Information hiding method based on big data search and robot system
A robot system and information hiding technology, applied in the fields of digital data protection, electrical digital data processing, instruments, etc., can solve the problems of limited data volume and easy to be cracked, and achieve high security, low computing overhead, and ensure security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
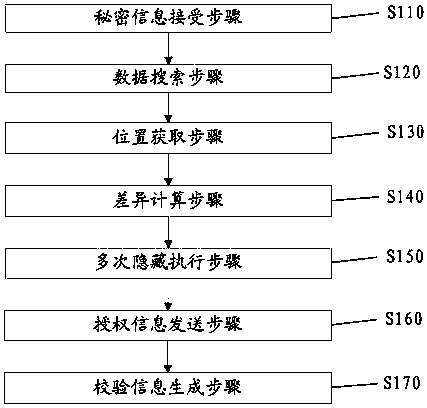
[0075] Embodiment 1 provides an information hiding method, such as figure 1 As shown, the method includes step S110 to step S170.
[0076] Secret information accepting step S110: Accept the secret information that needs to be hidden; for example, the information that needs to be hidden is 100 first photos.
[0077] Data search step S120: Search out the first information y' with a high degree of matching with the secret information y from the big data. Secret information refers to information to be hidden, which can be text, passwords, images, graphics or sounds, and so on. For example, search for second photos with a matching degree greater than 80% of 100 first photos from big data (such as Google Search or Baidu Search) as the first information. Wherein, the first information may consist of one or more data in the big data, and these data may be distributed in any position in the big data. The high degree of matching means that the degree of matching between the secret in...
Embodiment 2
[0086] Embodiment 2 provides a preferred information hiding method, according to the information hiding method described in Embodiment 1, combined with big data.
[0087] Step S110 includes an information splitting step S111: splitting the secret information y into a plurality of partial secret information y1, y2, . . . , ym (m is the number of splits).
[0088] Step S120 includes a multi-data search step S121: search for a plurality of first information y1', y2', ..., ym with a high degree of matching with a plurality of secret information y1, y2, ..., ym from the big data ';
[0089] Step S130 includes multi-position acquisition step S131: acquire multiple positions of multiple first information y1', y2', ..., ym' in the big data as multiple first positions s1, s2, ..., sm .
[0090] Step S140 includes a multi-difference calculation step S141: taking the corresponding differences between a plurality of first information y1', y2', ..., ym' and a plurality of secret informat...
Embodiment 3
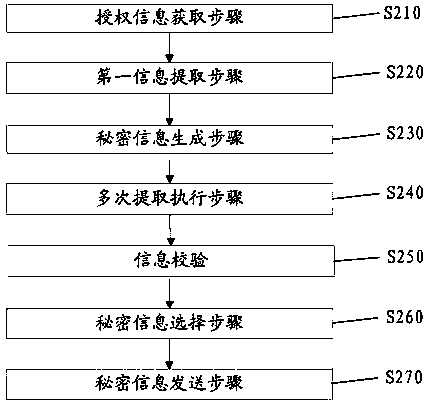
[0095] Embodiment 3 provides an information extraction method, the method includes step S210 to step S270, such as figure 2 shown.
[0096] Authorization information acquisition step S210: Accept at least one set of first position s and second information z. Generally, the first position s and the second information z are received from the user terminal through the network.
[0097] First information extraction step S220: Extract first information y' from the first position s in the big data. For example, 100 second photos are downloaded from 100 network addresses in the first location as the first information.
[0098] Secret information generation step S230: Generate secret information y according to the first information y' and the second information z. Because in the hidden stage, the second information = f(secret information, first information), where f is the function of finding the difference between the secret information and the first information, so when restorin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com