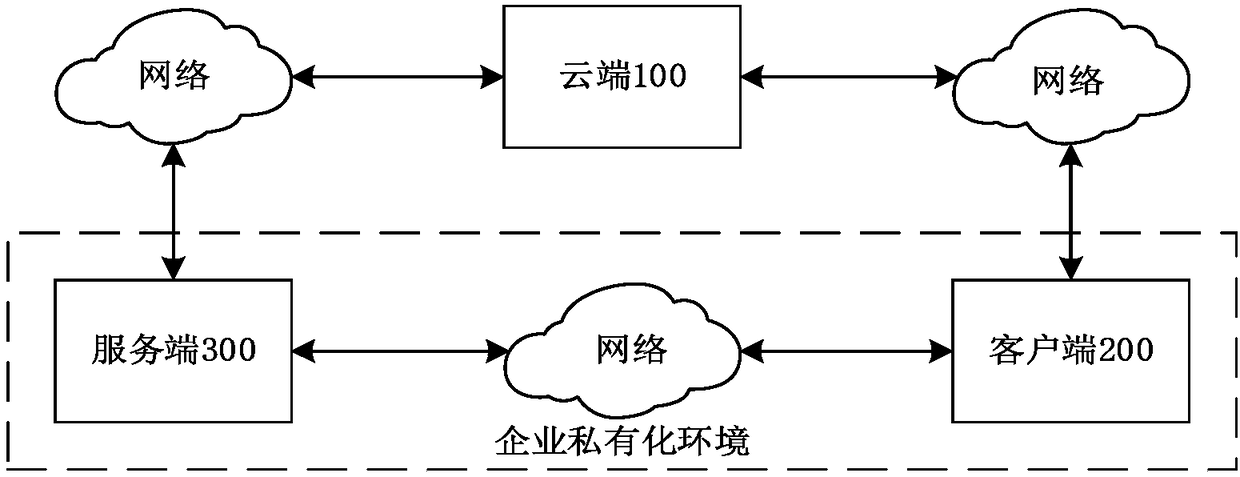
Encryption and decryption method and device
A technology for encrypting, decrypting and encrypting data, applied in the field of encryption and decryption, it can solve the problems of low JavaScript security and security problems, and achieve the effect of avoiding security problems and shortening the effective period.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
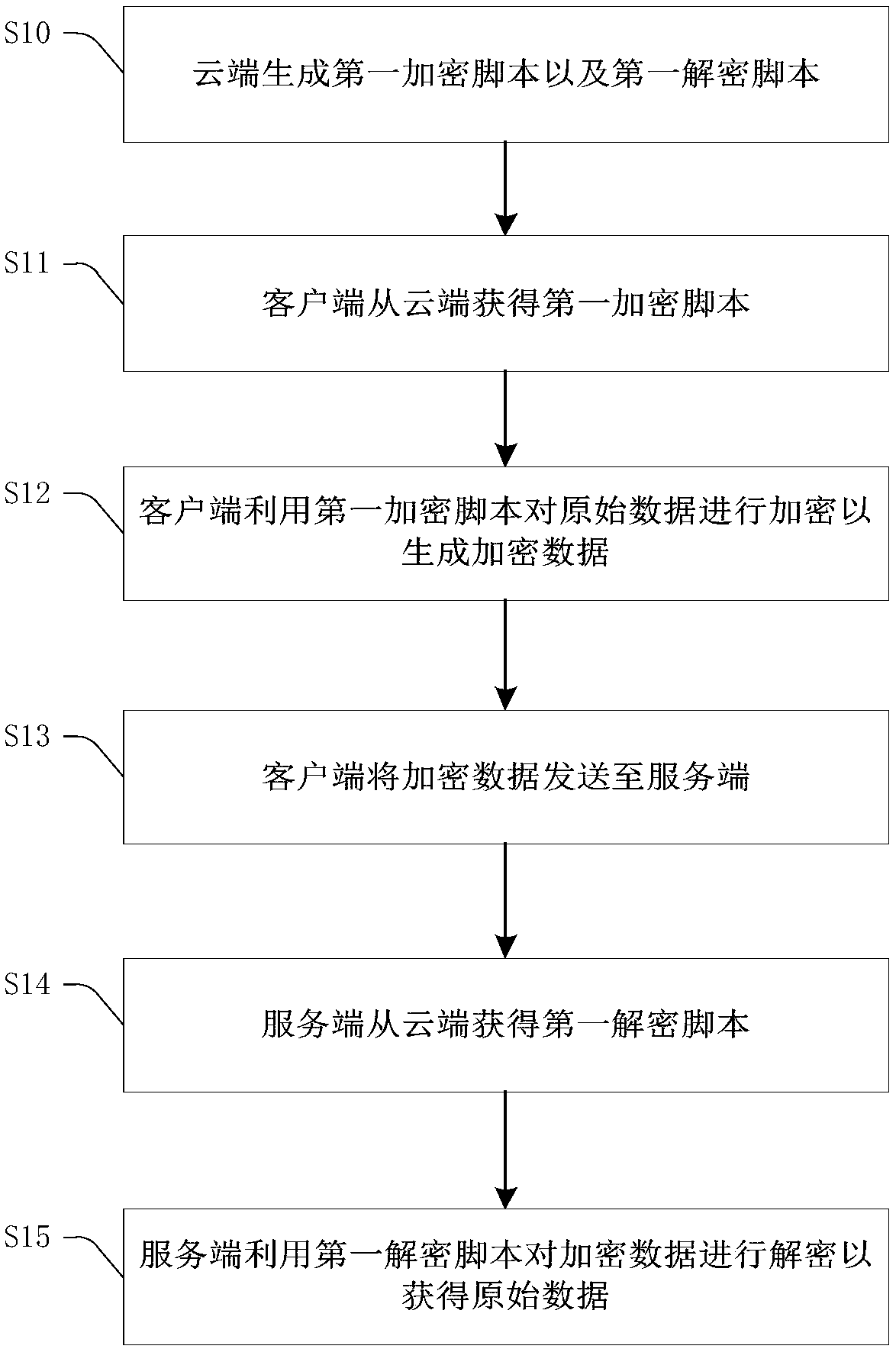
[0059] image 3 A flow chart of the encryption and decryption method provided by the first embodiment of the present invention is shown. refer to image 3 , the encryption and decryption methods include:
[0060] Step S10: the cloud 100 generates a first encrypted script and a first decrypted script.
[0061] The first encryption script is the script used when the client 200 encrypts the original data to generate encrypted data, the first decryption script is the script used when the server 300 decrypts the encrypted data to obtain the original data, the first encryption script and the first The decryption scripts have a mutual matching relationship, that is, the encrypted data generated by the first encryption script can only be decrypted by the first decryption script. Wherein, the first encryption script and the first decryption script are usually javascript scripts, which have the characteristics of being cross-platform and supporting hot update, and of course they can ...
no. 2 example
[0076] Figure 4 A functional block diagram of the encryption and decryption apparatus 500 provided by the second embodiment of the present invention is shown. refer to Figure 4 , the encryption and decryption device 500 provided by the second embodiment of the present invention is applied to the cloud 100 , and includes an encryption script sending module 510 and a decryption script sending module 520 . Wherein, the encrypted script sending module 510 is used to send the first encrypted script to the client 200, and the first encrypted script is used to encrypt the original data to generate encrypted data; the decrypted script sending module 520 is used to send the encrypted script corresponding to the first encrypted script The matching first decryption script is sent to the server 300, and the first decryption script is used to decrypt the encrypted data.
[0077] The encryption and decryption device 500 provided in the second embodiment of the present invention, its imp...
no. 3 example
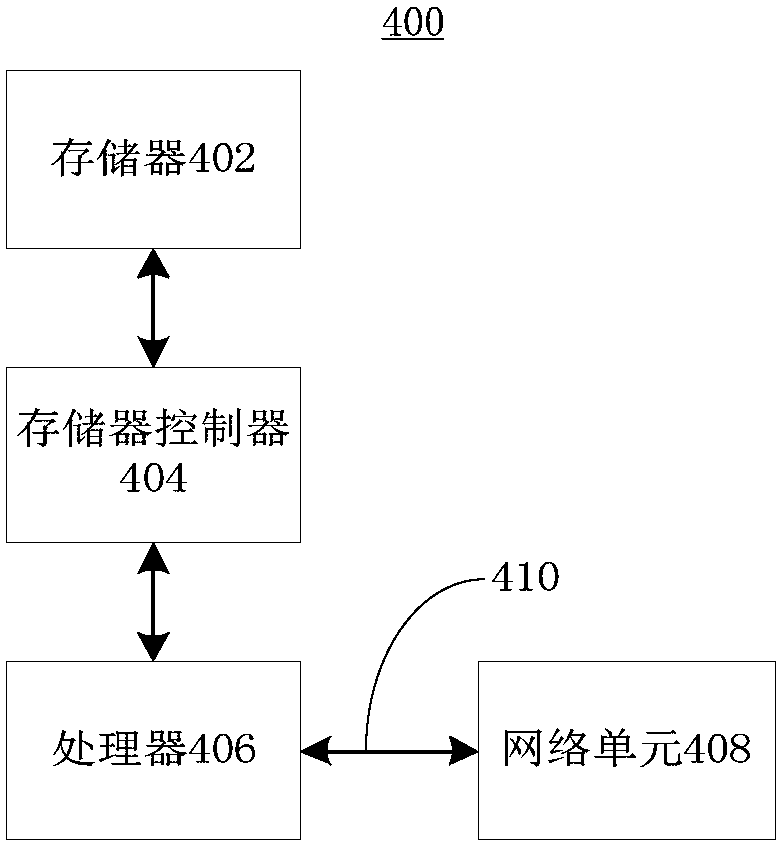
[0079] The third embodiment of the present invention provides a computer storage medium. Computer program instructions are stored in the computer storage medium. When the computer program instructions are read and run by the processor of the computer, the method provided in the first embodiment of the present invention is executed. The part executed on the cloud 100. The computer storage medium can be implemented as, but not limited to figure 2 Memory 402 is shown.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com