Signal processing method and terminal equipment
A signal processing and terminal equipment technology, applied in voice analysis, voice recognition, instruments, etc., can solve problems such as failure to work normally, potential safety hazards of user voice interaction, and inability to accurately distinguish between real voice and recorded voice, etc. Achieve the effect of improving accuracy, improving user experience, and realizing effective recognition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
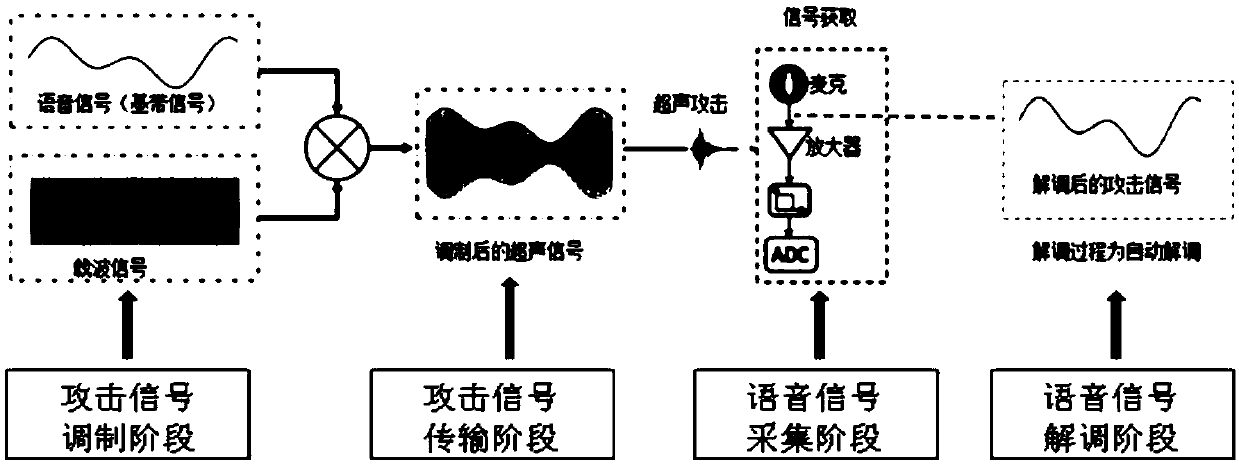
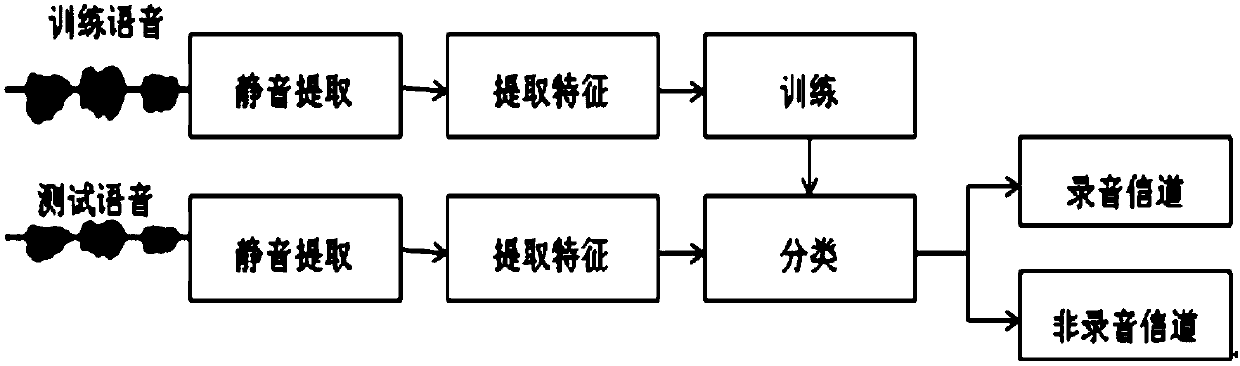
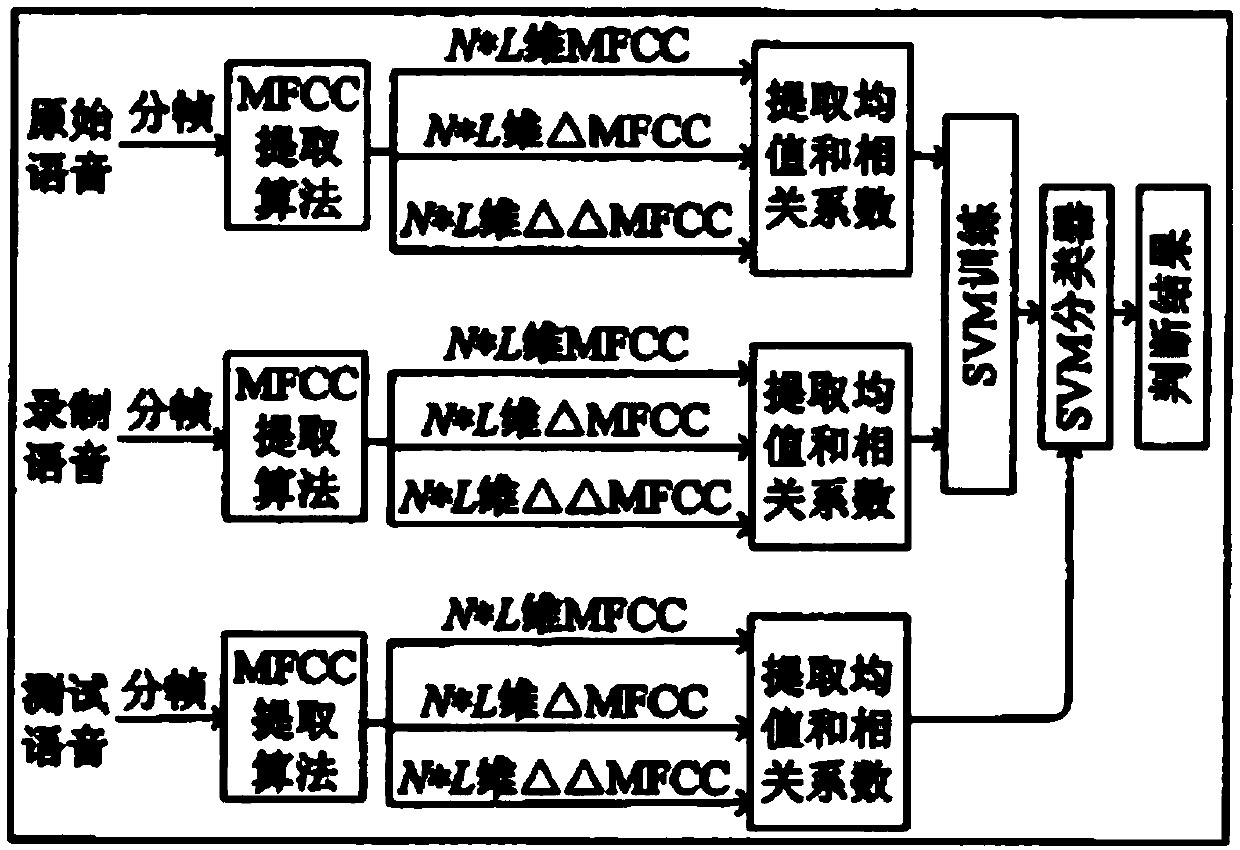
[0178] The embodiment of the present invention discloses a method for identifying abnormal voice signals used for attack by extracting voice signal features and using machine learning to identify the voice signal features. The detailed system block diagram of this embodiment is as follows Figure 13 shown.
[0179] step:
[0180] 1. Prepare a large amount of normal speech signal and abnormal speech signal data for attack for training the network model and classifier of machine learning. The larger the amount of data, the better the stability of the network model and the discrimination of the classifier.
[0181] 2. Through the band-pass filter, extract the normal voice signal and demodulate the voice information of the abnormal voice signal used for the attack in the frequency range of 2000 Hz to 3000 Hz.
[0182] 3. Extract the short-term zero-crossing rate and short-term energy characteristics of the normal speech signal and the abnormal speech signal after passing through ...
Embodiment 2
[0186] A dynamic wake-up command is generated and notified to the user.
[0187] Dynamic instructions can be customized by the user. For example, the user can set the words or sentences for the wake-up instruction; the system can also set a set of words or sentences for the user to wake up by default; Click, and then extract keywords as words or sentences for wake-up instructions.
[0188] At present, many terminal devices can display information floatingly on the screen when they are in a standby state. Such as Figure 14 As shown, so the wake-up word can be displayed on the screen in the standby state, or displayed on the screen of the wearable device connected to it. The user sees the current wake-up command, and then wakes up the terminal by uttering the wake-up command equipment.
[0189] For example, the terminal device currently randomly selects one of the previously defined wake-up words and displays it on the screen, and the user speaks the current wake-up word whe...
Embodiment 3
[0192] The attack signals are distinguished by the characteristic changes of the signals.
[0193] This method can change the characteristics of the user's voice signal when the user initiates a voice command to the terminal device by slightly shaking the terminal device up and down, or adding gestures between the terminal device and the user. The terminal device distinguishes whether it is a normal voice signal according to the change of the signal characteristics, and responds to the voice command only if it is a normal voice signal.
[0194] In this mode, the characteristics of the input voice signal will change regularly, and if the terminal device detects that the change pattern of the characteristics of the input voice signal is consistent with the set change pattern, the voice signal is considered to be a normal voice signal , otherwise, it is regarded as an abnormal speech signal.
[0195] It is also possible to pre-train the machine learning network model for the abo...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap