpretation/emulationMemory systemsSoftware engineeringRecovery procedure
In a system including a plurality of physical machines to execute virtual machines (VM1, VM2), migration virtual machine information and definition information are saved in a physical machine executing a virtual machine (VM1) to be migrated and a storage of a physical machine as a migration destination. During the migration of the virtual machine, machine identification information of a migration partner, unique information assigned to the virtual machine, and information indicating whether the physical machine executing the processing is a migration-source or migration-destination physical machine are saved in a migration information storage area. A migration recovery section examines information stored in a definition information storage area and a migration information storage area to determine a recovery procedure to restore the virtual machine.
Owner:HITACHI LTD
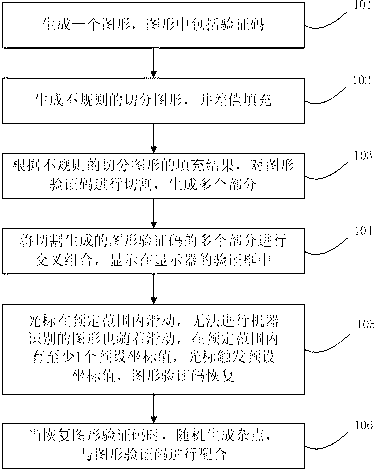
Method for verifying through graphical verification code
ActiveCN102890761AImprove recognition rateRealize the verification functionDigital data authenticationGraphicsTheoretical computer science
The invention discloses a method for verifying through a graphical verification code. The method comprises the following steps of: generating an irregular segmentation graph and performing difference filling; segmenting a graphical verification code according to a filling result of the irregular segmentation graph to generate not less than two parts; performing cross combination on not less than two parts which are generated by segmenting to generate a graph which cannot be subjected to machine identification; sliding a cursor in a predetermined range, wherein the graph which cannot be subjected to the machine identification slides along with the cursor, and not less than one predetermined coordinate value is in a predetermined range; triggering the predetermined coordinate value by the cursor; recovering the graphical verification code; and displaying a clear verification code. By adopting the method for verifying through the graphical verification code, a verification function can be realized, simultaneously user identification rate is improved, and input time cost is reduced.
Owner:BEIJING WENHAI SICHUANG TECH
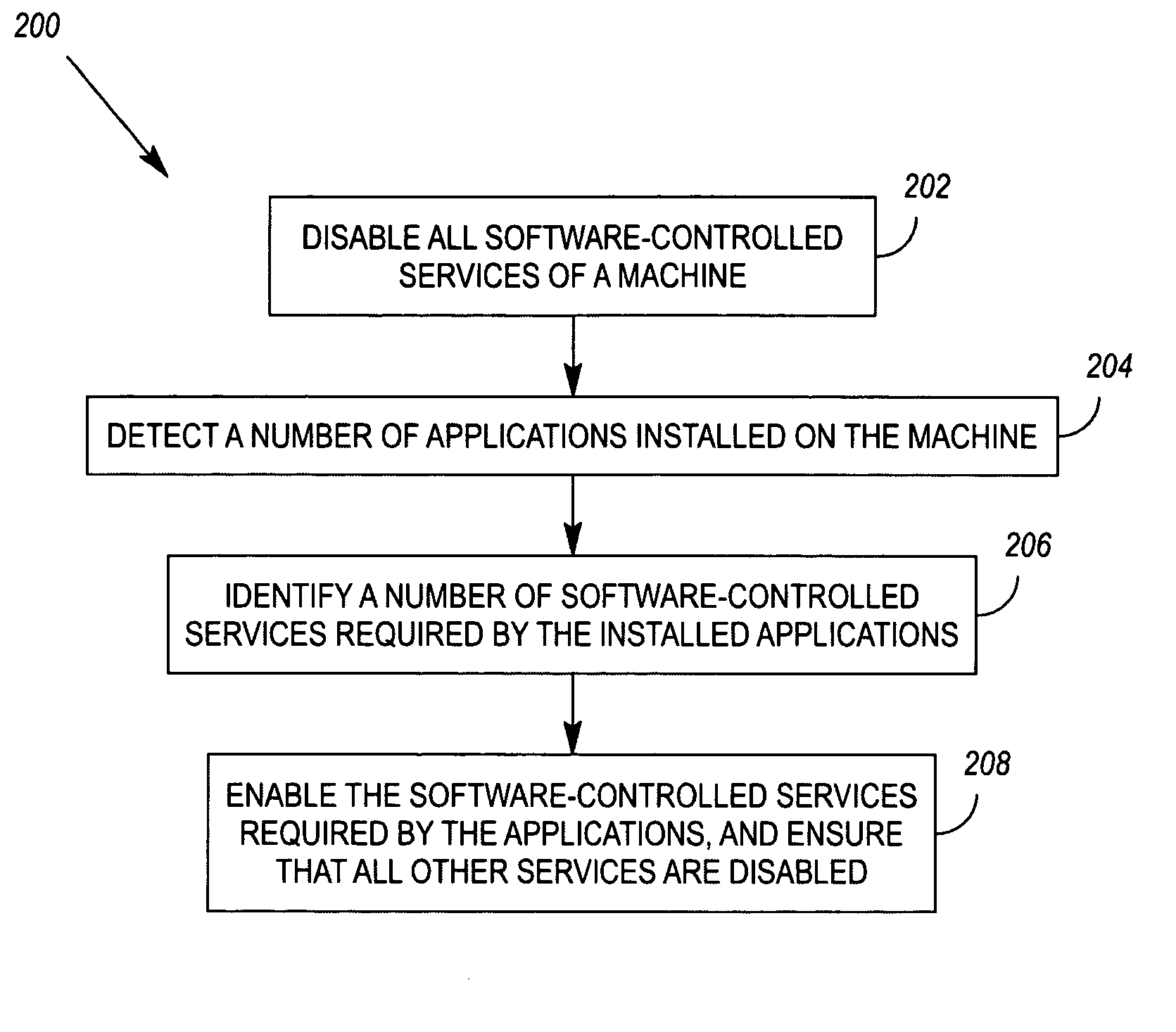
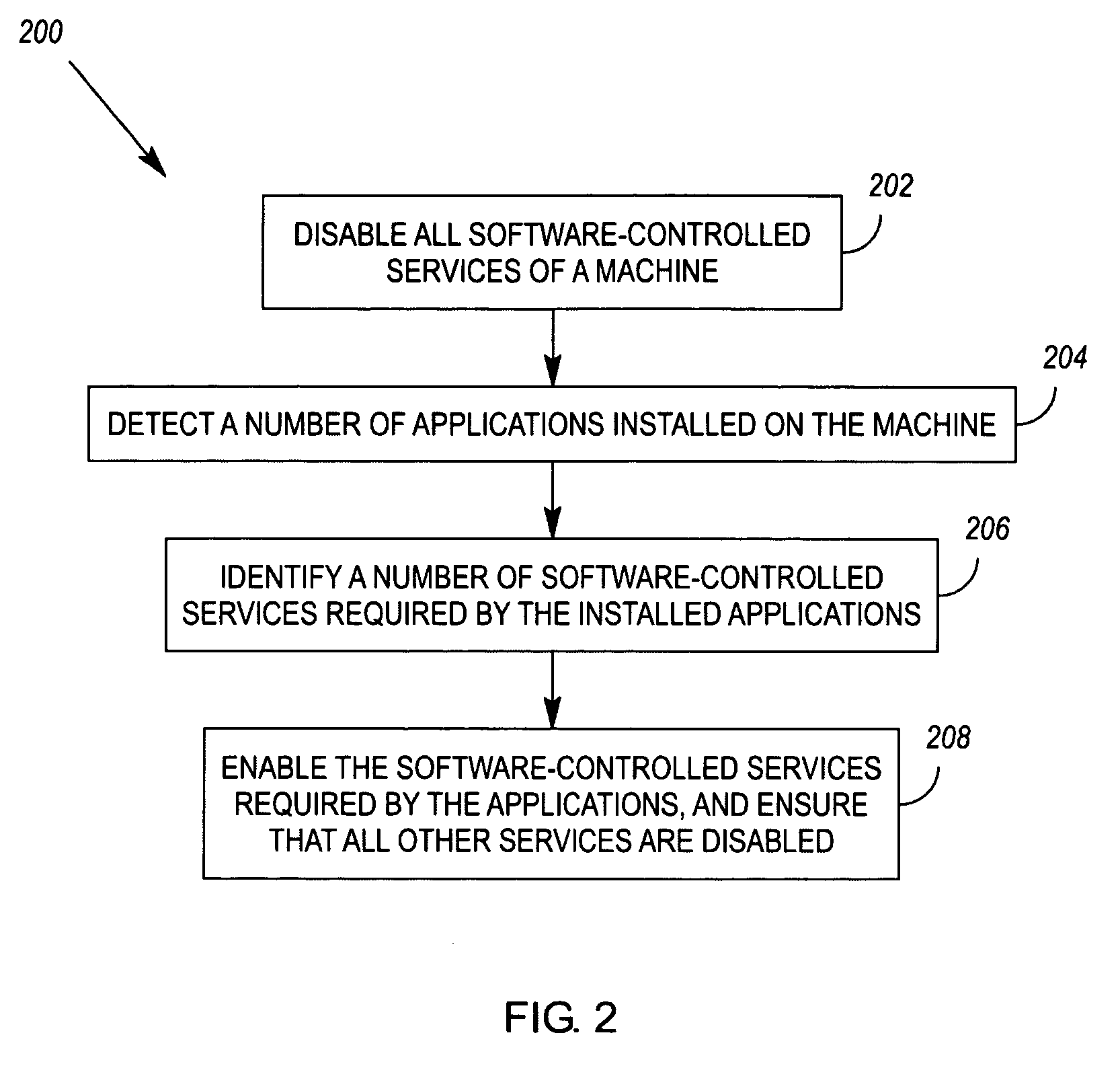
Enablement of software-controlled services required by installed applications
InactiveUS20060069754A1Digital computer detailsPlatform integrity maintainanceSoftware engineeringApplication procedure
Sequences of instructions may be stored on machine-readable media such that, when they are executed by a machine, the instructions cause the machine to 1) identify a number of applications installed on the machine, 2) identify a number of software-controlled services required by the installed applications, and 3) enable the software-controlled services required by the applications and ensure that non-required services are disabled. Related methods and apparatus are also disclosed.
Owner:HEWLETT PACKARD DEV CO LP
Software content use authorization method
ActiveCN110162936AAvoid the problem of cloning and crackingReduce risk of intercept analysisProgram/content distribution protectionUsabilityClient-side
The invention discloses a software content use authorization method. The method comprises the steps that 101, a bit cloud server receives a protection instruction which is triggered by a first user through a software content provider client and is associated with software content; 102, the bit cloud server generates an authorization code for a second user to use the software content based on any device according to the protection instruction; 103, the bit cloud server receives an authentication request sent by a software client in any device; and 104, the bit cloud server carries out authentication processing on the authentication request according to a pre-defined authentication strategy, and if the authentication is qualified, a secure communication channel for data interaction between the software client and the bit cloud server is established. According to the method, the defects of inaccurate machine identification, poor usability, incapability of realizing self-service authorization, low safety intensity, easiness in cloning and copying and the like in the prior art are overcome.
Owner:北京比特安索信息技术有限公司
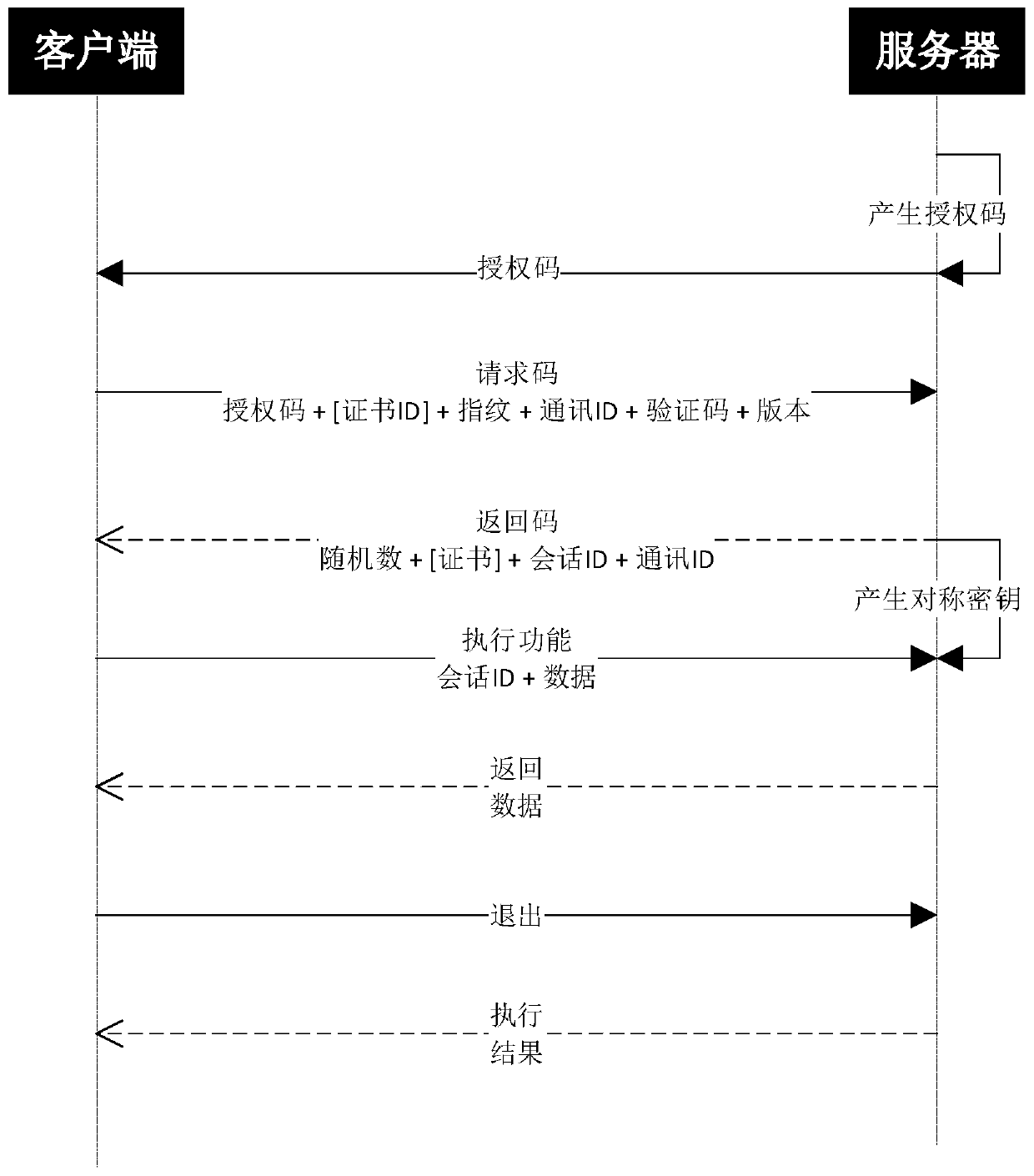
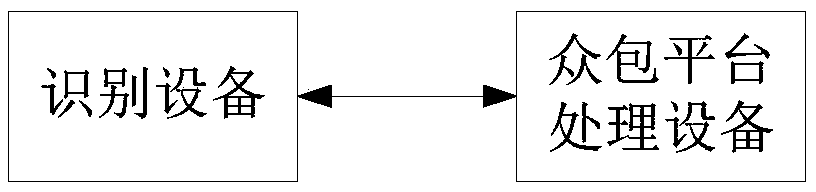
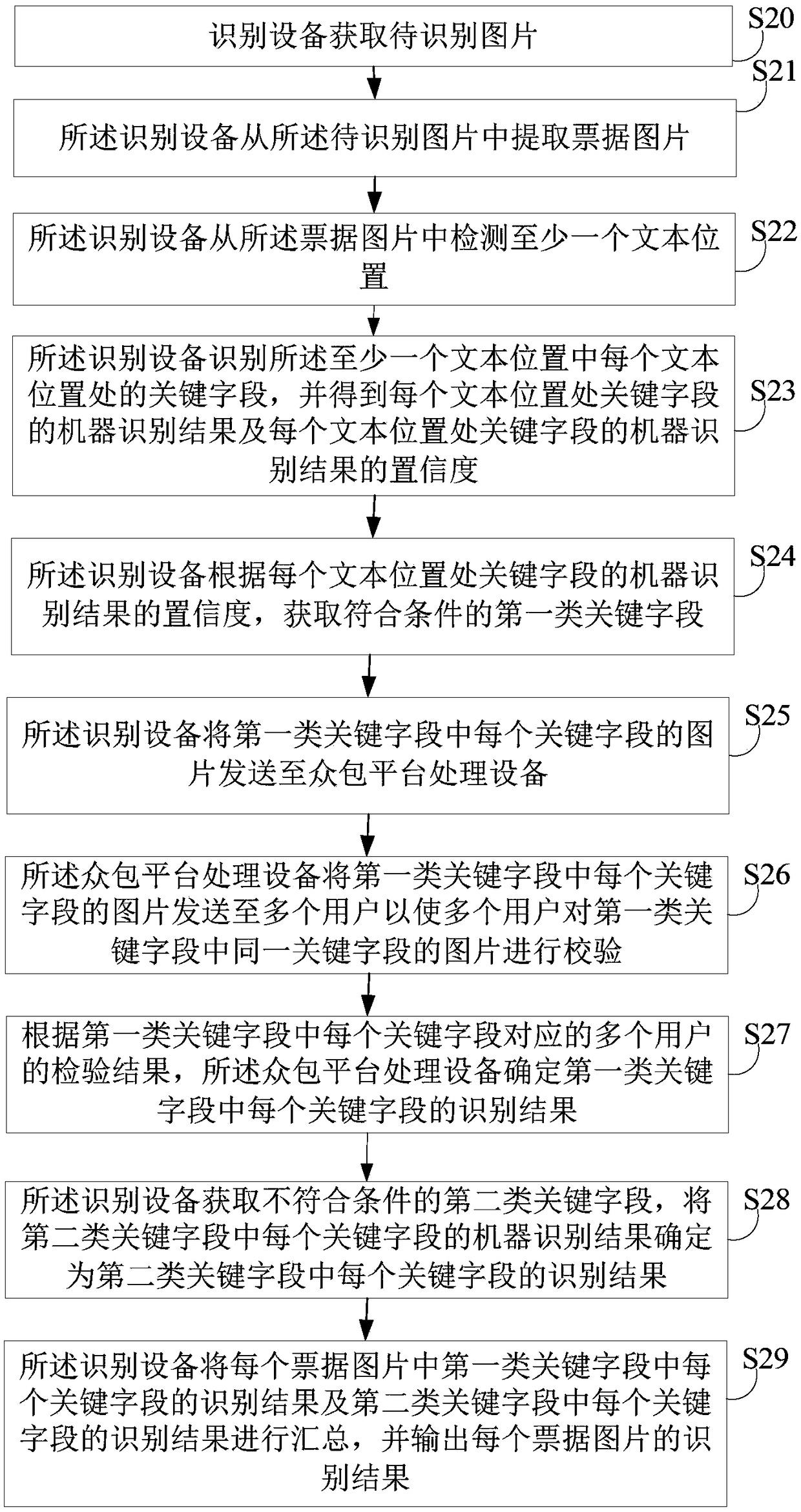
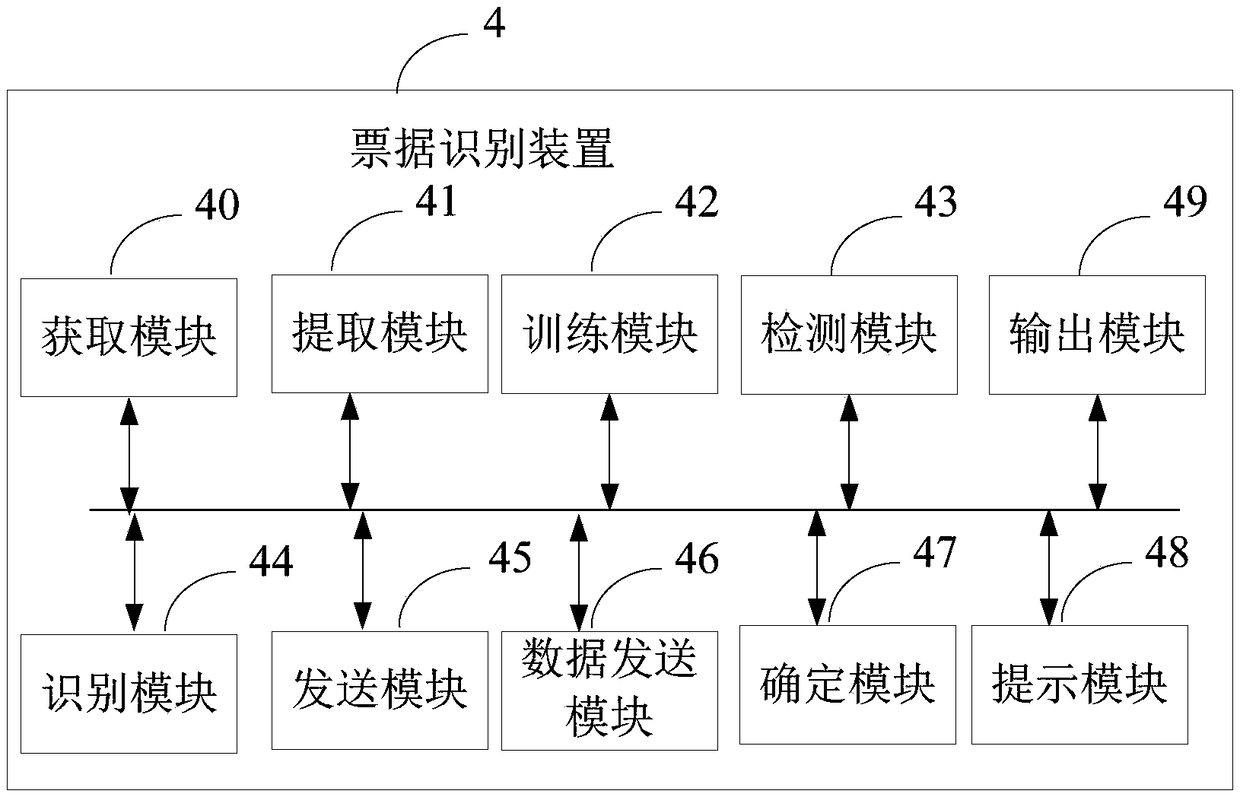
Ticket identification method, apparatus and storage medium
InactiveCN108664897AImprove accuracyQuick fileCharacter recognitionCrowd sourcingRecognition algorithm
The invention provides a ticket identification method comprising the following steps of: firstly detecting and identifying key fields with regard to the inputted ticket picture by using intelligent identification algorithm, then obtaining the confidence of machine identification results of the key fields; sending the key fields of which the confidence is lower than the threshold value to a crowd sourcing platform to verify; sending a same key field to a plurality of users to verify by the crowd sourcing platform, and obtaining verification results from a plurality of users for the same key field; and finally outputting the identification results of the ticket picture. The invention further provides a ticket identification apparatus and a storage medium. According to the ticket identification method, apparatus and storage medium, accuracy of ticket identification can be improved, so that a file can be quickly constructed.
Owner:PING AN TECH (SHENZHEN) CO LTD
Indoor common object identification method based on machine vision
InactiveCN102708380AMitigate the impact of object recognitionCharacter and pattern recognitionMachine visionMulti dimensional
The invention discloses an indoor common object identification method based on machine vision. The method comprises the following step of: (1) establishing a visual word bank of a kind of objects, and clustering the scale of the determiner bank through an mean value K; (2) preliminarily processing images, expressing an image with the words in the word bank, and approximately distinguishing a background and a foreground with similar threshold values; (3) describing the images, wherein the information contained in one image is mapped into a multi-dimensional column vector (x0,x1x2......xP-3xP-2xP-1y0y1y2......yQ-3yQ-2yQ-1) of 1*(P+Q), and the characteristics and the space relation in the images are vectorized, P is the emerging times of the word in the visual word bank, and Q is the statistics of the space relation; and (4) supporting a vector machine with a no-supervision identification classifier so as to realize the classified identification. With the adoption of the indoor common object identification method, the machine can identify the object more accurately.
Owner:SOUTHEAST UNIV
Location-centric project data delivery system for construction
ActiveUS20060174239A1Automatic deliveryResourcesSpecific program execution arrangementsProgram planningData file
A project data delivery apparatus for automatically delivering project data files to a construction machine based on the geographical location and identification of the construction machine. The apparatus includes a project data distributor for storing, maintaining and transmitting project data files that are associated with project site locations and project plan machine identifications.
Owner:CATERPILLAR TRIMBLE CONTROL TECH
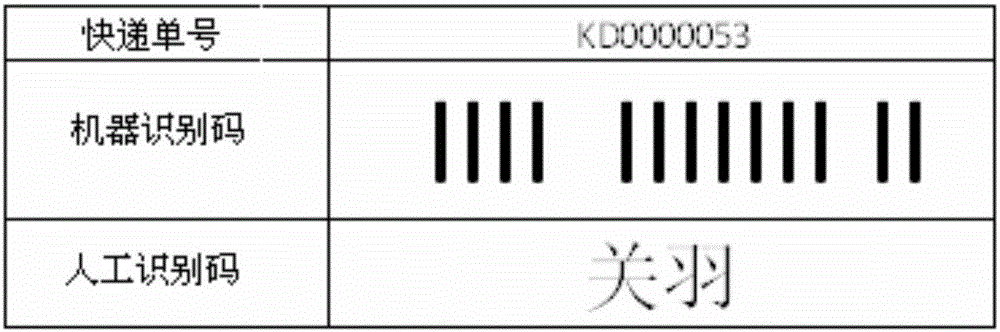
Logistics processing method capable of protecting privacy by information decomposition
A logistics processing method capable of protecting privacy by information decomposition is mainly characterized in that only machine identification codes, manual identification codes and courier numbers are contained in articles and article labels, no privacy information of users are contained, all the information including users' names, contact details and address information are stored in cloud, articles and all information are associated with each other through the courier numbers, and only necessary information fragments are sent to dispatchers or transfer equipment through a network during a logistics process without displaying all information. The information fragments may be transfer places, or destinations, which are not private information. In this way, user privacy can be protected without affecting express delivery. Information flow is transmitted through data, which eliminating manual writing, printing and identification. The express delivery efficiency is thus improved.
Owner:宋同晶
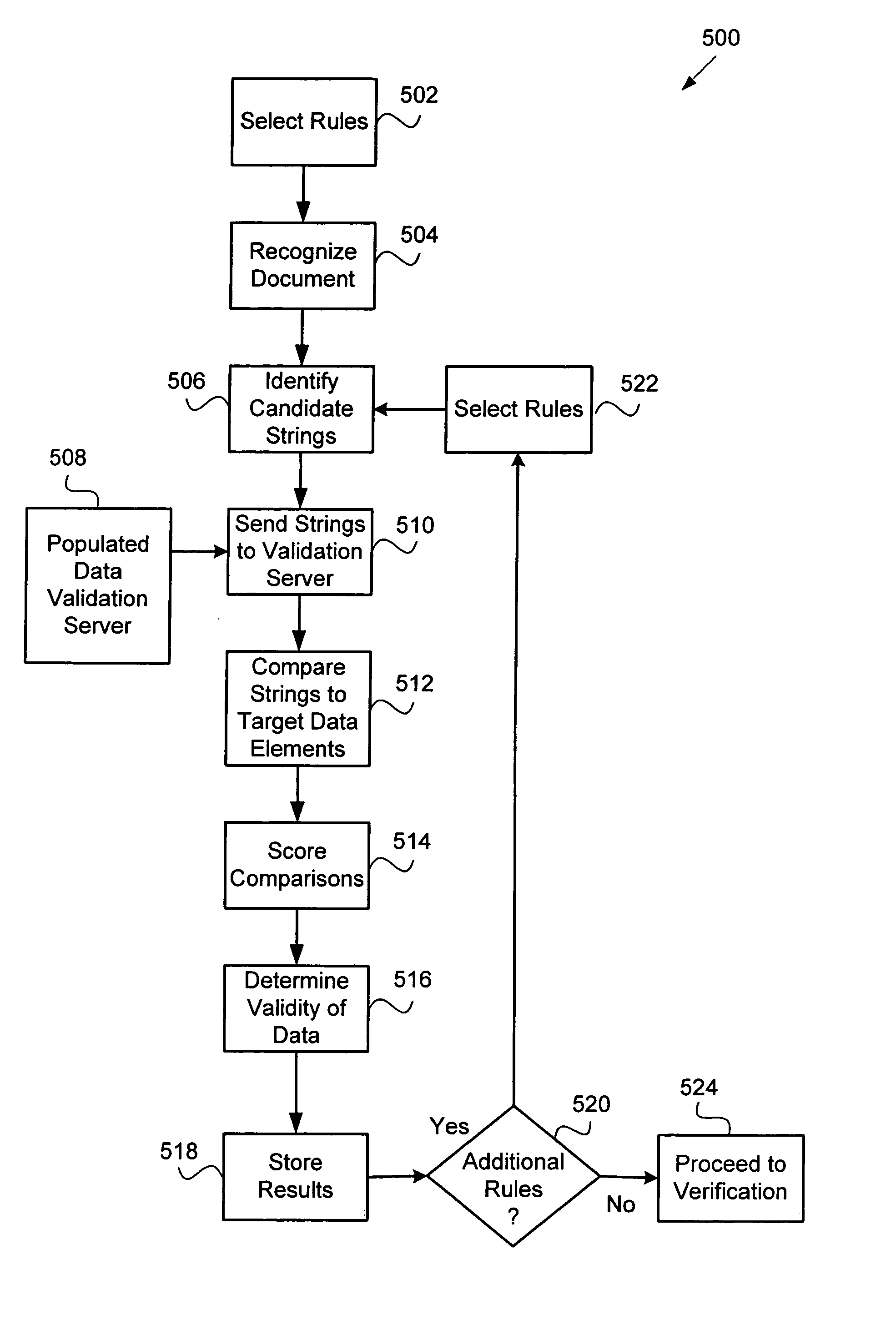
Property record document data verification systems and methods
InactiveUS20070217692A1Database updatingCharacter and pattern recognitionData validationImage server
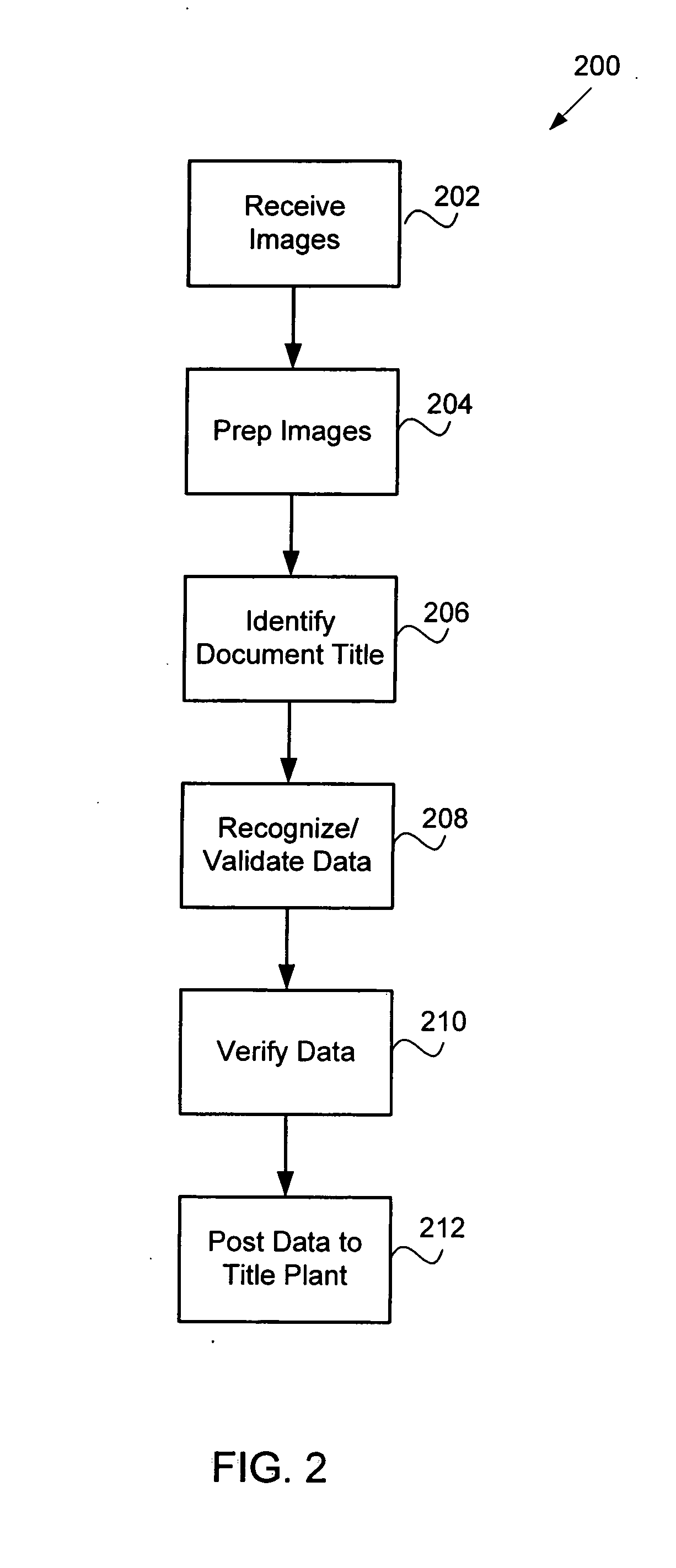
A data verification system is configured to verify machine-recognized data elements acquired during a machine-implemented data acquisition process. The system includes a data verification workstation, a image server, and a data entry server. The data verification workstation is configured to obtain document images from the image server, present portions of document images to an operator, wherein the document images include text, and receive input from the operator based on the text. The input includes data elements. The data verification workstation is also configured to acquire machine-recognized data elements from the data entry server. The machine-recognized data elements were acquired from the document image during a machine-implemented data acquisition process based on the text. The data verification workstation is also configured to compare the data elements received from the operator to the machine-recognized data elements and selectively prompt the operator to re-input the data elements based on the comparison.
Owner:DATA TRACE INFORMATION SERVICES
Remote server
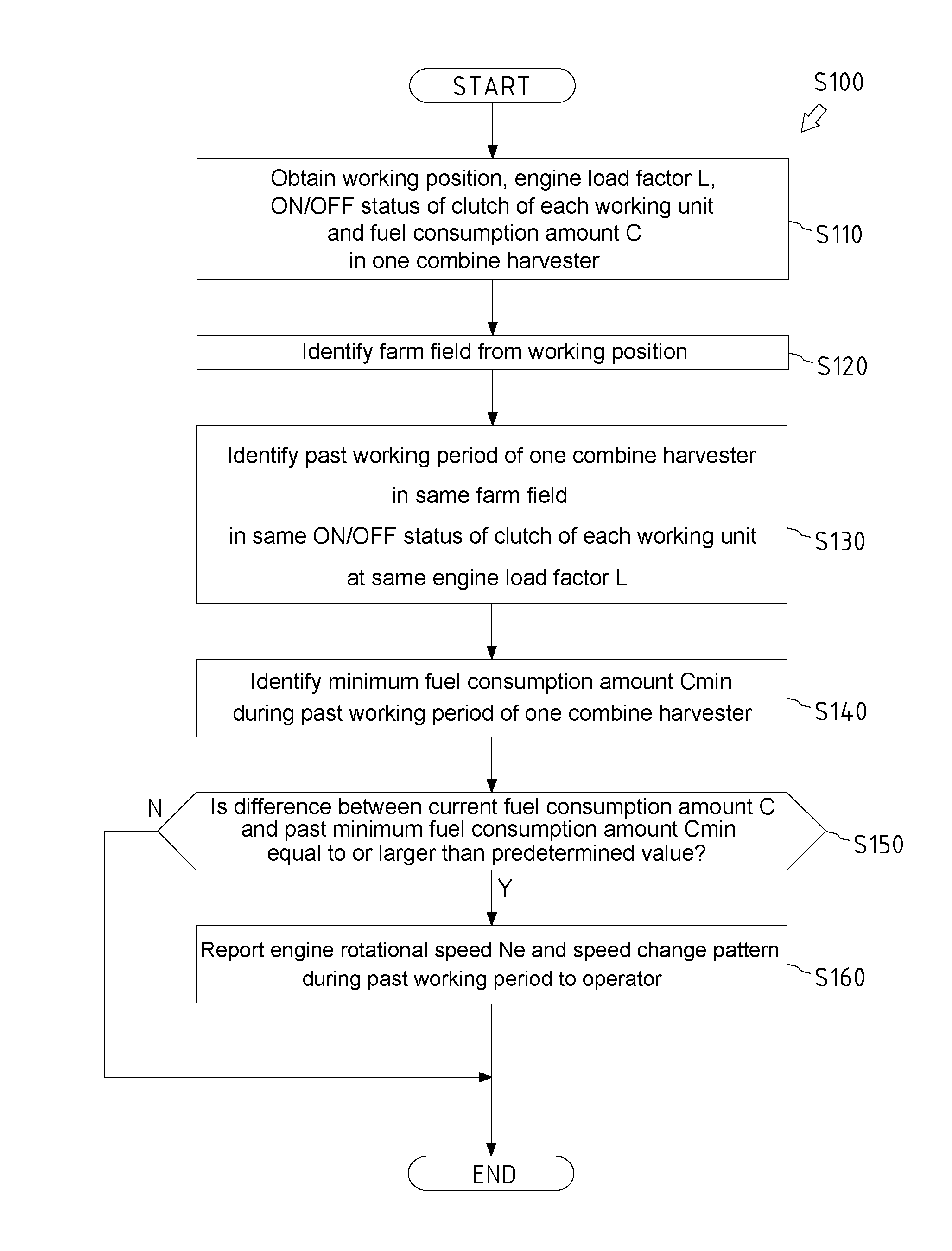
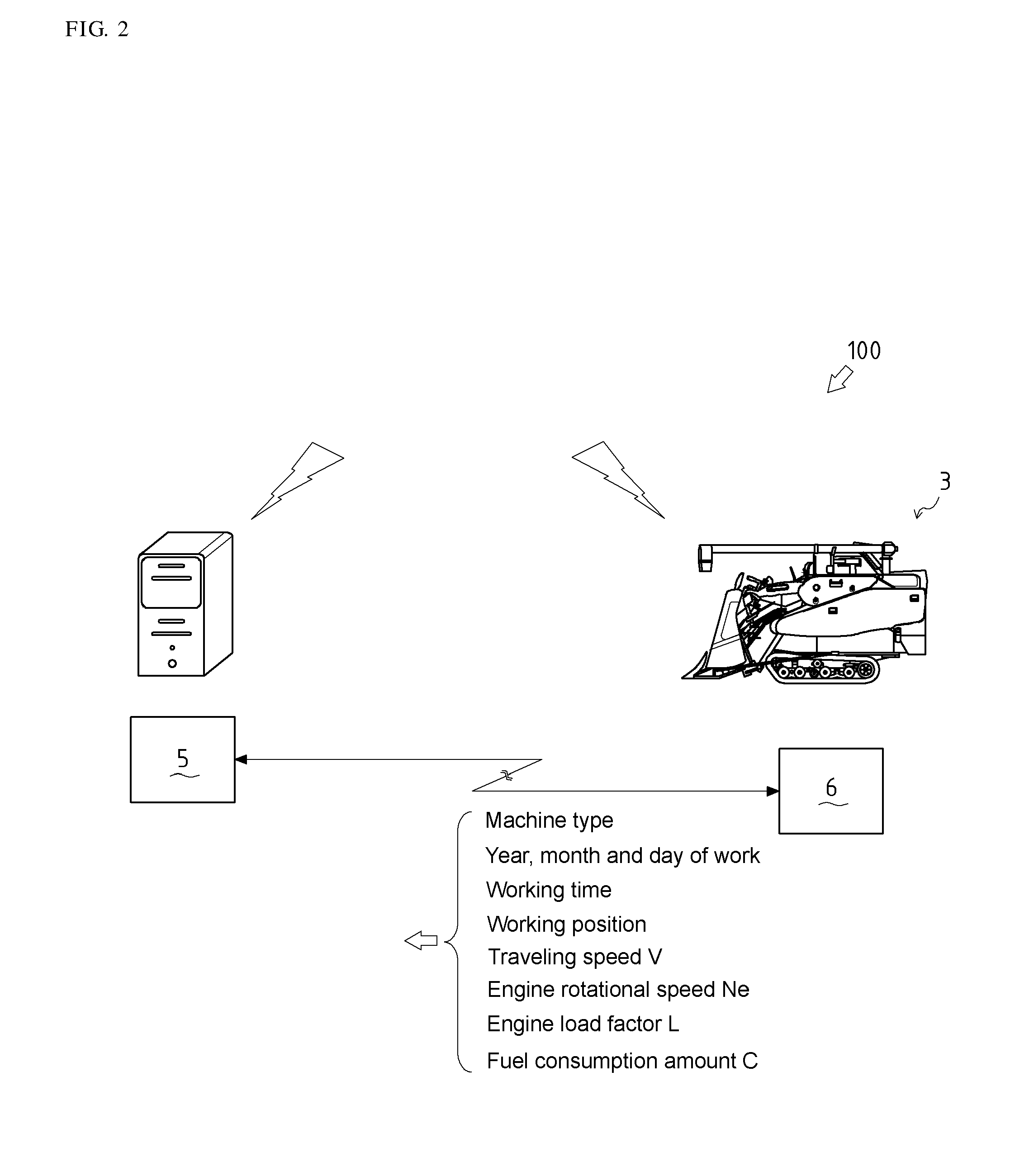
There is provided a remote server that receives a machine type, an operating day, a position, a load factor, an engine rotational speed, a traveling speed, and a fuel consumption amount. The remote server identifies a working position based on the position, selects past operating days of an operation status corresponding to a current load factor of the same machine at the same working position, identifies a minimum fuel consumption amount out of fuel consumption amounts corresponding to the selected past operating days, and compares a current fuel consumption amount with the past minimum fuel consumption amount. If the current fuel consumption amount is larger than the past minimum fuel consumption amount, the remote server transmits an engine rotational speed and a traveling speed during a working period of the minimum fuel consumption amount, to a predetermined communication terminal corresponding to information for machine identification.
Owner:YANMAR POWER TECHNOLOGY CO LTD
Wheel hub mounting hole flexible and automatic machining system based on machine vision
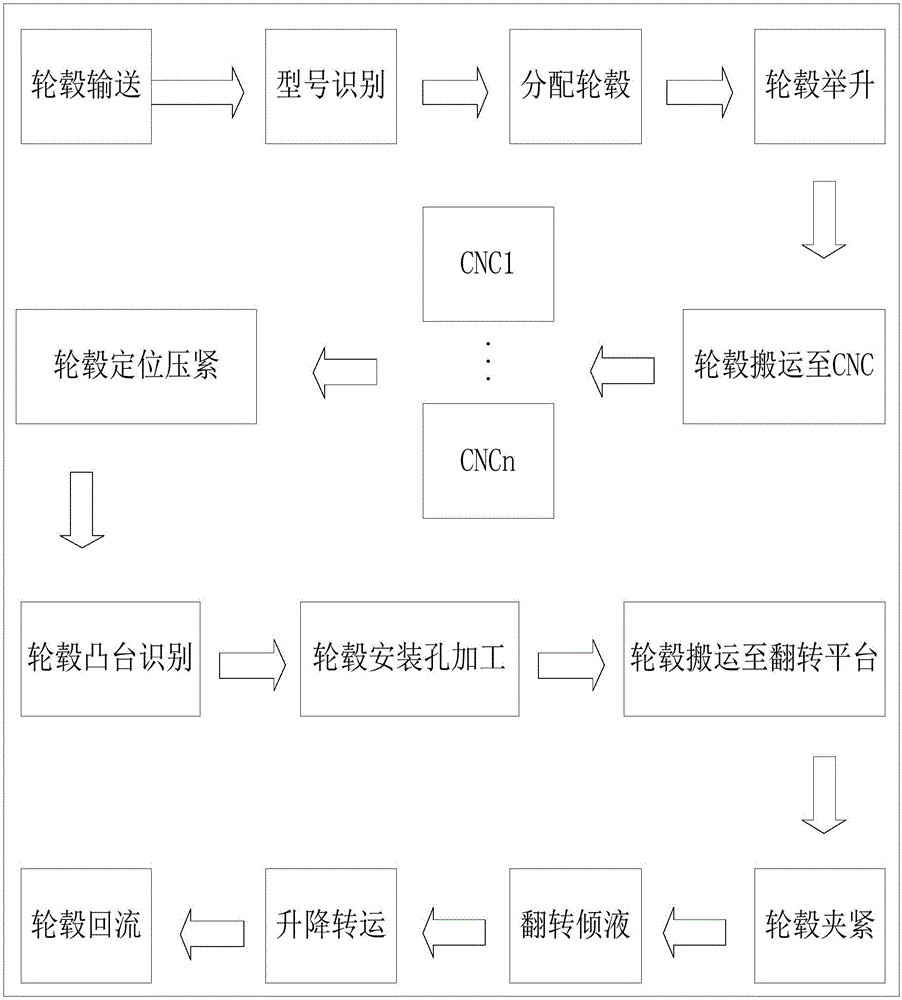
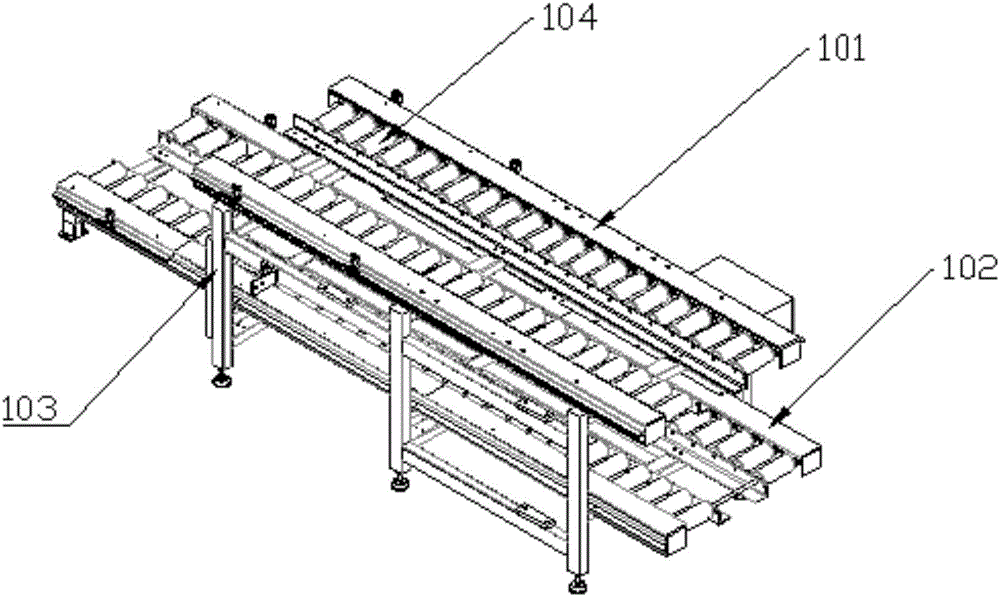
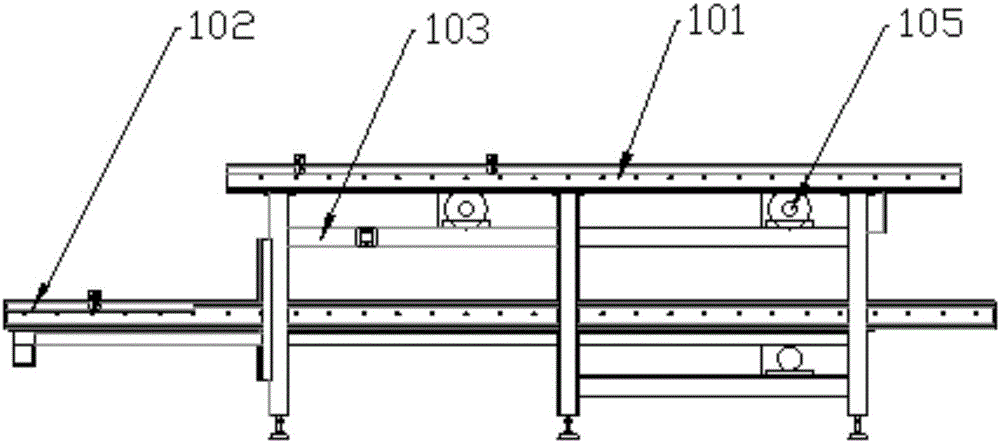
The invention discloses a wheel hub mounting hole flexible and automatic machining system based on machine vision, comprising a conveying system, an automatic feeding and discharging system, a machining system, a positioning system, a vision system, a poured liquid return system, and a computer control system. A model identification system is used to identify a to-be-machined wheel hub on a feeding layer and compare the model of the to-be-machined wheel hub with models pre-stored in a computer system, the corresponding machining system is allocated for the to-be-machined wheel hub according to the comparison result, the to-be-machined wheel hub is transferred to the allocated machining system by the automatic feeding and discharging system, and the to-be-machined wheel hub is clamped and positioned by the positioning system; then, a machining identification system shoots a static image of the wheel hub through an industrial camera and a light source and analyzes and processes the image, and the circumferential coordinate location of the boss of the wheel hub is calculated to provide a machining location coordinate for a CNC numerical control machine tool to machine the wheel hub; and finally, cuttings and cutting fluid on the surface of the machined wheel hub are cleaned by the poured liquid return system, and the wheel hub is conveyed to a specified location through a return layer.
Owner:中科图灵视控(北京)智能科技有限公司
Wafer expander with high expansion uniformity
InactiveCN104008986AReduce occupancyMeet packaging requirementsSemiconductor/solid-state device manufacturingEngineeringSemiconductor
The invention provides a wafer expander used in the semiconductor industry and the LED industry. A cross blue film is expanded in the direction of two mutually perpendicular chip cutting ways so that the cut wafers stuck to the cross blue film are evenly expanded and chips can be separated. The distances between the adjacent chips are the same, the subsequent measurement and sorting processes occupy less machine identification and positioning time, the requirements of chip-level packaging or wafer-level packaging are met, and the subsequent processes are facilitated.
Owner:FOSHAN CITY NANHAI DISTRICT LIANHE GUANGODNG XINGUANGYUAN IND INNOVATION CENT +1
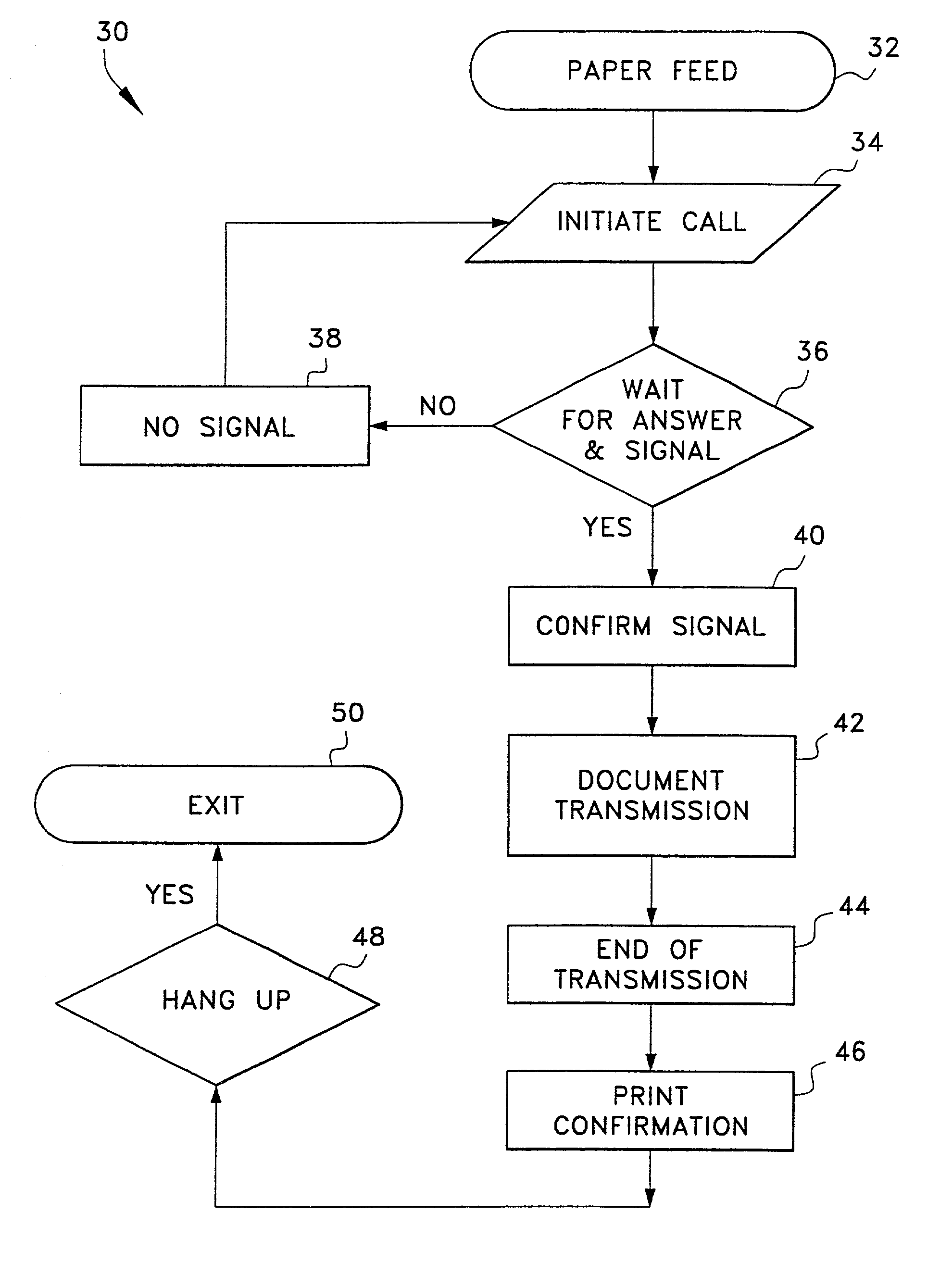
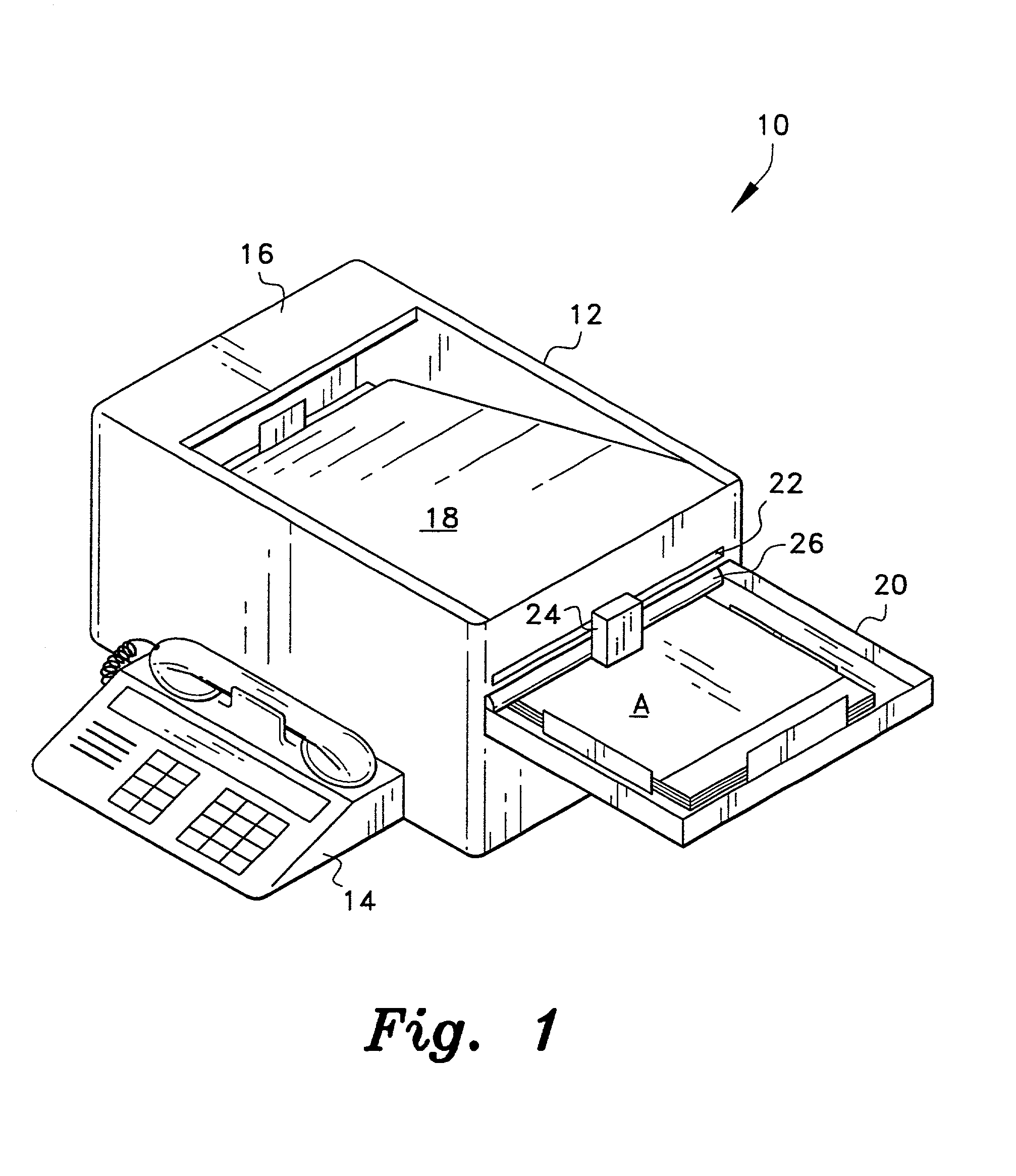
Fax confirmation device
A method and apparatus for placing an indelible mark on each page of a document which has been sent by FAX. The sender's FAX machine applies a clear / transparent chemical or ink message on the surface of the document which contains information such as the FAX machine identification number, telephone number of the FAX recipient, and the time and date of the FAX transmission. The information is printed and is invisible to the naked eye, but becomes visible underneath a low voltage UV light. The light is placed above the tray in which completed faxes are temporarily stored to make the mark visible to the operator to assure that each page of the document was separately sent. A separate pen light allows a sender or management person to confirm that a document has been properly and completely transmitted. Visible ink may be used if desired.
Owner:BURKE JAMES
Vending System
InactiveUS20090259590A1Complete banking machinesCredit registering devices actuationNetwork connectionWireless data
A vending system server for a vending system for selling products or services, from at least one vending machine connected to a network, to purchasers having mobile communicators configured to communicate with the network by wireless data packet network connection, comprises an operator server, connected to the network by an operator network connection, wherein the operator server is configured to (1) receive via the operator network connection a communication from a mobile communicator of identifying data of a vending machine at which the mobile communicator is located, without receiving personal identification information from the mobile communicator, (2) transmit, via the operator network connection to the mobile communicator, vending machine identification information, (3) receive, via the operator network connection, authorization information from an external authorization center, and (4) authorize the vending machine to supply a good or service in response to the authorization information.
Owner:INTELLECTUAL VENTURES FUND 83 LLC +1
Holographic video monitoring system and method for directional picture capture based on sound classification algorithm
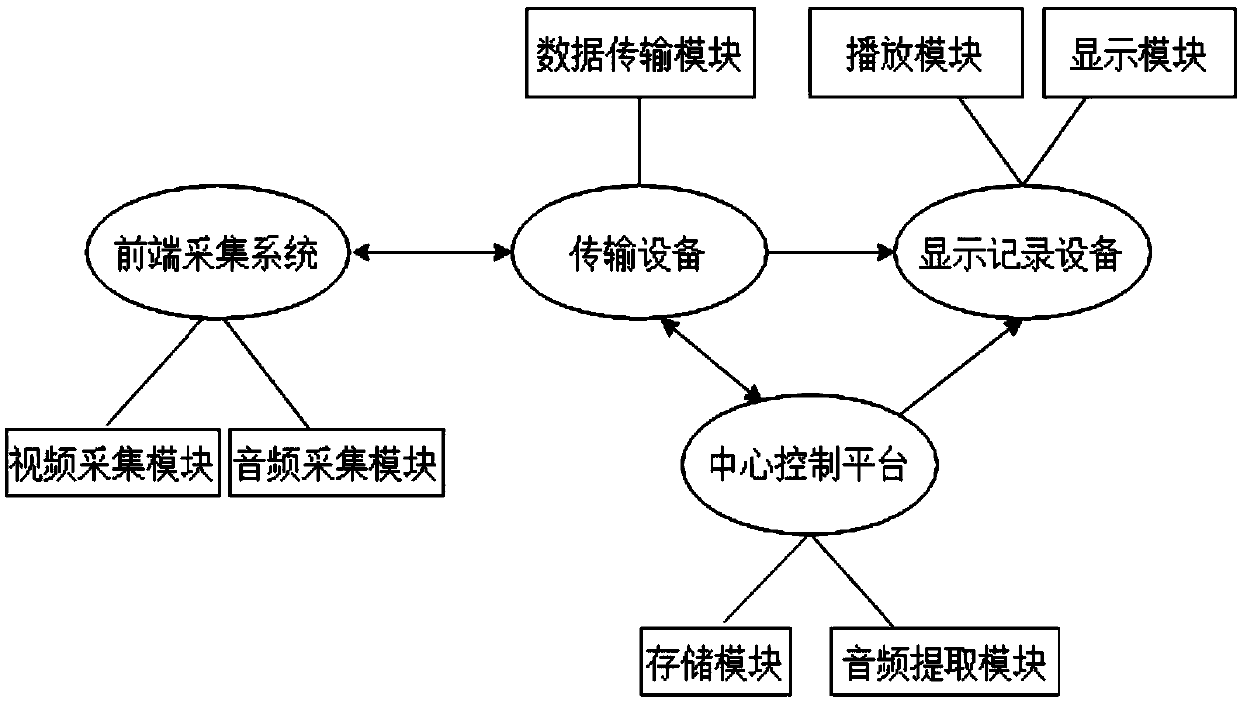
InactiveCN109547695AAvoid the lack of intelligent image captureRealize holographic video surveillance systemTelevision system detailsColor television detailsMel-frequency cepstrumSupport vector machine
The invention provides a holographic video monitoring system and method for directional picture capture based on a sound classification algorithm. The system comprises a front end collection system, atransmission device, a central control platform and a display recording device; the front end collection system is configured to collect onsite audio data and video data and transmit the sane to thecentral control platform through the transmission device; the central control platform is configured to perform noise reduction processing and sound classification on the audio data through a supportvector machine identification algorithm of the Mel frequency cepstrum coefficient, perform segmentation extraction on the audio data required by the user, send the audio data required by the user andthe corresponding video data to the display recording device, and directionally capture and amplify a corresponding video picture by selecting the specific sound; and the display recording device is configured to synchronously play the monitoring data of the monitoring system in real time, call the monitoring data of any time period in real time, and play the corresponding video picture corresponding to the capture and amplification of the specific sound.
Owner:SHANDONG JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com