System upgrading method and related device
A system upgrade and upgrade instruction technology, applied in the field of system inspection, can solve the problems of developers' economic losses, reduce the safety and reliability of the upgrade system, and achieve the effect of ensuring safety and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
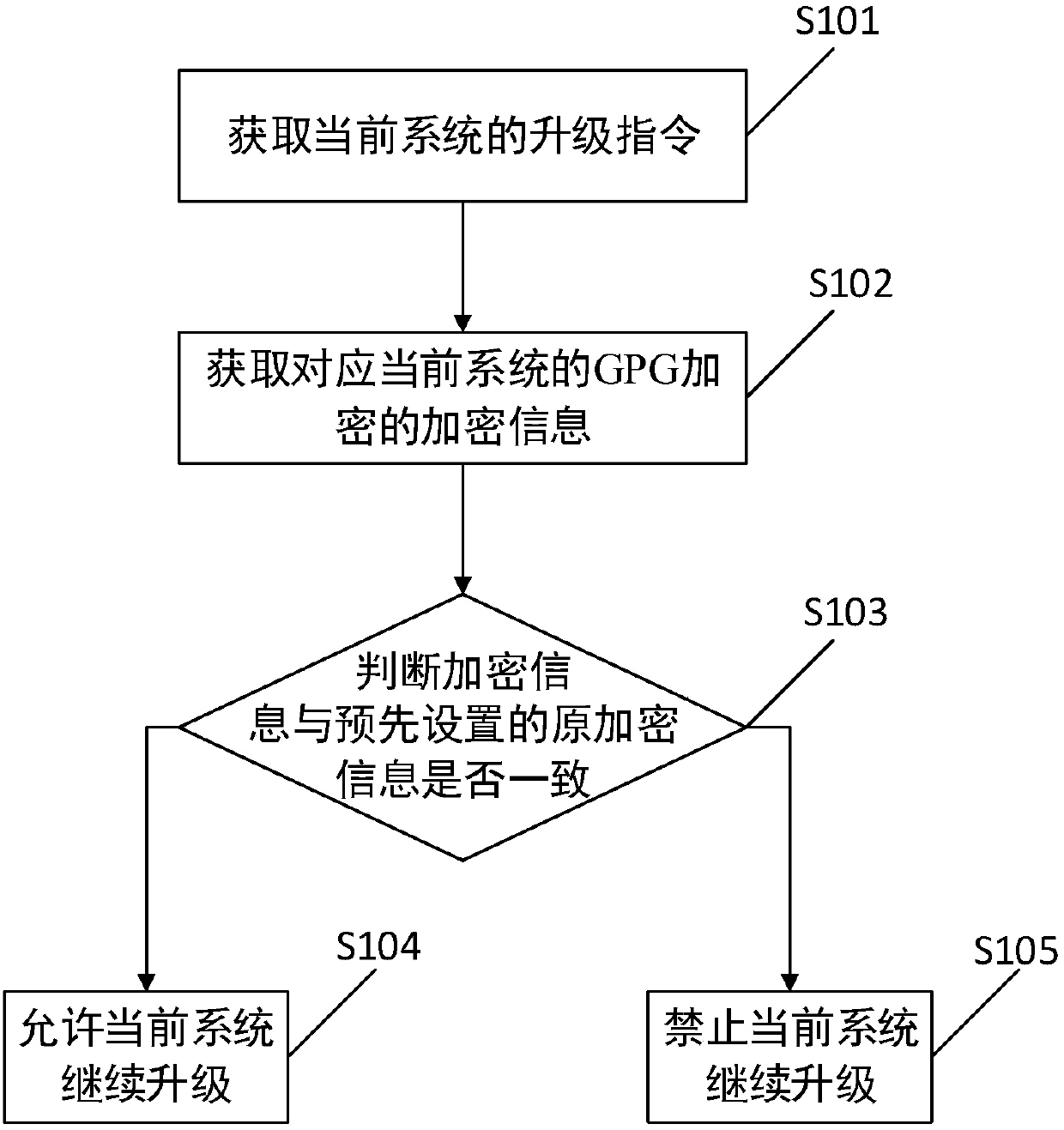
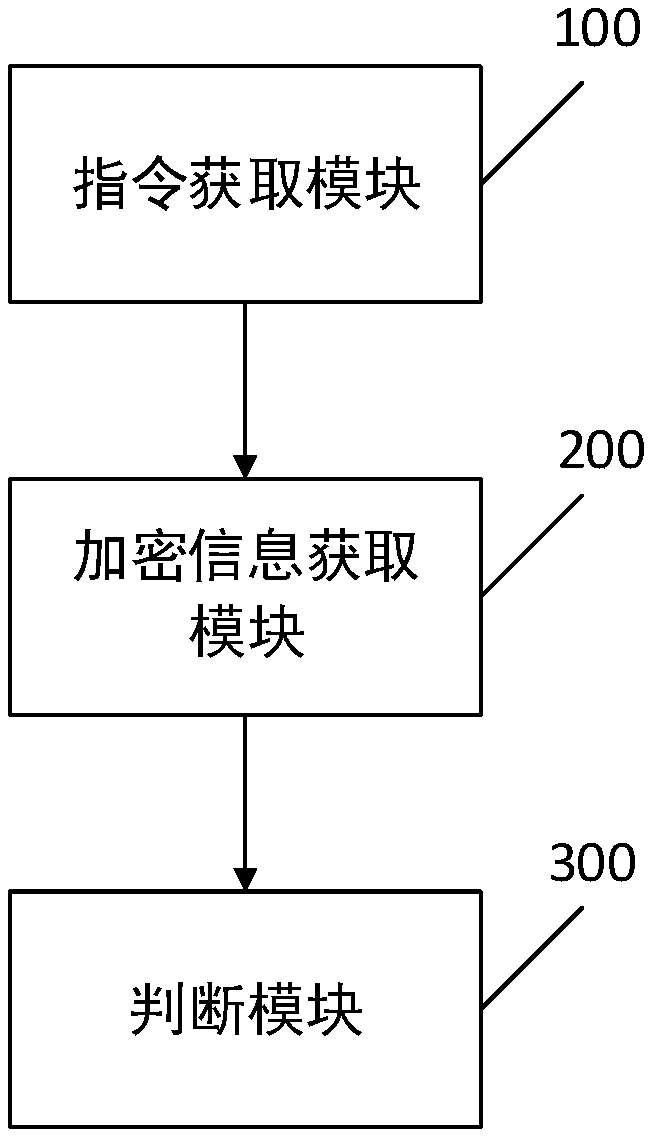
[0034] The core of the invention is to provide a system upgrading method. In the prior art, the system is usually encrypted by means of GPG encryption. When it is necessary to unlock the system encrypted by GPG, the public key and the private key are usually required to be unlocked together to succeed.
[0035] However, users or hackers can delete or replace GPG through technical means, so that the public key and private key of GPG will change so that users can successfully unlock the system through other public keys or private keys, thereby bypassing the developer’s direct control of the system. The system is upgraded or modified. Deleting or replacing GPG by the user is equivalent to bypassing the system's first check of encrypted information. If the user upgrades the system by himself rather than through the developer, it will cause a lot of economic losses to the developer.
[0036] And a kind of system upgrading method provided by the present invention can judge whethe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com