A method and credit card for enhancing the security of card-not-present payment transactions
A credit card and security technology, applied in the field of information security, can solve problems such as fraud, and achieve the effect of enhancing security and reducing the possibility of fraud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] This embodiment provides a method for enhancing the security of card-not-present payment transactions, the method comprising:
[0050] Step S1, the credit card is powered on, and the system is initialized;
[0051] Step S2, the credit card is dormant, wakes up when a preset interruption is detected, and executes step S3;
[0052] Step S3, the credit card enters the preset interruption processing flow to execute the preset interruption processing, and when the preset interruption processing is completed, exit the preset interruption processing flow and return to step S2;
[0053] Default interrupt handling includes:
[0054] Step a1, obtain the dynamic security code factor, and generate the first data block according to the dynamic security code factor and the card personalization data in the card;
[0055] In this embodiment, the card personalization data includes: main account number, card expiration date and service code sequence;
[0056] Generating the first data...
Embodiment 2
[0061] This embodiment provides a method for enhancing the security of card-not-present payment transactions, the method comprising:
[0062] Step 101, after the credit card is powered on, the system is initialized.
[0063] Step 102, the credit card sleeps, wakes up when an interruption is detected, and executes step 103.
[0064]Step 103 , the credit card enters the interruption processing flow to execute the interruption processing, and when the interruption processing is completed, exit the interruption processing flow and return to step 102 .
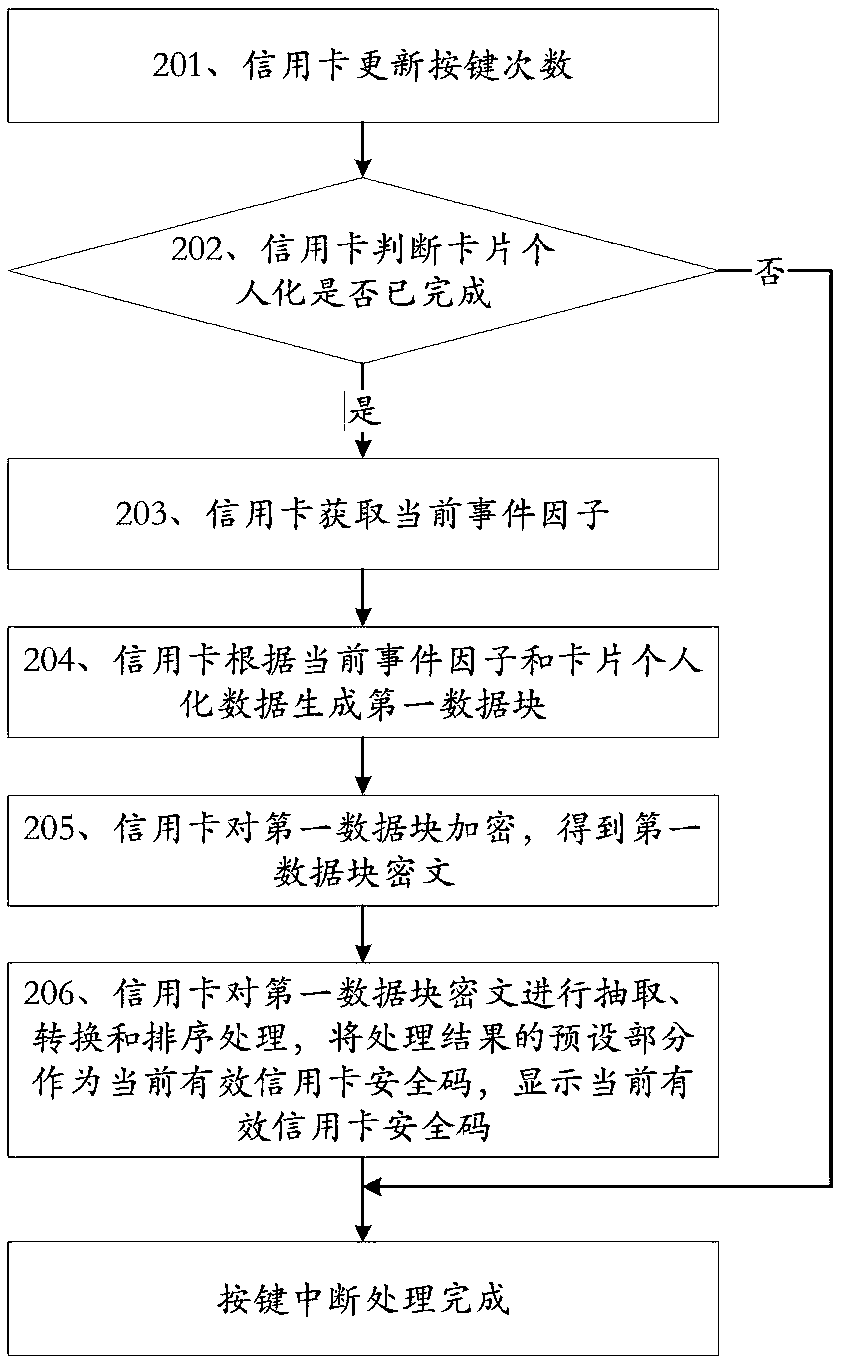
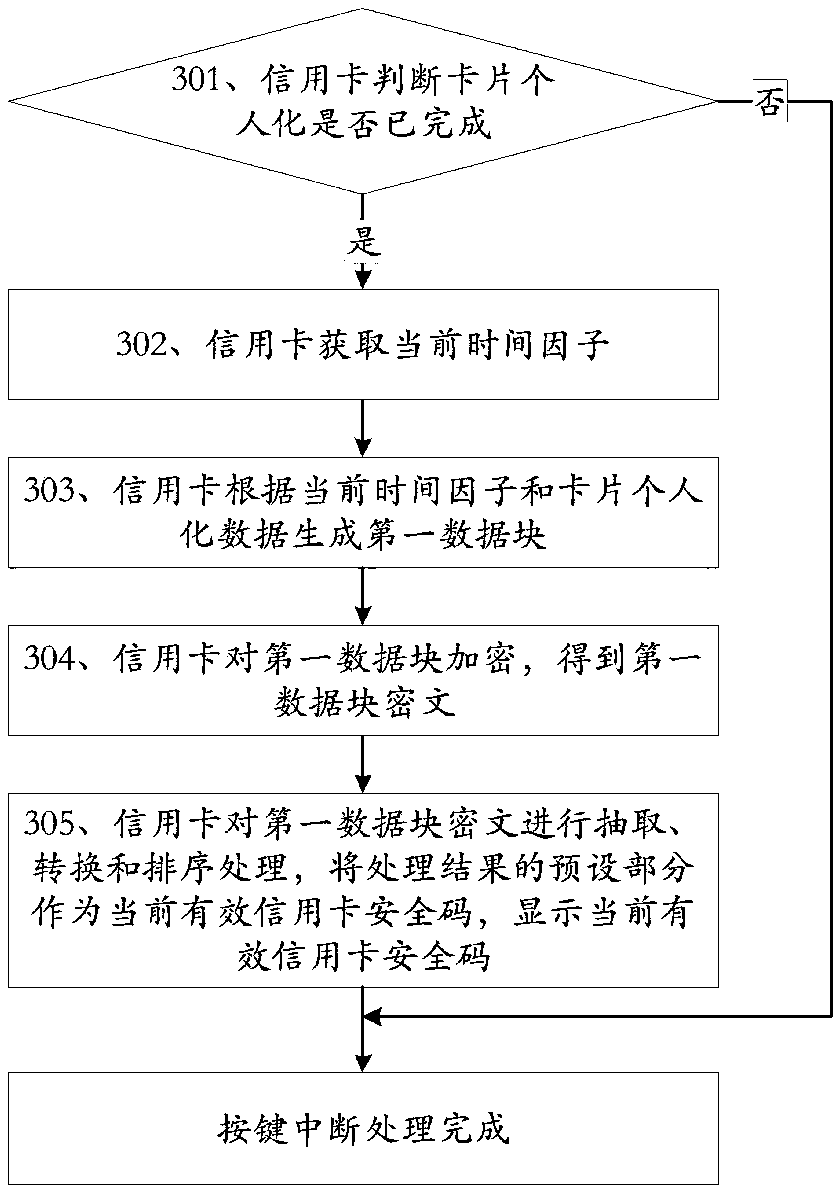
[0065] The interruption described in this embodiment specifically includes communication interruption and key interruption:
[0066] When the credit card detects a communication interruption, it is awakened, enters the communication interruption processing flow to execute the communication interruption processing, and exits the communication interruption processing flow when the communication interruption processing is completed; ...
Embodiment 3
[0097] This embodiment provides a method for enhancing the security of card-not-present payment transactions, the method comprising:
[0098] Step 101, after the credit card is powered on, the system is initialized.
[0099] Step 102, the credit card sleeps, wakes up when an interruption is detected, and executes step 103.
[0100] Step 103 , the credit card enters the interruption processing flow to execute the interruption processing, and when the interruption processing is completed, exit the interruption processing flow and return to step 102 .
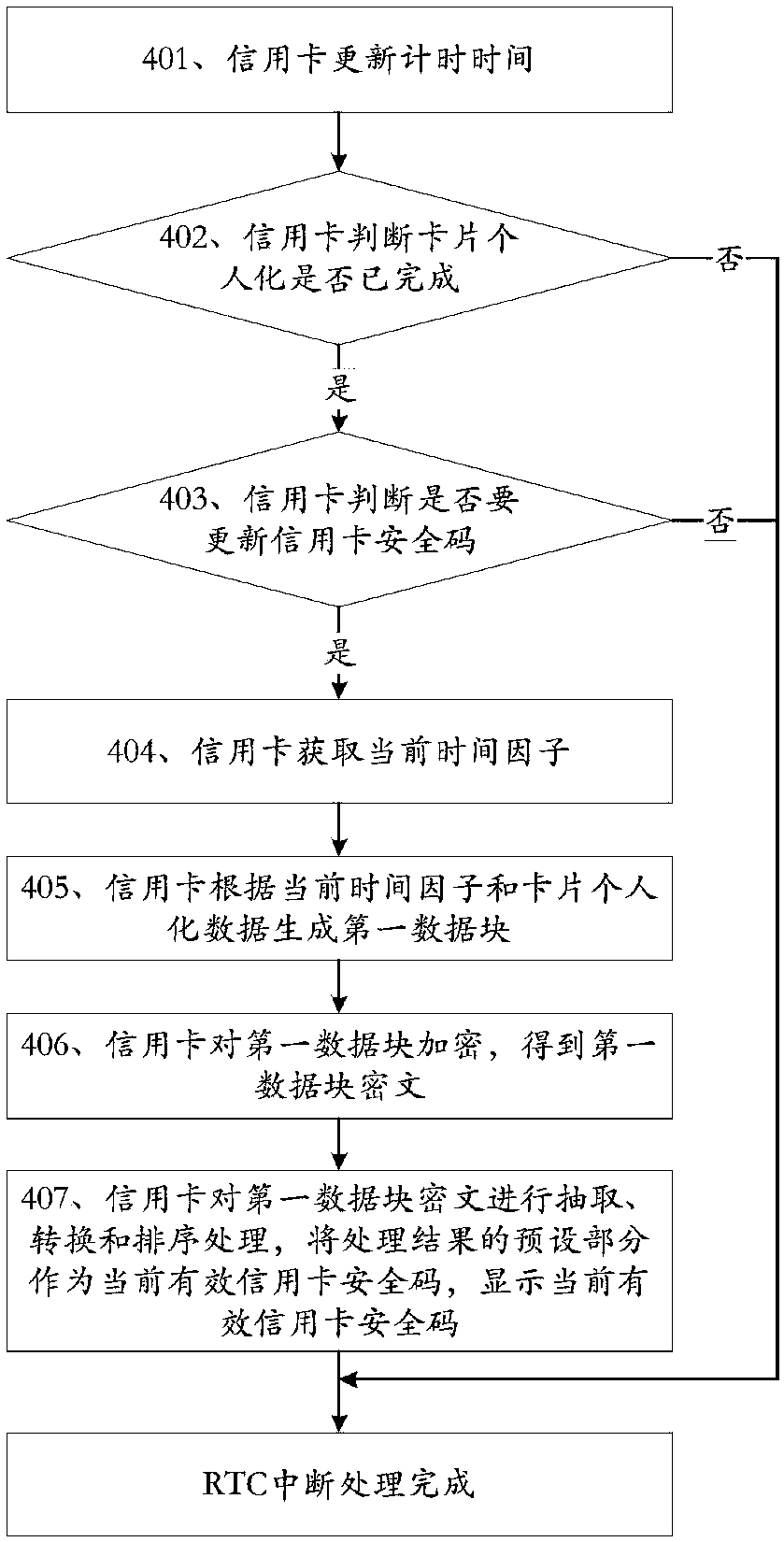
[0101] The interruption described in this embodiment specifically includes communication interruption, RTC interruption and key interruption:
[0102]When the credit card detects a communication interruption, it is awakened, enters the communication interruption processing flow to execute the communication interruption processing, and exits the communication interruption processing flow when the communication interruption process...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com