Method and system for computing intersection of privacy-preserving sets based on polynomial representation
A technology of privacy protection and calculation method, which is applied in the field of computer network communication data security and privacy protection, and can solve the problem of low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
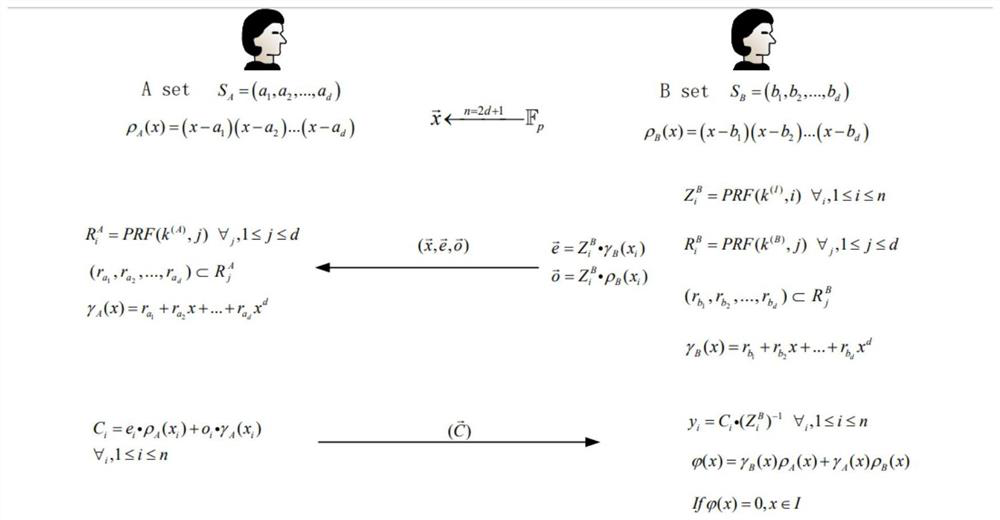
[0059] The present invention provides a privacy protection set intersection calculation method based on polynomial representation, which is applied to both users A and B who participate in the request, and participant A holds the first set, and participant B holds the second set, please refer to figure 1 , the method includes the following steps:
[0060] First execute step S1: initial setting of parameters, parameters include the construction vector generated by participant B, the second set of polynomials constructed by participant B according to the second set, and the first set of polynomials constructed by participant A according to the first set.
[0061] Specifically, the construction vector is constructed by the session initiator. In this embodiment, participant B is used as the session initiator. Of course, in other implementation manners, participant A may be used as the session initiator.
[0062] Specifically, step S1 specifically includes the following sub-steps: ...
Embodiment 2
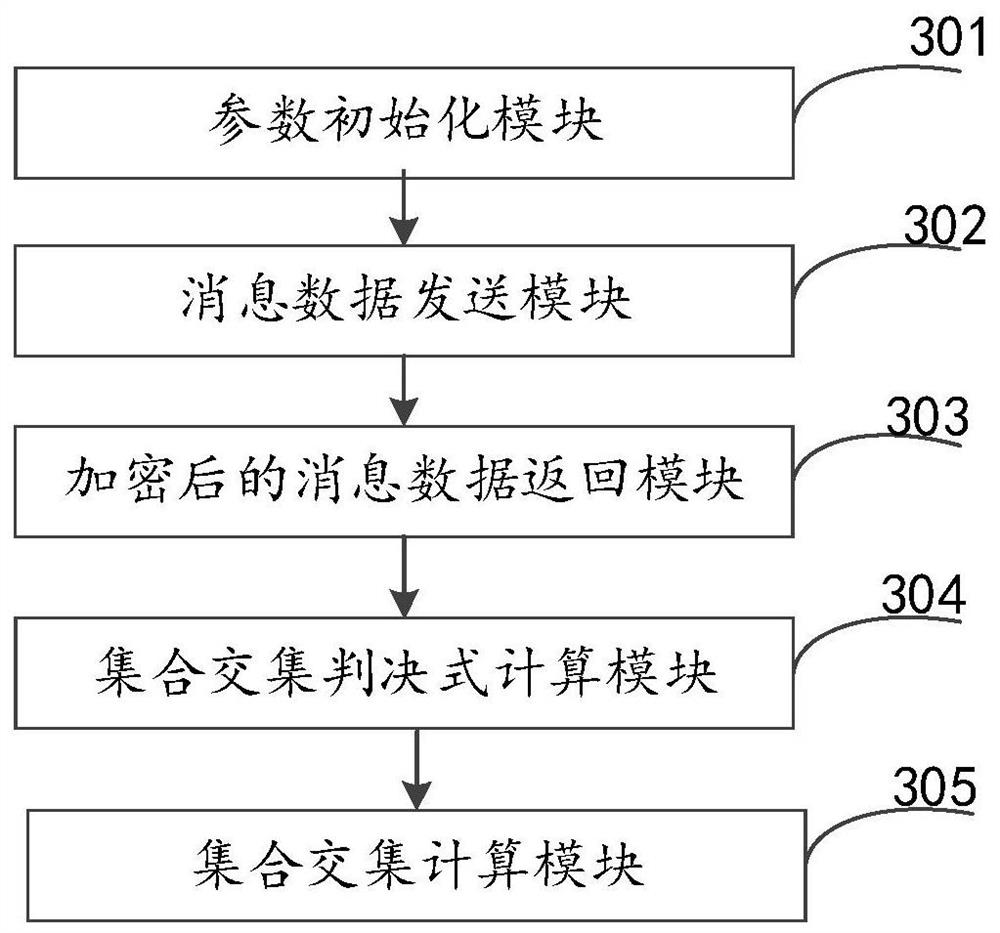
[0095] This embodiment provides a privacy-preserving set intersection calculation system based on polynomial representation. The polynomial-based privacy-preserving set intersection calculation system is applied to both users A and B participating in the request, and participant A holds the first set, Party B holds the second set, see image 3 , the system includes:
[0096] The parameter initialization module 301 is used for initializing and setting parameters, and the parameters include the construction vector generated by participant B, the second set of polynomials constructed by participant B according to the second set, and the first set of polynomials constructed by participant A according to the first set ;
[0097] The message data sending module 302 is used for participant B to send message data to participant A, wherein the message data includes a construction vector, a first message representation vector and a second message representation vector, wherein the firs...
Embodiment 3
[0124] Based on the same inventive concept, the present application also provides a computer-readable storage medium 400, please refer to Figure 4 , on which a computer program 411 is stored, and the method in Embodiment 1 is implemented when the program is executed.
[0125] Since the computer-readable storage medium introduced in the third embodiment of the present invention is the computer-readable storage medium used to implement the polynomial representation-based privacy-preserving set intersection calculation in the first embodiment of the present invention, it is based on the introduction in the first embodiment of the present invention Those skilled in the art can understand the specific structure and deformation of the computer-readable storage medium, so details will not be repeated here. All computer-readable storage media used in the method of Embodiment 1 of the present invention belong to the scope of protection of the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com