Code analysis tool for recommending encryption of data without affecting program semantics
A technology of application code and database, which is applied in the field of code analysis tools for recommending data encryption without affecting program semantics, and can solve problems such as failure of application code, difficulty in implementing the strongest encryption scheme, and insufficient protection
Active Publication Date: 2017-11-28
MICROSOFT TECH LICENSING LLC
View PDF4 Cites 3 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Determining the strongest encryption scheme that can be applied to each database column can be very difficult to achieve for the reasons discussed abo
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
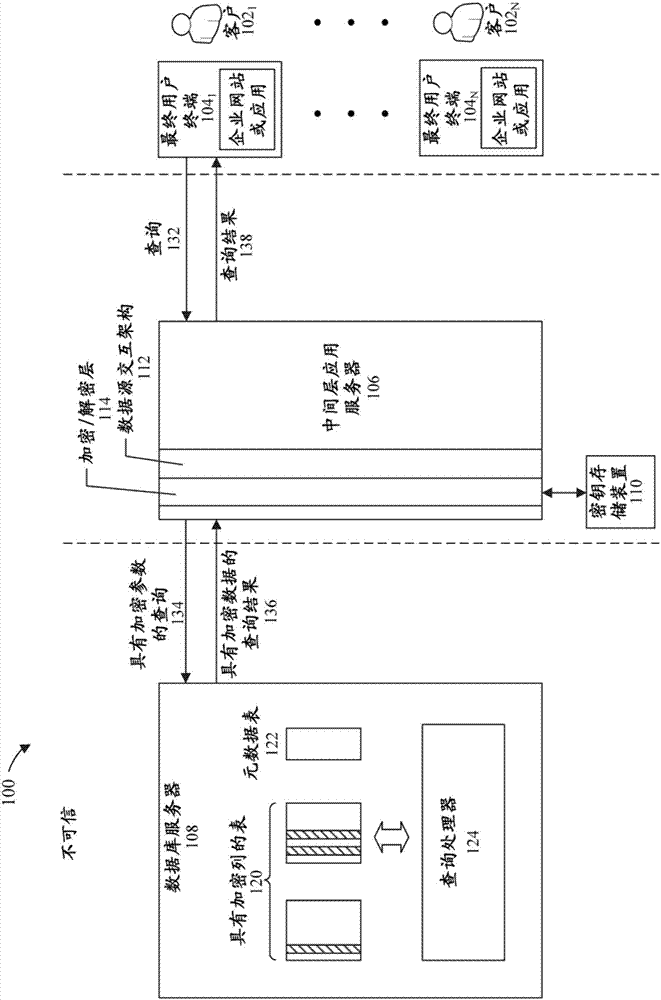
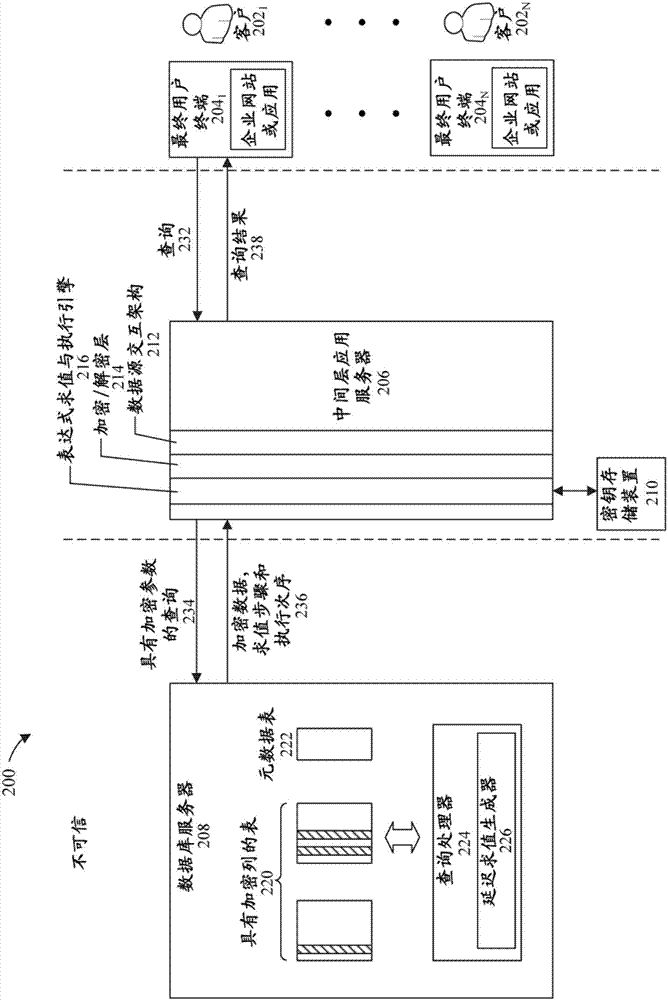
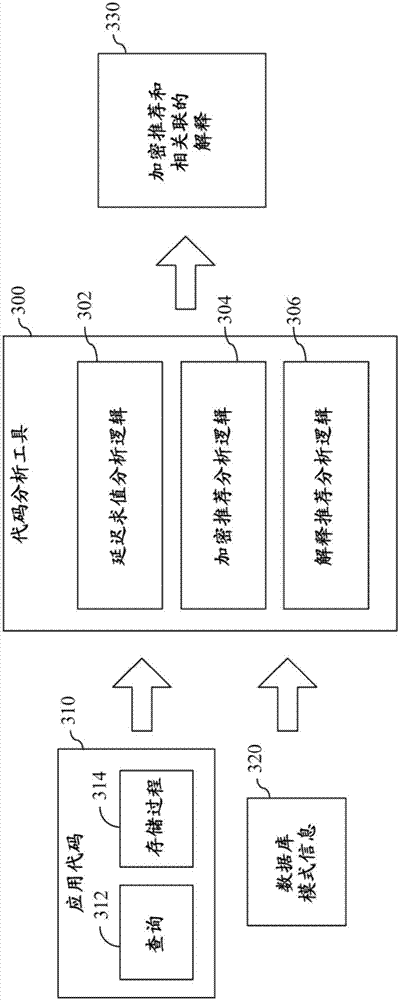
Systems, methods and computer program products are described that analyze the code of an application and, based on the analysis, identify whether data elements (e.g., columns) referenced by the code can be encrypted, and for those data elements that can be encrypted, recommend an encryption scheme. The recommended encryption scheme for a given data element may be the highest level of encryption that can be applied thereto without affecting the semantics of the application code. The output generated based on the analysis may not only include a mapping of each data element to a recommended encryption scheme, but may also include an explanation of why each recommendation was made for each data element. Such explanation may include, for example, an identification of the application code that gave rise to the recommendation for each data element.
Description
Background technique [0001] As more and more data is stored digitally, data leakage is getting more and more attention. For example, for applications that use cloud services to manage sensitive and business-critical information, data leakage may be the main deterrent. On the public cloud, applications must guard against potential malicious cloud administrators, malicious co-tenants, and other entities that can gain access to data through various legal means. Since the computing and storage platform itself cannot be trusted, any data in plaintext anywhere on the cloud platform (on disk, memory, or on the transmission line) must be considered vulnerable to leakage or malicious destruction. In industries such as finance, banking, and healthcare, compliance requirements mandate strong protection against these types of threats. However, existing security solutions such as Transparent Data Encryption (TDE) and Transport Layer Security (TLS) only protect data at rest and in transit, ...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L9/00H04L9/08G06F21/62
CPCG06F21/6227H04L9/008H04L9/0897H04L9/088H04L9/14
Inventor A·S·曼彻帕利于浩海M·J·兹韦灵K·瓦斯瓦尼P·安拓诺波洛斯
Owner MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com