Malicious number mark recognition method based on block chain
An identification method and block chain technology, applied in block chain applications and mobile Internet security fields, can solve problems such as data tampering, personal information being stolen, and data authenticity cannot be guaranteed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to make the purpose, technical solution and advantages of the present invention clearer, the embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
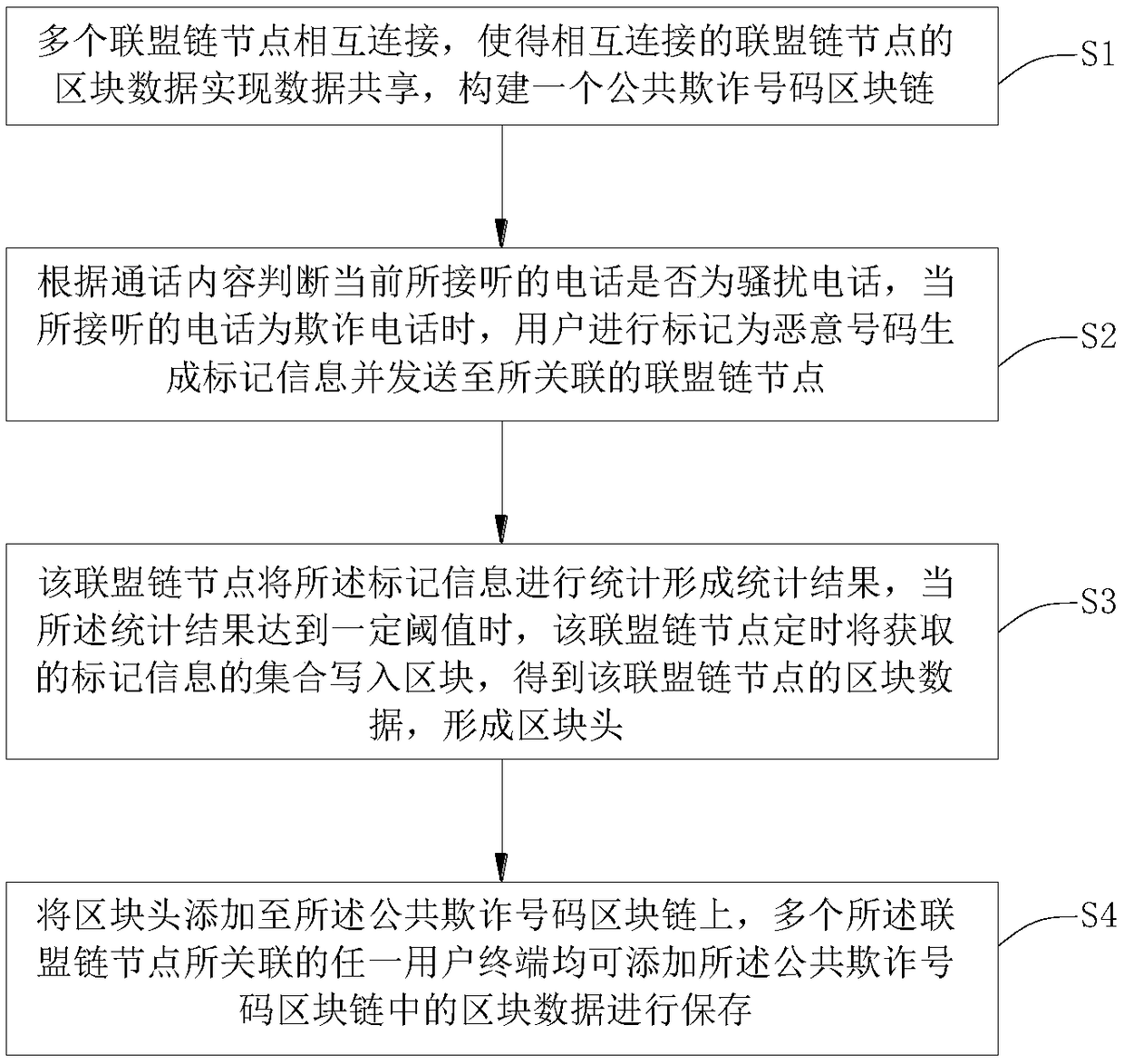
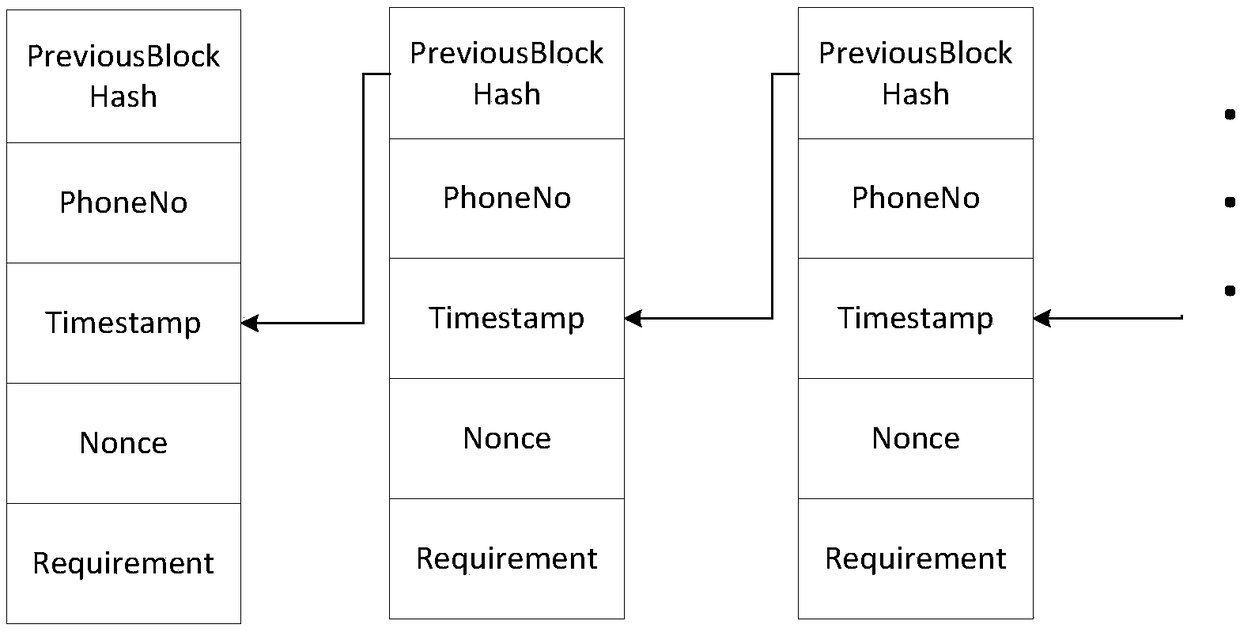
[0020] Please refer to figure 1 with figure 2 , the embodiment of the present invention discloses a method for identifying a malicious number mark based on blockchain, including several alliance chain nodes, each of which has block data stored in the alliance chain nodes, and at least two of the alliance chain nodes Connect to each other, and make the block data of the connected alliance chain nodes realize data sharing, and build a public fraud number blockchain.
[0021] After the user connects a call, judge whether the call received by the current mobile phone is a fraudulent call according to the content of the call. When the received call is a fraudulent call, the user will mark it as a malicious number to generate marking information and send it ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap