Trusted repeater, key encryption method, device and system for quantum communication network
A technology of key encryption and quantum key, which is applied in the key encryption method and system field of quantum communication network, and can solve the hidden dangers of relay key leakage and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
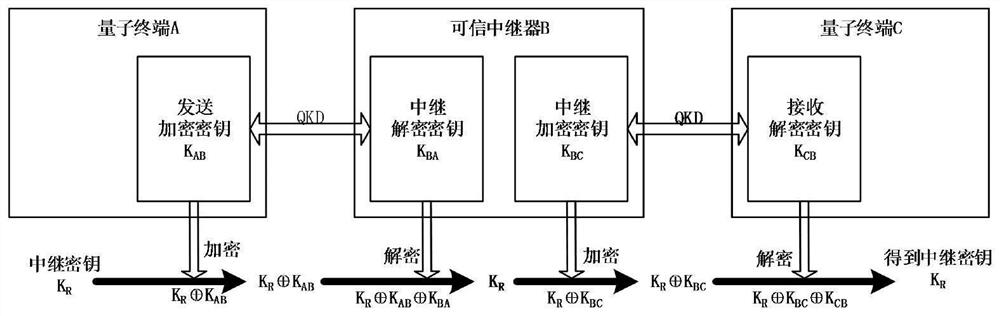
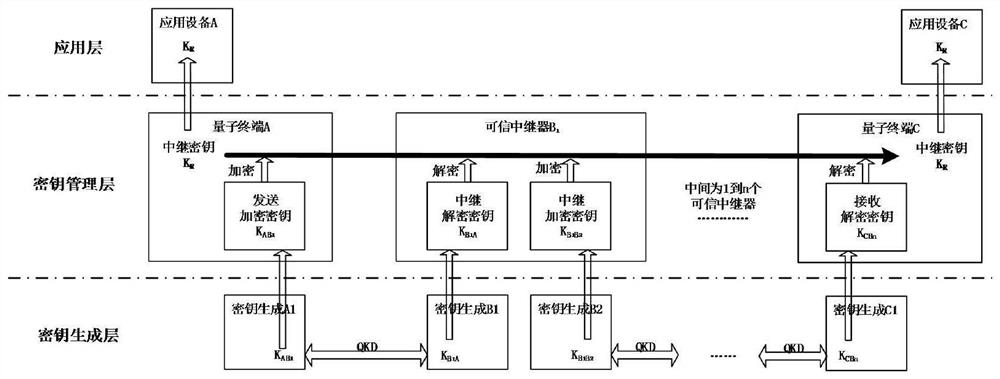
[0116] The embodiment of the present invention proposes a key encryption method for a trusted repeater. In order to make the whole process more clear, such as image 3 , Figure 4 Shown is a schematic diagram of the application of the trusted repeater in the quantum communication network. image 3 , Figure 4 Shown are the application of the above scheme on a trusted relay and multiple trusted relays ( Figure 4 Where n is a positive integer, n≥2) the above scheme is applied. Depend on image 3 , Figure 4 It can be seen that, compared with the prior art, a preset key encryption key is added to each trusted repeater for encrypting the key stored in the key cache module. Since the workflow of each trusted relay is the same, the image 3 Specifically shown are:
[0117] Step 101, the trusted relay B receives the first relay key K sent by the previous node R ⊕K AB Afterwards, decrypt the key K through the encrypted relay BA ⊕K B For the first relay key K R ⊕K AB Dec...
Embodiment 2
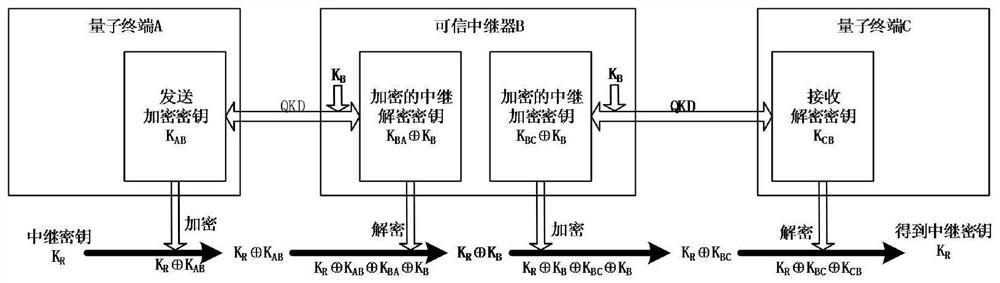
[0126] At the same time, the embodiment of the present invention also proposes a key encryption device of a trusted repeater corresponding to the aforementioned embodiment 1, the structure of which is as follows Figure 5 As shown, it includes a key encryption module, a key relay and forwarding module, and a key cache module;
[0127] The key encryption module is used to store the preset key encryption key K B , and encrypt the key K with a preset key B Decryption key K for relay BA Encrypt to obtain the encrypted relay decryption key K BA ⊕K B ; Also used to encrypt the key K through the preset key B To the relay encryption key K BC Encrypt to obtain the encrypted relay encryption key K BC ⊕K B ;
[0128] A key relay forwarding module, configured to receive the first relay key K from the previous node R ⊕K AB Afterwards, decrypt the key K through the encrypted relay BA ⊕K B For the first relay key K R ⊕K AB Decrypt to obtain the encrypted relay key K R ⊕K B ; ...
Embodiment 3
[0133] At the same time, the embodiment of the present invention also proposes a key encryption method for a quantum communication network, such as image 3 with Figure 4 One or more trusted relays are shown. Compared with the prior art, a preset key encryption key is added to each trusted repeater for encrypting the relay encryption key and the relay decryption key. Since the workflow of each trusted relay is the same, the image 3 Specifically, the method shown is:
[0134] Step 701, sending the relay key K that quantum terminal A will need to send R Send encryption key K using AB Obtain the first relay key K after encryption R ⊕K AB , and then the first relay key K R ⊕KAB Send to the next node; wherein the sending encryption key K AB with the relay decryption key K at the next node BA Corresponding;
[0135] Step 702, the trusted relay B receives the first relay key K sent by the previous node R ⊕K AB Afterwards, decrypt the key K through the encrypted relay B...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com