A resource access method and terminal
A resource access and resource technology, applied in digital transmission systems, data exchange networks, electrical components, etc., can solve problems such as high concurrency and inability to respond in real time, to ensure consistency, ensure fast update and timely response, and timely response Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
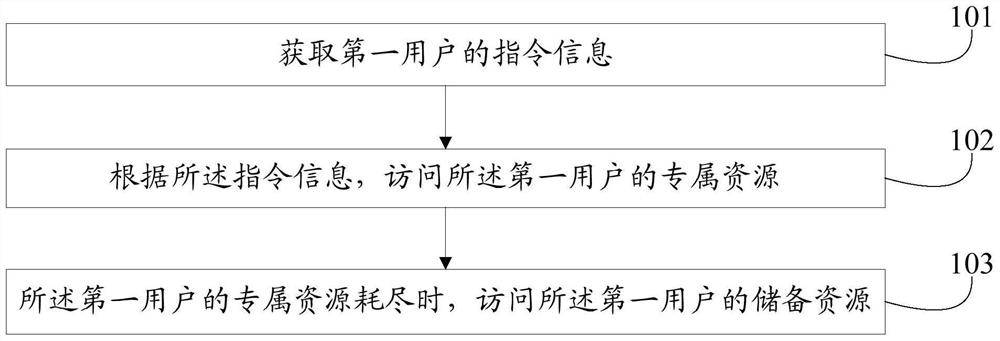
[0049] Embodiments of the present invention provide a resource access method, which is applied to the resource access terminal, which includes mobile phone, laptop, tablet, even in-vehicle computer, such as figure 1 As shown, the method includes:
[0050] Step 101, acquire instruction information of the first user;
[0051] Here, the first user first sends its own instruction information to the terminal, which includes the first user wants to access the resource type and quantity. The first user will inform the corresponding terminal by this command information.
[0052] Step 102, in accordance with the command information, access the exclusive resource of the first user.
[0053] Among them, each user has a corresponding exclusive resource. In actual use, resources are often used as public access objects, which can be accessed by multiple users or even multiple groups. Here, the group is composed of multiple users.
[0054]In this embodiment, it is considered that resources can b...
Embodiment 2
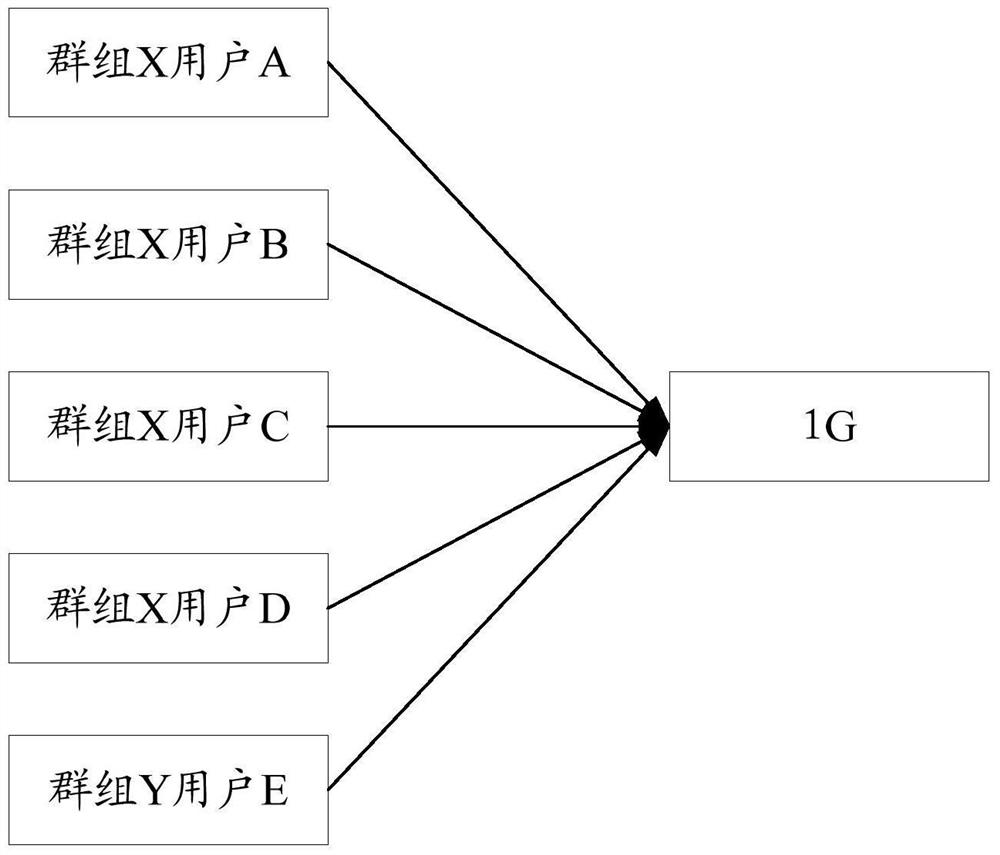
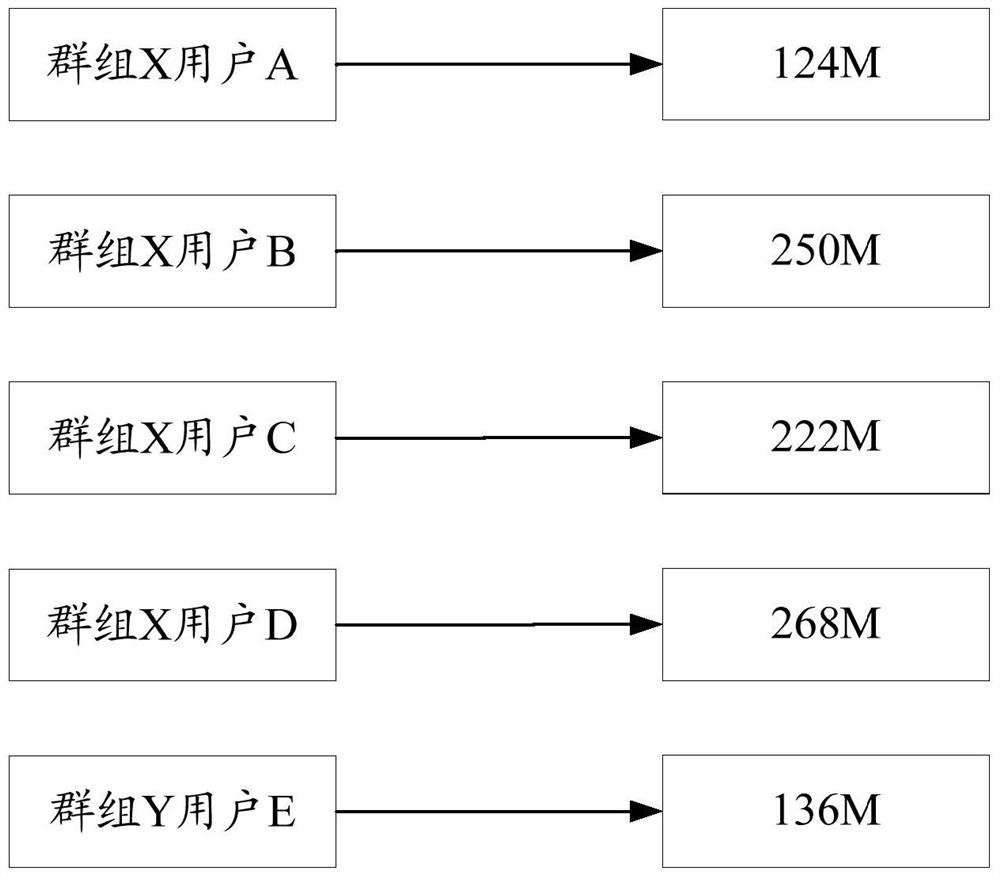
[0106] The embodiment of the present invention provides a resource access method, which is applied to a resource access terminal. It is assumed that u is a user, now U-accessed WeChat as an example, such as Image 6 As shown, the method includes:
[0107] Step 201, p Gets the command information of the U.
[0108] At present, the application (App) in the terminal involves both the user's life, although the function of the APP is very different, they basically have a common point: traffic is required. The flow is one of the resources, and in the actual traffic access, it is a case where multiple users are simultaneously accessed. Next, use U using WeChat as an example.
[0109] U is ready to contact his family through WeChat, first, U must open WeChat; second, enter information in the input box corresponding to his family; finally, click the "Send" button. As the final click action, P will acquire command information that requires traffic, and P will send the instruction information...
Embodiment 3
[0134] Embodiments of the present invention provide a resource access terminal 30, such as Figure 7 As shown, the terminal includes:
[0135] The module 301 is acquired to acquire instruction information of the first user;
[0136] Access module 302 for accessing the first user's exclusive resource according to the command information; wherein each user has corresponding exclusive resources;
[0137] When the access module 302 is also used for the exclusive resource depletion of the first user, the access module 302 is used to access the first user's reserve resource; the reserve resources of the first user are exclusive resources of the remaining users outside the first user. .
[0138] In this way, the user can implement concurrency access to resources according to the resources of different attributes, and can ensure high concurrent access to the rapid update and timely response of shared resources, thereby avoiding high and unenregation. Phenomenon.
[0139] At the same time, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com