Malicious code confusion detection method and system, computer device, and medium
A malicious code and detection method technology, applied in the field of computer software, can solve problems such as single detection technology, difficulty in accurately analyzing malicious code, obfuscation and anti-detection capability, and unreasonable detection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only some, not all, embodiments of the present invention. Based on the embodiments of the present invention, all other embodiments obtained by persons of ordinary skill in the art without making creative efforts belong to the protection scope of the present invention.
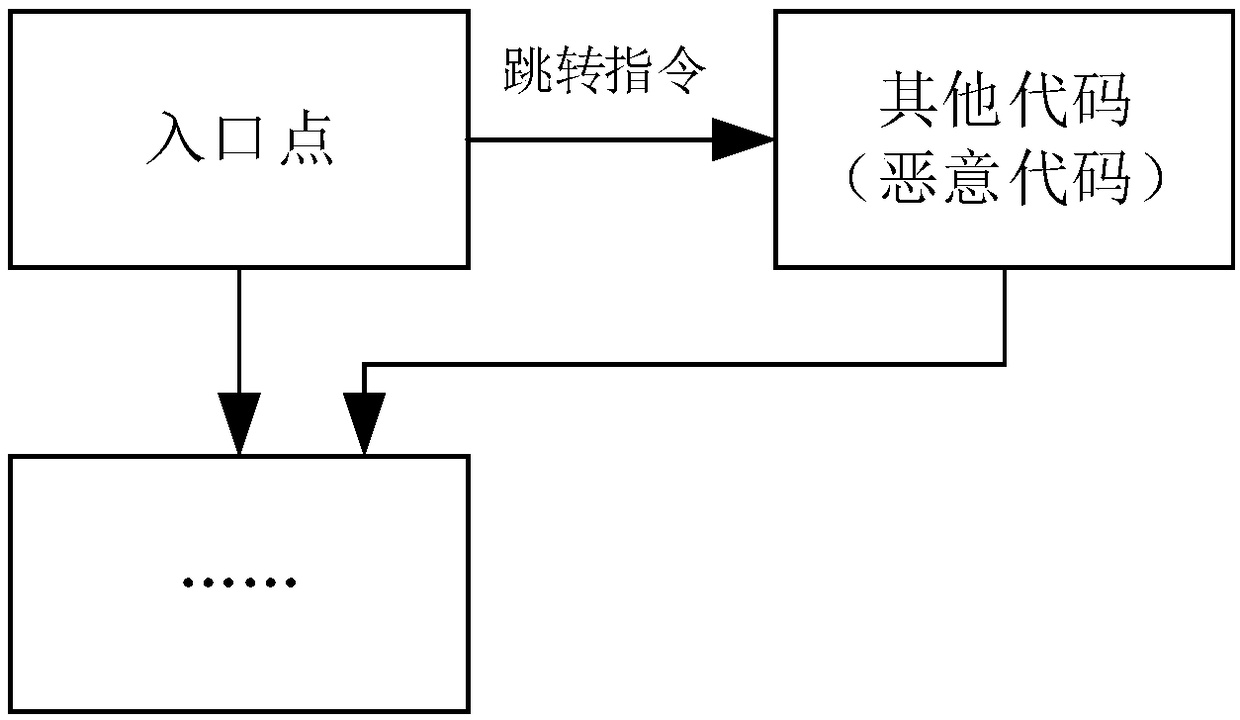
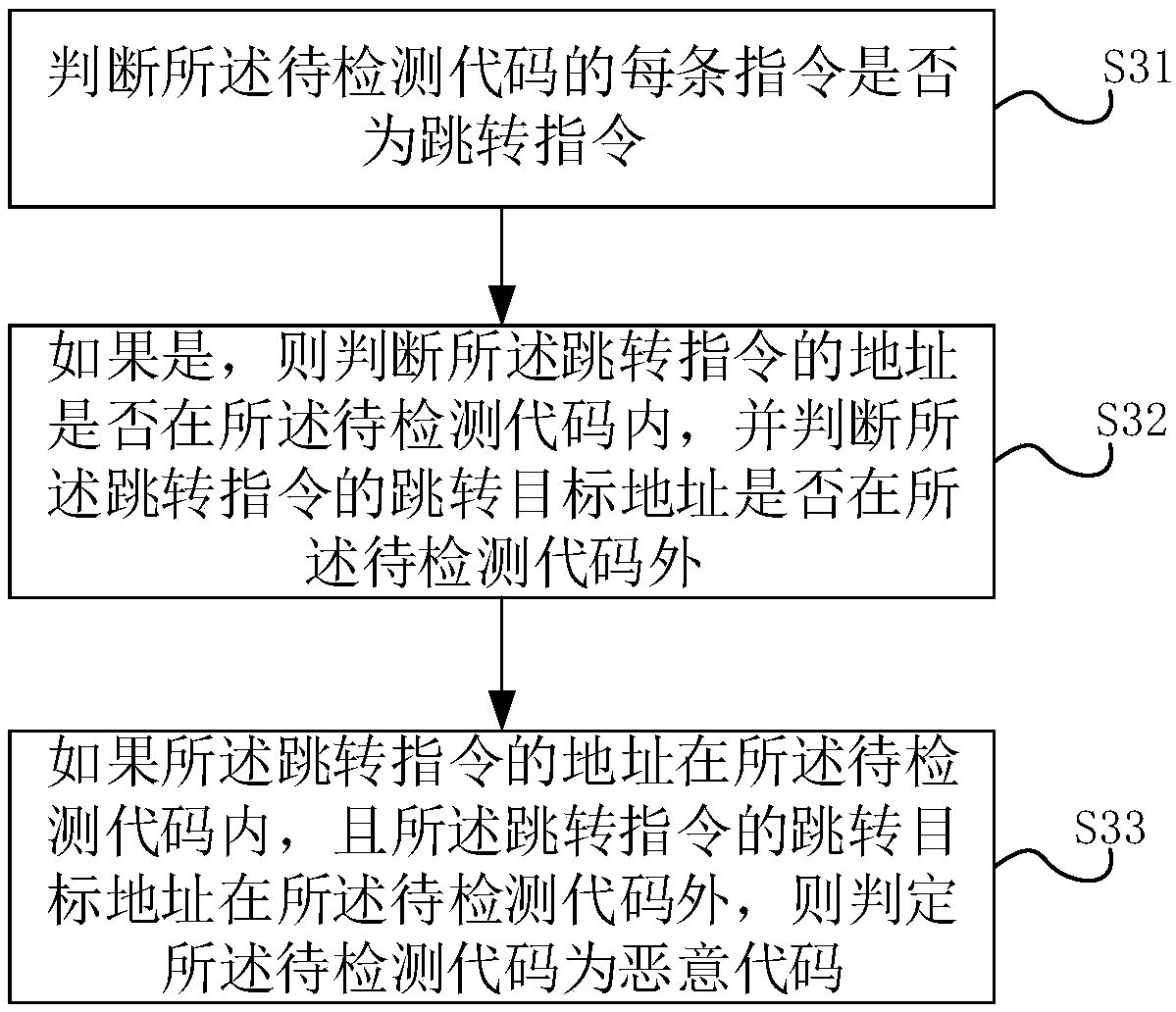
[0071] Please refer to figure 1 , figure 1 It is a flowchart of a malicious code obfuscation detection method provided by a specific embodiment of the present invention.
[0072] In a specific implementation manner of the present invention, the embodiment of the present invention provides a malicious code obfuscation detection method, including:
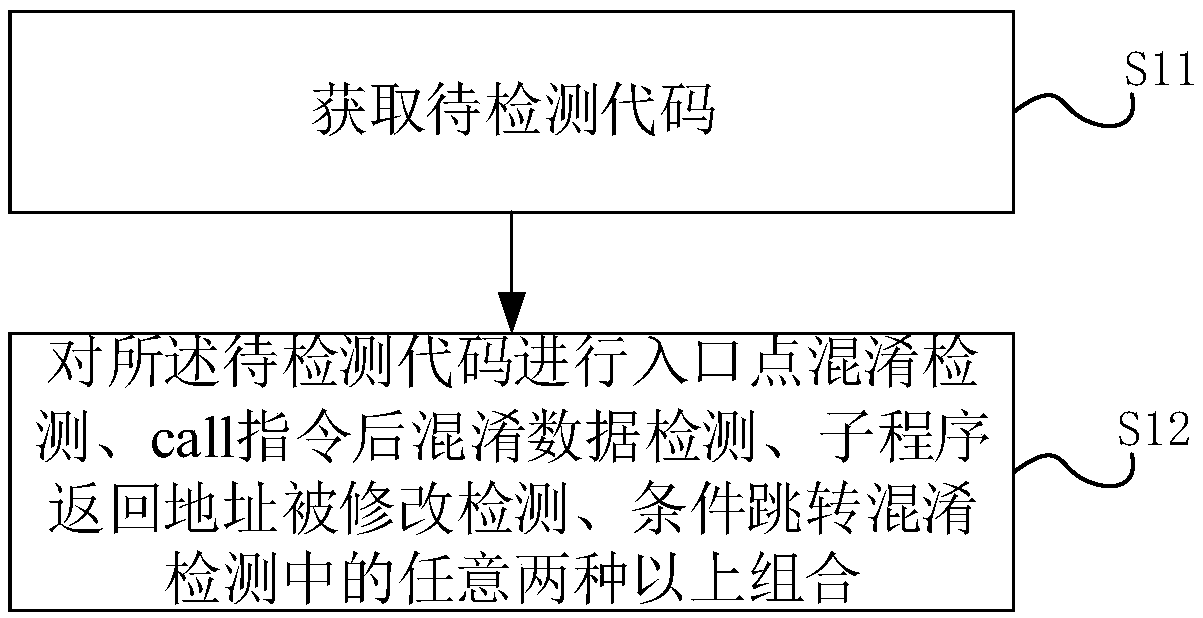
[0073] S11: Obtain the code to be detected;
[0074] S12: Perform any combination of two or more of entry point...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap