Image protection method and device, and image restoring method and device
An image restoration and image technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of image content leakage, encrypted image interception or breach, low image security, etc., and achieve the effect of increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
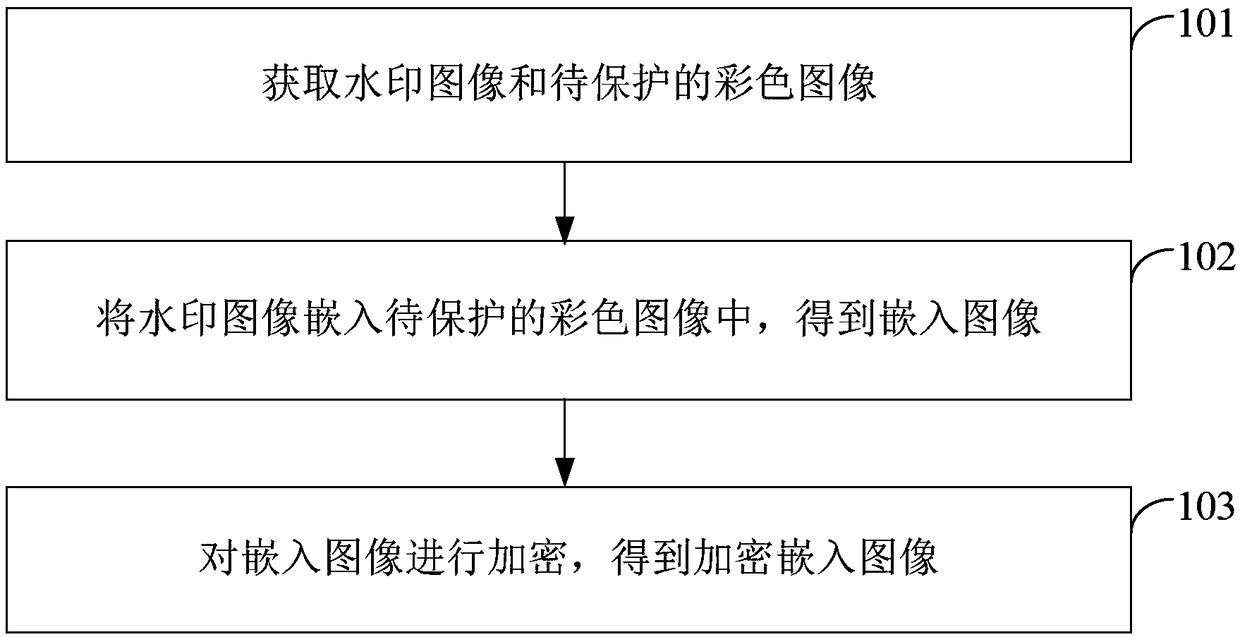
[0058] see figure 1 , the embodiment of the present invention provides an image protection method, the method specifically includes the following steps:
[0059] Step 101: Obtain a watermark image and a color image to be protected.
[0060] The color image to be protected is an image that is important to the user and needs to be protected from leakage. The watermark image can be an image that can represent personal identity features or biological features, such as a fingerprint image or a face map. The executive subject of the embodiment of the present invention is a terminal for image protection, which receives the color image to be protected and the watermark image submitted by the user, and then embeds the watermark image into the color image to be protected through the operations of steps 102 and 103 and encrypts the image , in order to achieve the purpose of multiple protection for the color image to be protected.
[0061] Step 102: Embedding the watermark image into t...
Embodiment 2
[0118] see Figure 4 , the embodiment of the present invention provides an image restoration method, the method is used to restore the color image to be protected from the encrypted embedded image generated by the image protection method provided in the above embodiment 1, the restoration process is provided by the embodiment 1 The reverse process of the image protection process. The method specifically includes the following steps:
[0119] Step 201: Obtain an encrypted embedded image corresponding to the color image to be protected.
[0120] Receive the encrypted embedded image corresponding to the color image to be protected submitted by the user, or receive the encrypted embedded image corresponding to the color image to be protected sent by other terminals.
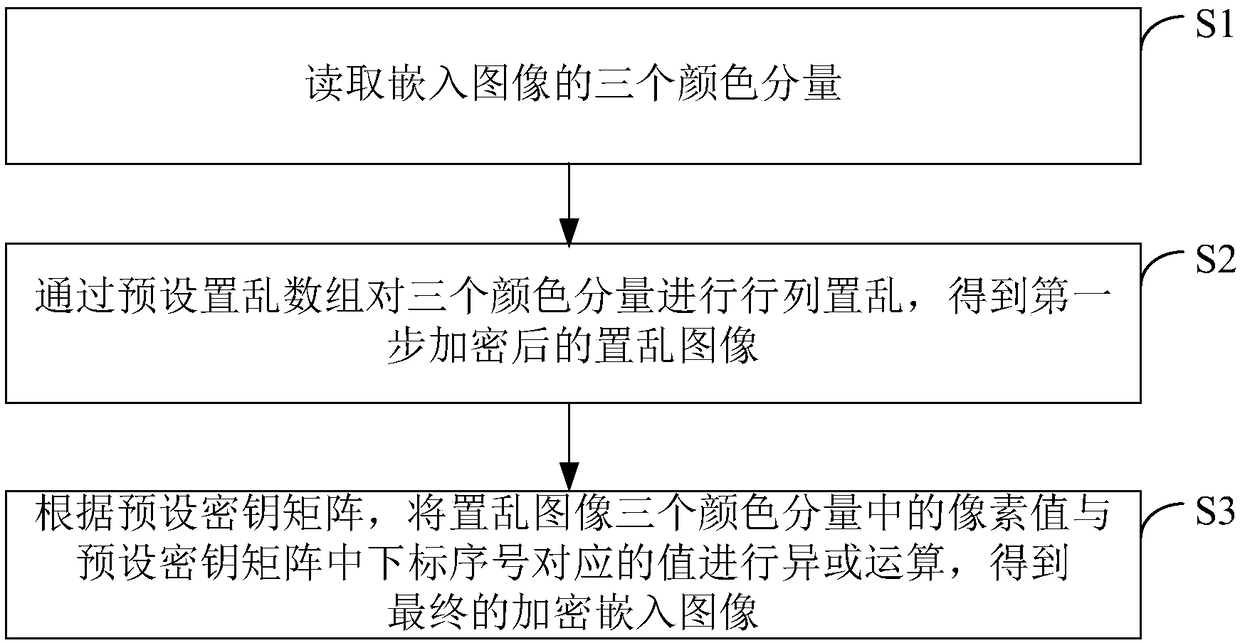
[0121] Step 202: Decrypt the encrypted embedded image to obtain the embedded image corresponding to the color image to be protected.
[0122] In the embodiment of the present invention, the encrypted embedded imag...
Embodiment 3
[0158] see Figure 6 , the embodiment of the present invention provides an image protection device, the device is used to implement the image protection method provided in the above-mentioned embodiment 1, the device includes:
[0159] An acquisition module 30, configured to acquire watermarked images and color images to be protected;
[0160] The embedding module 31 is used to embed the watermark image in the color image to be protected to obtain the embedded image;
[0161] The encryption module 32 is configured to encrypt the embedded image to obtain the encrypted embedded image.
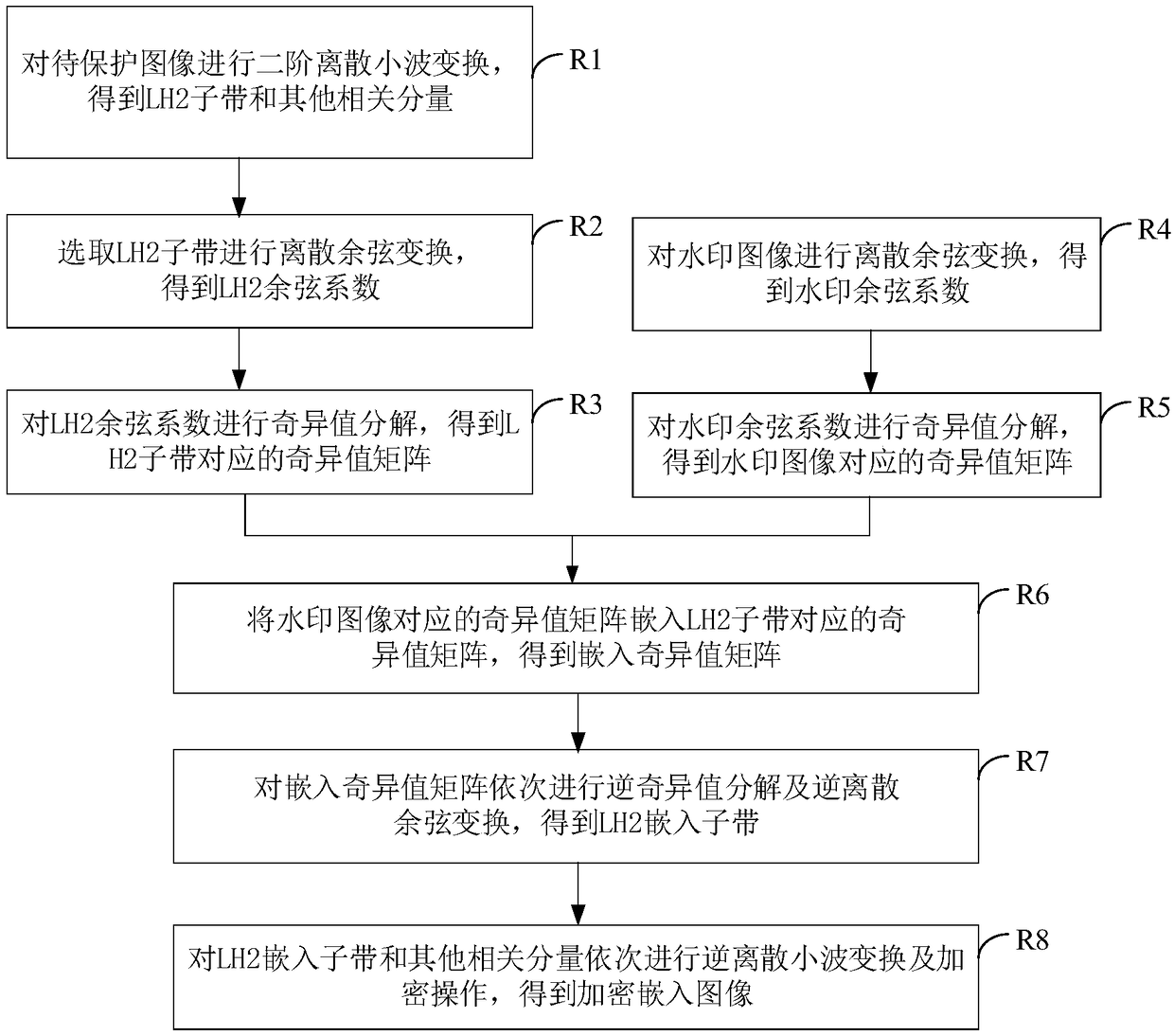
[0162] Above-mentioned embedded module 31 comprises:
[0163] Decomposition unit for decomposing LH2 subbands and other related components from the color image to be protected;
[0164] An embedding unit, configured to embed the watermark image into the LH2 subband;
[0165] The merging unit is used to perform inverse wavelet transform according to other related components of the secondary wa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com