Application permission processing method, terminal and server
A processing method and a technology of application permissions, applied in the field of information processing, can solve problems such as indeterminate permission applications, privacy data leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
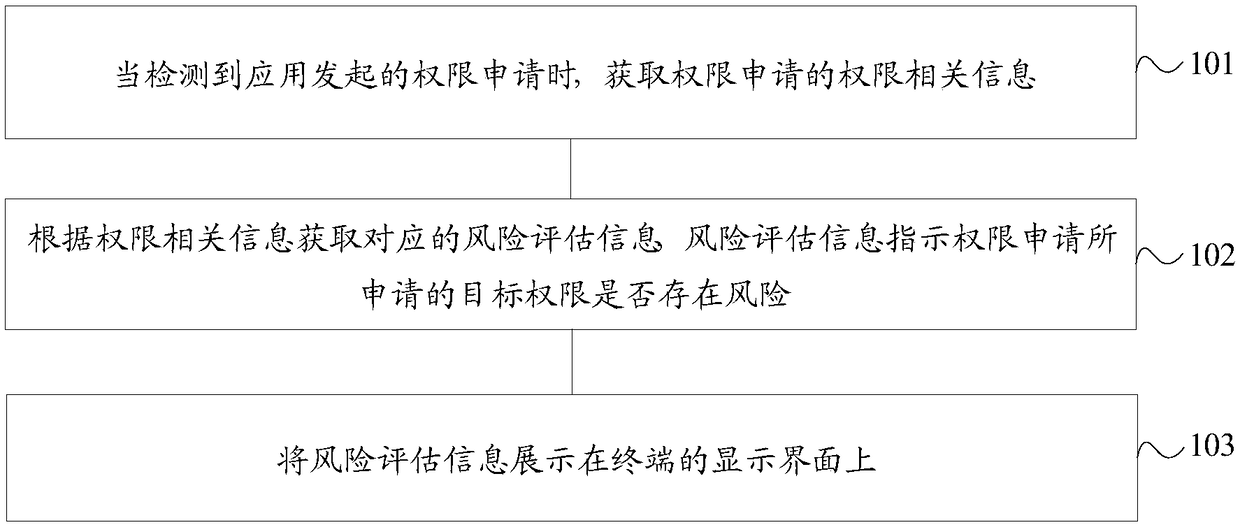
[0041] figure 1 It is a flow chart of an application authority processing method according to an embodiment of the present invention. figure 1 The shown application permission processing method is applied to the terminal, and the method includes:
[0042] Step 101. When detecting a permission application initiated by an application, obtain permission-related information of the permission application.
[0043] Existing operating systems such as the Android operating system have become the main targets of malicious application software. Malicious application software will induce users to abuse permissions. Obtain the user's private data, and the leakage of private data will pose a threat to the security of the user's private data. For example, a calculator application applies for malicious permissions such as address book permissions to obtain user address book data.
[0044] In order to solve the above problems, an embodiment of the present invention provides a method for pr...
Embodiment 2
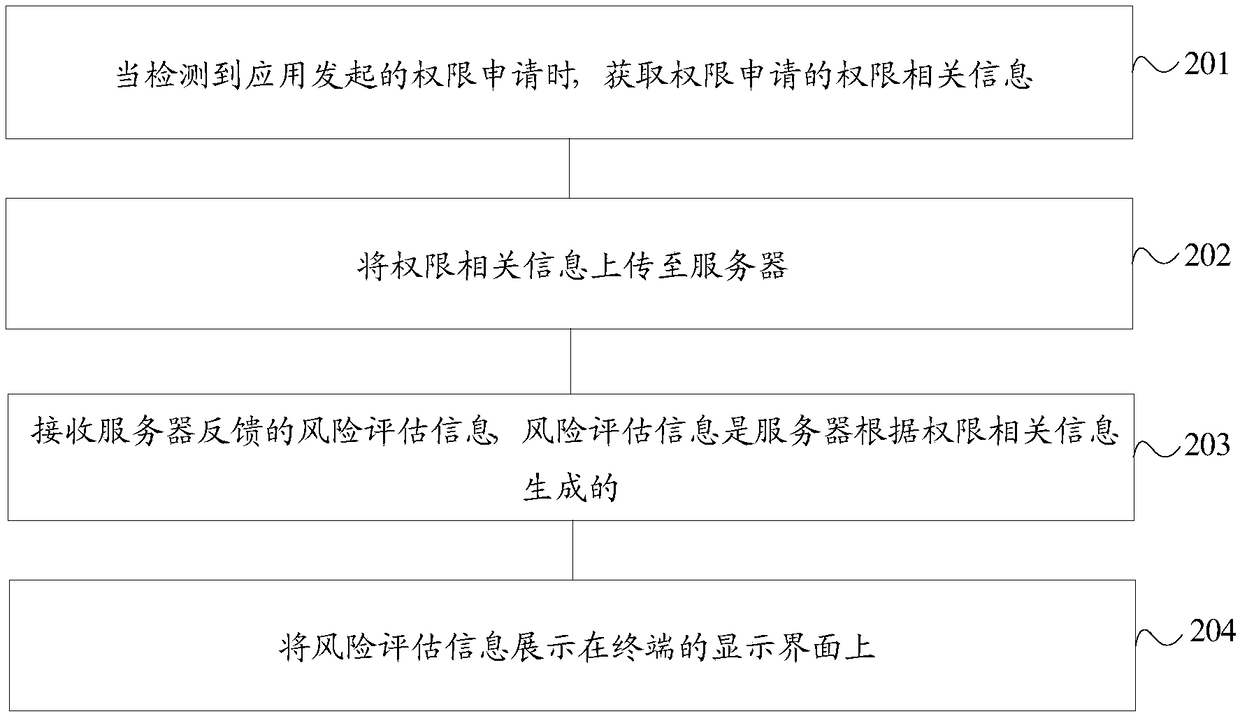
[0070] figure 2 It is a flowchart of an application permission processing method according to another embodiment of the present invention. figure 2 The shown application permission processing method is applied to the terminal, and the method includes:
[0071] Step 201. When detecting a permission application initiated by an application, obtain permission-related information of the permission application.
[0072] For details, refer to the above step 101, which will not be repeated here.
[0073] Step 202, upload the permission-related information to the server.
[0074] After obtaining the permission-related information of the permission application initiated by the application, upload the permission-related information to the server, so that the server generates risk assessment information according to the permission-related information.
[0075] Step 203, receiving the risk assessment information fed back by the server, the risk assessment information is generated by t...
Embodiment 3
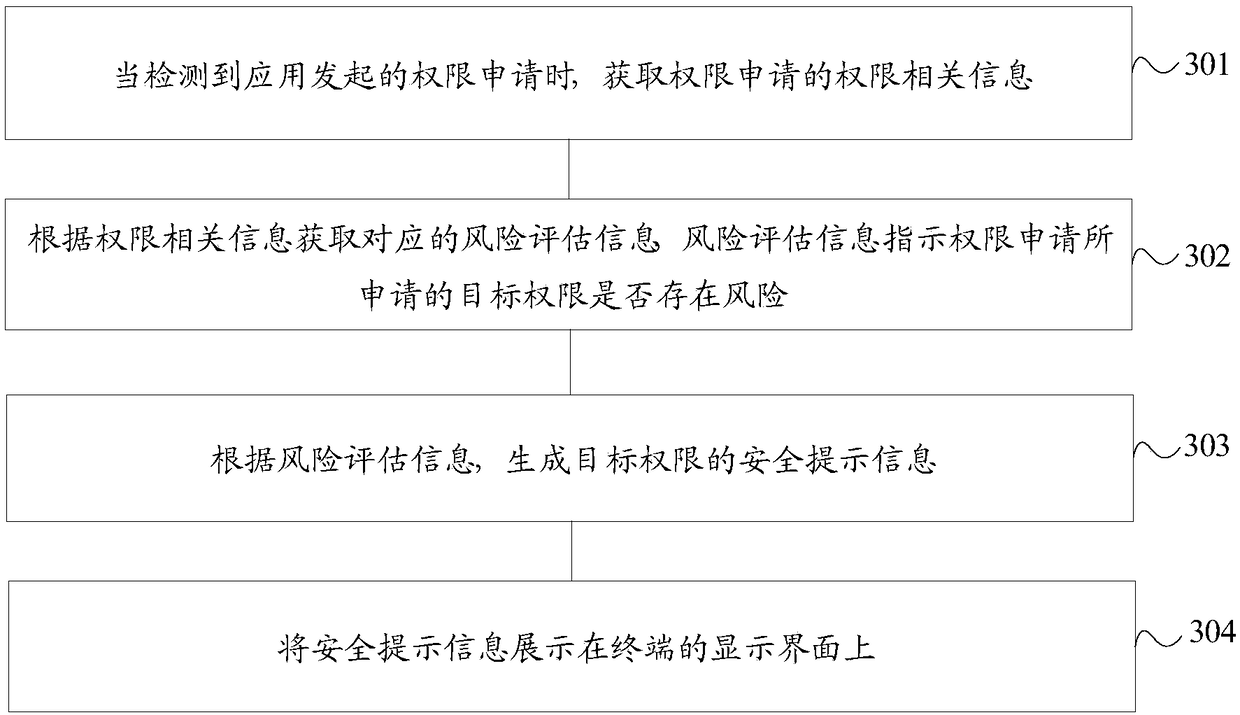
[0098] image 3 It is a flowchart of an application permission processing method according to another embodiment of the present invention. image 3 The shown application permission processing method is applied to the terminal, and the method includes:
[0099] Step 301. When detecting a permission application initiated by an application, obtain permission-related information of the permission application.
[0100] The information content contained in the permission-related information can be various, such as the package name of the application installation package, the identification of the target permission applied for by the permission application, and the scene information for determining the usage scenario of the application when the permission application is initiated. When the permission-related information includes the package name of the application installation package and the identification of the target permission applied for by the permission application, the appl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com