USB attack protection
A technology for protecting equipment and accessory equipment, applied in internal/peripheral computer component protection, instruments, computing, etc., can solve problems such as attacking USB hosts, and achieve the effect of preventing attacks, blocking attacks, and improving personalized functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
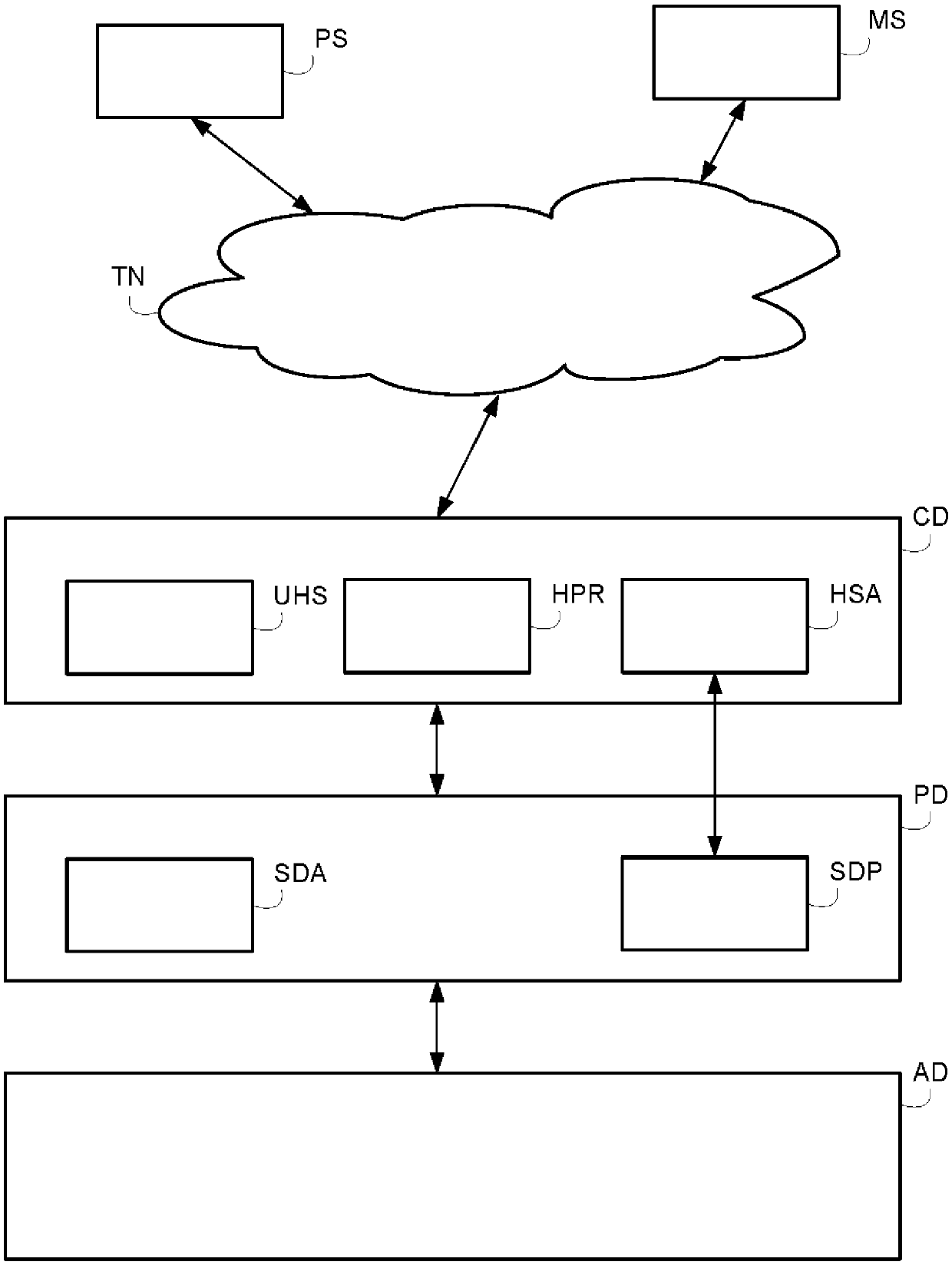
[0042] refer to figure 1 , the communication system according to the invention comprises a communication device CD, a protection device PD and an accessory device AD, as well as a protection server PS and a monitoring server MS accessible by the communication device CD through the telecommunication network TN.
[0043] The telecommunications network TN may be a wired or wireless network, or a combination of wired and wireless networks.
[0044] The telecommunications network TN may be a packet network, for example an IP ("Internet Protocol") high-speed network such as the Internet or an Intranet, or even a company-specific private network.
[0045] The communication device CD can be directly connected with the accessory device AD via a USB link to access content stored in the accessory device. The communication device may be referred to as a host device that receives the accessory device AD via a plug.
[0046] The communication device CD may be, for example, a personal ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com