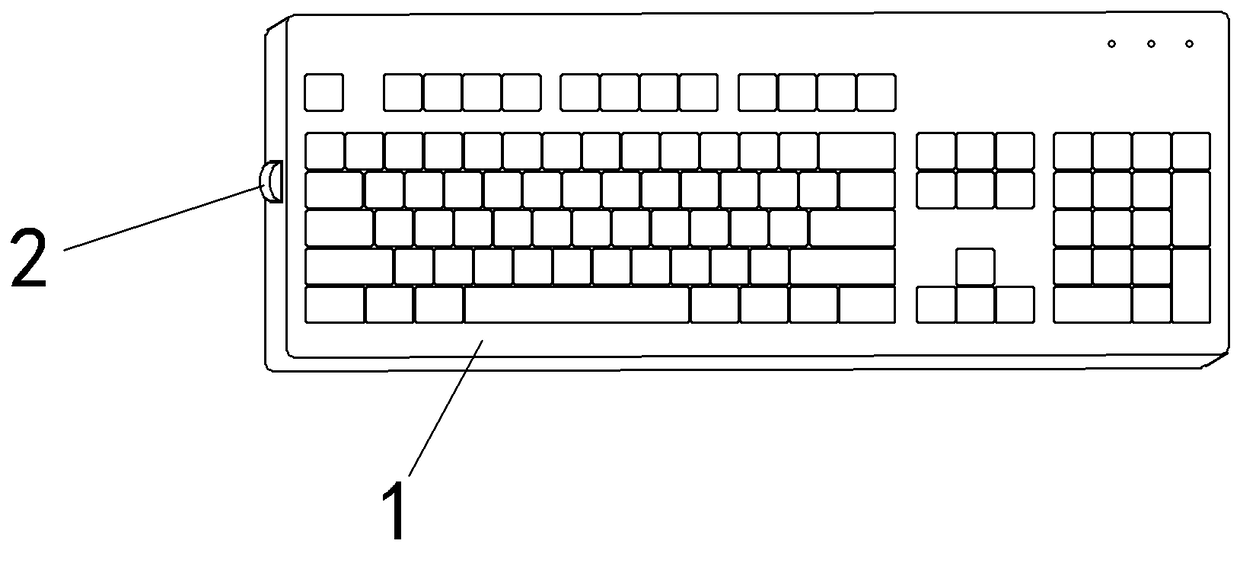
Keyboard with one-key screen locking function
A keyboard and key lock technology, applied in the input/output process of data processing, the input/output of user/computer interaction, instruments, etc., can solve the problems of others peeping, and achieve the effect of preventing data leakage
Inactive Publication Date: 2018-08-28
XIANGYANG NO 42 MIDDLE SCHOOL
View PDF0 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
But sometimes when we are operating, someone comes to us, if we can't turn off the screen quickly, it will still cause others to peep
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
[0008] figure 1 As shown: the keyboard 1 is provided with a control switch 2 at the side end, which can lock the screen with one key.
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention provides a keyboard with a one-key screen locking function. A control switch is arranged on the side of a keyboard body, so that during use of a computer, a screen locking key can be pressed if a person is discovered to be on the side, and a display screen can be turned off immediately to avoid peep of the person, so that data leakage can be prevented.
Description
technical field [0001] The invention relates to a keyboard, in particular to a keyboard capable of locking the screen with one key. Background technique [0002] When working in a company, in order to prevent data leakage, people usually turn off the computer screen and lock the screen before leaving the computer to prevent others from peeping. But sometimes when someone comes to us during operation, if the screen cannot be turned off quickly, it will still cause others to peep. Contents of the invention [0003] The object of the present invention is to provide a keyboard that can lock the screen with one key. The keyboard can control the screen lock of the display screen with one key, which is very convenient and quick. [0004] The invention includes a keyboard, and the adopted technical solution is that: the keyboard is provided with a control switch at the side end, which can lock the screen with one key. [0005] The beneficial effects of the present invention are:...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06F3/02
CPCG06F3/0227G06F21/84
Inventor 杨鹏宇
Owner XIANGYANG NO 42 MIDDLE SCHOOL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com