Semi-supervised intrusion detection method combining improved Grey Wolf algorithm
An intrusion detection and semi-supervised technology, applied in the field of network information security, can solve the problems of low solution accuracy, difficulty in coordinating the exploration and development capabilities of the wolf algorithm, and achieve the effect of high detection accuracy and guaranteed detection accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
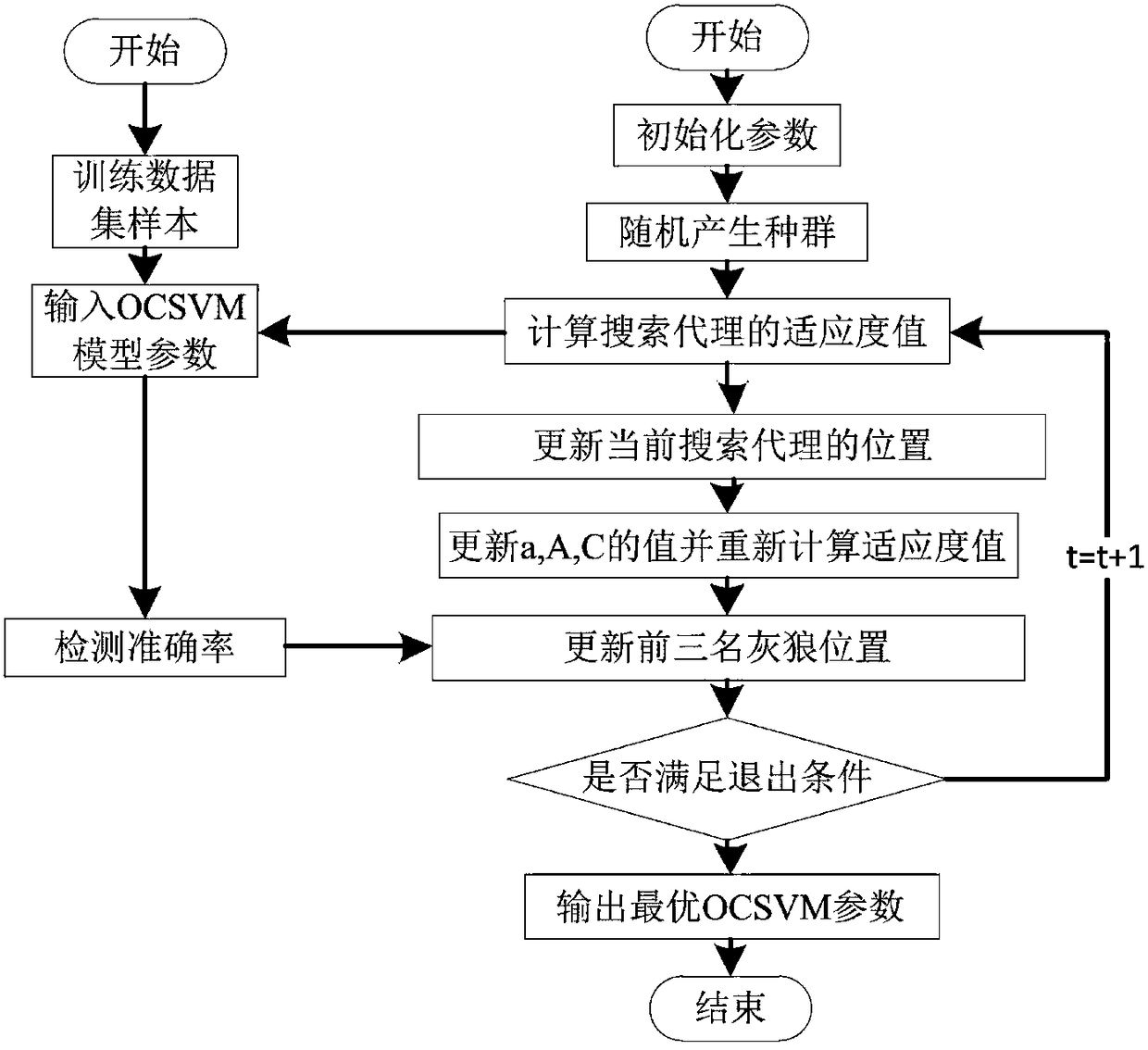
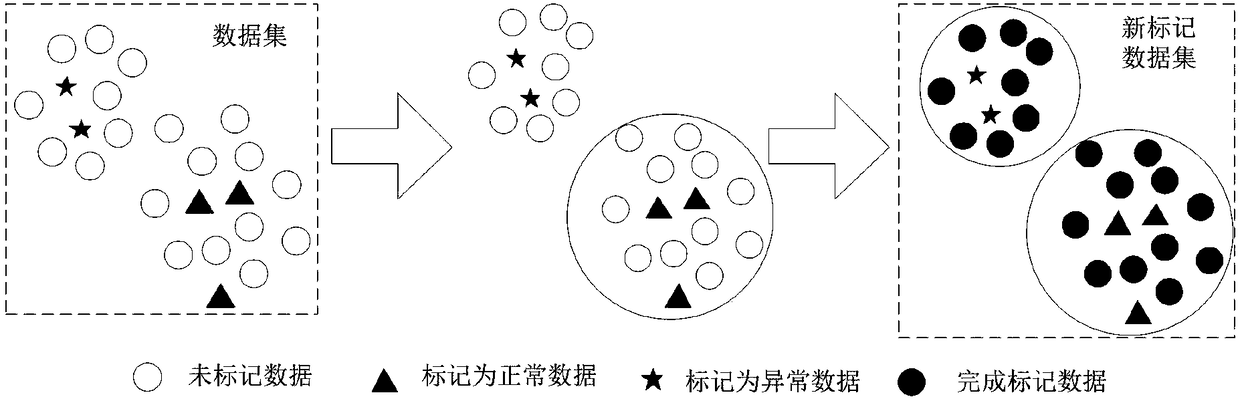
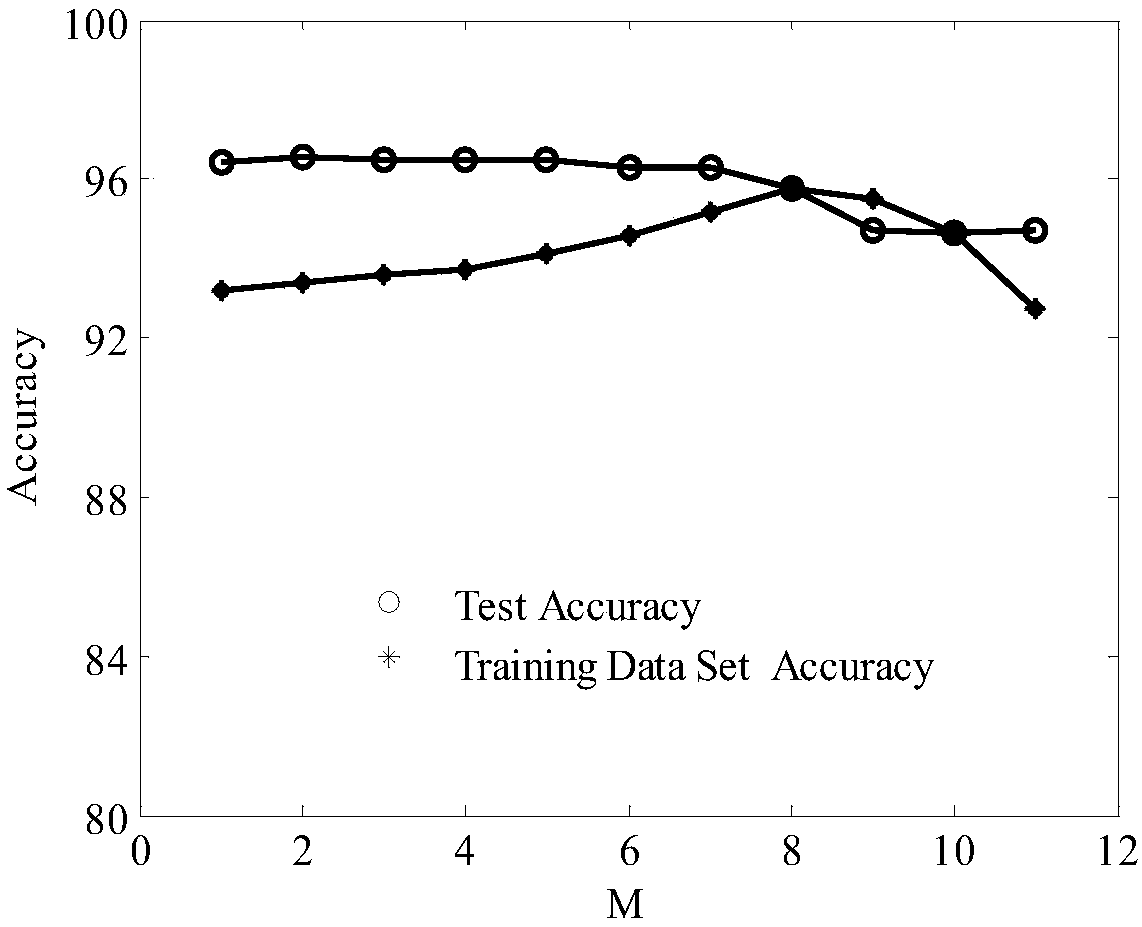
[0034] In order to solve the difficulty in adaptively selecting the characteristics of unknown attack traffic in the industrial control network, and the time-consuming and labor-intensive training data sets of a large number of accurately marked, the present invention adopts the cloud gray wolf algorithm to optimize the semi-supervised learning method of the K-means clustering center, using a small amount of Correctly mark the samples to generate a large-scale training data set, and then use the cloud gray wolf algorithm to optimize the parameters of the single-class support vector machine to more efficiently detect unknown attacks.
[0035] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0036] Step 1: Combine the basic GWO algorithm with the cloud model algorithm, optimize the control parameters of the GWO algorithm, and obtain the cloud GWO algorithm, so that it can obtain a larger search area and increase its ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com