Monitoring video management method and device, and terminal device
A technology for monitoring video and management methods, which is applied in the field of devices and terminal equipment, and monitoring video management methods, which can solve problems such as endangering privacy security and privacy leakage, and achieve the effect of ensuring privacy security, maintaining personal security and property security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
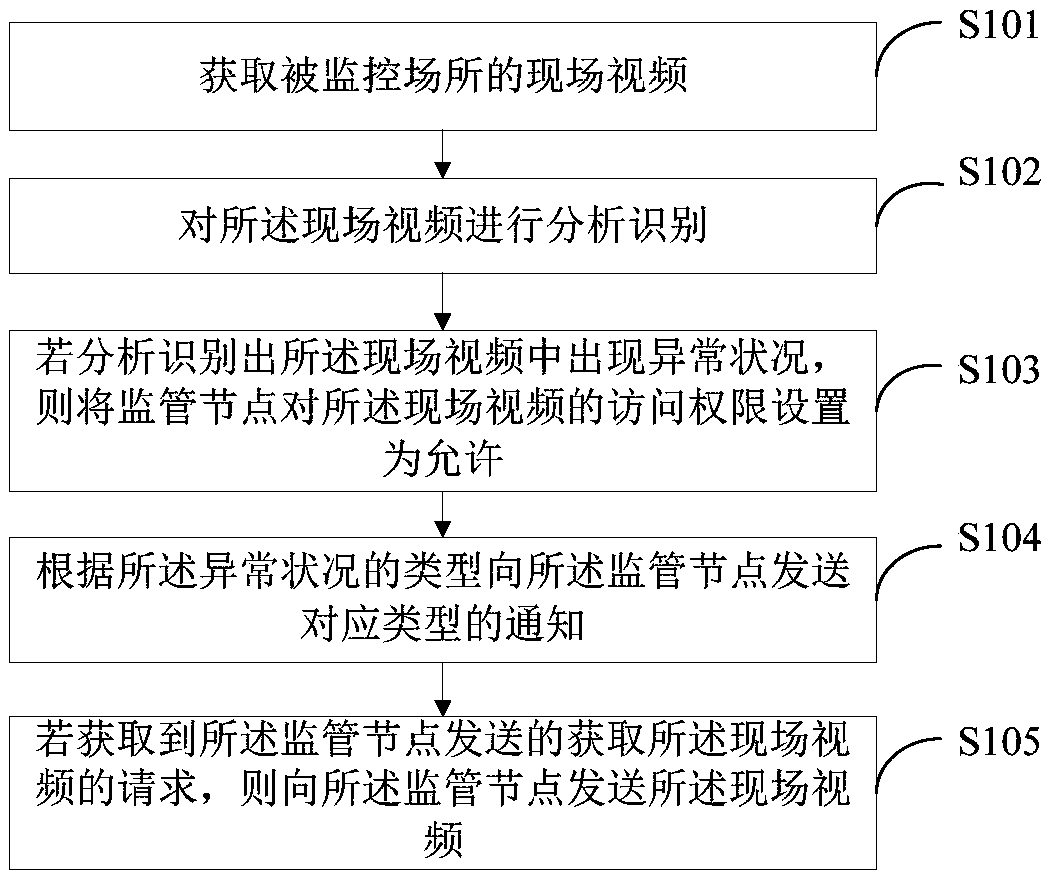
[0042] Such as figure 1 As shown, this embodiment provides a monitoring video management method, which can be applied to terminal devices such as mobile phones, PCs, tablet computers, and intelligent monitoring devices. The surveillance video management method provided by this embodiment includes:
[0043] S101. Obtain live video of the monitored place.
[0044] In a specific application, the monitored place is photographed through at least one camera communicatively connected with the current terminal device, and the live video of the monitored place sent by the camera is obtained. Among them, the camera includes but is not limited to a monocular camera, a binocular camera, a camera with a face recognition function, and a camera with a fire and smoke recognition function. In this embodiment, when the camera is connected to the internal network of the monitored place, the camera can be accessed from the external network using the internal network penetration technology. For...
Embodiment 2
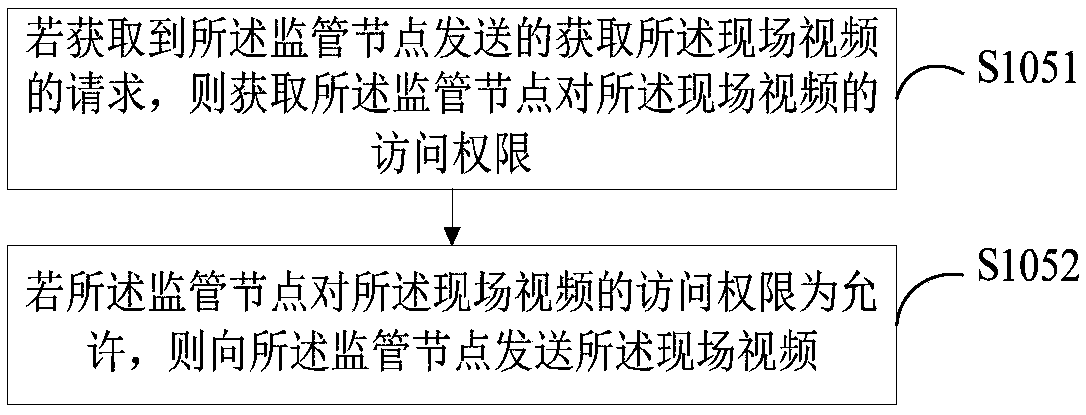
[0062] Such as figure 2 As shown, this embodiment is a further description of the method steps in the first embodiment. In this embodiment, step S105 includes:
[0063] S1051. If the request for acquiring the live video sent by the supervisory node is acquired, acquire the access right of the supervisory node to the live video.
[0064] In a specific application, if the request for obtaining the live video sent by the supervisory node is obtained, the access authority of the supervisory node to the live video is obtained, and it is judged whether the supervisory node has the right to view the live video.
[0065] S1052. If the supervisory node has permission to access the live video, send the live video to the supervisory node.
[0066] In a specific application, if the supervisory node has permission to access the live video, then the supervisory node has the right to view the live video, and then sends the live video to the supervisory node, so that supervisors can handle...
Embodiment 3
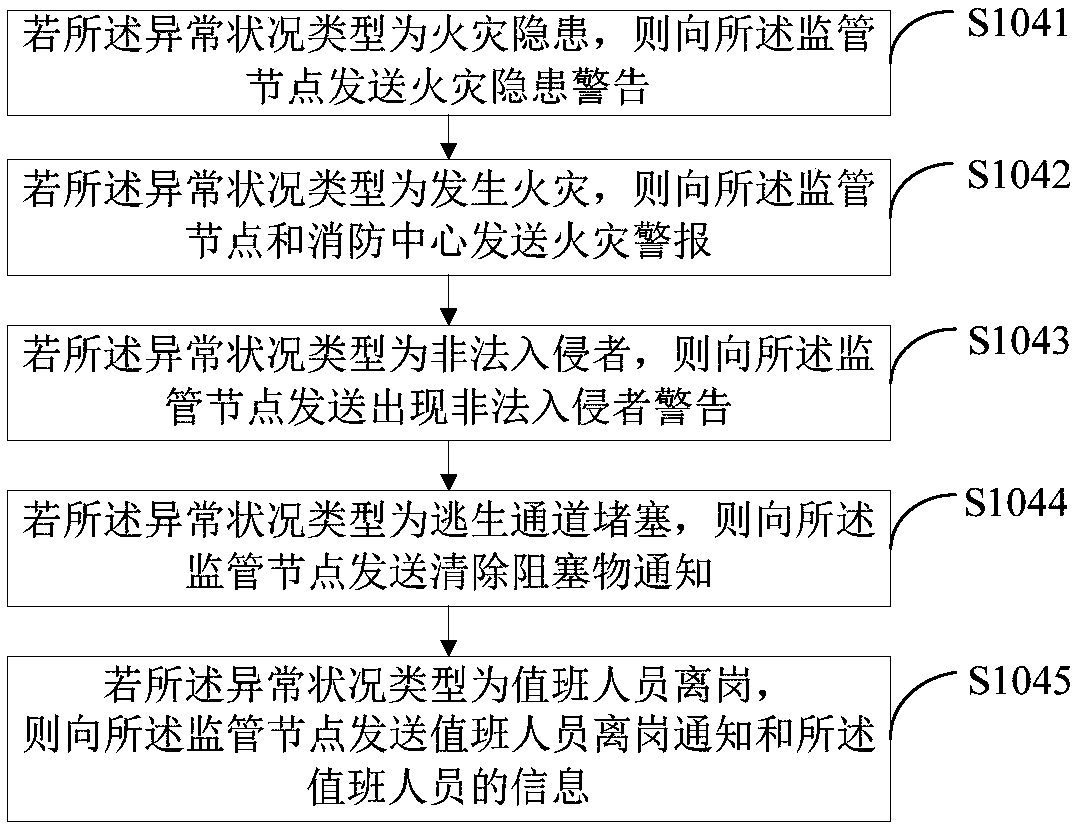
[0072] Such as image 3 As shown, this embodiment is a further description of the method steps in the first embodiment. In this embodiment, step S104 includes:
[0073] S1041. If the type of the abnormal situation is a fire hazard, send a fire hazard warning to the supervisory node.
[0074] In a specific application, if it is identified that the type of abnormal situation in the on-site video is a fire hazard, a fire hazard warning will be sent to the supervisory node, and a fire hazard notification will be sent to the on-duty personnel, so that the on-duty personnel and supervisors can deal with the fire hazard in time and avoid There is a fire.
[0075] S1042. If the type of the abnormal situation is a fire, send a fire alarm to the supervision node and the fire center.
[0076] In a specific application, if the analysis identifies that the type of abnormal situation in the on-site video is a fire, a fire alarm will be sent to the supervisory node and the fire center, so...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com