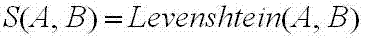Fake user detection method based on hierarchical clustering.
A detection method and hierarchical clustering technology, applied in the field of data security, can solve problems such as not being able to resist attacks well, and achieve the effect of small dependence on data characteristics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The present invention will be further described below in conjunction with accompanying drawing:
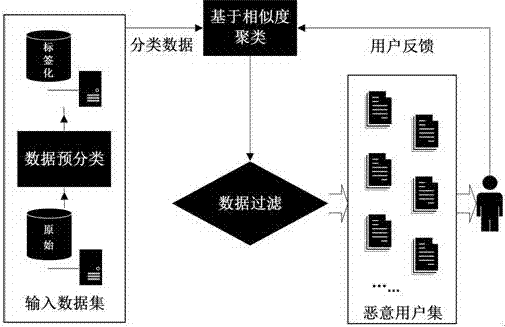
[0014] figure 1 In , a method of false user detection based on hierarchical clustering, including the following steps:
[0015] (1) Back up the user data table, obtain the data set from the data table, and then determine which columns can be used as user unique identification fields;
[0016] (2) Map the user's unique identification field into a string pattern and store it in another data table to ensure data integrity, and at the same time pre-classify massive data according to different string composition patterns;
[0017] (3) For each classification, use each element in the classification as a set, calculate the similarity between data sets based on string similarity, and merge the two sets with the highest similarity;
[0018] (4) Repeatedly calculate the similarity between new sets, and merge the sets with the highest similarity. Until the minimum similarity reache...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com