Security protection methods, devices and system
A security protection and security gateway technology, applied in the field of network security, can solve problems such as illegal manipulation of IoT devices, IoT device failures, security accidents, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
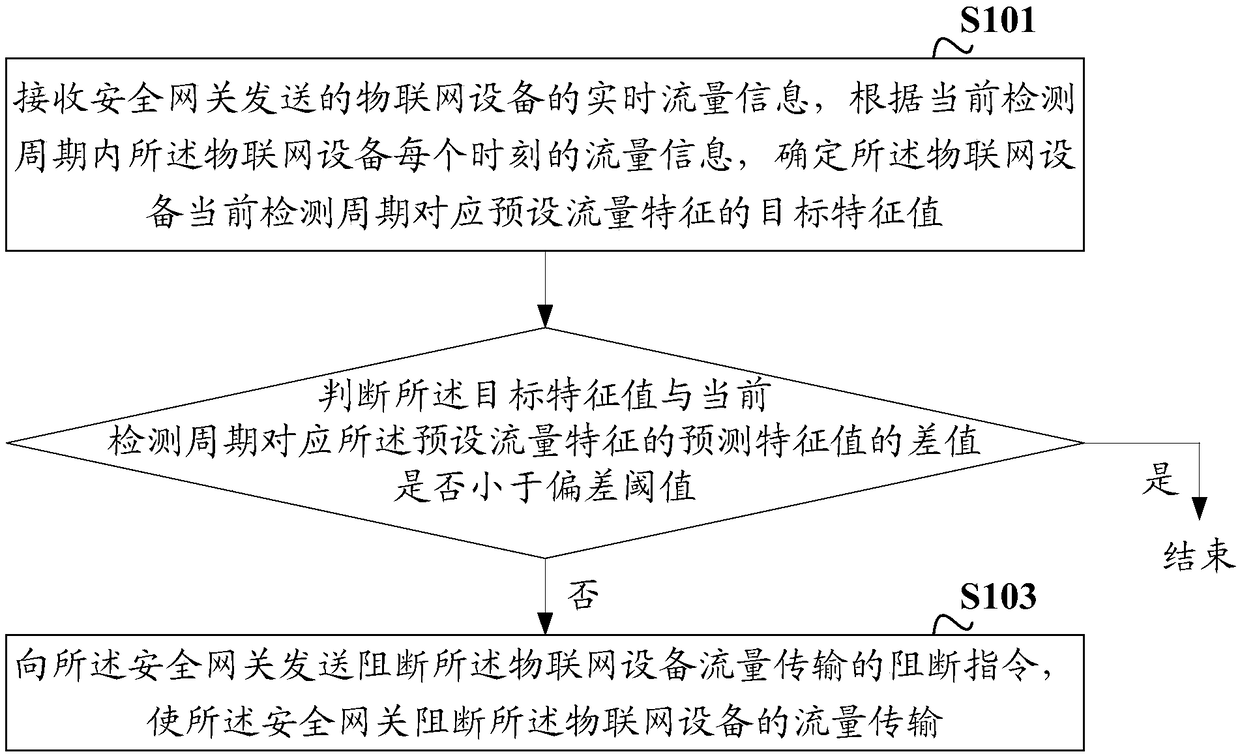
[0071] figure 1 A schematic diagram of a security protection process provided by an embodiment of the present invention, the process includes:
[0072] S101: Receive the real-time traffic information of the IoT device sent by the security gateway, and determine the target characteristic value corresponding to the preset traffic characteristic of the IoT device in the current detection cycle according to the traffic information of the IoT device at each moment in the current detection cycle .
[0073] The security protection method provided by the embodiment of the present invention is applied to a security server. The security server may also be a security server cluster composed of multiple security servers, or a security platform composed of multiple security servers. There can be one or more security gateways with a communication connection with the security server, and there can be one or more IoT devices connected to the security gateway. An example of a security gatewa...
Embodiment 2
[0084] Different from traditional terminals such as computers or mobile phones, the destination address of IoT devices is relatively fixed and can be enumerated. In order to further improve the effect of security protection, on the basis of the above embodiments, in the embodiments of the present invention, according to The flow information of the Internet of Things device at each moment in the current detection cycle, before determining the target characteristic value corresponding to the preset flow characteristic of the current detection cycle of the Internet of Things device, the method further includes:
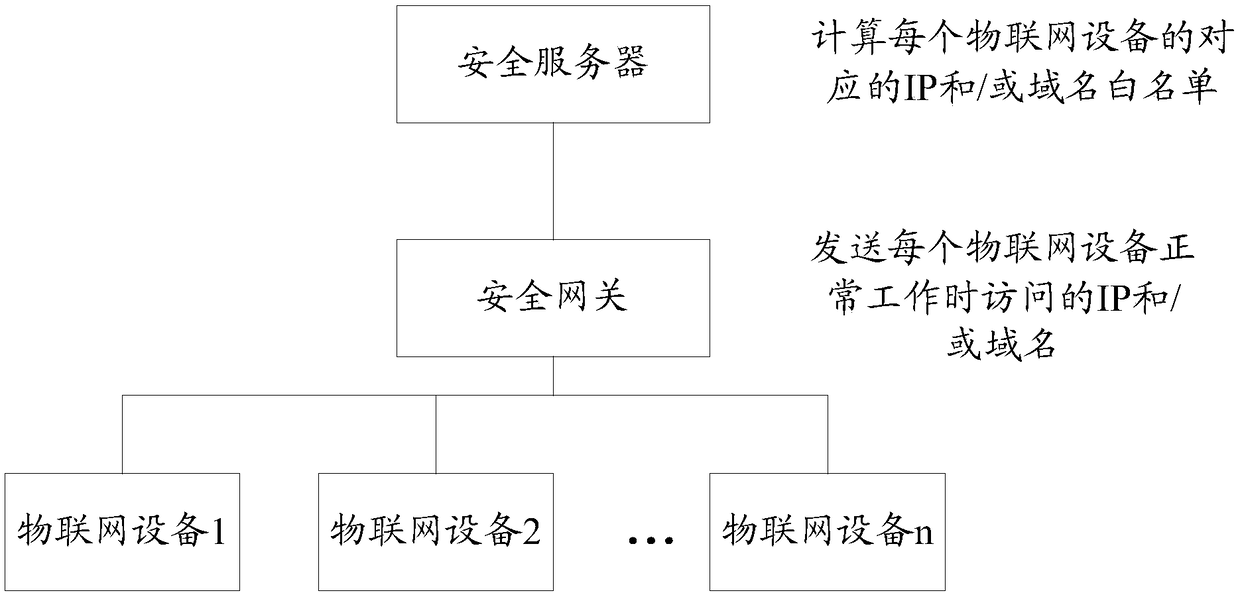
[0085] receiving the IP and / or domain name accessed by the IoT device sent by the security gateway;
[0086] Judging whether the IP and / or domain name is recorded in the IP and / or domain name whitelist corresponding to the IoT device, wherein the IP and / or domain name whitelist is based on the historical IP and domain names visited by the IoT device / or determined by th...
Embodiment 3
[0093] In order to prevent a single Internet of Things device from being mistaken for being normal due to abnormal access or being attacked, on the basis of the above-mentioned embodiments, in the embodiment of the present invention, if the target characteristic value corresponds to the preset traffic of the current detection period The difference between the predicted feature values of the features is less than a deviation threshold, the method further comprising:
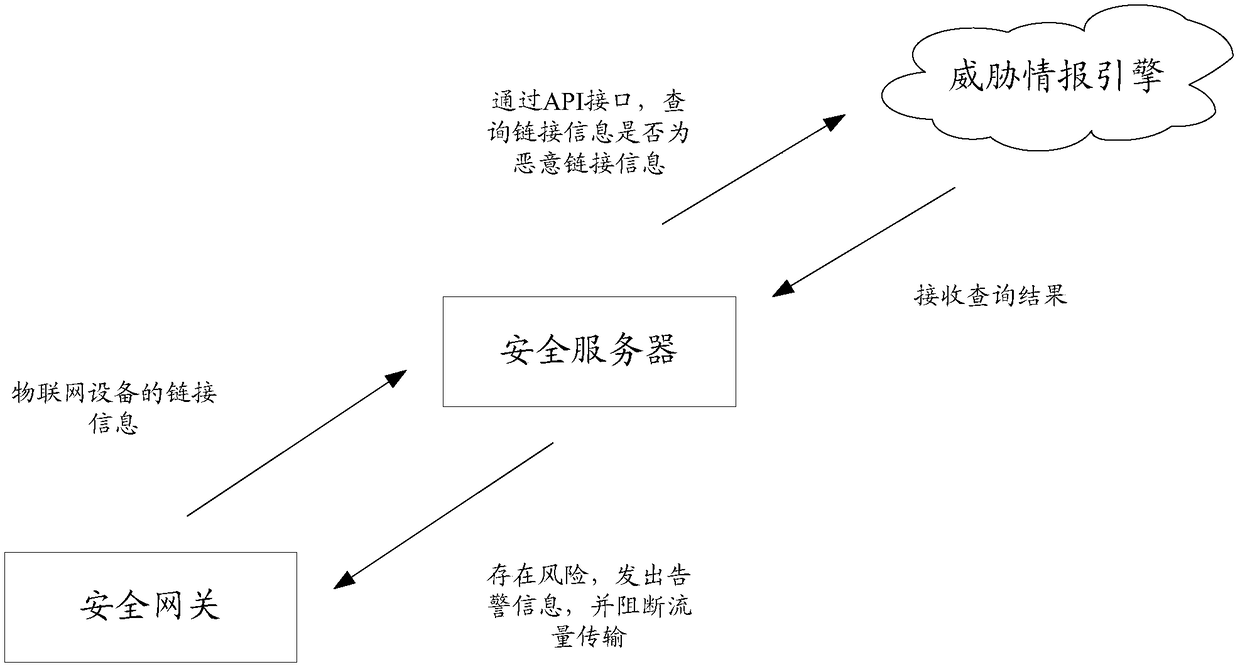
[0094] receiving the device model of the IoT device sent by the security gateway;
[0095] Judging whether the target traffic feature value and the IP and / or domain name are in the pre-saved traffic feature set and IP and / or domain name set corresponding to the device model;
[0096] If not, send a blocking instruction to block the traffic transmission of the IoT device to the security gateway, so that the security gateway blocks the traffic transmission of the IoT device.
[0097] In this embodiment of the law...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com