Logistics processing method capable of protecting privacy by information decomposition
A processing method and logistics technology, applied in the field of logistics, can solve problems such as easy leakage of user information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
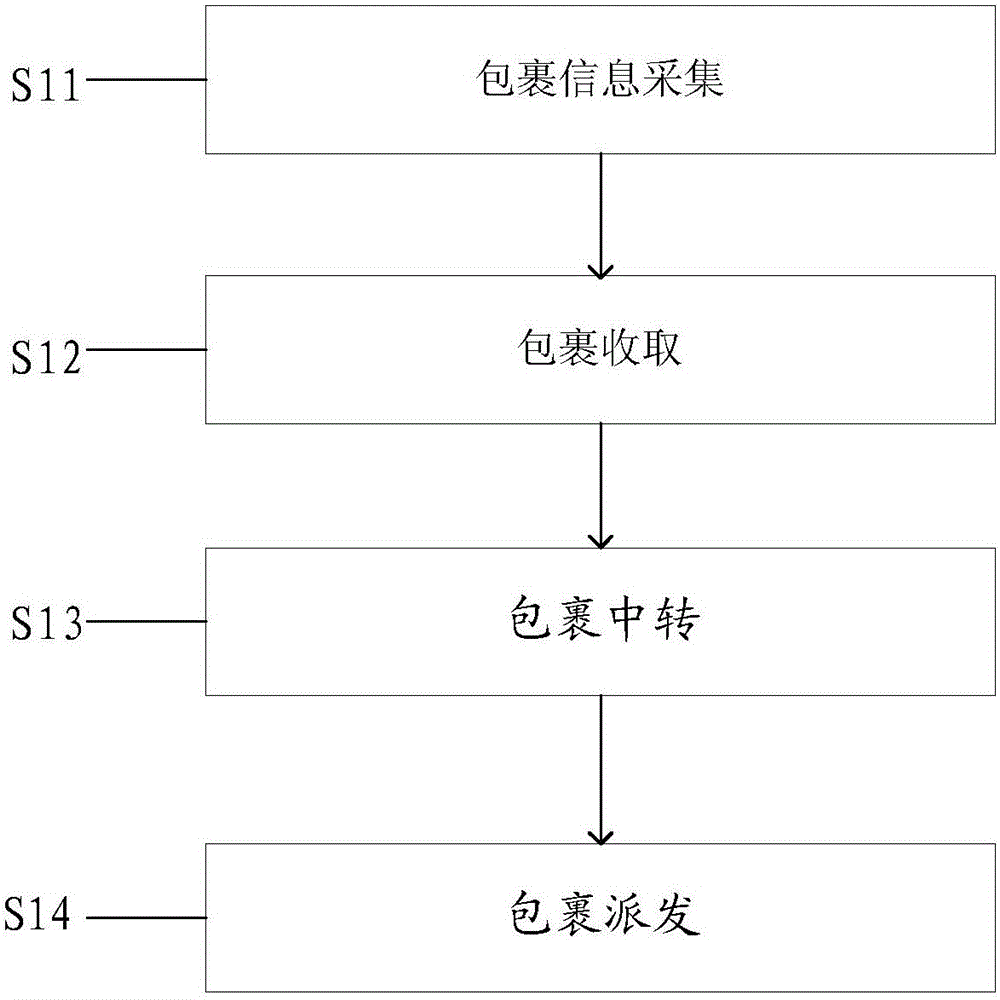
[0018] This example provides a logistics processing method that protects privacy through information decomposition. The flow chart is as follows figure 1 shown.
[0019] S11: Package information collection.
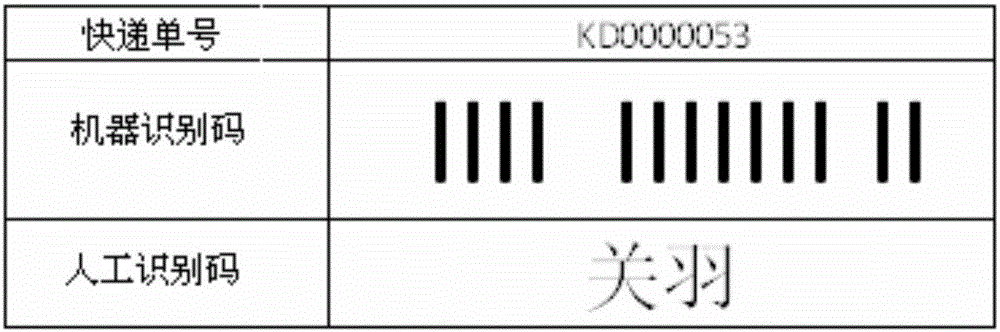
[0020] The specific process of parcel information collection is: the cloud server acquires and stores parcel user information and parcel logistics transit information, among which, parcel user information includes sender information and recipient information, and parcel user information can be called user privacy information; parcel logistics Transit information is information that does not involve user privacy in the process of logistics transfer. For example, it can be information such as the current transfer location, the next transfer location, and the status of the package. The package logistics transfer information is mainly used for the transfer of packages. Through step S11, both the user privacy information and the parcel transfer information about the parcel in...
Embodiment 2
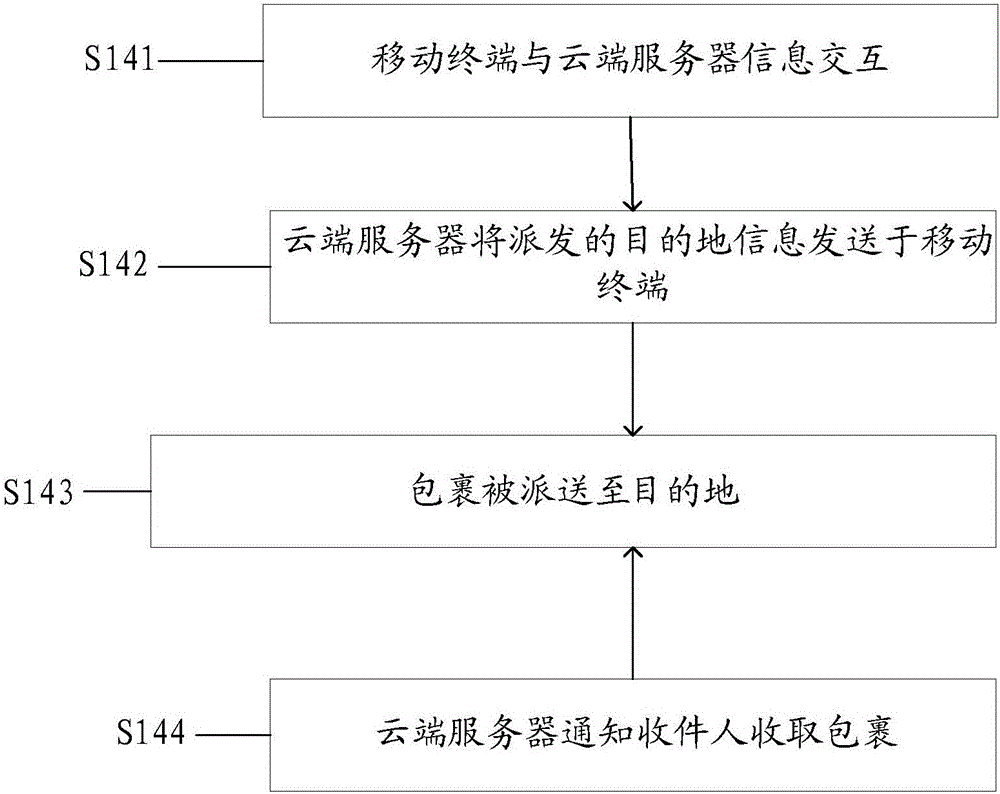
[0059] Based on the first embodiment, the solution for collecting package user information in step S11, this example adopts the first method of embodiment one to collect package user information, specifically including the following steps, the flow chart of which is as follows Figure 4 shown.
[0060] S21: The mobile terminal collects sender and sender information.
[0061] Specifically, the sender uses the mobile terminal to scan the barcode of the courier receipt, and connects to the cloud server through the link of the barcode. Then, the sender enters the mailing and recipient information on the mobile terminal, and completes payment and other operations. The meanings of the sender information and receiver information are similar to those of the sender information and receiver information in Embodiment 1, and will not be repeated here.
[0062] Specifically, the sender can directly enter the recipient's name, address, phone number, sender's name, address, phone number, in...
Embodiment 3
[0080] Based on Embodiment 1 and Embodiment 2, this example adopts the third method of Embodiment 1 to collect package user information, which specifically includes the following steps, and its flow chart is as follows Image 6 shown.
[0081] S41: The server obtains the sender's information and the recipient's phone number.
[0082] In this step, the sender uses the mobile terminal to choose to send a courier based on an interactive platform. The interactive platform is preferably WeChat. When the sender chooses to send a courier through a WeChat public account, the sender will obtain a courier service box, which includes The sender service box and the receiver service box, if the sender has registered an account before, the sender will enter the registered account into the sender service box through the mobile terminal, and the sender service box will automatically obtain the sender information, otherwise, the sender needs to enter the sender’s information in the sender’s i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com