Network device and secure method
A network device, network technology, applied in the direction of program control device, computer security device, internal/peripheral computer component protection, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
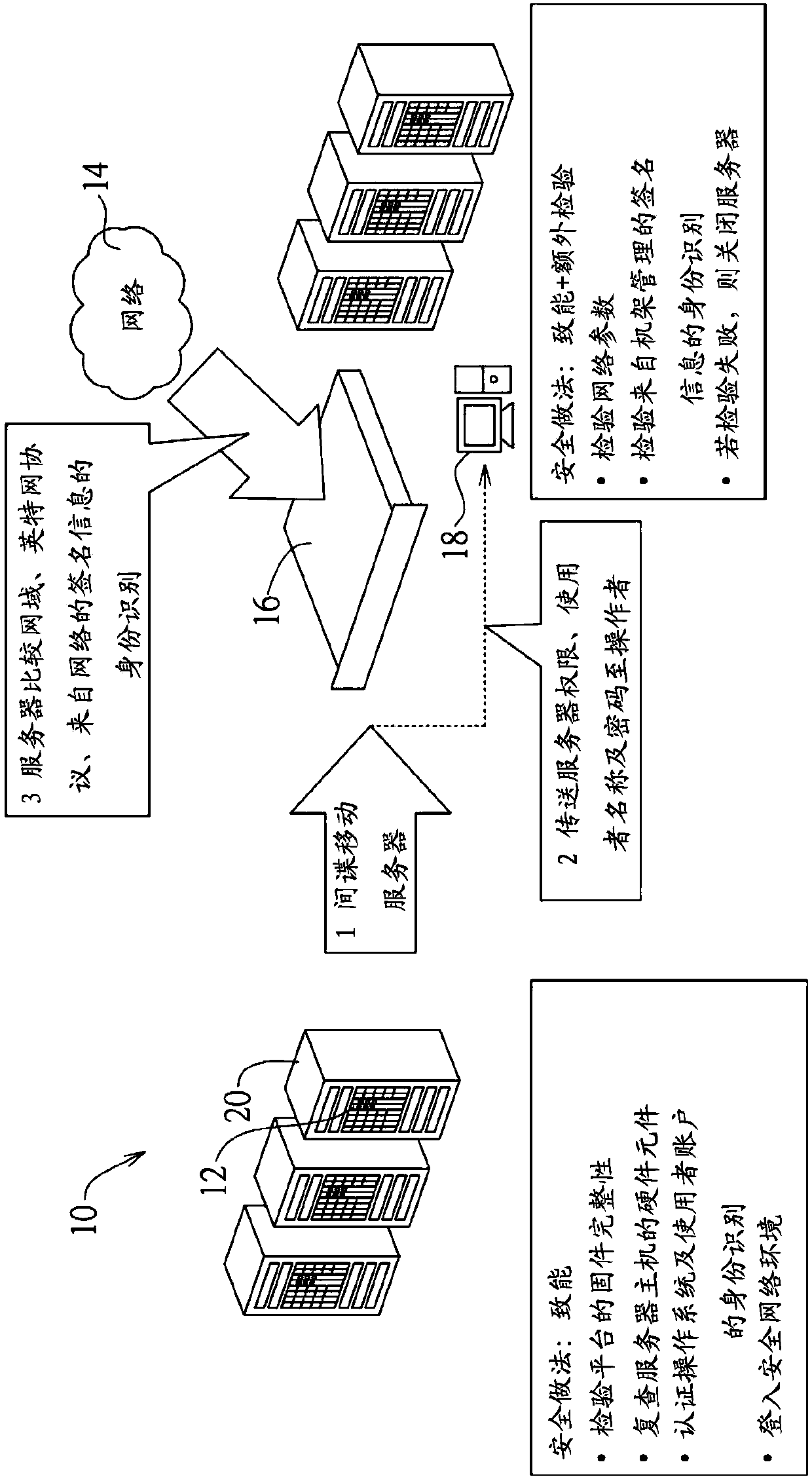
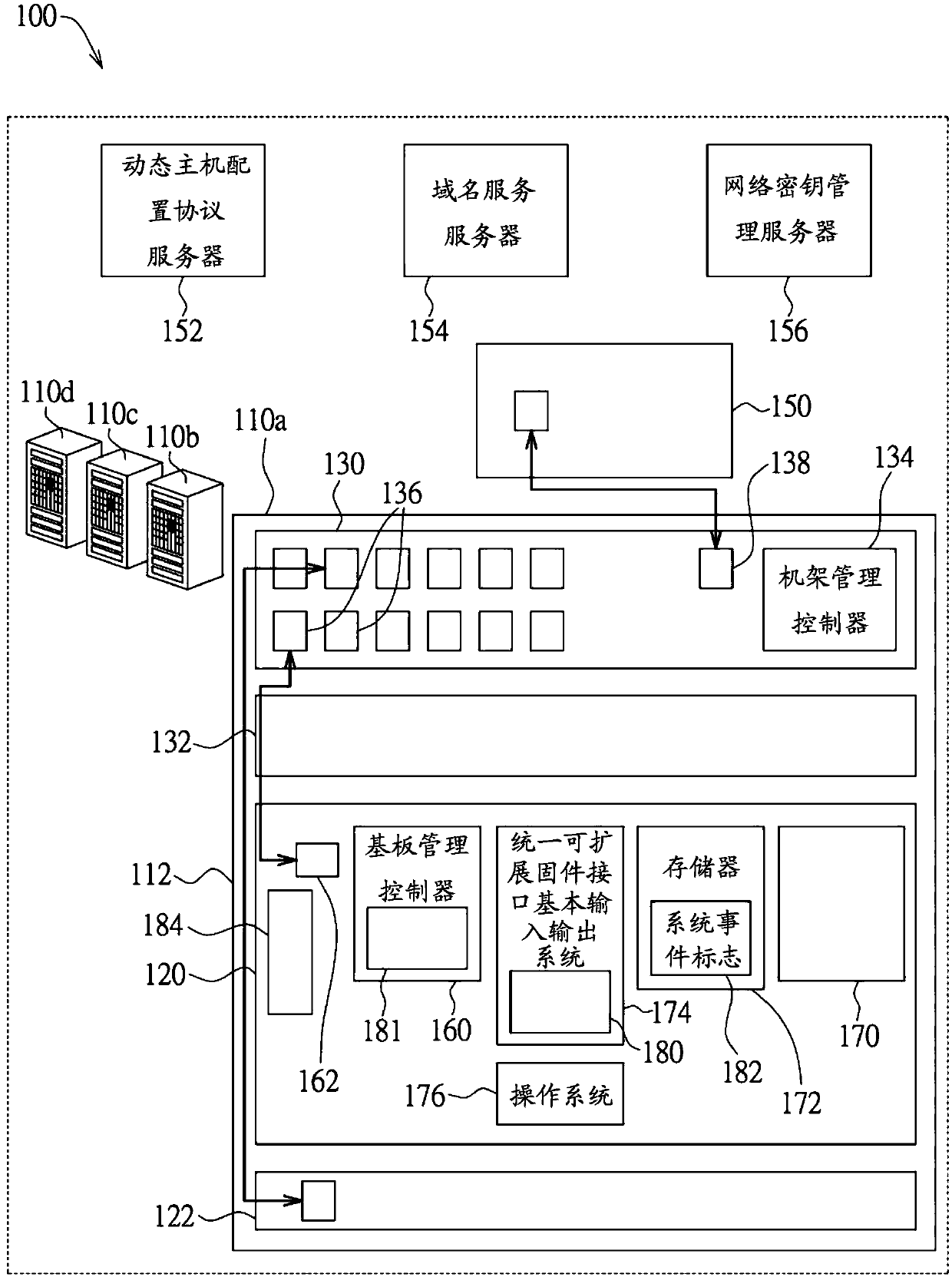
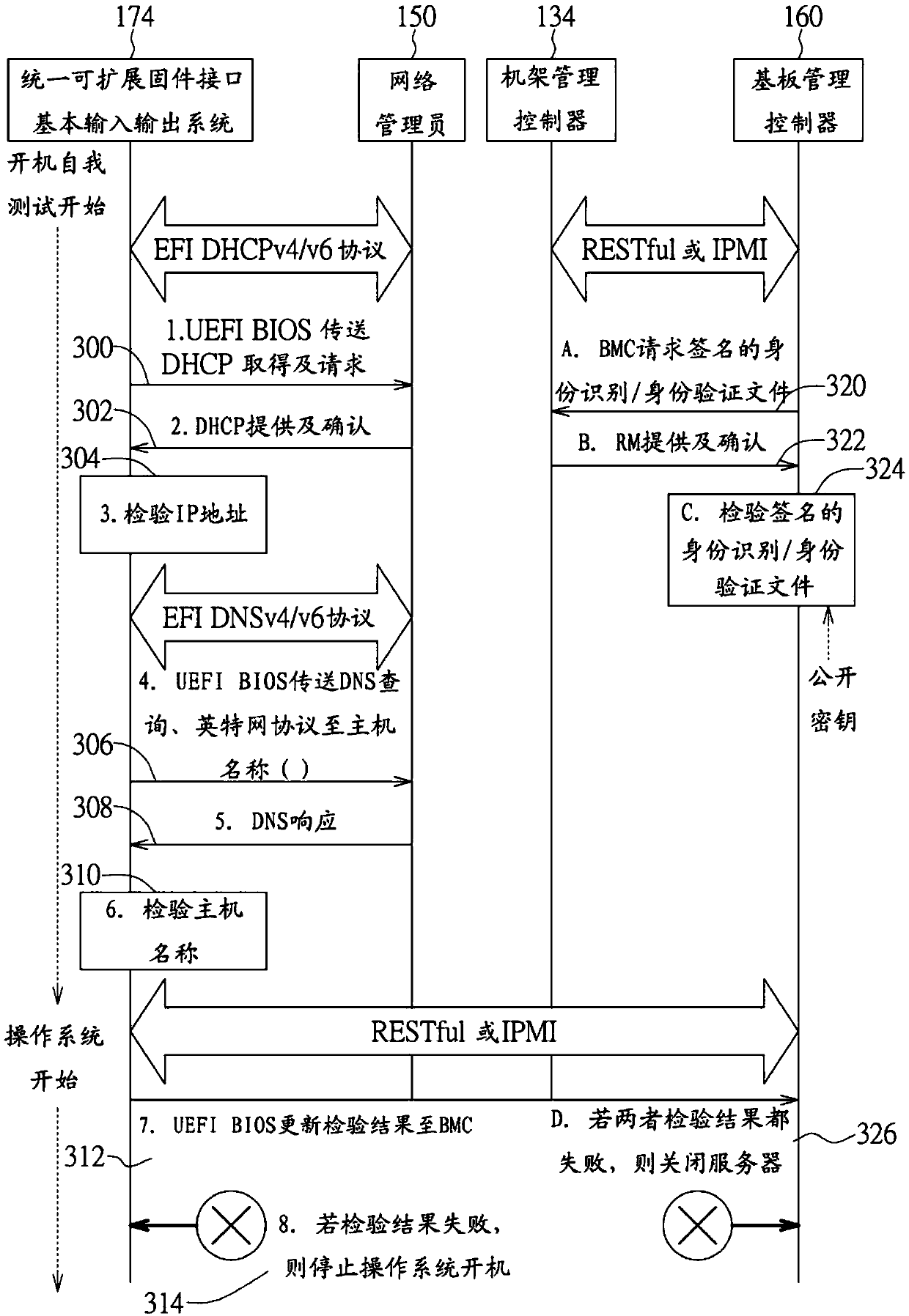
[0055] The present disclosure can be implemented in many different forms. The representative implementations are shown in the drawings and will be described in detail here. What is disclosed here is an example or depiction of a rule of the present disclosure, and it is not limited to the broadest aspect disclosed in the depicted embodiment. Within this scope, the disclosed components and limitations, such as the abstract, the content of the invention, and the embodiments, which are not clearly stated in the claims, should not be inserted in a single or integrated manner in the sense or inference. Claims. For the purpose of the detailed description of the present invention, unless expressly abandoning a single including a plurality, and vice versa; and the term "including" means "including without limitation". In addition, similar terms, such as "approximately", "almost", "substantially", "approximately", etc., can be used herein, for example, to mean "at, close to, or near" o...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap