Method for preventing network attack performed by using legal data or tampering legal data
A legal data and network attack technology, applied in the field of network security, can solve problems such as calculation theory difficulties, achieve the effect of protecting network and server resources, ensuring timeliness, and preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
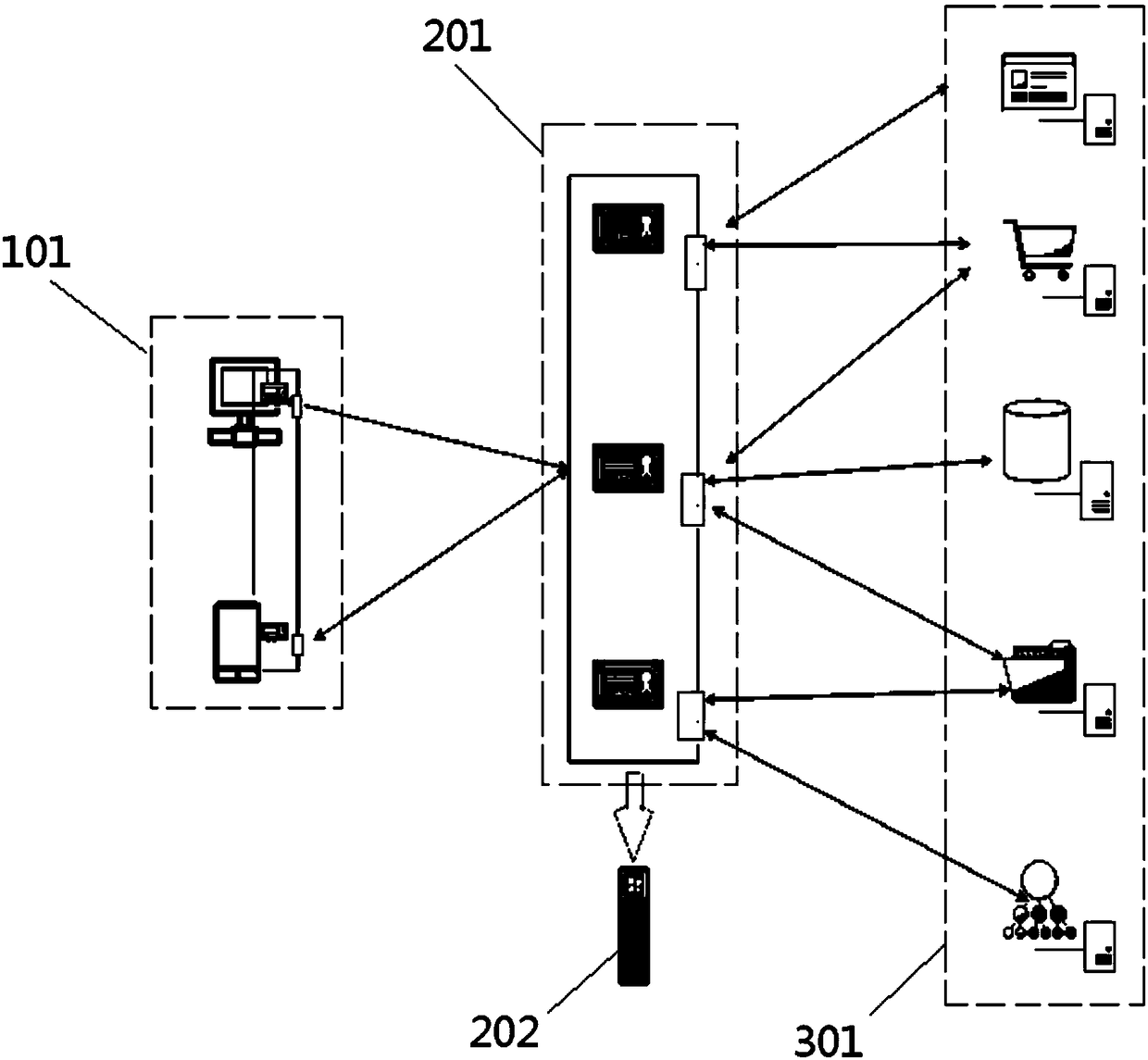
[0031] A method to prevent attacks using legal data or tampering with legal data, which can be used in Internet of Things (ipp) projects, launcher projects and other mobile terminal and cloud access, such as figure 2 As shown, in this embodiment, it is mainly applied to an Internet of Things project including various application services 301 .
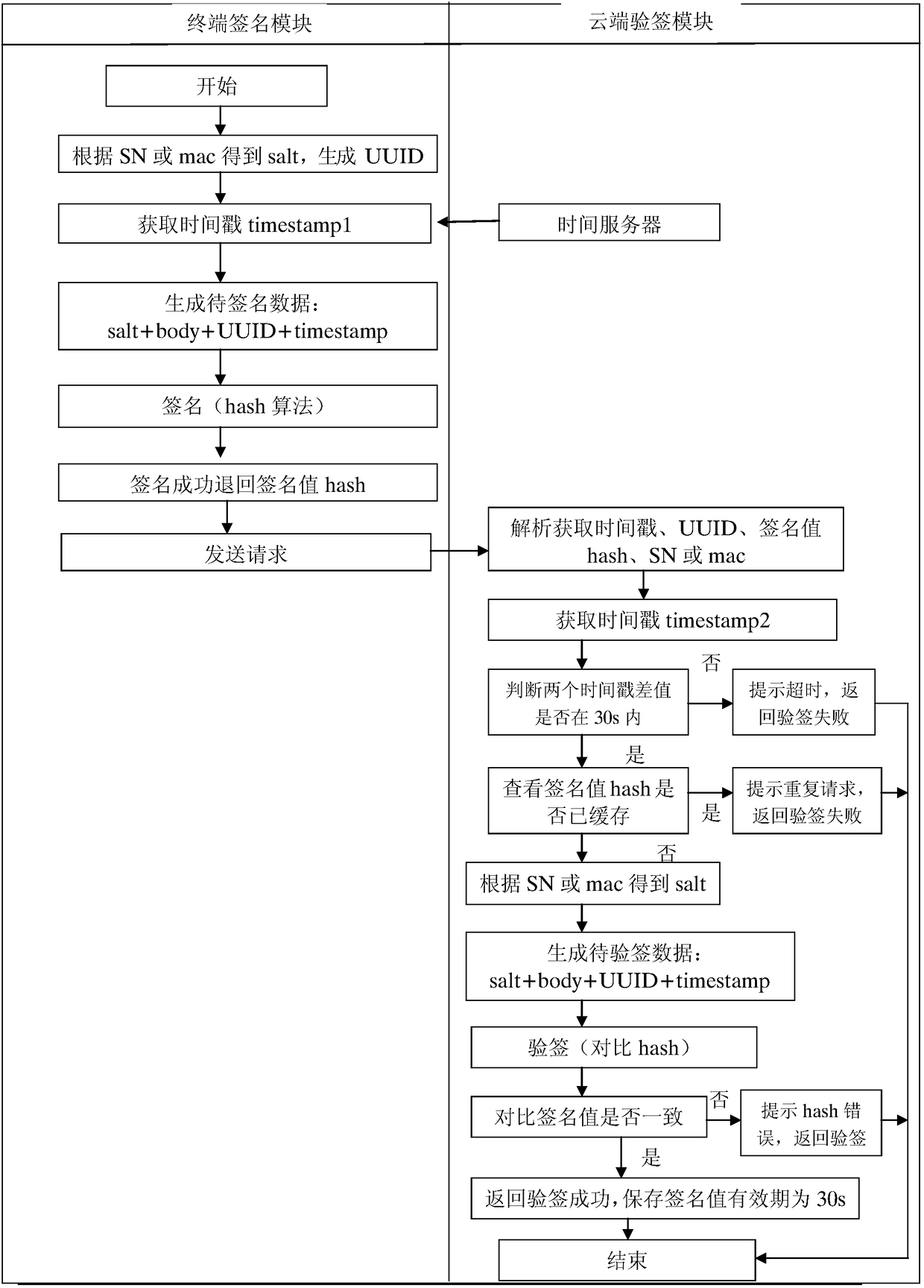
[0032] Such as figure 1 As shown, the method for preventing attacks using legal data or tampering with legal data is mainly implemented by two modules: a terminal signature module 101 and a cloud signature verification module 201, wherein these two modules have the following functions respectively :
[0033] Terminal signature module 101: the main function is to add timestamp timestamp, non-repetitive random number, such as uuid, salt value salt agreed between the terminal and the cloud to the business data body sent by the business terminal, and perform hash algorithm on the combined data, Get the hash value; among them, the salt v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com