A login verification processing method, system and device
A technology of login verification and processing method, which is applied in the field of login verification processing method, system and device, and can solve problems such as request failure, invalidation, business server cannot guarantee the order of concurrent refresh tokens, etc., so as to improve user experience and ensure logical correctness Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] method embodiment
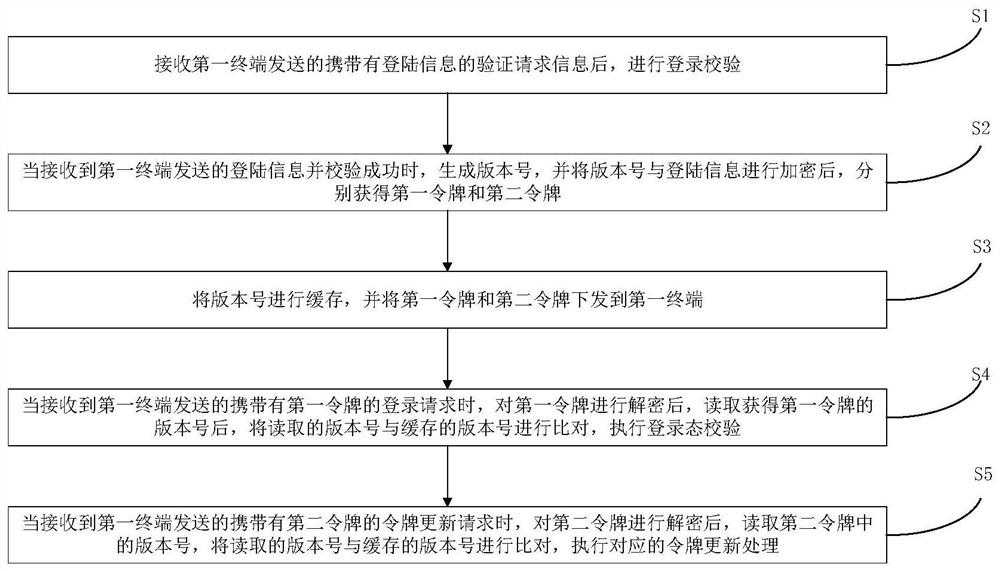
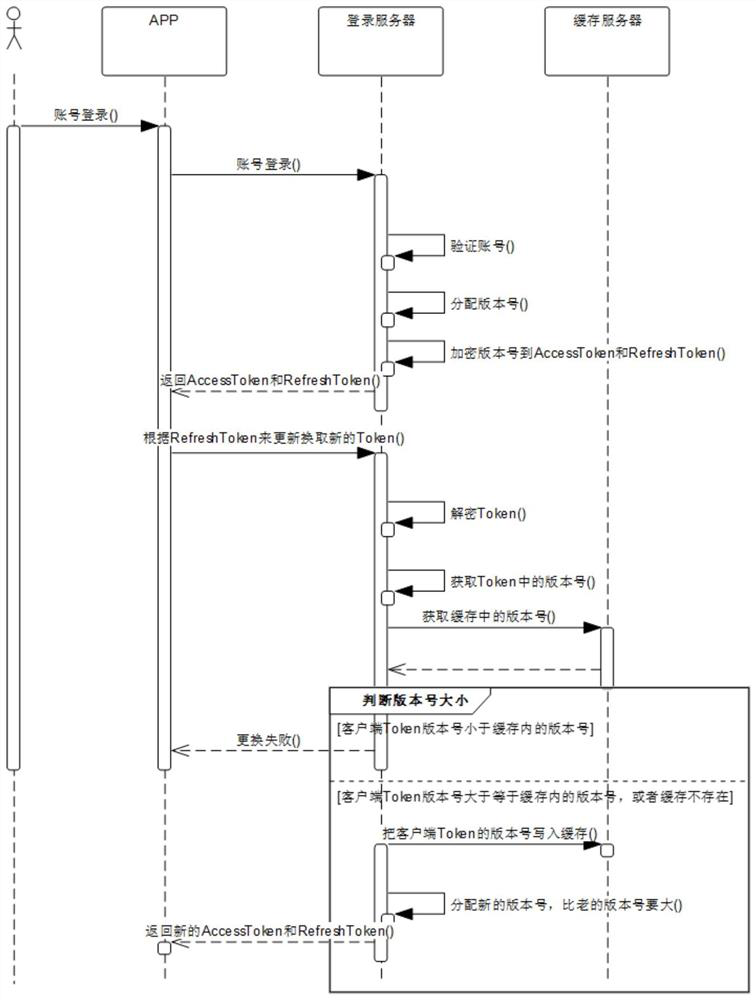
[0042] refer to figure 1 , this embodiment provides a login verification processing method, the method is mainly executed in the login server, and is used to realize the process of refreshing the login state supporting idempotence, and specifically includes the following steps:
[0043] S1. After receiving the verification request information carrying the login information sent by the first terminal, perform login verification, and after the verification is successful, proceed to the next step; the login information includes login account number and password and other information; in the actual execution process , only after verifying that the login information is correct, continue to perform the following steps, and use the login state verification method to log in to the account; here, the first terminal can be various smart terminals such as smart phones, tablets, computers, and vehicle-mounted terminals;
[0044] S2. When the login information s...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap