Intelligent POS anti-root method based on Android system
An intelligent and file-based technology, which is applied in the directions of instruments, electrical digital data processing, and platform integrity maintenance, etc., can solve problems such as slowing down the system startup speed and affecting system performance, so as to prevent permanent access to root privileges and protect stolen effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
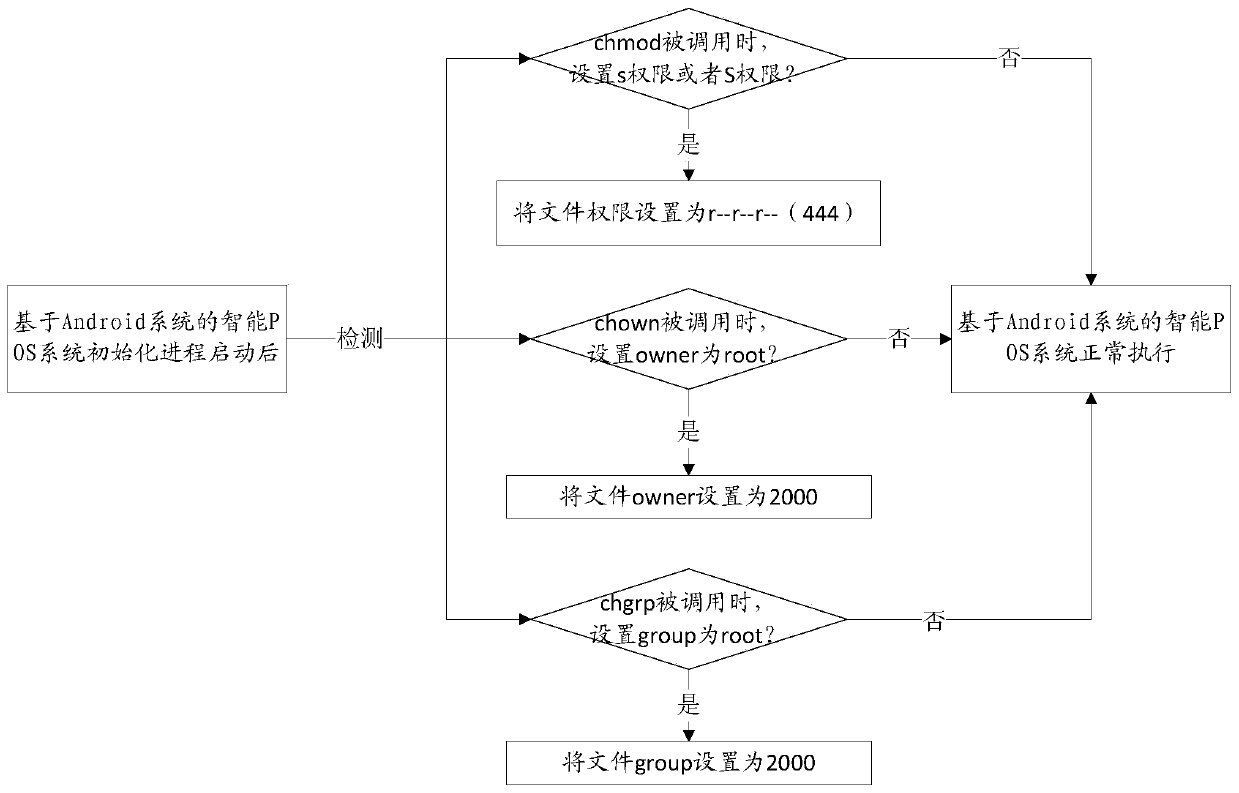
[0018] In this embodiment, for the first case, specifically, the detection calls chmod to assign special permissions to files, specifically, detects whether there is a behavior of calling chmod to assign s permissions or S permissions to files, and if so, then Forcibly change the file permissions to values without s permissions and S permissions.
[0019] In this embodiment, the permissions of files under Linux use rwx to represent read, write and execute permissions respectively, and the files also have two special permission bits called SUID permission bits and SGID permission bits. When the SUID or SGID permission bits of a file When it is set and has x executable permission at the same time, it can be said that the file has s permission. When the SUID permission bit or SGID permission bit of the file is set, but there is no x executable permission, it is expressed as S permission. When the file has the s permission, the file will not run with the UID of the caller, but t...
Embodiment 2
[0024] In this embodiment, for the second case, the detection calls chown to grant special permissions to the file, specifically, detects whether there is a call to chown to change the file owner to a high-privilege user, and if so, force the file owner to Change to a low-privileged user.
[0025] In this embodiment, chown is the command name, and its usage authority is root, and the owner of the file can be changed by using the chown command. Generally speaking, this command can only be used by the system administrator (root). General users do not have permission to change the owner of other people's files, nor do they have permission to change the owner of their own files to someone else. Only the system administrator (root) has such authority.
[0026] In this embodiment, each file under Linux has an owner, indicating who owns the file. When the file is set with s permission, the file will obtain the permission of the owner. Therefore, when the behavior of calling chown t...
Embodiment 3
[0028] In this embodiment, for the third case, the detection calls chgrp to assign special permissions to the file, specifically, detects whether there is a behavior of calling chgrp to change the file group to a high-privilege group, and if so, force the file group Change to a low-privilege group.
[0029] In this embodiment, chgrp is the name of the command. The chgrp command can be used to change the group to which files and directories belong. The setting method can be either the group name or the group identification code.
[0030] In this embodiment, each file under Linux also belongs to a certain group, and when the file has the S permission, the file will also have the permission of this group. Therefore, when it is detected that the file group is changed to a high-privilege group by calling chgrp, the file group is also directly changed to a low-privilege group, which can also improve system security.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com