Weblog anomaly detection method in combination with GRU and SVDD
An anomaly detection and logging technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve the problems of large manpower and material resources, low detection accuracy, weak detection ability of unknown abnormal types, etc., to achieve good detection and positioning. , the effect of reducing false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
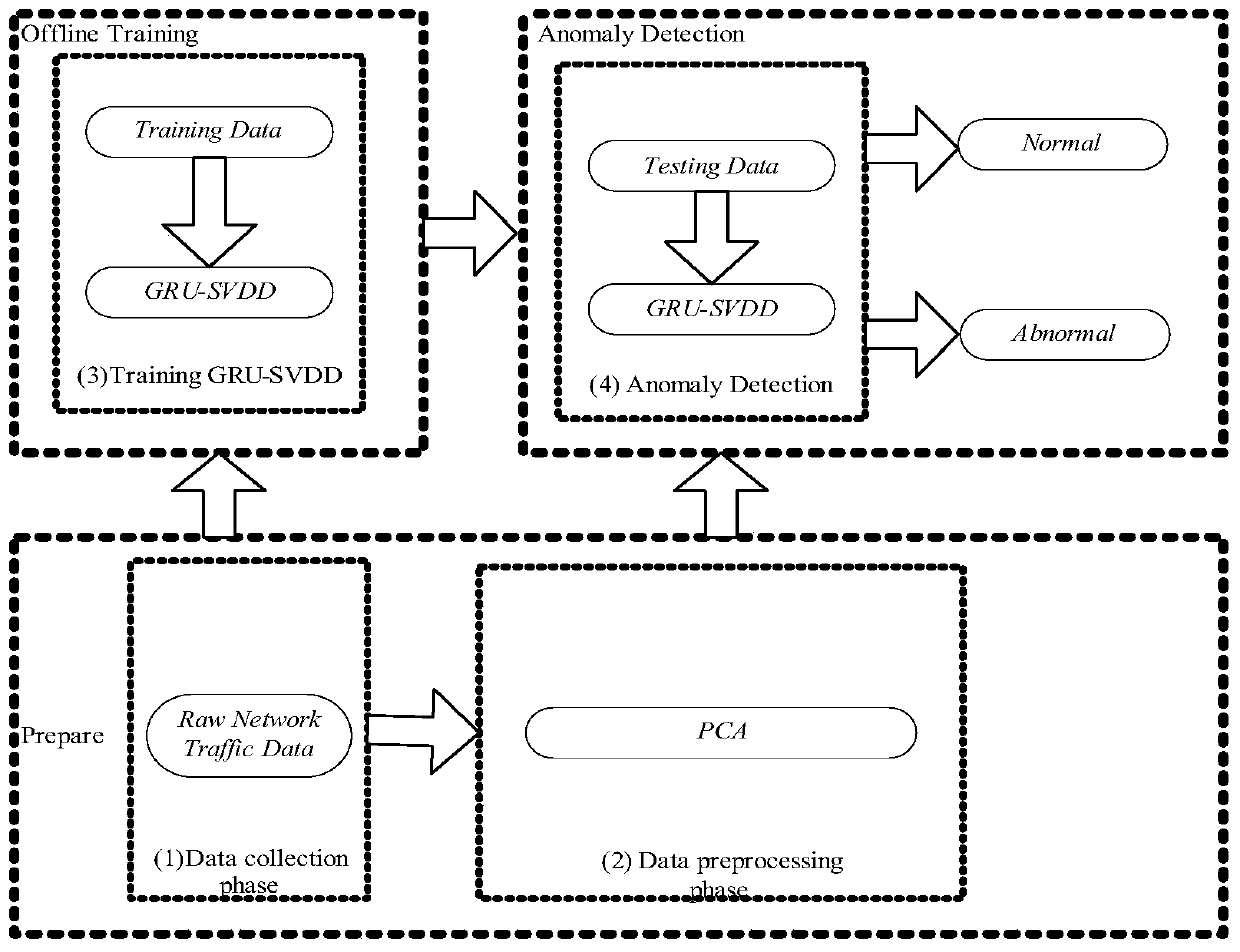
[0029] Such as Figure 1-3 As shown in one of them, the present invention discloses a network log anomaly detection method combined with GRU and SVDD, which performs data dimensionality reduction processing on the original network log data set with high correlation between high latitude and characteristic attributes, and converts the attribute features of the network log data set into It is converted into a new principal component that is irrelevant among attributes; then GRU is used to extract the data attribute features after dimensionality reduction preprocessing, and finally the high-efficiency single classification method is used to replace the output layer of GRU to obtain abnormal users.
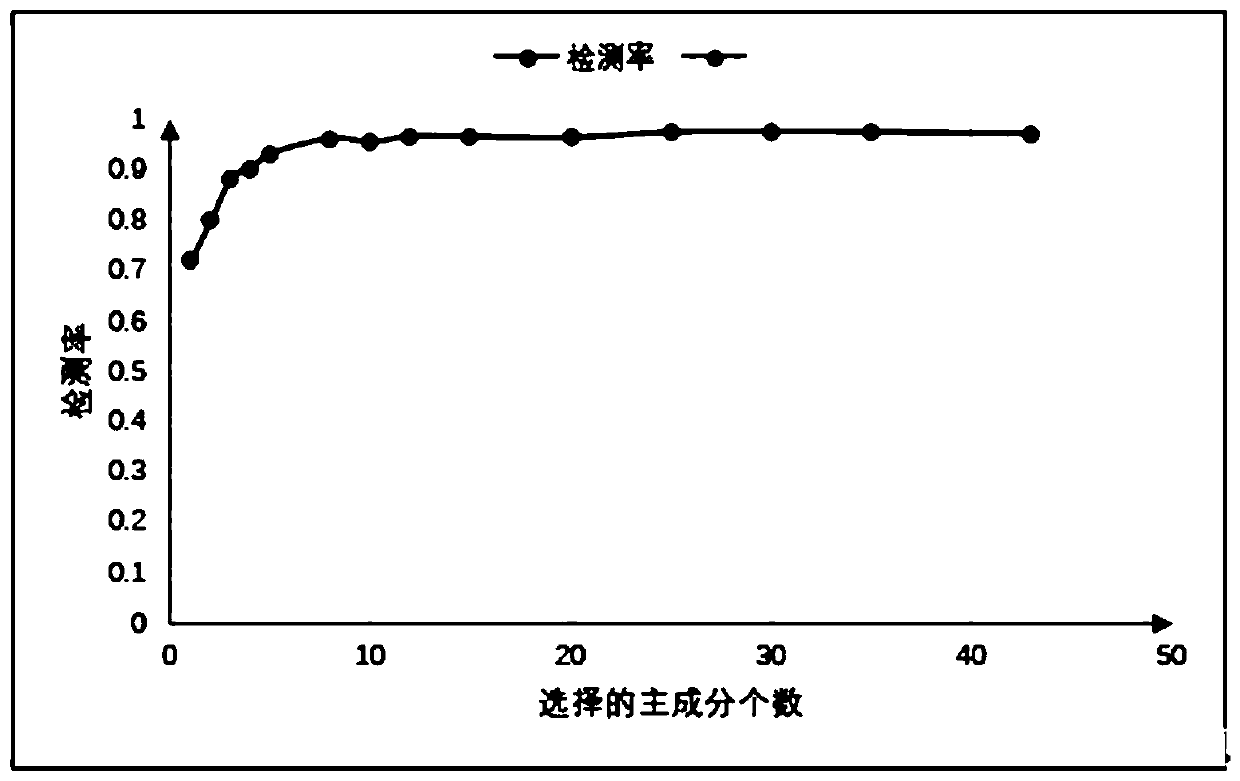
[0030] Furthermore, the principal component analysis method is used to reduce the dimensionality of the original network log data set with high correlation between high latitude and characteristic attributes.
[0031] Further, the method includes a model training phase and an anomaly ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap