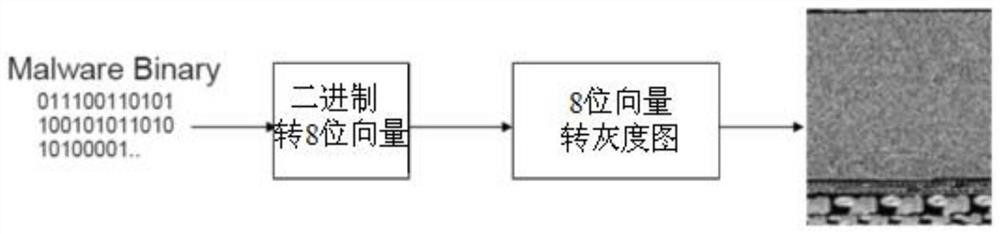
A Visual Analysis Method of Malicious Code Based on Space Filling Curve
A space-filling curve and malicious code technology, which is applied in the field of malicious code visualization analysis based on space-filling curves, can solve the problem of analysis program termination, inability to see grayscale images, and inability to intuitively reflect whether samples are encrypted or packed. and other problems to achieve the effect of reducing business level requirements and improving analysis efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0026] A method for visual analysis of malicious code based on space-filling curves, specifically:
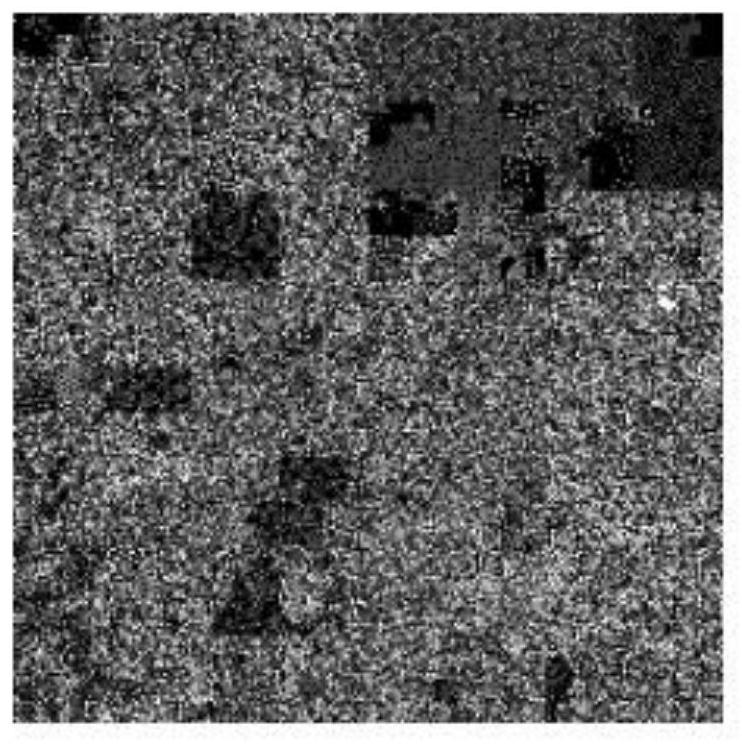
[0027] Step 1: Take Rootkit.Win32.Podnuha class sample.alo as an example, its file size is 205824 bytes, and the sequence is represented as 77-90-80-0-0-2-0-0-0-4- in decimal 0-15-0-255-255-0-0..., according to the step size Step=205824 / 65536=3.140625 sampling, then the new sequence is 77-0-0-4-0-0...; then give the byte Mark RGB value: Byte 77 is a printable character, using only the green channel, so the RGB value is marked as (0, 77, 0), byte 0 is a non-printable character, using both red and blue channels, so its RGB The value is marked as (0, 0, 0), and similarly byte 4 is a non-printable character, and its RGB value is marked as (4, 0, 4)...; finally, the pixel sequence of the marked RGB value is divided into 8-order Hilbert The order of the curve traversing the 256*256 two-dimensional plane fills the area and generates a Hilbert diagram, such as Figure 2A As shown, th...
Embodiment 2
[0032] The malicious code visual analysis method based on the space-filling curve described in Embodiment 1 is used to generate images of Backdoor.Win32.Rukap class samples .geu, .kl, and .lc, such as Figure 3A-Figure 3C , Figure 4A-Figure 4C ,as well as Figure 5A-Figure 5C As shown, the present invention can find subtle differences between images from multiple perspectives when analyzing malicious samples of the same family, which provides a basis for grasping the evolution of the variants of the family.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com