Information hiding method based on big data and dynamic time recursion and robot system
A technology of information hiding and big data, which is applied in the information field, can solve the problems of limited data volume and easy cracking of information hiding, and achieve the effect of improving capacity, security and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
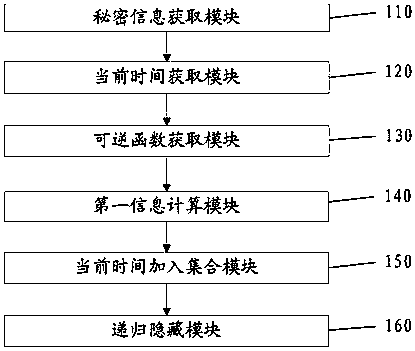
[0062] Embodiment 1 provides an information hiding method, such as figure 1 As shown, the method includes step S110 to step S160.
[0063] Secret information acquiring step S110: acquiring secret information x. Preferably, the secret information can be obtained by accepting user input information or files. Secret information refers to the information to be hidden, which can be text, password, image, graphics or sound, etc.
[0064] The current time obtaining step S120: obtaining the current time t. The current time can be obtained through system time conversion or online. Preferably, if the preset number of recursions is k, the current times obtained successively are t1, t2, ..., tk, respectively.
[0065] Reversible function acquisition step S130: Obtain a preset reversible function g with secret information x and current time t as variables; preferably, the reversible function is g(x, f(t)), where f is the second preset function, corresponding to The inverse function of is x=g-...
Embodiment 2
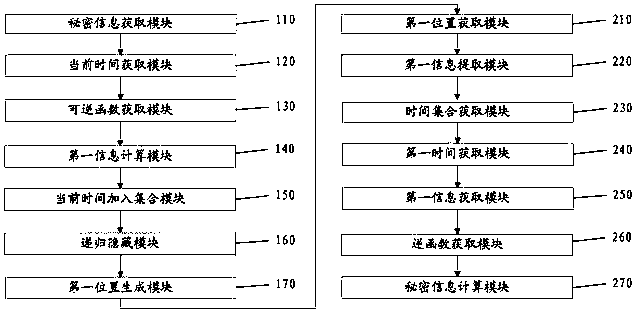
[0070] Embodiment 2 provides a preferred information hiding method. According to the information hiding method described in Embodiment 1, combined with big data, such as figure 2 As shown, the method further includes step S170.
[0071] First position generation step S170: insert y into the big data, and obtain the position of y in the big data as the first position. Preferably, y is randomly inserted into the big data. Preferably, the position of y in the big data includes the start position and the end position of y. Preferably, the first position is output to the user.
[0072] The beneficial effect of this embodiment is that after inserting the first information into the big data, the cracker is further unable to find the first information, and the secret information needs to be converted from the first information, which naturally makes the secret information more difficult to crack
Embodiment 3
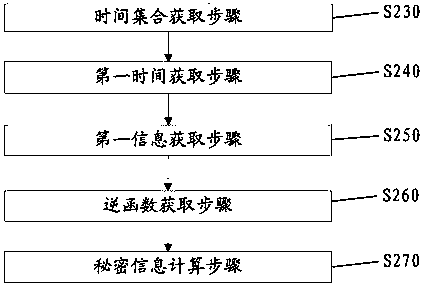
[0073] Embodiment 3 provides a preferred information hiding method. According to the information hiding method described in Embodiment 2, the first position generating step S170 specifically includes: generating the first position according to the time in the first time set and the preset function h. Position, insert y into the first position in the big data. Preferably, the first position p is generated using the time closest to the present in the first time set and the preset function h, that is, p=h(t).
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com