An electronic device and a safety protection method for the electronic device
An electronic device and protected technology, applied in the field of communications, can solve the problems of user privacy data being stolen, users can no longer modify access rights, application access rights can no longer be changed, etc., to achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
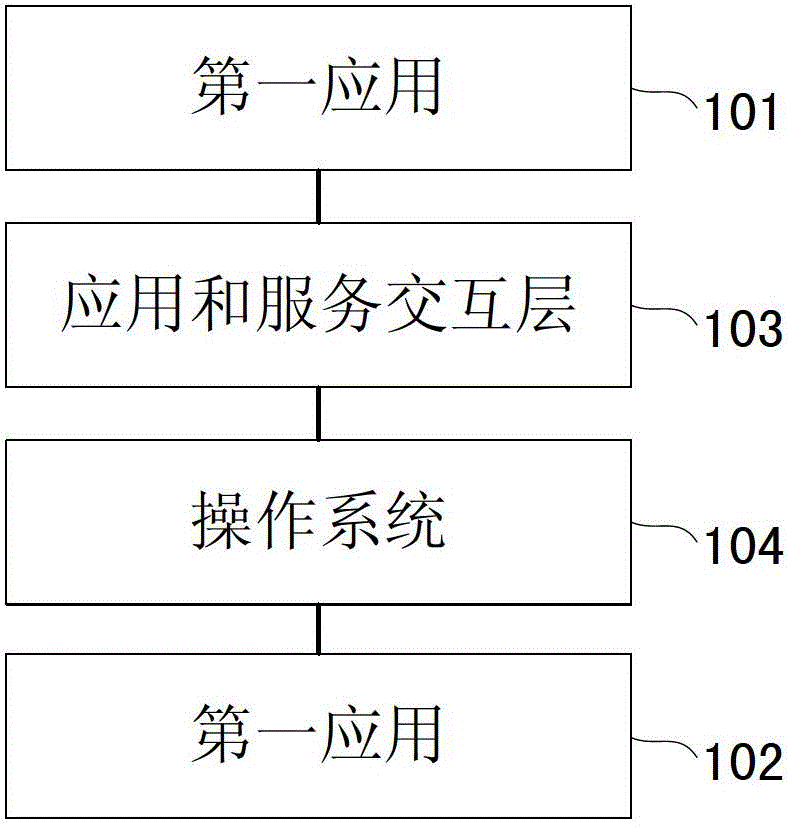
[0047] see figure 1 , showing a schematic diagram of Embodiment 1 of an electronic device of the present invention. The electronic device has at least one application, at least one service, an application and service interaction layer, and an operating system; wherein each of the at least one service corresponds to a service interface for the at least one application to call;
[0048] a first service 101 in the at least one service, used for acquiring first data or executing a first function;
[0049] The first application 102 in the at least one application is configured to call the first service interface of the first service through the application and service interaction layer, and request the first service to obtain the first data or execute the first function;
[0050] The application and service interaction layer 103 is configured to obtain service information called by the first application when the first application calls the first service interface, and determine w...
Embodiment 2
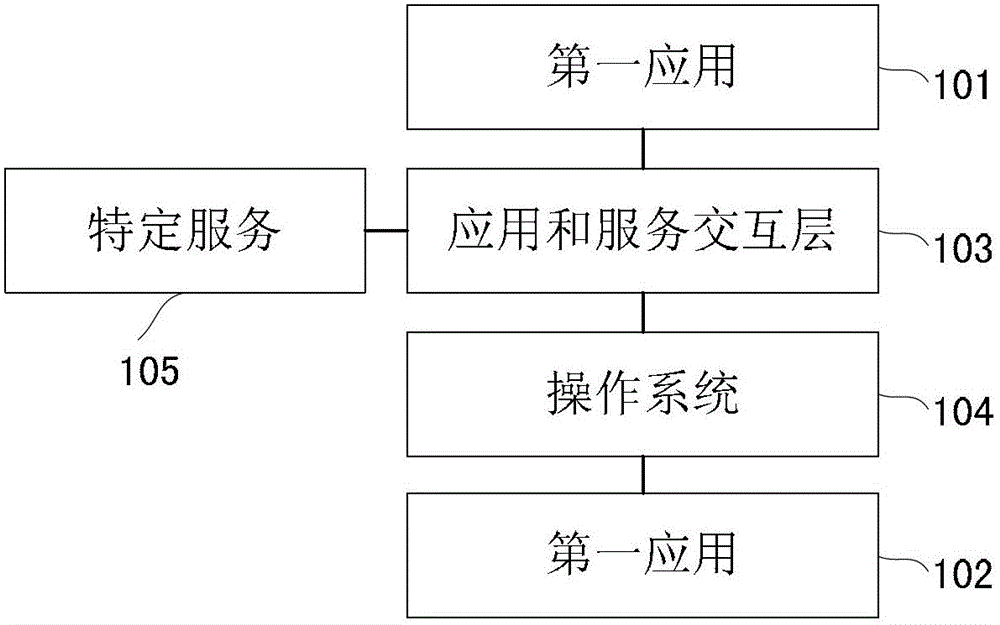
[0069] see figure 2 , showing a schematic diagram of Embodiment 2 of an electronic device of the present invention, and the electronic device further includes:
[0070] A specific service 105 for receiving the user's security settings;
[0071] The application and service interaction layer 103 is specifically configured to judge whether the service invoked by the first application is a protected service by invoking the specific service.
[0072] The electronic device in this embodiment of the present invention may also receive user settings, and after the application is installed, redefine the access authority of the application according to the user's needs, that is, the user's access authorization to the application is no longer simply subject to the application's compulsion After the application is installed, users can authorize access to it according to their own wishes, which provides a technical basis for proactively defending against illegal access to the application....
Embodiment 3
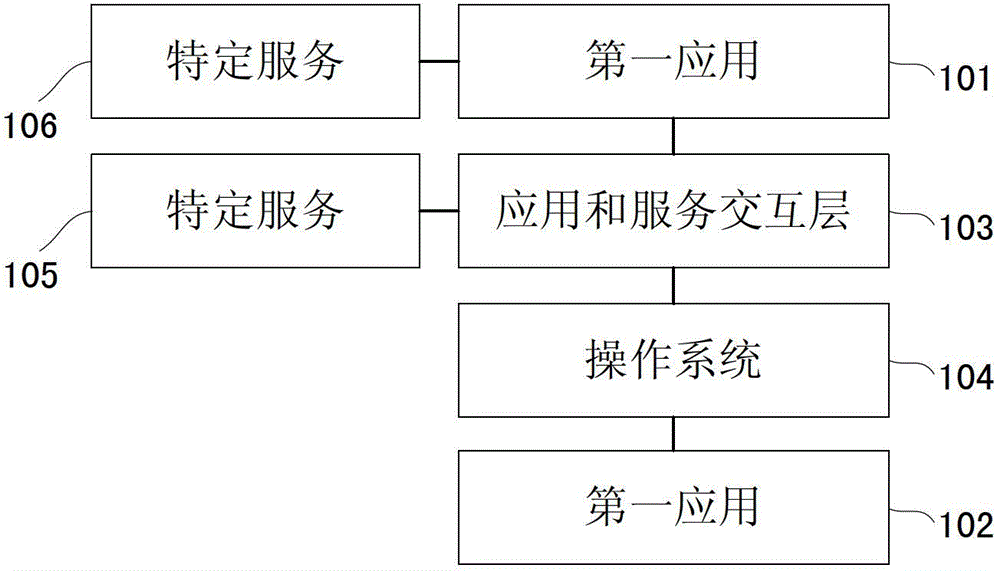
[0074] see image 3 , showing a schematic diagram of Embodiment 3 of an electronic device of the present invention, and the electronic device further includes:
[0075] The service management 105 is configured to receive the request of the first application, and send the first service interface of the first service to the first application.
[0076] The access behavior of the application to the service is realized by calling the service interface of the service. Therefore, before the application initiates access to the service, it needs to know the service interface to be called. The service management stores the information of multiple services and service interfaces of the electronic device, and the application can obtain the service interface to be called by sending a request to the service management.
[0077] In addition, it should be noted that the application and service interaction layer in the embodiment of the present invention may be embodied as a dynamic library I...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com