Data processing method and device, equipment and machine readable medium
A data processing and processor technology, applied in the computer field, can solve problems such as file leakage, achieve the effect of improving security and reducing the risk of key leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
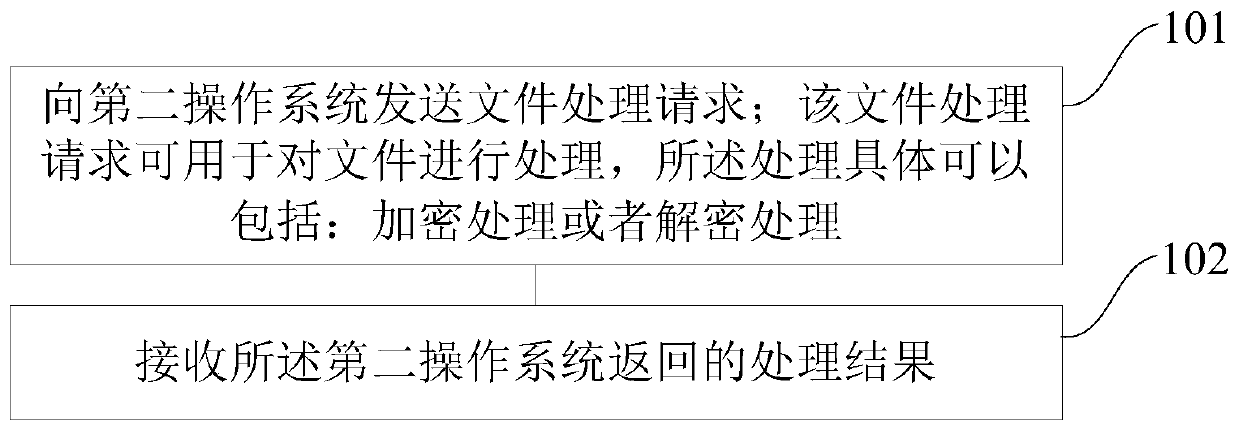
[0074] refer to figure 1 , shows a flow chart of the steps of Embodiment 1 of a data processing method of the present application, the device to which the method is applied is loaded with a first operating system and a second operating system; wherein, the first operating system corresponds to the first execution Environment, the namespace of the first operating system includes: files; the second operating system corresponds to a second execution environment, and the second operating system stores a key corresponding to the file; the method may specifically Including the following steps:
[0075] Step 101. Send a file processing request to the second operating system; the file processing request can be used to process the file, and the processing can specifically include: encryption processing or decryption processing;
[0076] Step 102, receiving a processing result returned by the second operating system.
[0077] figure 1 At least one step included in the illustrated met...
Embodiment 2
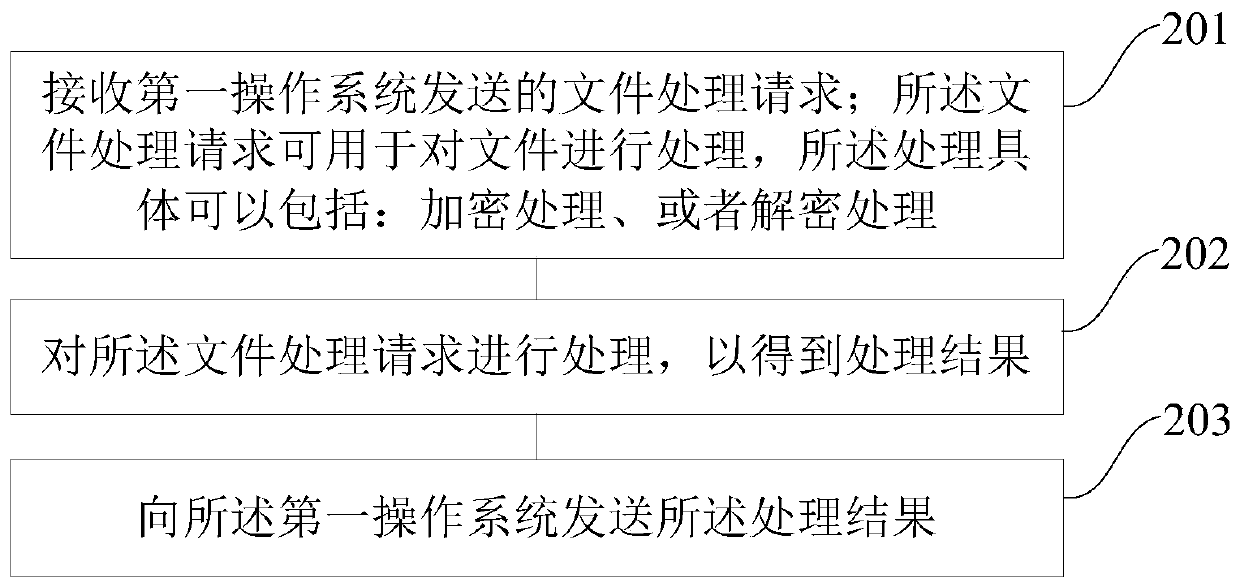
[0101] refer to figure 2 , shows a flow chart of the steps of Embodiment 2 of a data processing method of the present application, the device to which the method is applied may be loaded with a first operating system and a second operating system; wherein, the first operating system may correspond to the second operating system An execution environment, the namespace of the first operating system may include: a file; the second operating system may correspond to a second execution environment, and a key corresponding to the file may be stored in the second operating system;
[0102] The method may specifically include the following steps:
[0103] Step 201: Receive a file processing request sent by the first operating system; the file processing request can be used to process the file, and the processing can specifically include: encryption processing or decryption processing;
[0104] Step 202, process the file processing request to obtain a processing result;
[0105] Ste...
Embodiment 3
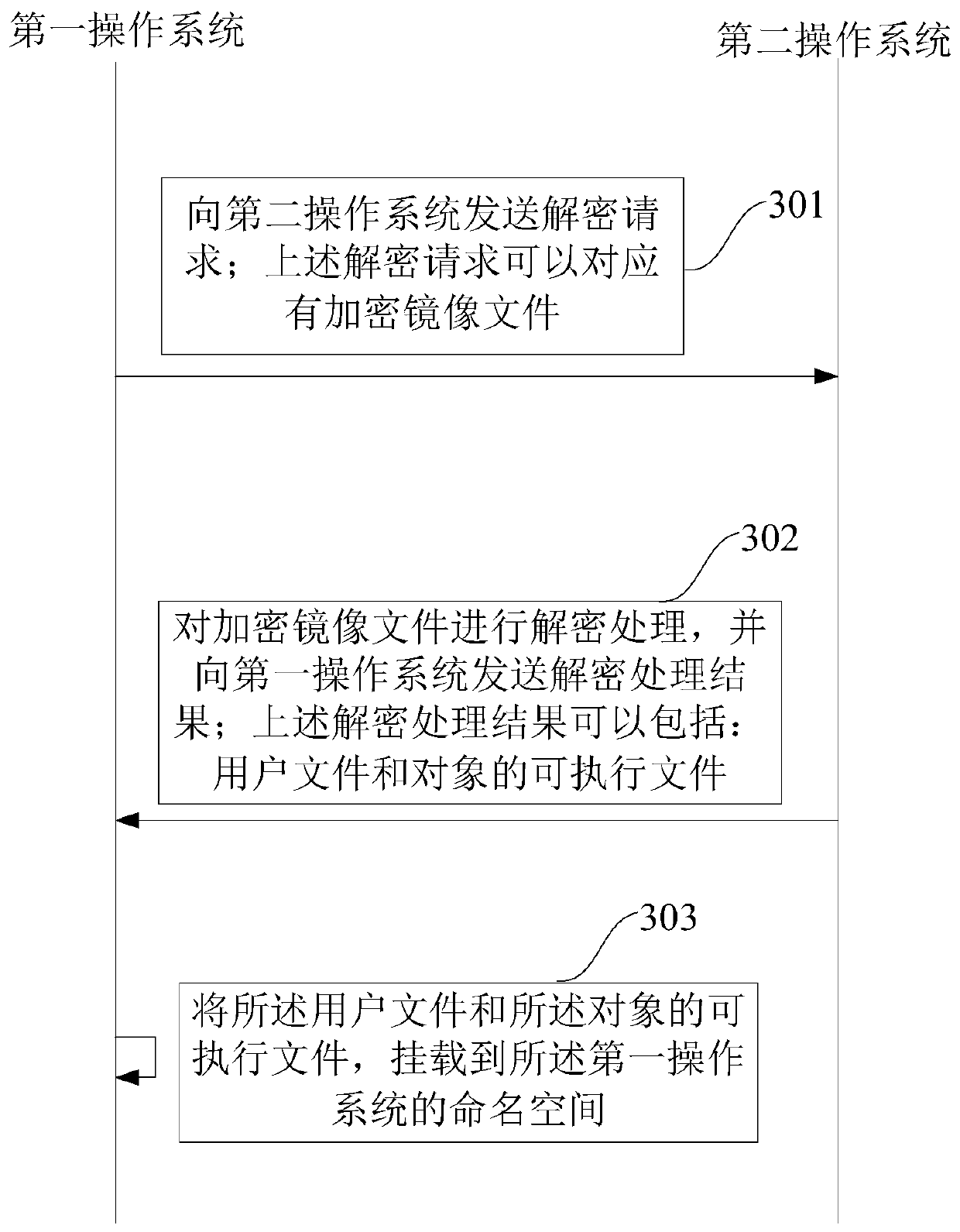
[0117] refer to image 3 , shows a flow chart of steps in Embodiment 3 of a data processing method of the present application, the device to which the method is applied may be loaded with a first operating system and a second operating system; wherein, the first operating system may correspond to the second operating system An execution environment, the namespace of the first operating system may include: a file; the second operating system may correspond to a second execution environment, and a key corresponding to the file may be stored in the second operating system;
[0118] The method may specifically include the following steps:
[0119] Step 301, the first operating system sends a decryption request to the second operating system; the decryption request may correspond to an encrypted image file;
[0120] Step 302, the second operating system decrypts the encrypted image file, and sends the decryption result to the first operating system; the decryption result may inclu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com