Attack tree-based intelligent network connection vehicle information security event occurrence probability evaluation method and system
A technology for the occurrence of probability and security events, applied in computer security devices, instruments, electrical digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
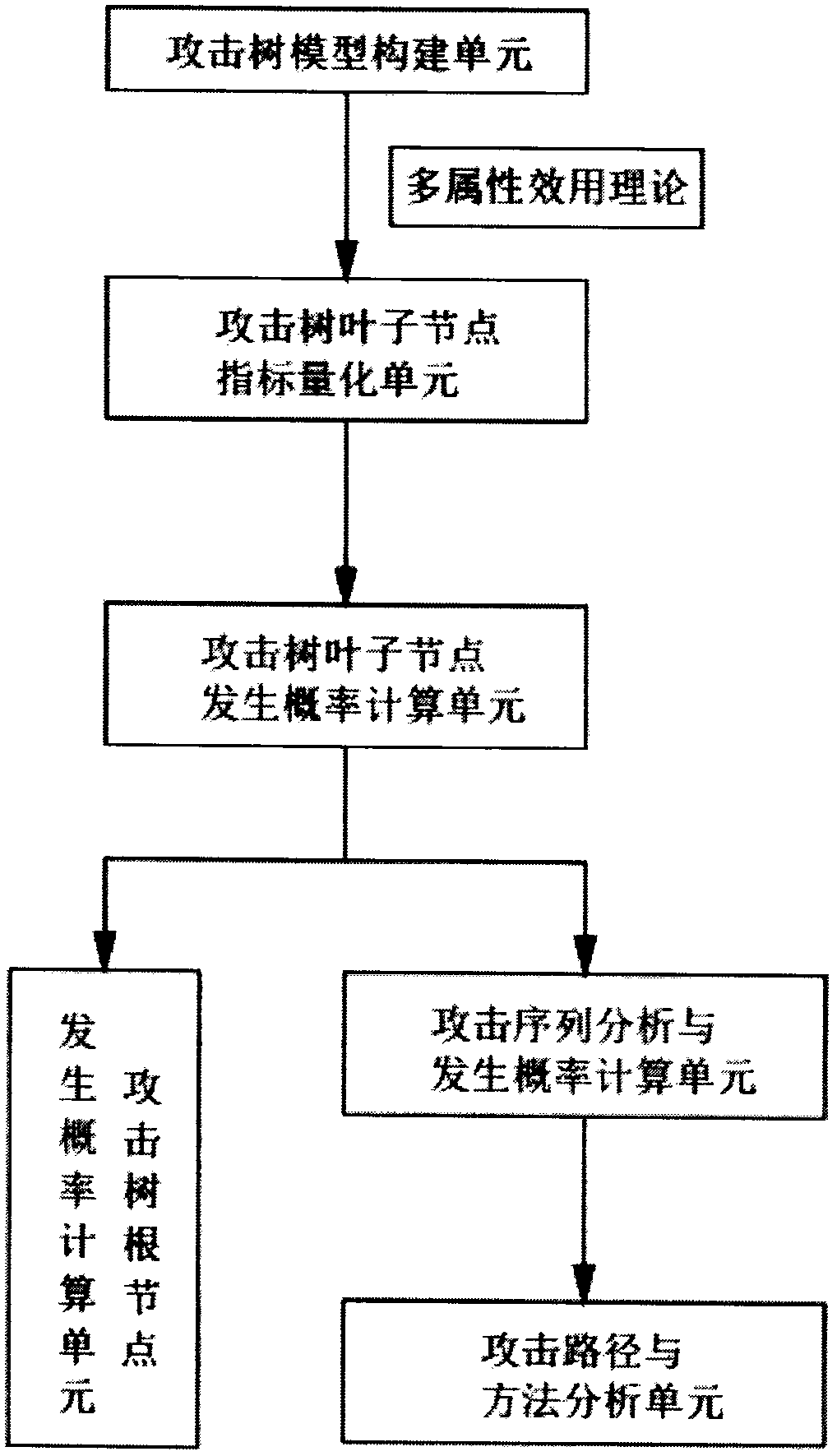
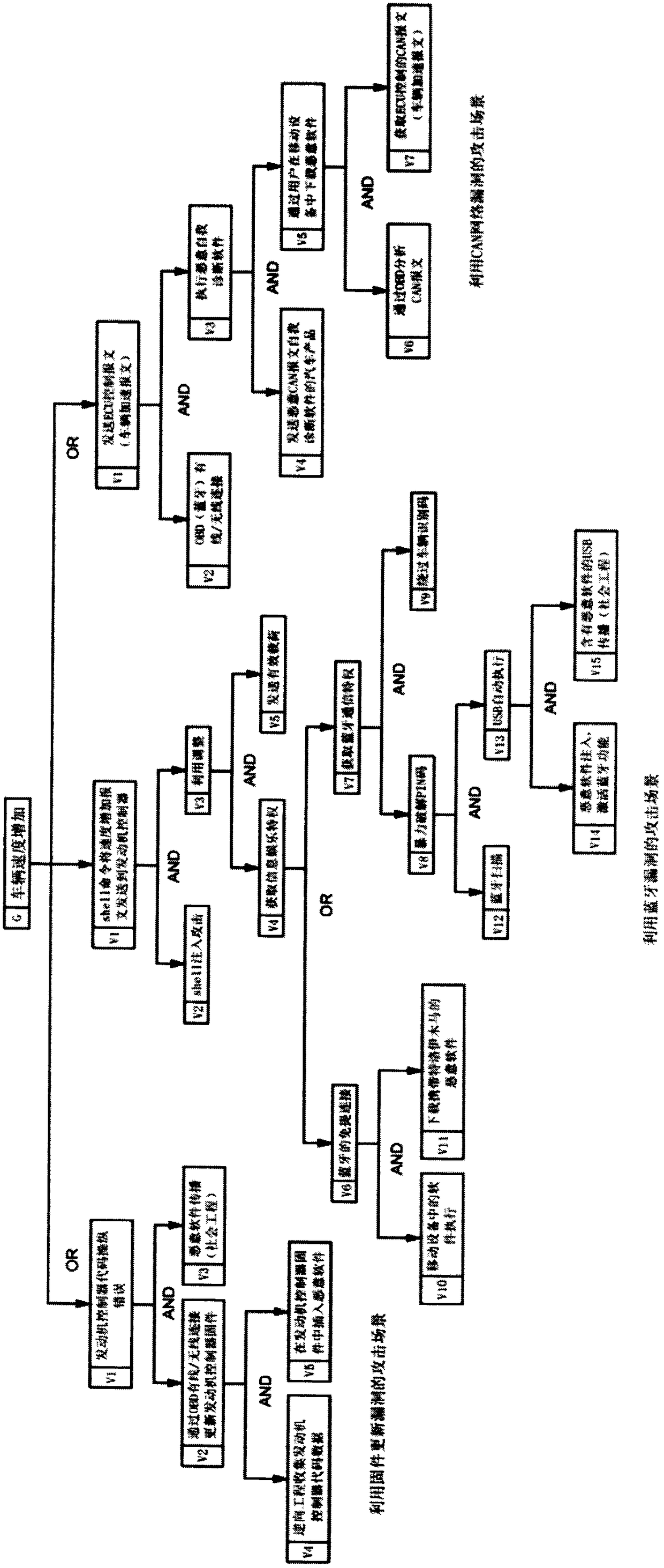
[0039] Such as figure 1 As shown, the embodiment of the present invention provides an attack tree-based method for evaluating the probability of occurrence of information security incidents of intelligent networked vehicles. In this method, the attack tree analysis method is used to calculate the probability of occurrence of information system security incidents for the service cases of intelligent networked vehicles. , analyze the attack sequence of the attack tree, and use the multi-attribute utility theory to calculate the probability of the root node and each attack sequence being subjected to information attack risks, reveal the most risky attack path in the system attack tree, and determine the most risky attack path when formulating protection measures for the system. Attacks that should be prevented. The steps to assess the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com