Method for preventing leakage of user information
A user information and user name technology, applied in user identity/authority verification, encryption devices with shift registers/memory, electrical components, etc., can solve problems such as user information loss, and achieve the effect of improving security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
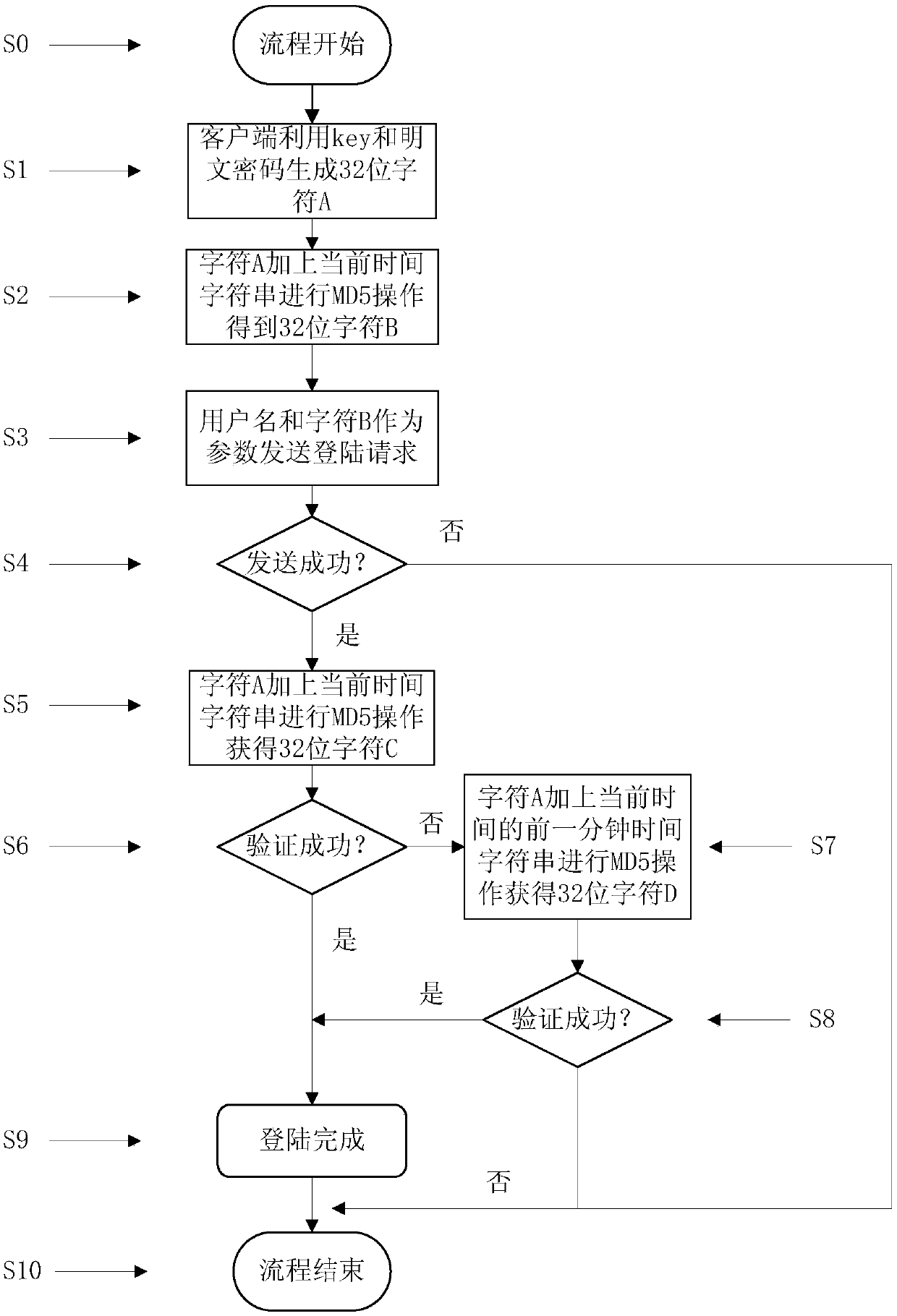
[0032] The present invention will be further elaborated and described below in conjunction with the accompanying drawings and specific embodiments of the present invention.
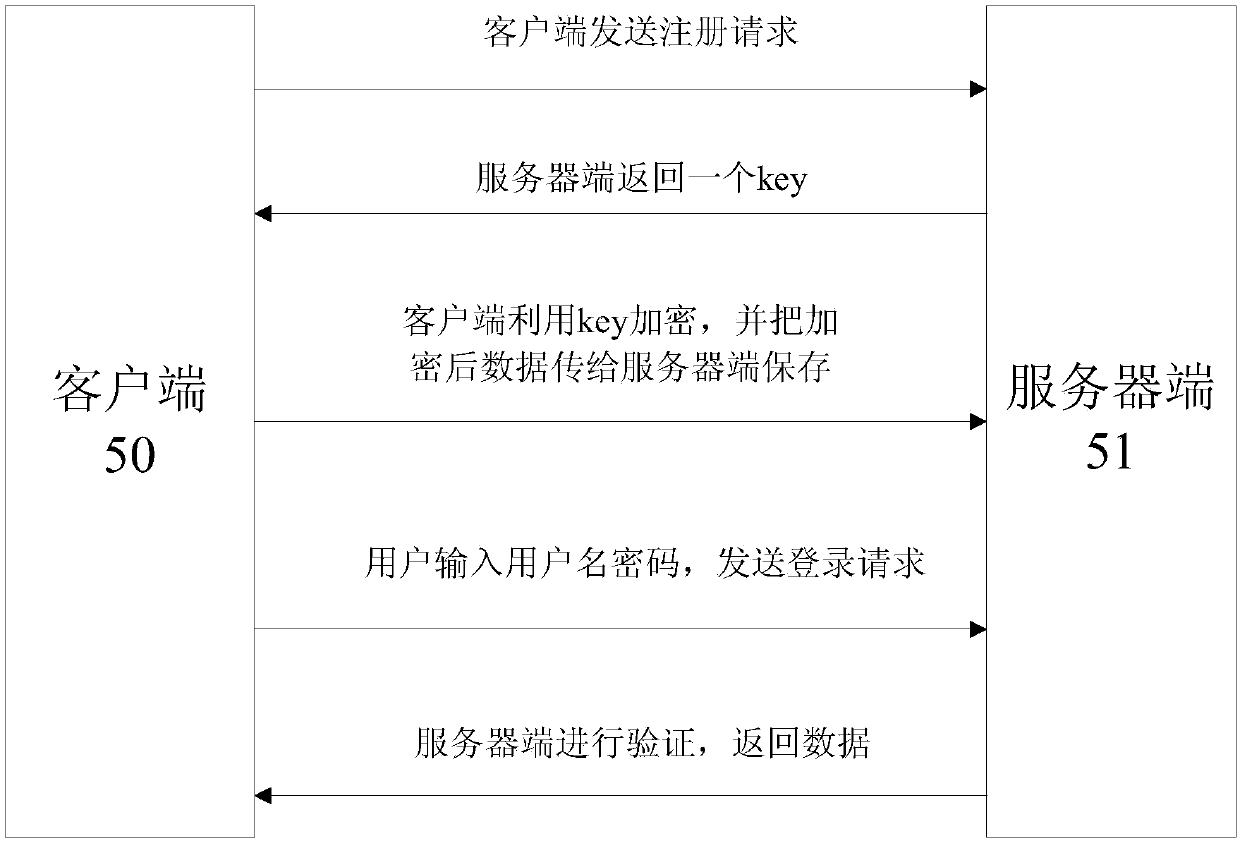
[0033] figure 1 A schematic diagram of the overall flow of the method for preventing user information leakage according to the present invention is shown. The client sends a registration request, and the server returns a key. The client uses the key value to encrypt, and transmits the encrypted data to the server for storage. The user inputs Username and password, send a login request, verify on the server side, and return data.
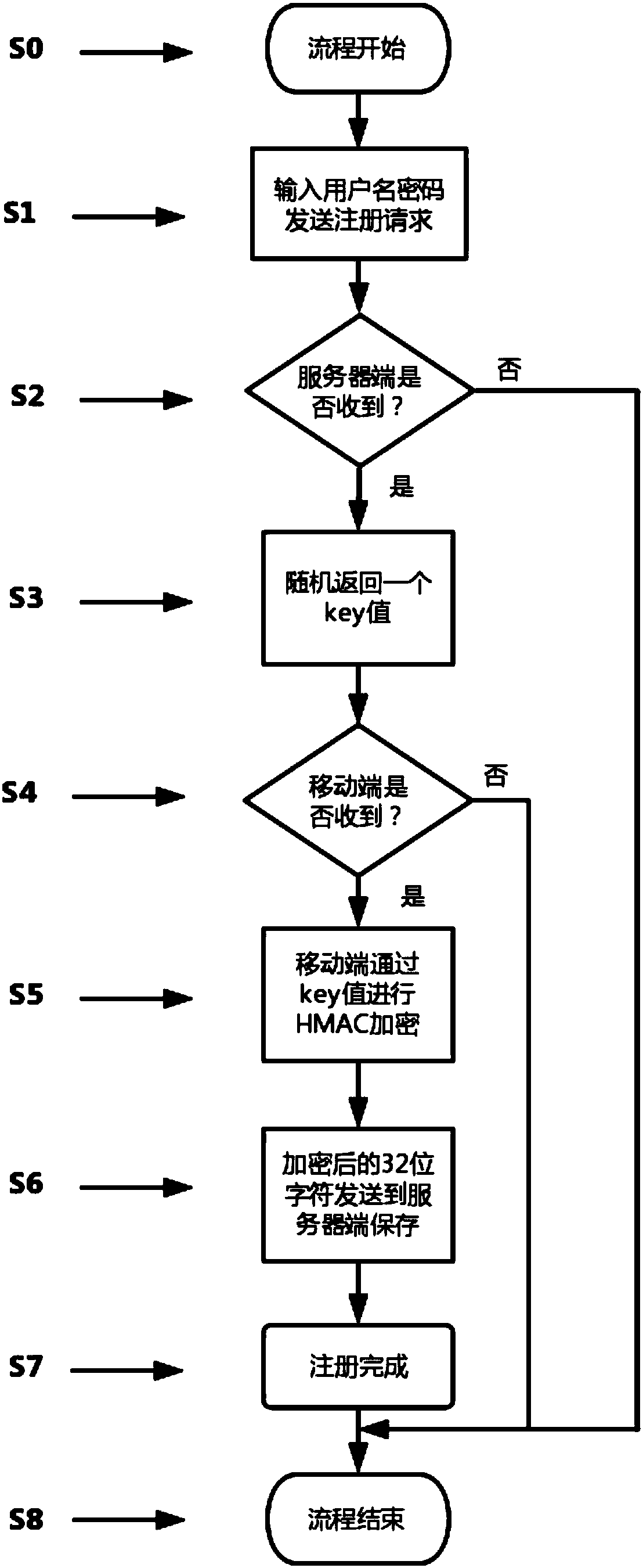
[0034] figure 2 The registration flow chart of the present invention is shown, and the registration steps are as follows:
[0035] S1: The user fills in the user name and password, and sends a registration request;
[0036] S2: The server judges whether the reception is successful, if it fails, the process ends, and if it succeeds, it enters step S3;
[0037] S3: The server...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap