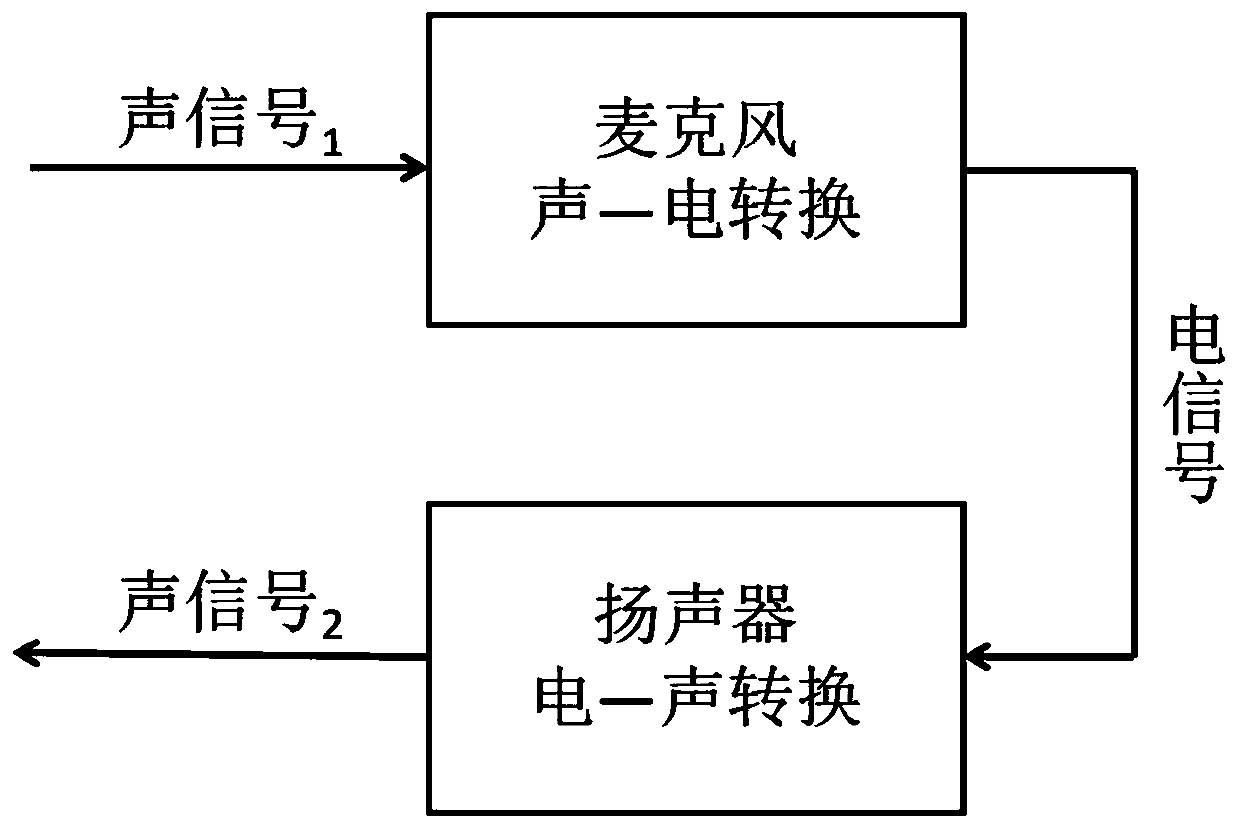
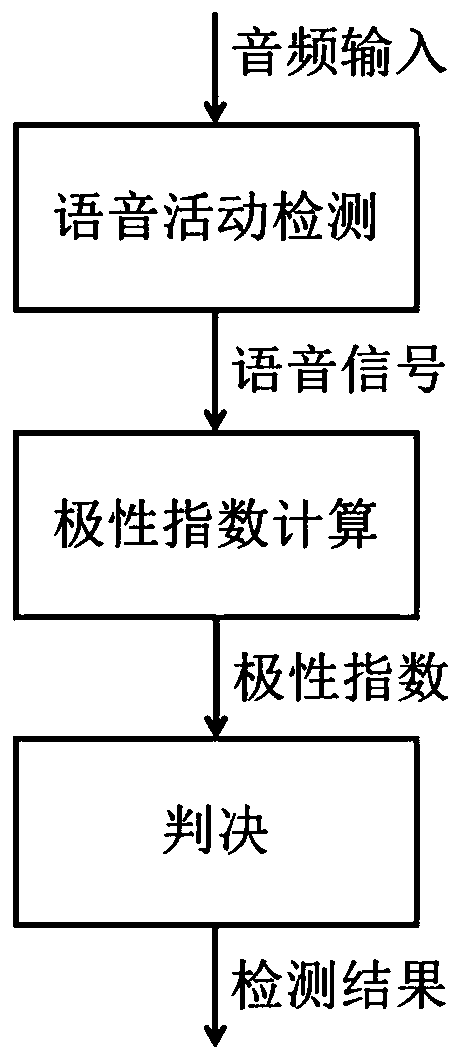
Replay attack detection method of voice certification system
A voice authentication and replay attack technology, applied in the field of voice authentication technology and security, can solve the problems of microphone and speaker quality influence, low detection accuracy, etc., and achieve the effect of simple method, low algorithm complexity, and low delay.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
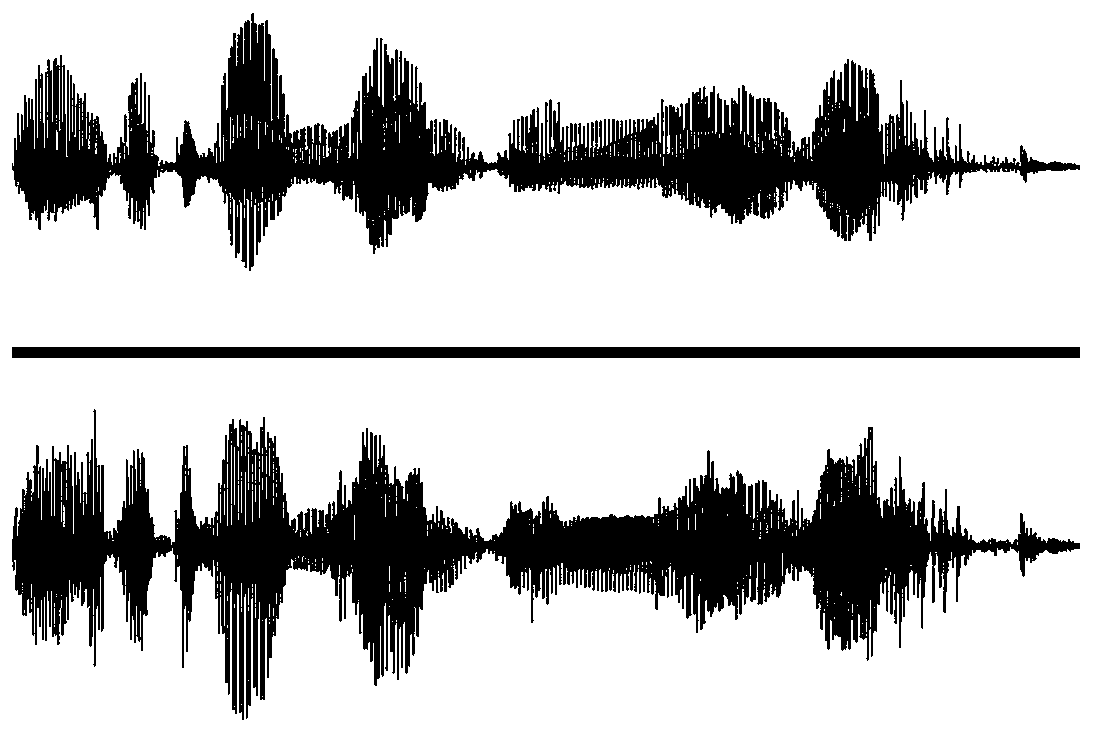
[0048] image 3 Among them, the upper channel is the live authentication voice signal obtained by the voice authentication system, and the lower channel is the voice signal obtained by HiVi audio replay attack. It can be clearly seen that the positive polarity ratio of the live voice signal is much higher than the negative polarity ratio, while the replay attack signal is just the opposite. After the first two steps of the detection method (voice activity detection, polarity index calculation), the polarity index of the live body authentication voice signal can be calculated to be 0.583, which is obviously greater than the polarity index of the replay attack voice signal, which is 0.494.
Embodiment 2
[0050] In this embodiment, the in vivo authentication voices of a total of 20 people (14 men and 6 women) were collected, and 8 kinds of loudspeakers with a wide quality distribution including the aforementioned HiVi audio were used to carry out replay attacks. The judgment threshold is set to 0.52, that is, the speech with a polarity index greater than 0.52 is judged as a live speech. Anyway, when it is judged as a replay attack, the detection accuracy of the live speech is 93.2%, and the detection accuracy of the replay attack is 96.5%.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com