Contract online verification method
A verification method and contract technology, applied in the fields of digital data authentication, commerce, instruments, etc., can solve the problems of difficulty in distinguishing the authenticity of secondary contracts, and no method for re-authentication of contracts is provided, so as to improve security, ensure authenticity and effectiveness sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment 1
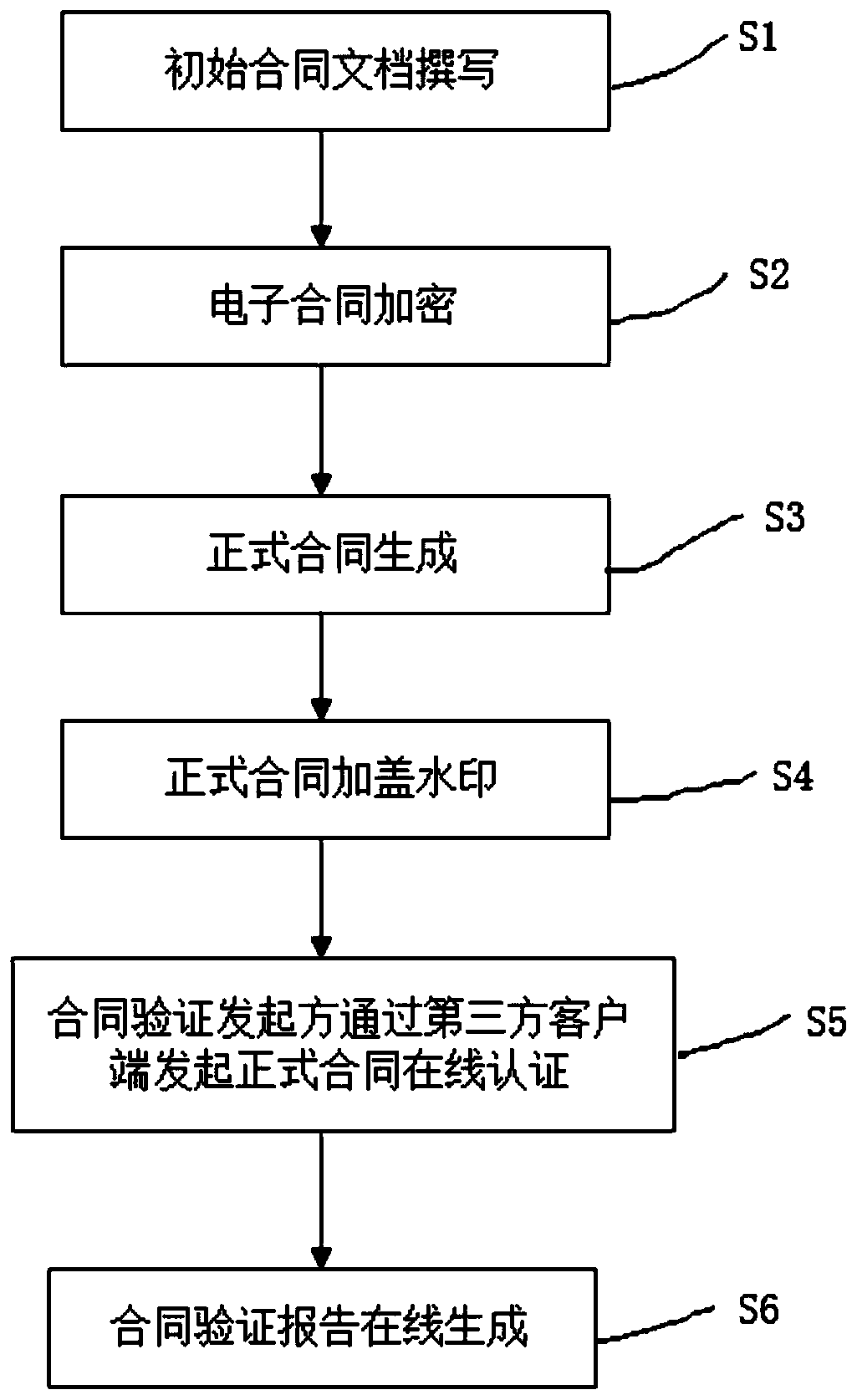
[0043] Example 1: Such as figure 1 As shown, the steps of electronic contract generation, verification, and verification report generation: the contract initiator logs in to the third-party client with a dedicated account, and the contract initiator initiates contract writing to the third-party client; after the contract is written, the third-party client uses hash The algorithm extracts and encrypts the digest value of the written electronic contract. The encrypted electronic contract is sent to the contract initiator and the contract signer by email; after the contract signer receives the information, he logs in to the third-party client with his own account and encrypts The document is decrypted, the official electronic contract is checked, and after the contract is confirmed, the electronic signature and seal are called, stamped on the electronic contract, and the official contract is generated; the contract signer dictates a text and voice through the voiceprint collection ...
Embodiment 2
[0045] Embodiment 2: A specific step of the identity verification of the contract initiator is: First, the contract verification initiator initiates online contract verification through a third-party client, and the third-party client verifies the identity information of the contract verification initiator, and the third party The client verifies the identity information of the initiator of contract verification through one or a combination of the following methods;
[0046] A1. The contract verification initiator manually enters the digital password on the third-party client password interface;
[0047] A2. Send online identity verification information via email;
[0048] A3. Verify identity information by sending SMS verification code;
[0049] A4. Compare and verify with the voice information pre-stored in the third-party client by reading a 5-second voice password message;
[0050] A5. Collect and verify the identity image information of the initiator through the image sensor confi...
Embodiment 3
[0054] Embodiment 3: The specific steps of electronic contract comparison verification are as follows;
[0055] After the identity verification is completed, the contract verification initiator imports the pre-verified electronic contract document into the third-party system for electronic contract comparison verification. The electronic contract verification method is divided into manual verification method and system verification method. The manual verification method is Manually check the contents of the original formal electronic contract by the third-party client, and manually check the authenticity of terms and signatures by comparing with the contents of the pre-verified electronic contract documents; system verification methods include pre-verified electronic contract document content verification and pre-verified electronic contract Validity verification, pre-verified electronic contract document content verification is to extract the digest value information of the pre-v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com