Application interface detection method and device for forgery attack
An application interface and interface technology, applied in the direction of user interface execution, program control device, computer security device, etc., can solve the problems of low accuracy of application interface, easy to cause false positives, false negatives, etc., to improve detection accuracy, The effect of improving network security and reducing false negative rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
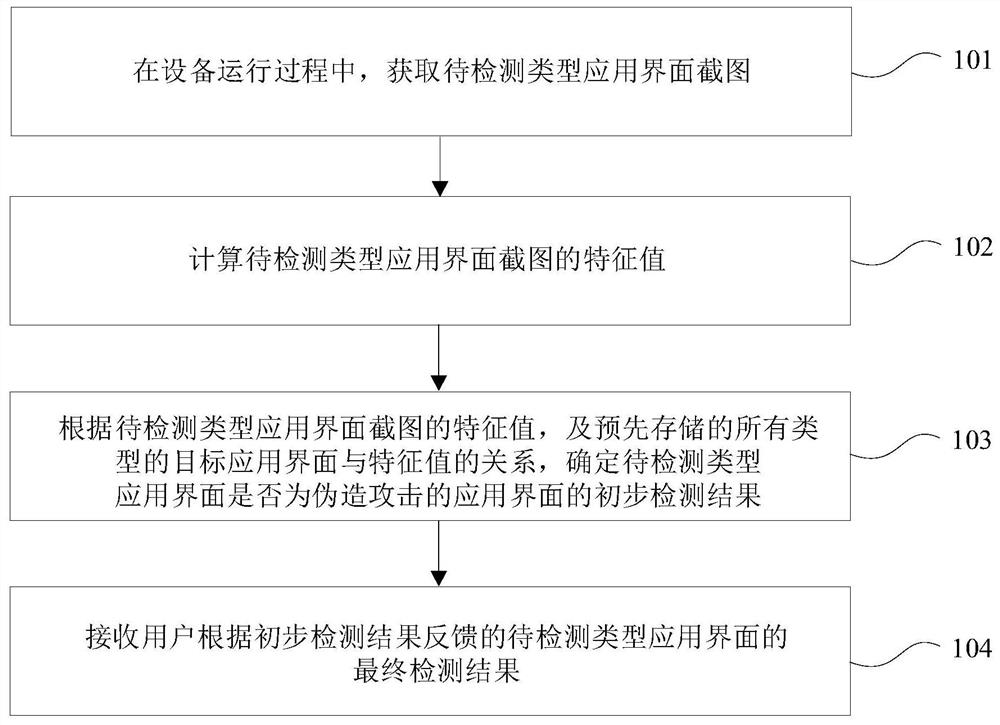
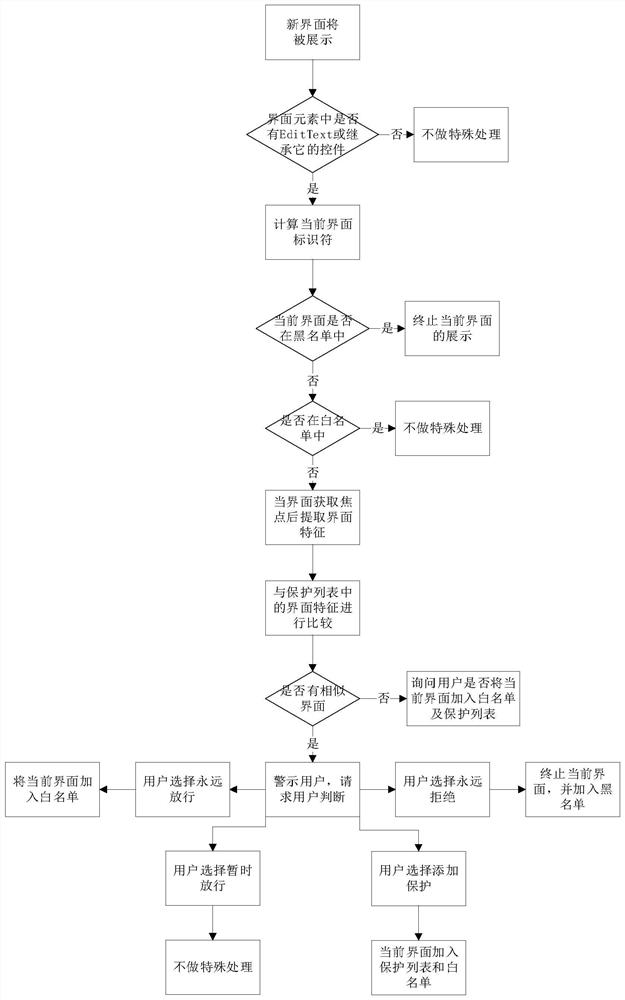
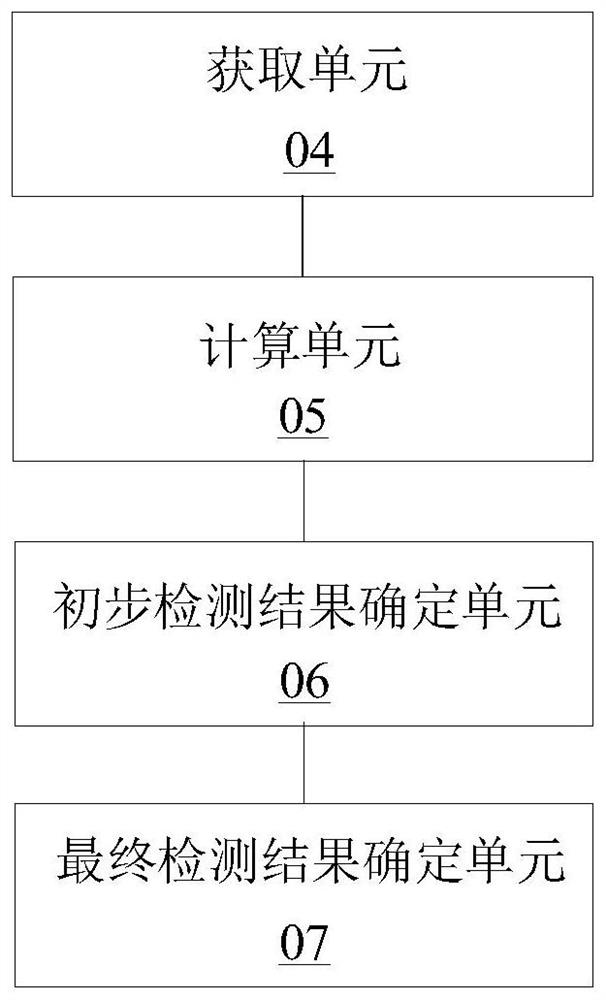
[0066] First, the interface identifier of the Activity interface can be: the class name of the Activity interface and the package name of the Activity interface; the interface identifier of the floating window interface can be: the hash operation result of the control layout tree structure information of the floating window interface; The interface identifier of the frame interface may be: a hash operation result of the dialog box interface control layout tree structure information.
[0067] In this case, in the process of controlling the current application display interface and determining whether the current application display interface is the application interface of the type to be detected, in addition to considering the interface identifier in the matching interface information, it is also necessary to consider the interface identifier in the interface information. The name of the application package, that is, the interface information of the application interface of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com