Anti-tamper and anti-replay method in support of REST API
An anti-replay and anti-tamper technology, applied in the field of Internet WEBAPI security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
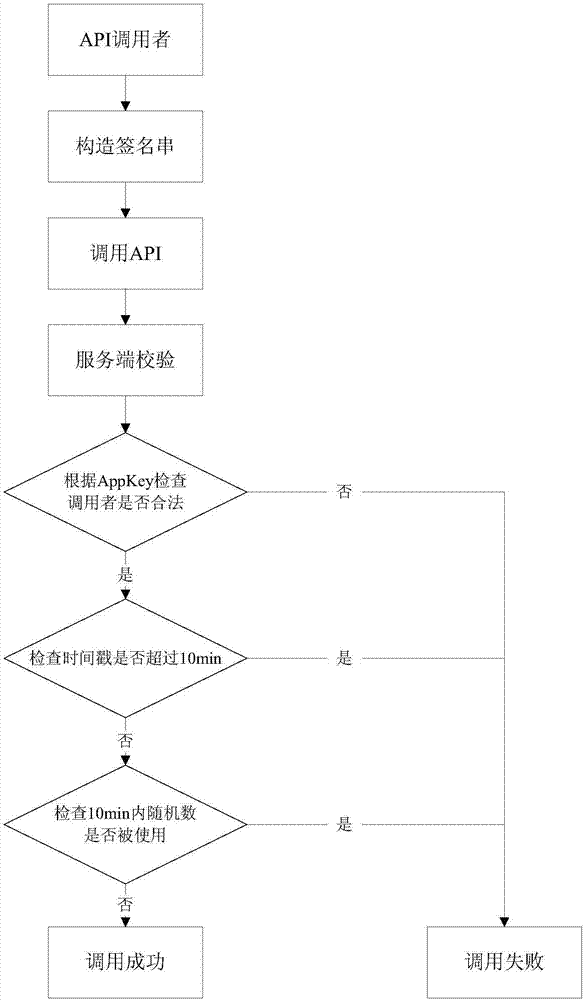
[0031] as attached figure 1 As shown, a method for supporting tamper-proof and anti-replay of REST API includes the following steps:
[0032] Step 1: Apply for user query API permission for the caller, obtain AppKey=11676533, AppSecret=a0a41ad0c8167a8ec3c9c384388f99e1;
[0033] Step 2: Construct the signature string: request parameters are sorted by dictionary, add the request header that needs to be signed, and the result is as follows:
[0034] {
[0035] X-CH-Key: 11676533
[0036] X-CH-Timestamp: 1500538695596
[0037] X-CH-Nonce: 4cdbc040657a4847b2667e31d9e2c3d9
[0038] / user? age=27&name=Jony
[0039]};
[0040] Step 3: Use a0a41ad0c8167a8ec3c9c384388f99e1 as the HMAC-SHA256 algorithm key to sign the signature string, and process the result with BAS...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com