A Progressive Calculation Method of K-Maximum Probability Attack Paths for a Specified Target Node Set
A technology of attack path and target designation, which is applied in the field of progressive solution of the K maximum probability attack path, can solve problems affecting the real-time performance of the attack path, increase calculation time, and increase calculation, so as to improve real-time calculation, reduce calculation time, The effect of reducing the amount of calculation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
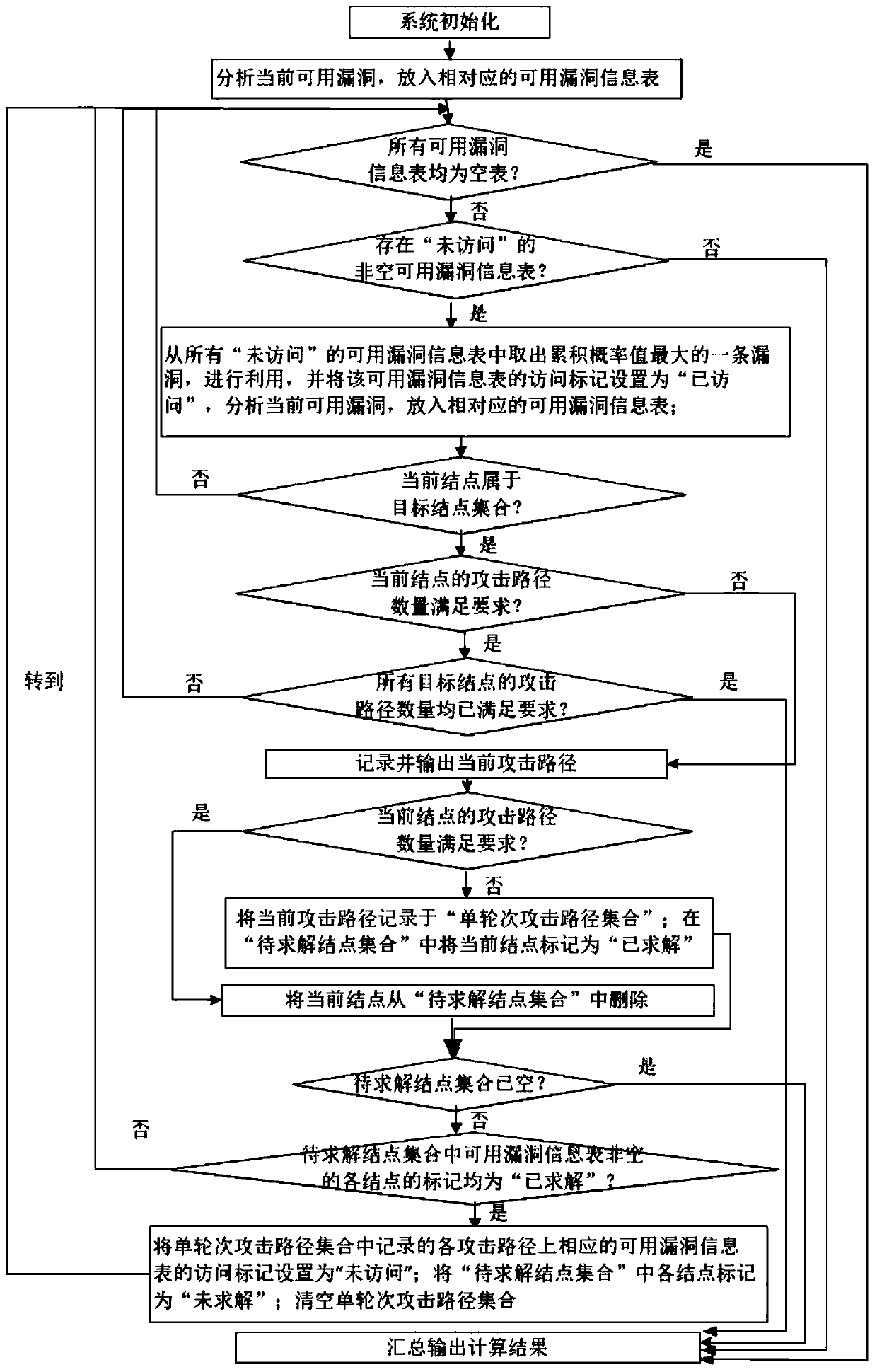
[0046] In order to make the technical means, creative features and objectives of the present invention easy to understand, the present invention is further described below in conjunction with specific embodiments.
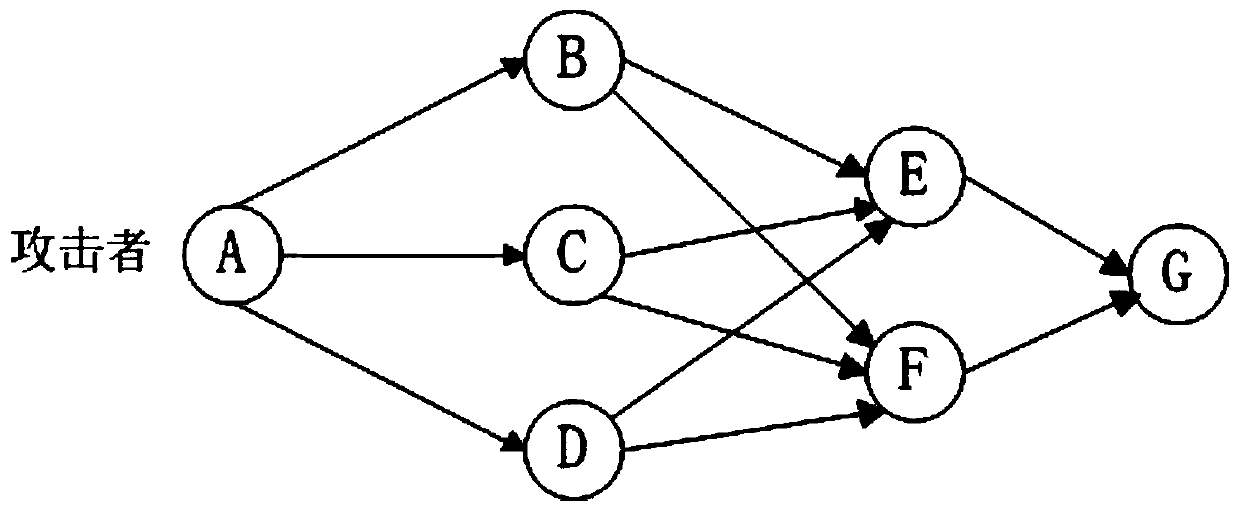
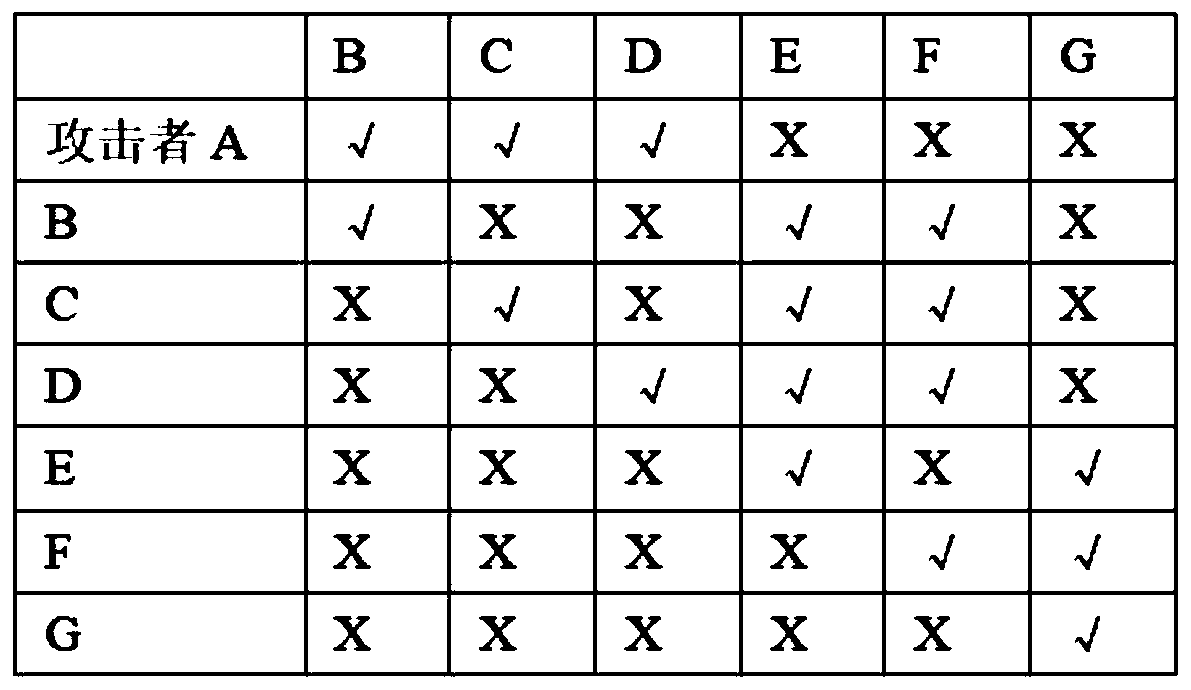
[0047] Network topology diagram such as figure 2 As shown, node A represents the attacker, nodes B, C, D, E, F and G represent the nodes in a given network system, and the directed arrows between nodes represent the access relationship between nodes, access relationship such as image 3 As shown, starting from the second line, each line represents a set of nodes that a node can access, "√" means direct access, "X" means no direct access, for example, the second line means that the attacker can directly access Nodes B, C, and D, but cannot directly access nodes E, F, and G. The third line indicates that node B can directly access nodes B, E, and F, but cannot directly access nodes C, D, and G. For the access relationship between other nodes, see image 3 . In t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com