VOIP call encryption method and terminal
A technology for encrypting calls and encryption algorithms, applied in the field of communications, can solve problems such as low call security, and achieve the effects of improving security, reducing the risk of key leakage, and reducing the risk of being intercepted
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] In order to have a clearer understanding of the technical features, purposes and effects of the present invention, the specific implementation manners of the present invention will now be described with reference to the accompanying drawings.
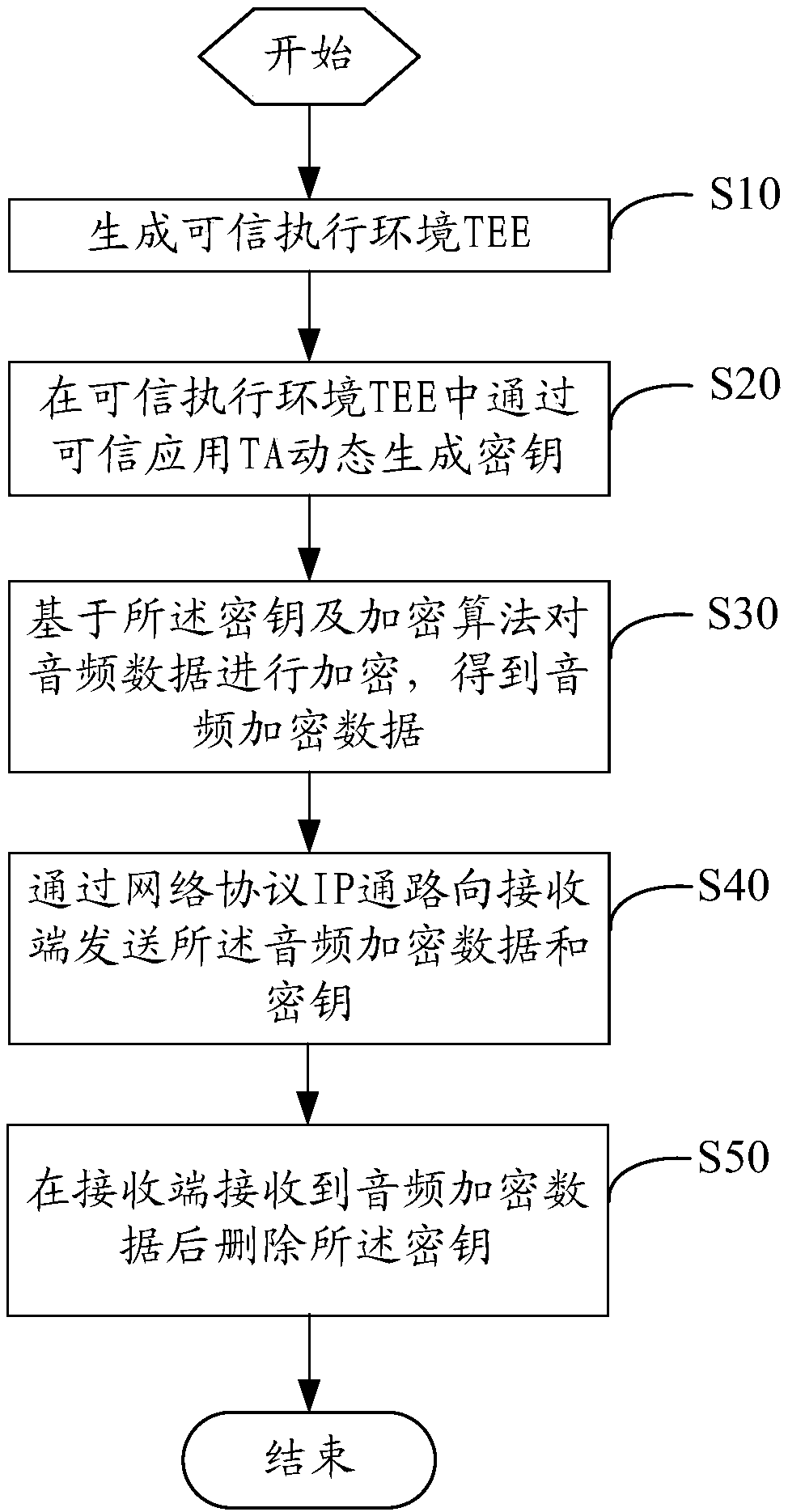
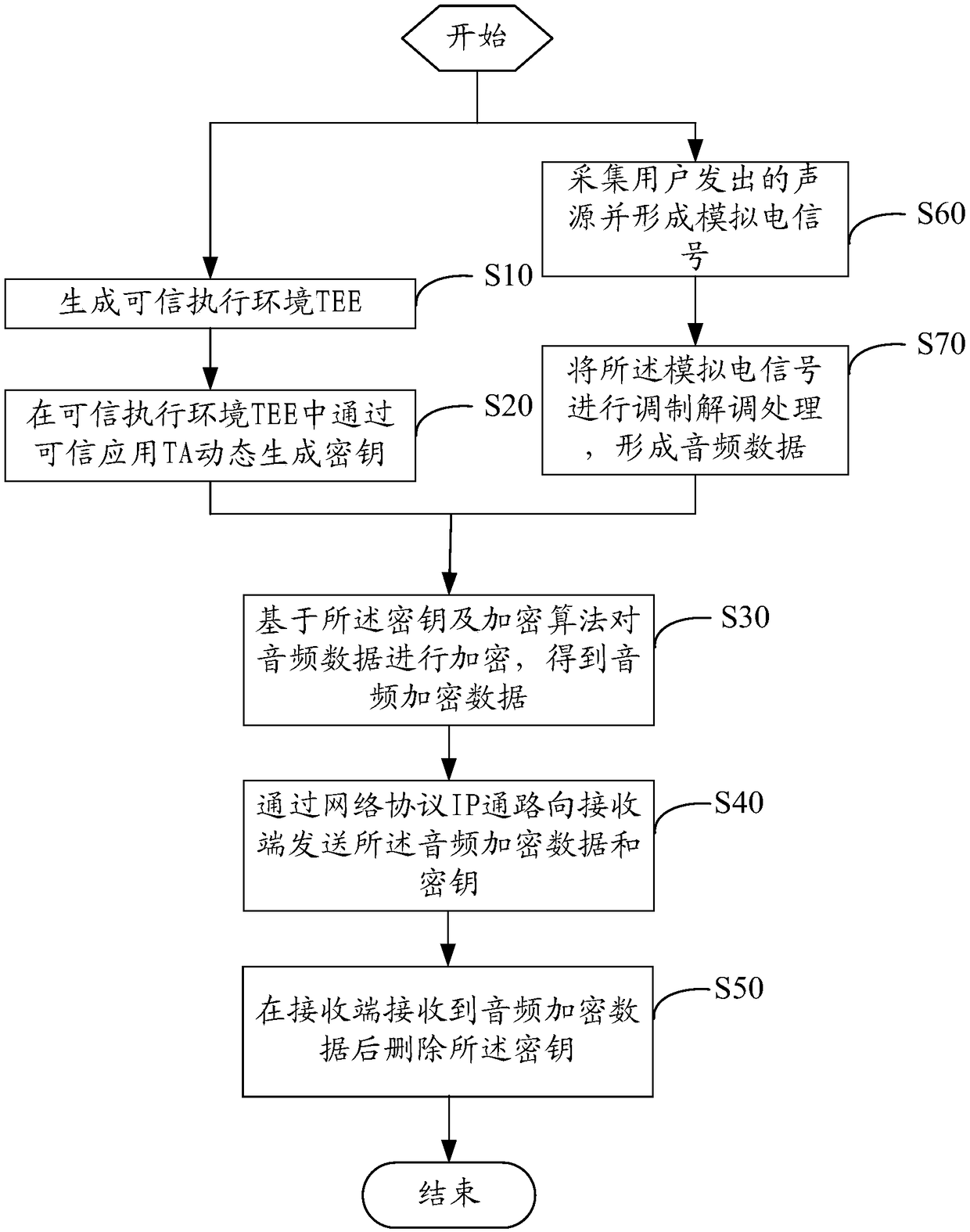
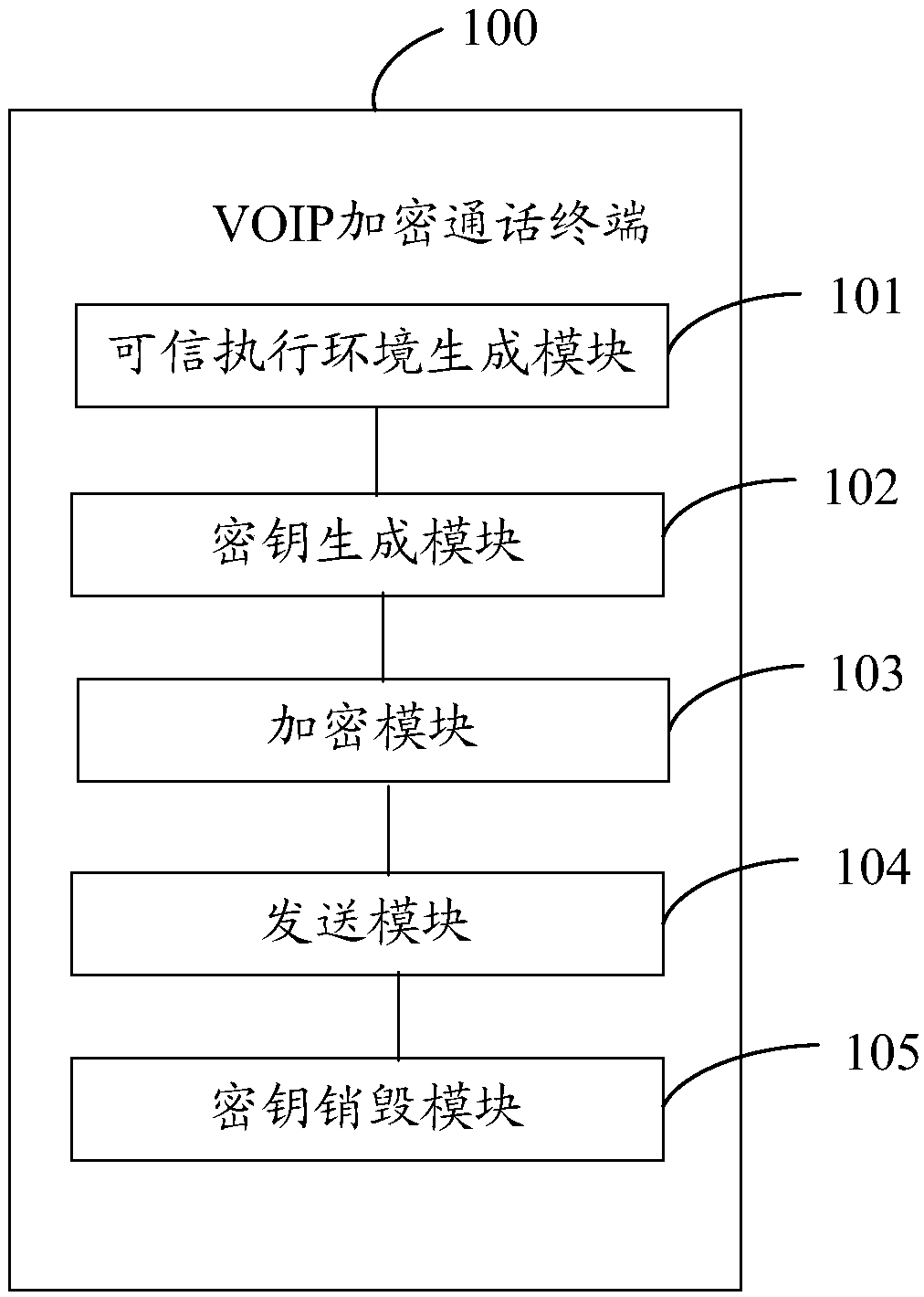
[0051] see figure 1 , figure 1 The flowchart of an embodiment of the VOIP encrypted call method provided by the present invention, as figure 1 shown, including the following steps:
[0052] Step S10, generating a trusted execution environment (Trusted Execution Environment, TEE).
[0053] In the embodiment of the present invention, the TEE may be generated on a VOIP encrypted call terminal, and the VOIP encrypted call terminal may be a smart phone. The TEE is a functional unit that integrates software and hardware inside the VOIP encrypted call terminal. Compared with the Rich Execution Environment (REE), the TEE can realize unified management and unified allocation of hardware resources, and the Different applications can be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com