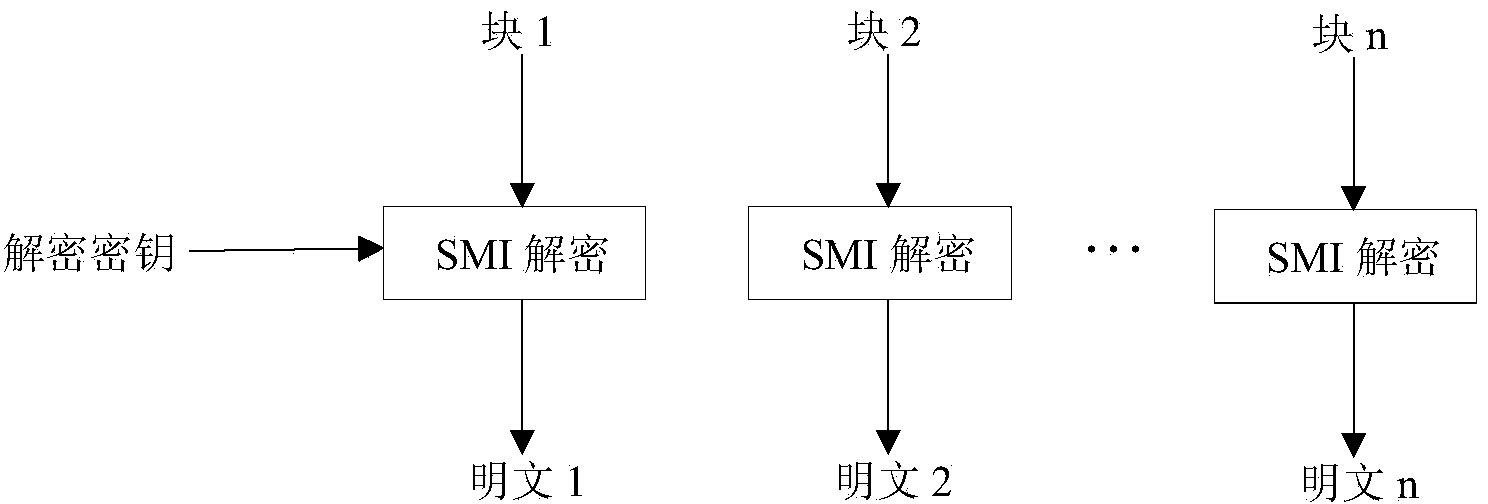
Patents
Literature
77results about How to "Won't steal" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Identity authentication method and apparatus, terminal and server
ActiveCN105468950AImprove accuracyWon't stealSpeech analysisCharacter and pattern recognitionThird partyPassword
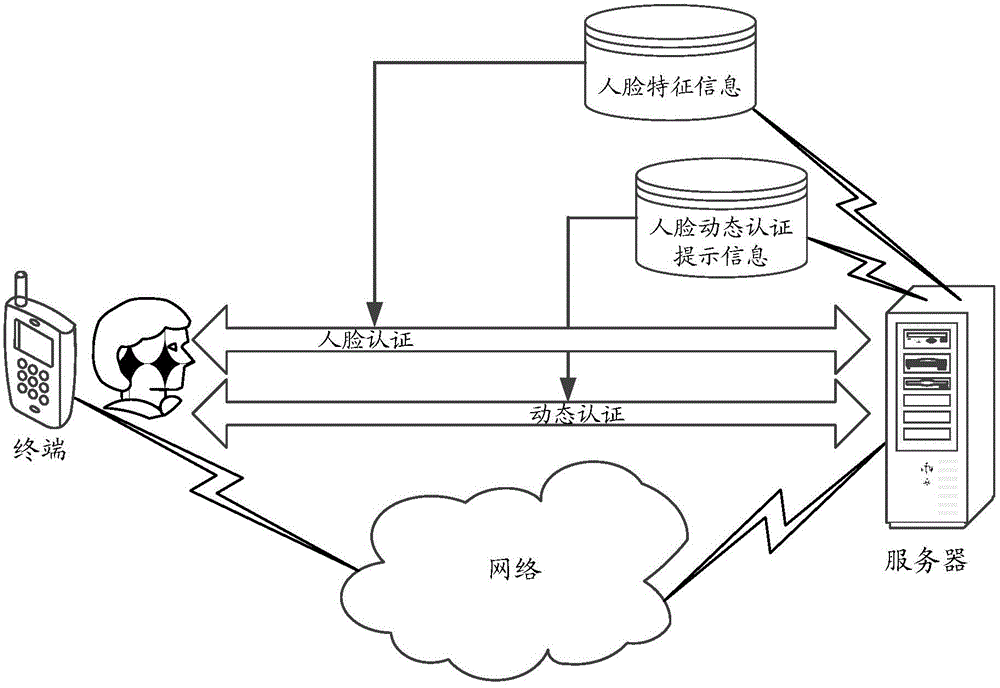
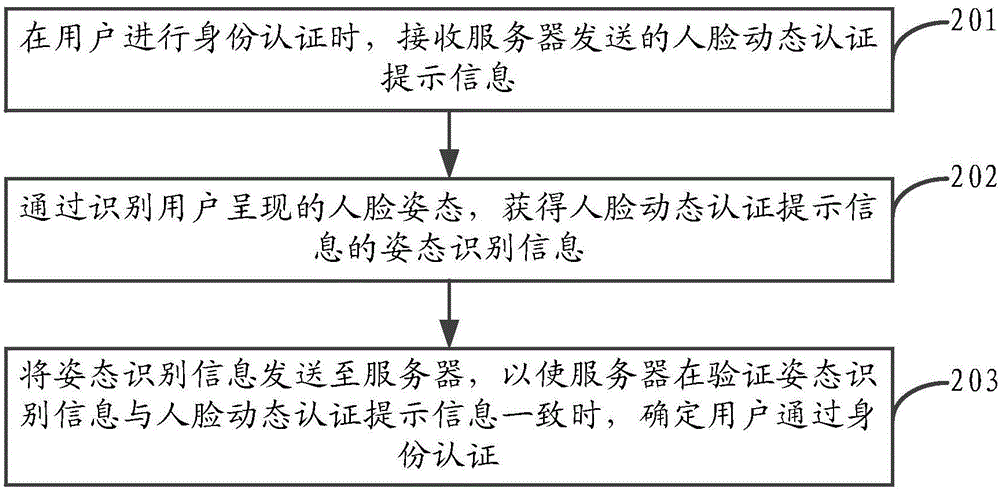
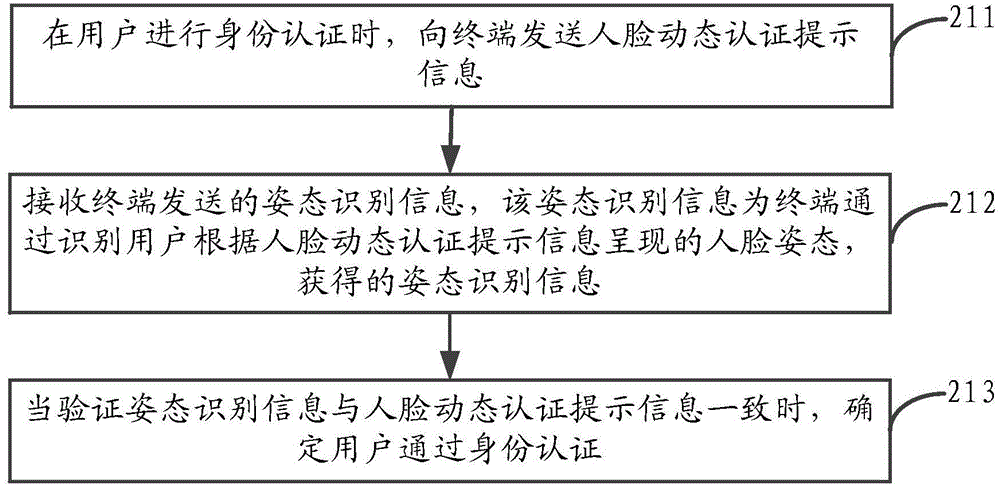
The present application discloses an identity authentication method and apparatus, a terminal and a server. The method comprises: when a user performs identity authorization, receiving face dynamic authentication prompt information sent by the server; identifying a face pose presented by the user to acquire pose identification information of the face dynamic authentication prompt information; and sending the pose identification information to the server, and when the pose identification information is the same as the face dynamic authentication prompt information, the server determining the user identity authentication is passed. According to the embodiments of the present application, the user identity can be authenticated with high security by means of the face dynamic authentication; compared with the prior method that uses password authentication to authenticate, authentication information will not be stolen by a malicious third party, thereby improving reliability of authentication; and the user can be identified as a living body by means of the face dynamic authentication, thereby further improving the accuracy of identity authentication and reducing safety risks existed during the process of authentication.
Owner:ADVANCED NEW TECH CO LTD
Method and device for reinforcing application program
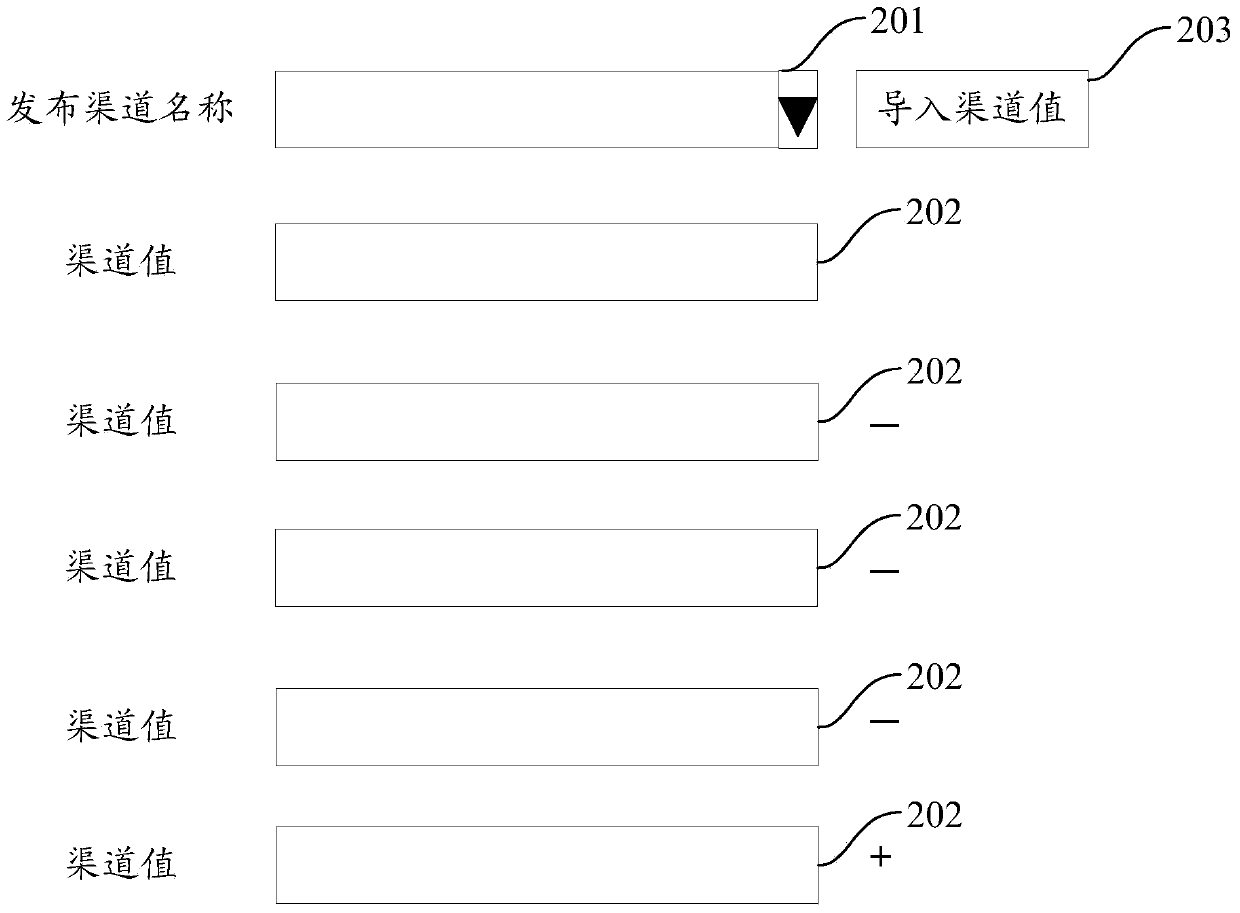
ActiveCN104217140AImprove securityPrevent decompilationProgram/content distribution protectionOperating systemResource file
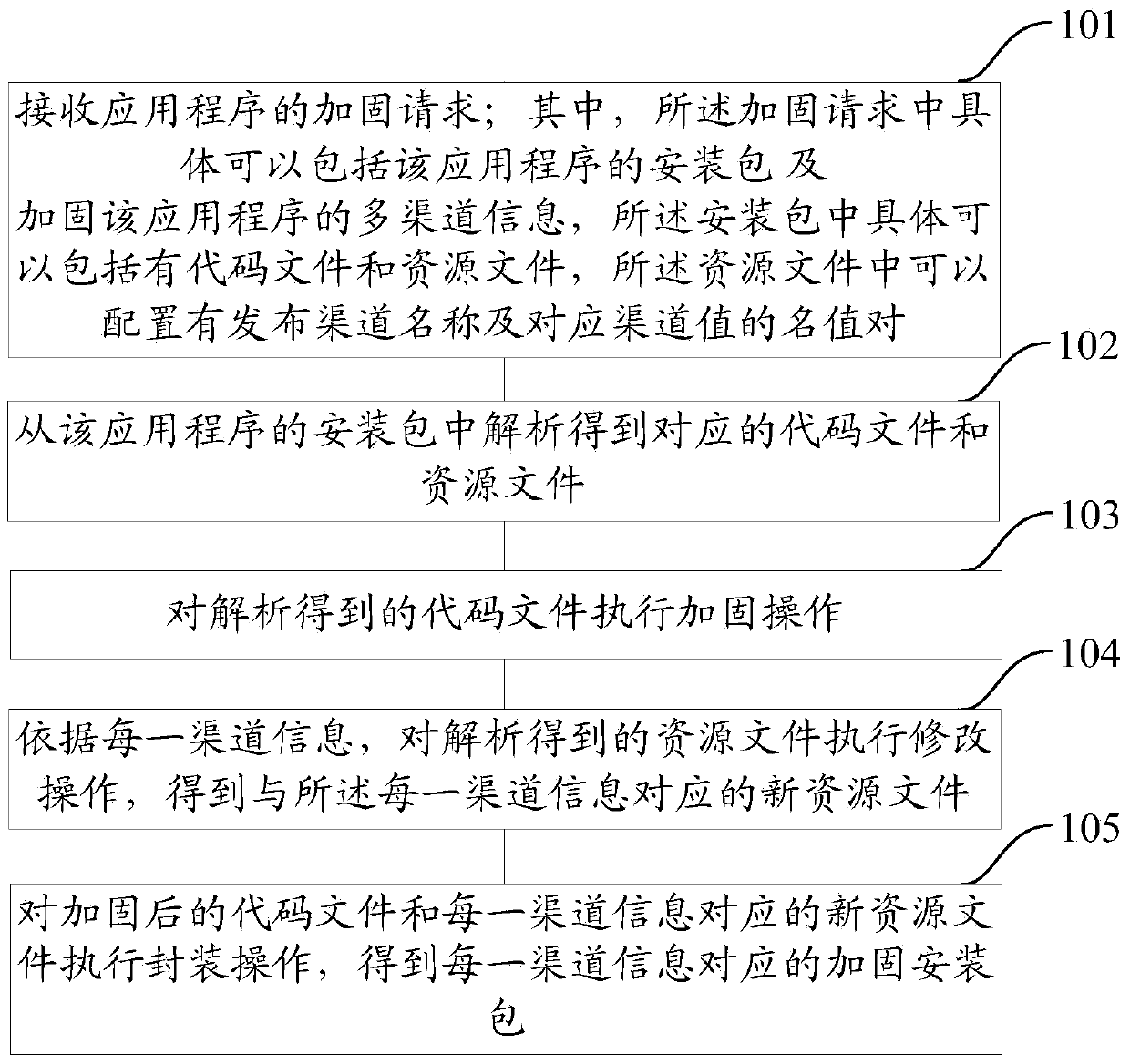
The embodiment of the invention provides a method and a device for reinforcing an application program. The method comprises the following steps of receiving a reinforcing request of the application program, wherein the reinforcing request comprises an installation package of the application program and multi-channel information for reinforcing the application program, the installation package comprises code files and resource files, and release channel names and corresponding channel values are configured in the resource files; analyzing to obtain corresponding code files and resource files from the installation package of the application program; executing reinforcing operation on the code files obtained through analysis; executing retouching operation on the resource files obtained through analysis according to each piece of channel information to obtain a new resource file corresponding to each piece of channel information; executing packaging operation on the reinforced code files and the new resource file corresponding to each piece of channel information to obtain a reinforced installation package corresponding to each piece of channel information. According to the method and the device, the safety of the application program can be improved and the efficiency of reinforcing multiple release channels is improved.
Owner:BEIJING QIHOO TECH CO LTD
Security distributed data management method based on public cloud
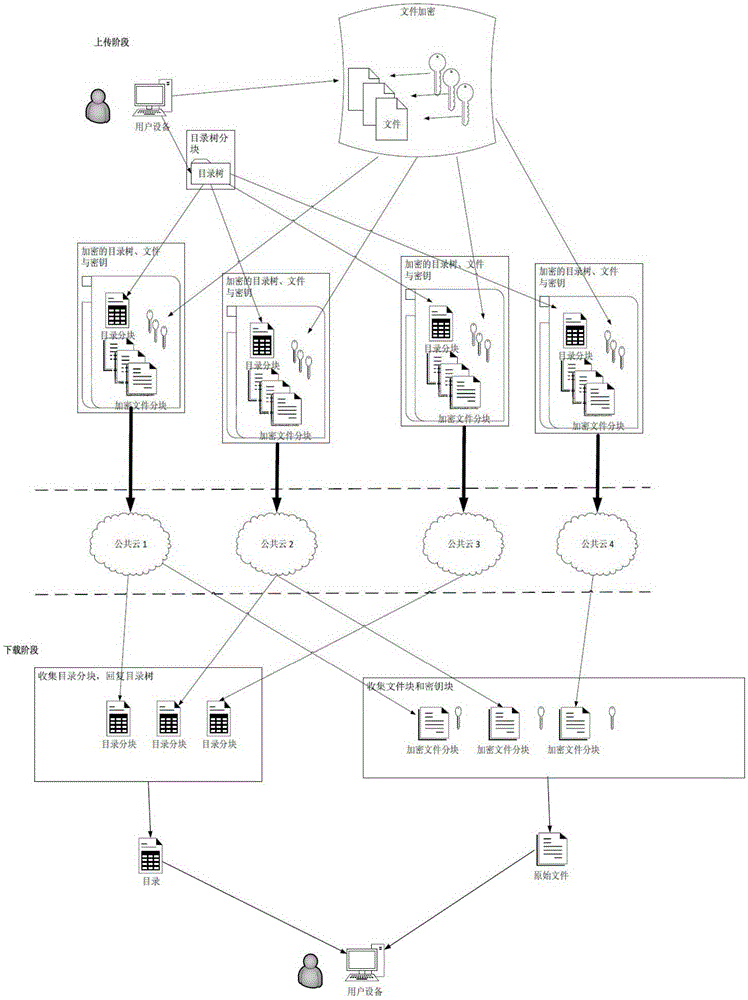
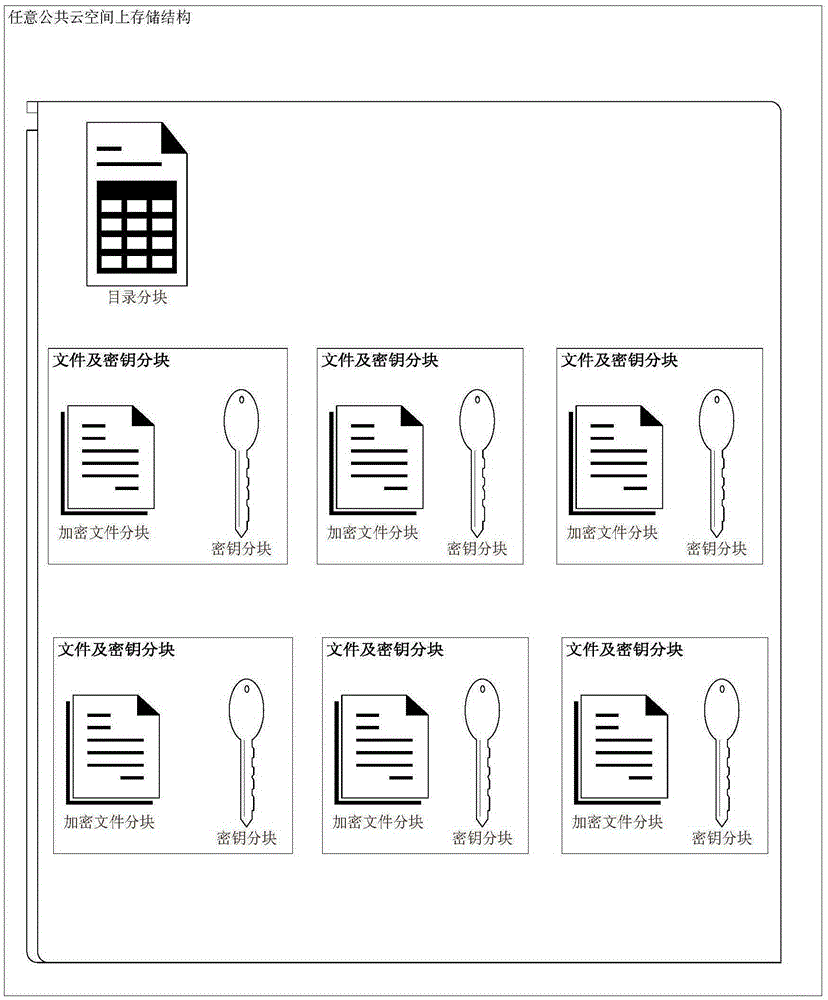
ActiveCN105356997AWon't stealImprove securityKey distribution for secure communicationSpecial data processing applicationsData informationStructure of Management Information
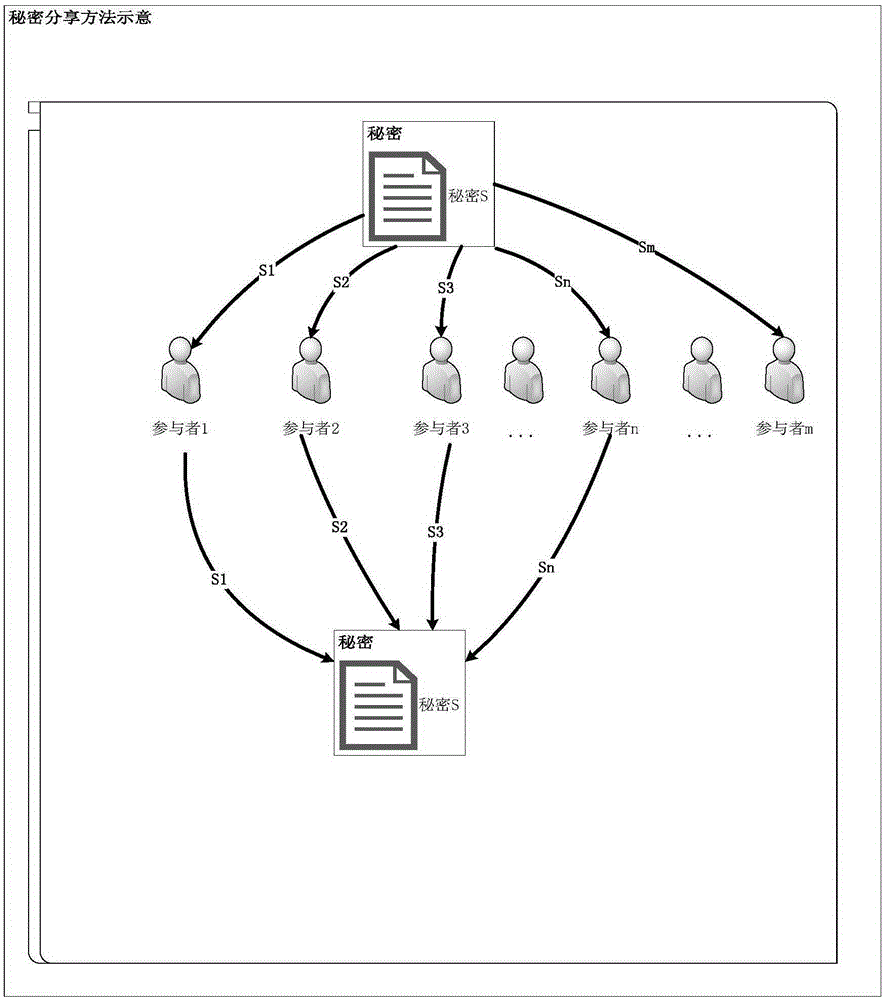
The invention discloses a security distributed data management method based on a public cloud. The security distributed data management method comprises the following steps: assuming that m public cloud spaces exist, extracting a storage directory structure on a local computer, encrypting all files in a directory, dividing each encrypted file into m blocks, sharing and dividing key secrets into m blocks, respectively sending the files and the key blocks into the m public cloud spaces, and sharing directory tree secrets into the m public cloud spaces. In the event of searching a specific file and downloading a file, a directory tree is fetched and restored from any n public cloud spaces at first, wherein n is less than m; the file is searched from the directory tree; then, sub-file blocks and sub-key blocks are continuously fetched from the n public cloud spaces according to the searching result; the file blocks are combined; simultaneously, a key is recovered; and finally, an original file is obtained by decrypting the file. By means of the technical scheme provided by the invention, data information in any insufficient n public cloud spaces is insufficient to recover the original file; therefore, the data information security is increased; and the risk in leaking user data information is reduced.
Owner:SOUTH CHINA AGRI UNIV
Online payment method and online payment system based on IC bank card
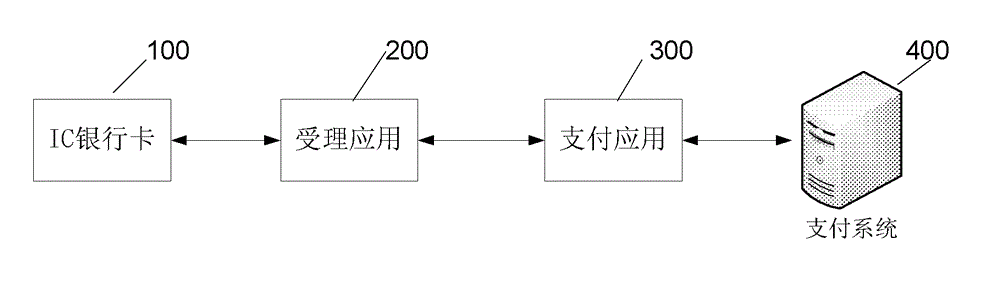
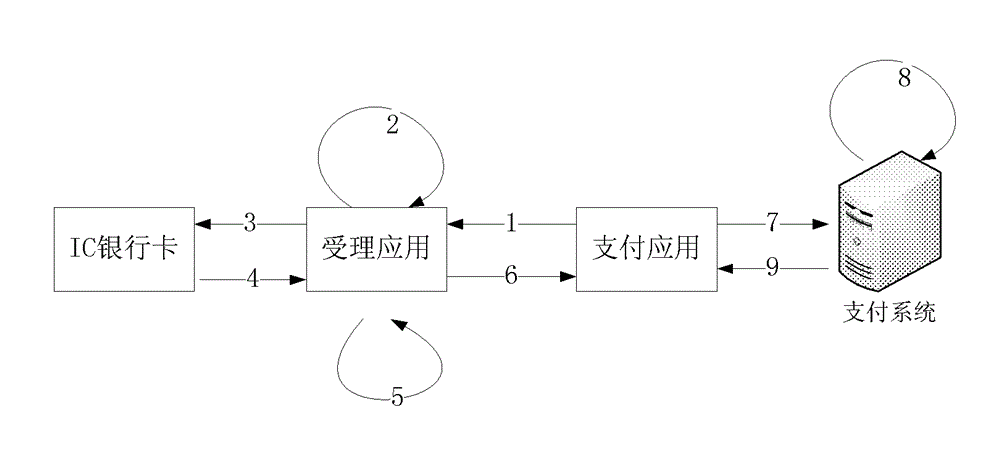
The invention relates to an online payment method and online payment system based on an IC bank card. The online payment method based on the IC bank card comprises a binding activating step and a payment step. The payment step comprises: a first sub step that a payment application initiates a dynamic token generating request to an accepting application; a second sub step that the accepting application verifies whether the dynamic token generating request is valid and initiates a dynamic token acquiring request to the IC bank card if yes; a third sub step that the IC bank card generates dynamic token abstract data according to the dynamic token acquiring request and returns the dynamic token abstract data to the accepting application; a fourth sub step that the accepting application generates a dynamic token according to the acquired dynamic token abstract data and returns the dynamic token to the payment application; a fifth sub step that the payment application transmits a payment request including the dynamic token to a payment system; and six sub step that the payment system authenticates the payment request and completes payment if authentication succeeds.
Owner:CHINA UNIONPAY
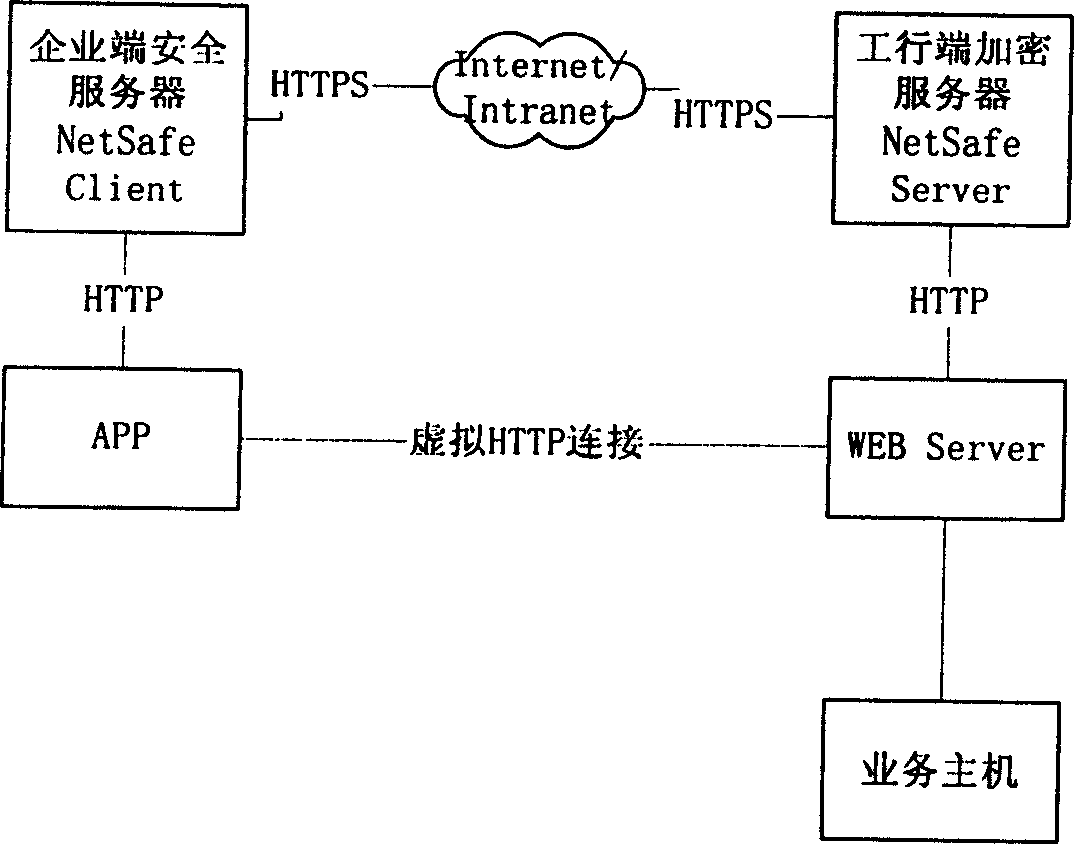
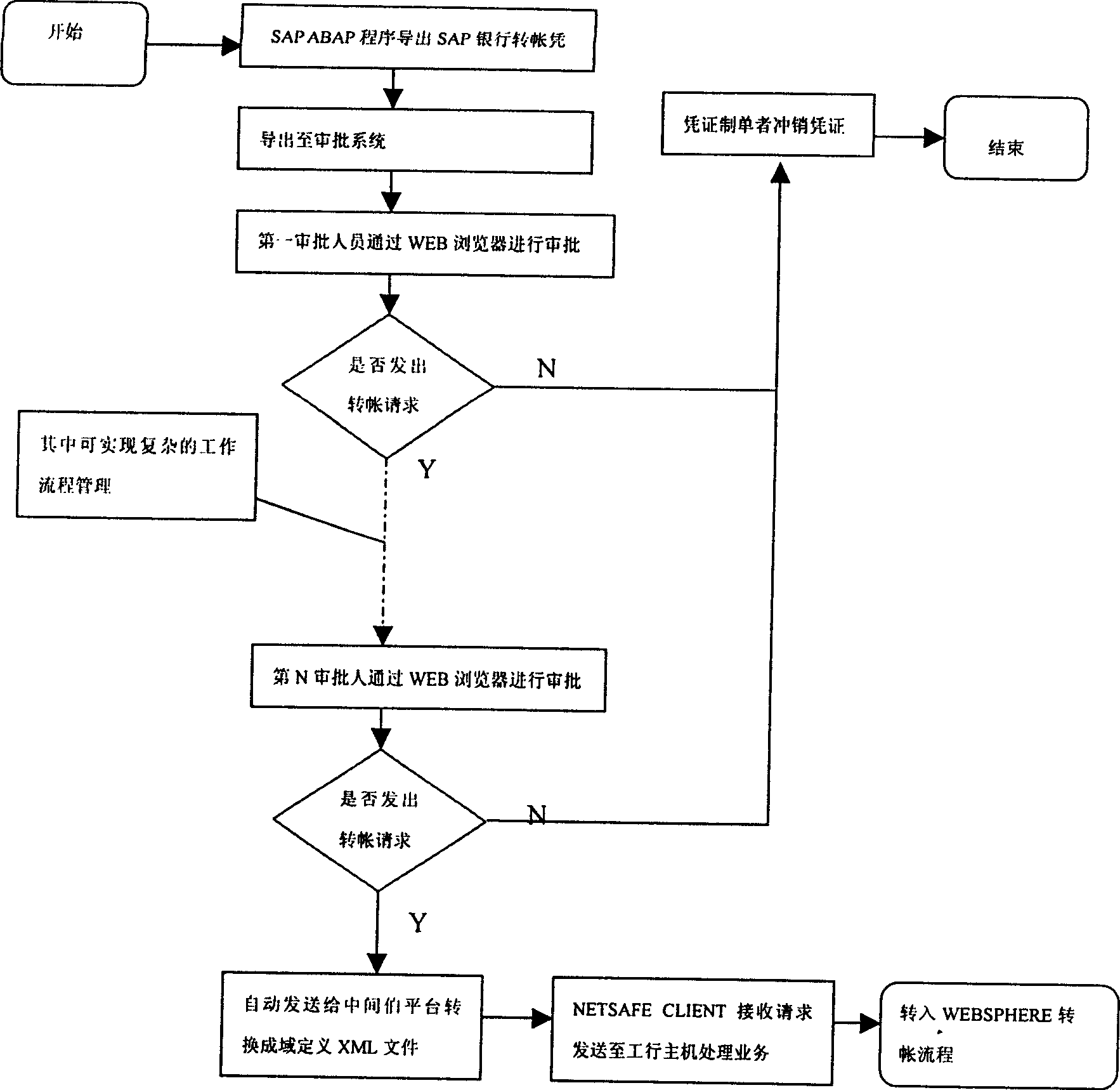
Network bank trade system and method between enterprise and bank
InactiveCN1598841AEnsure safetyWill not be tampered withData switching networksSpecial data processing applicationsPaymentBusiness Personnel
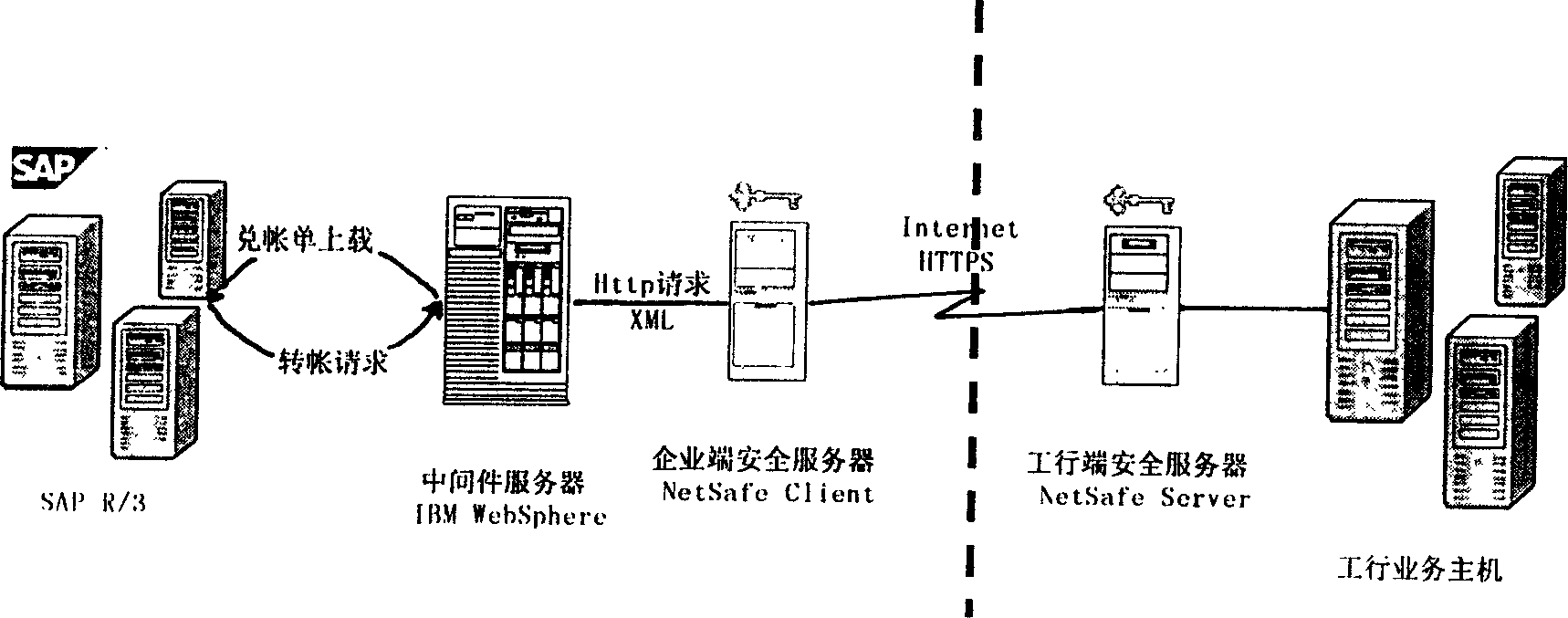
The invention relates to a method of network bank trading between companies and banks. The system includes computer units in bank and company, thereinto, SAP software system is used in company for every finance personnel. Payment service credence is programmed in each client by finance personnel. The payment data is uploaded to company server by special person using eduction program through examination of relative service personnel. Payment check personnel approve payment information through WEB browser in client according to respective rights. Company payment information after approval interacts with bank service host through Internet. In charge of security server in company and bank, trade request is sent to encryption server after encryption and is sent to background to process server after unencrypted by server in bank. At last, the result is returned.
Owner:SINOPEC YANGZI PETROCHEM
High temperature resistant rubber base composite material used for chip packaging and application thereof
InactiveCN102675881AHigh temperature resistantGuaranteed to workSemiconductor/solid-state device detailsSolid-state devicesMicrospherePlasticizer
The invention discloses a high temperature resistant rubber base composite material used for chip packaging and an application thereof, and belongs to the technical field of the high temperature resistant chip packaging material. The invention aims to provide a high temperature resistant, moisture-proof and damp-proof chip packaging composite material. The high temperature resistant rubber base composite material used for the chip packaging adopts the technical scheme that the high temperature resistant rubber base composite material used for the chip packaging comprises the following raw materials in parts by weight: 100 parts of silicon rubber, 0.1-2 parts of plasticizer, 1-10 parts of reinforcing agent, 50-100 parts of heat insulation microsphere and 1-15 parts of vulcanizing agent. The plastic rubber base composite material related by the invention has a high temperature resistant characteristic, a radio frequency identification device (RFID) chip can be comprehensively protected to normally work in the high temperature environment, the chip is free from being damaged due to overheat at the temperature of 300DEG C, and the packaged chip has an excellent moisture-proof and damp-proof performance.
Owner:NO 33 RES INST OF CHINA ELECTRONICS TECHNOOGY GRP
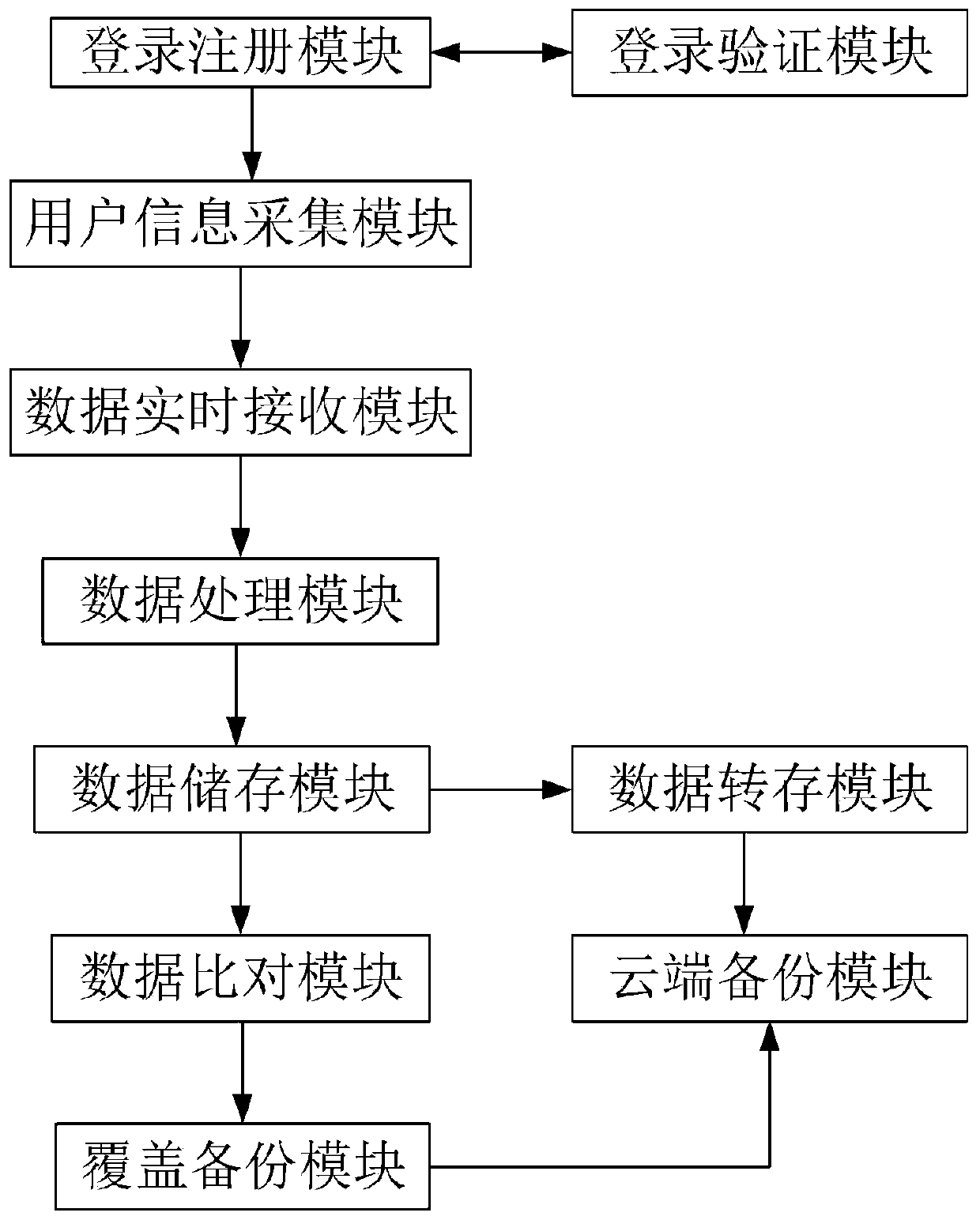
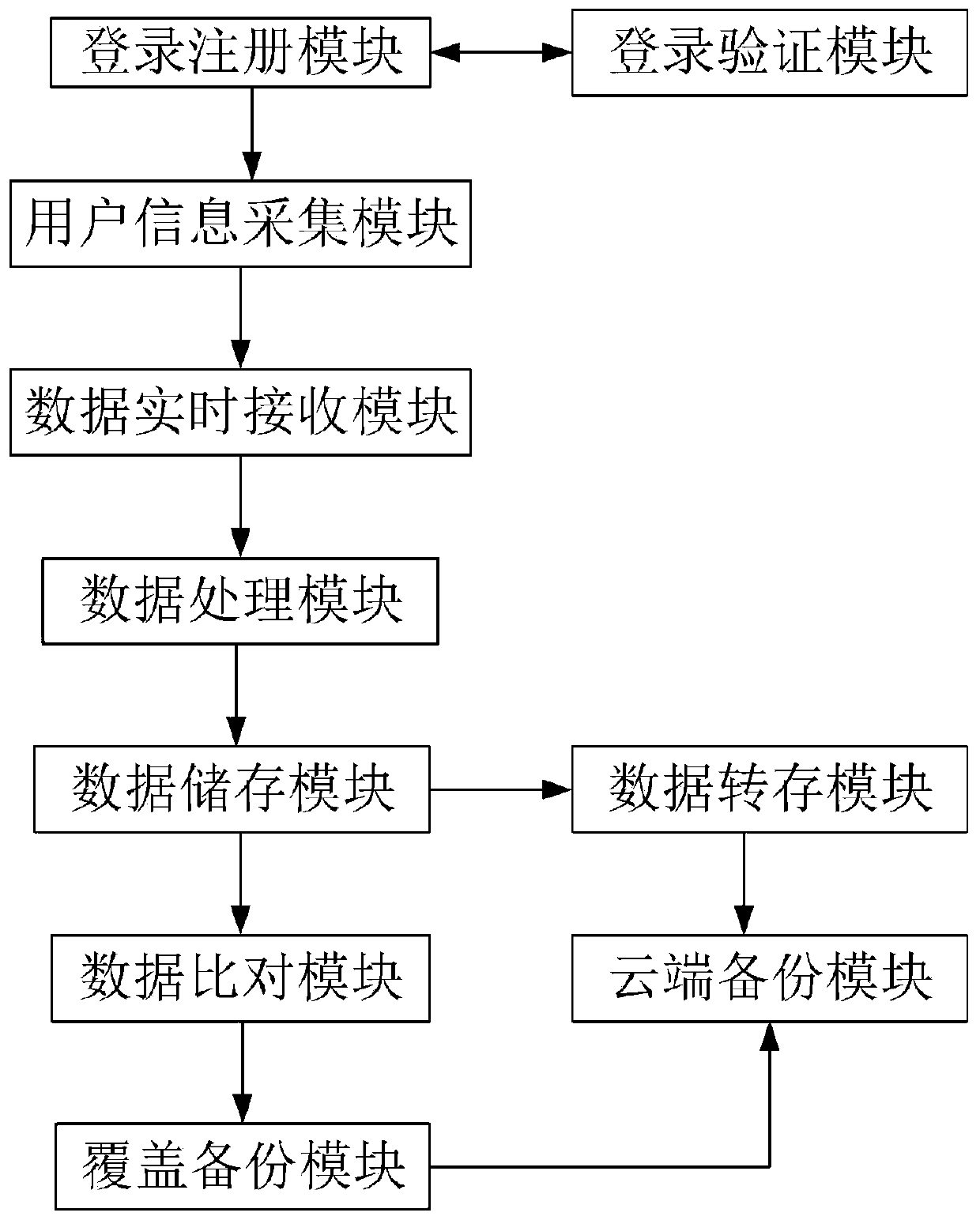
File storage intelligent backup system based on big data
InactiveCN110032476AImprove securityImprove comfortDigital data protectionDigital data authenticationData processingData analysis
The invention discloses a file storage intelligent backup system based on big data. The file storage intelligent backup system comprises a login registration module, a login verification module, a user information acquisition module, a data real-time receiving module, a data processing module, a data storage module, a data comparison module, a data transfer module, a cloud backup module and a coverage backup module, wherein the login registration module is in communication connection with the login verification module; the login and registration module is also in communication connection withthe user information acquisition module; the user information acquisition module is in communication connection with the data real-time receiving module, the data real-time receiving module is in communication connection with the data processing module, the data storage module is in communication connection with the data analysis module, and the data comparison module is in communication connection with the data storage module; in addition, the file storage security of the system can be better guaranteed, and meanwhile file storage can be better and more conveniently carried out.
Owner:LIUZHOU RAILWAY VOCATIONAL TECHN COLLEGE
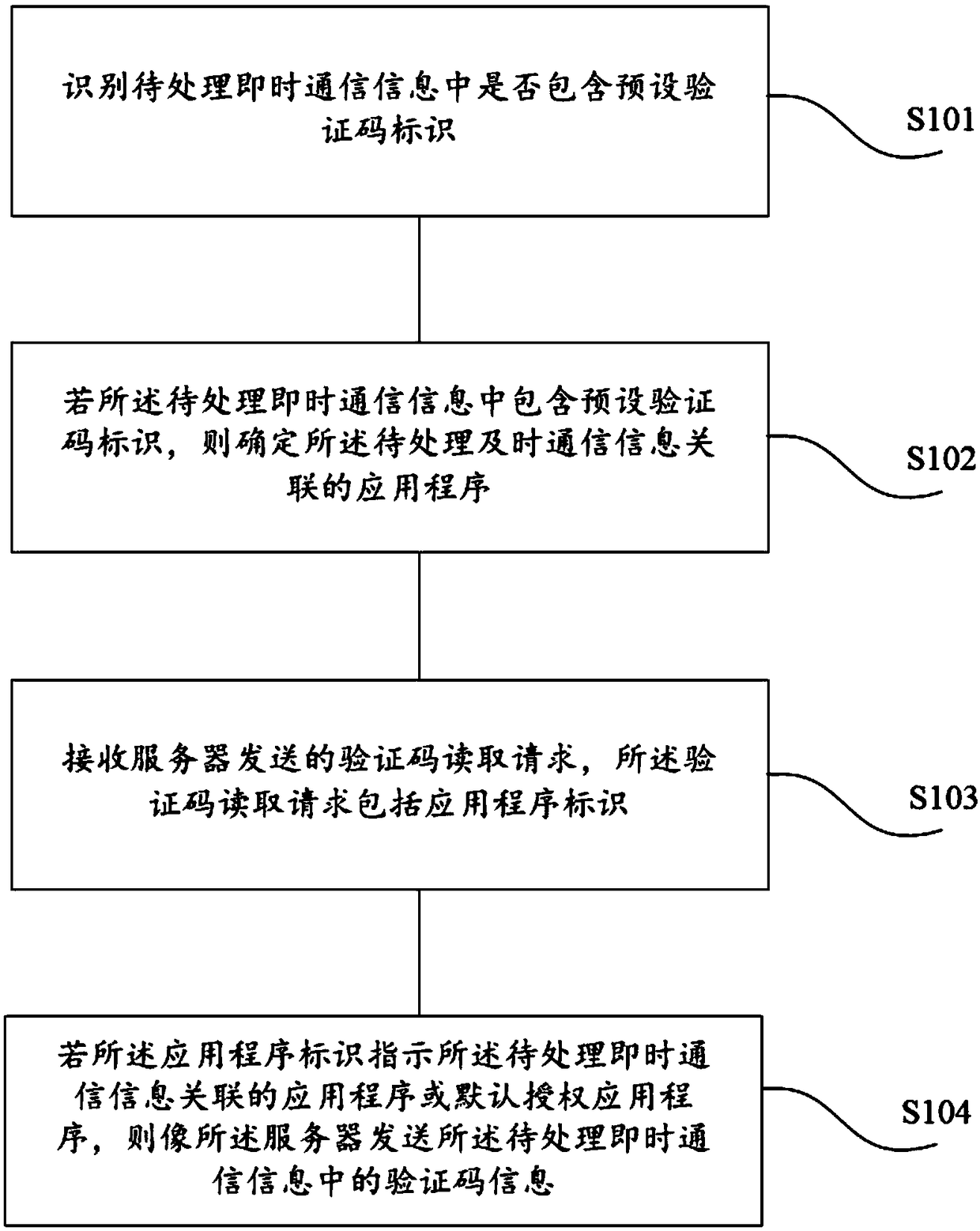
Instant messaging information verification code protection method and device
InactiveCN109245902AEnsure safetyWon't stealUser identity/authority verificationProgram/content distribution protectionApplication softwareAuthorization
The invention provides an instant messaging information verification code protection method and device, and relates to the field of communication. The method includes the steps: identifying whether to-be-processed instant messaging information includes a preset verification code identifier or not; determining an application program associated with the to-be-processed instant messaging informationif the to-be-processed instant messaging information includes the preset verification code identifier; receiving a verification code reading request sent by the server, wherein the verification code reading request includes an application identifier; enabling the server to send the verification code information in the to-be-processed instant messaging information if the application identifier indicates the application program associated with the to-be-processed instant messaging information or a default authorization application program. Compared with the prior art, the method guarantees the security of a mobile phone application or a personal account, and guarantees that the SMS verification code c not stolen by the rogue software.
Owner:XIAMEN MEITU MOBILE TECH CO LTD
Delivering device, self-service equipment and control method of self-service equipment
ActiveCN108346224AImprove storage space utilizationSolve the problem of low storage space utilizationCoin-freed apparatus detailsApparatus for dispensing discrete articlesEngineeringMechanical engineering
The invention aims at providing a delivering device, self-service equipment and a control method of the self-service equipment. The delivering device comprises a box body, and the box body comprises opposite front opening and rear opening; the front opening is communicated with the rear opening to form an article delivering channel; a gate is arranged in the rear opening and is used for closing oropening the rear opening. By means of the delivering device, the self-service equipment and the control method of the delivering device, the problem in the prior art that the storage space of the self-service equipment is low in utilization rate can be solved.
Owner:SHANDONG NEW BEIYANG INFORMATION TECH CO LTD
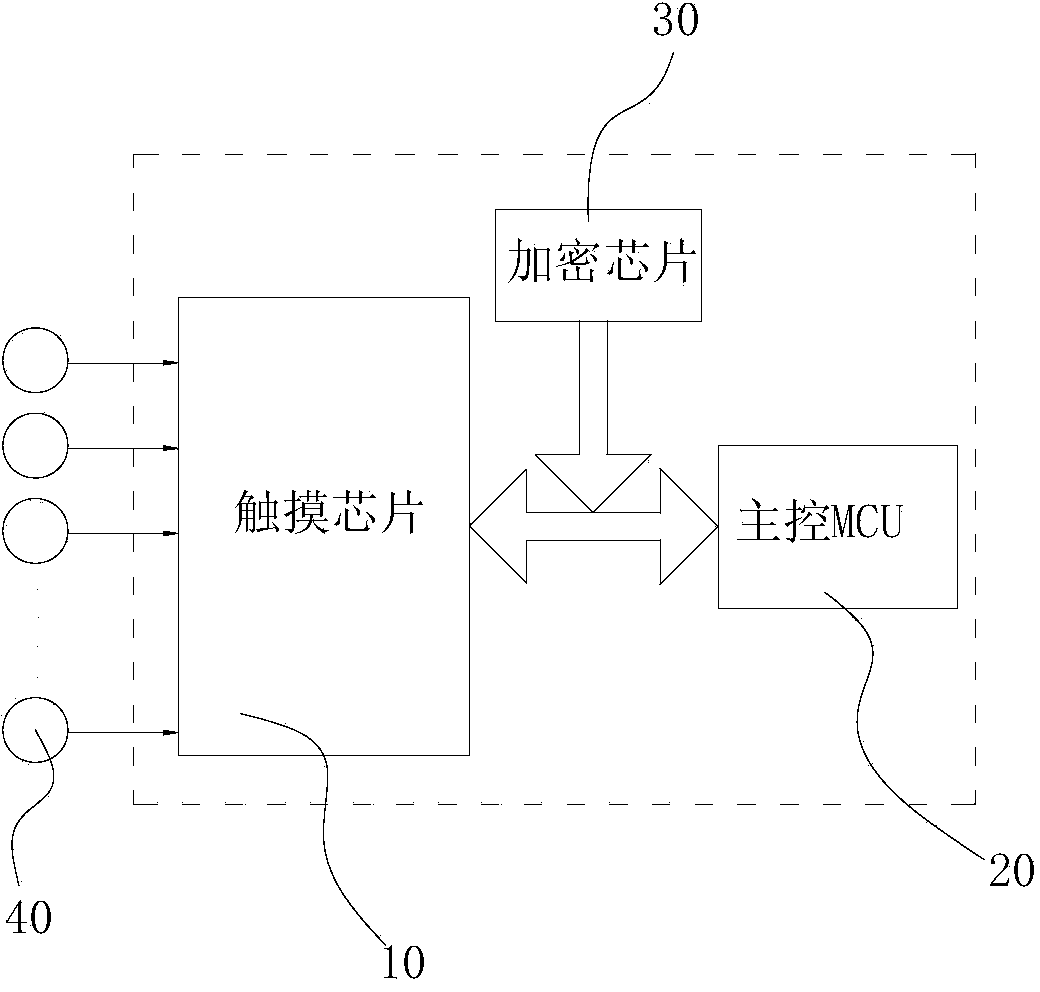
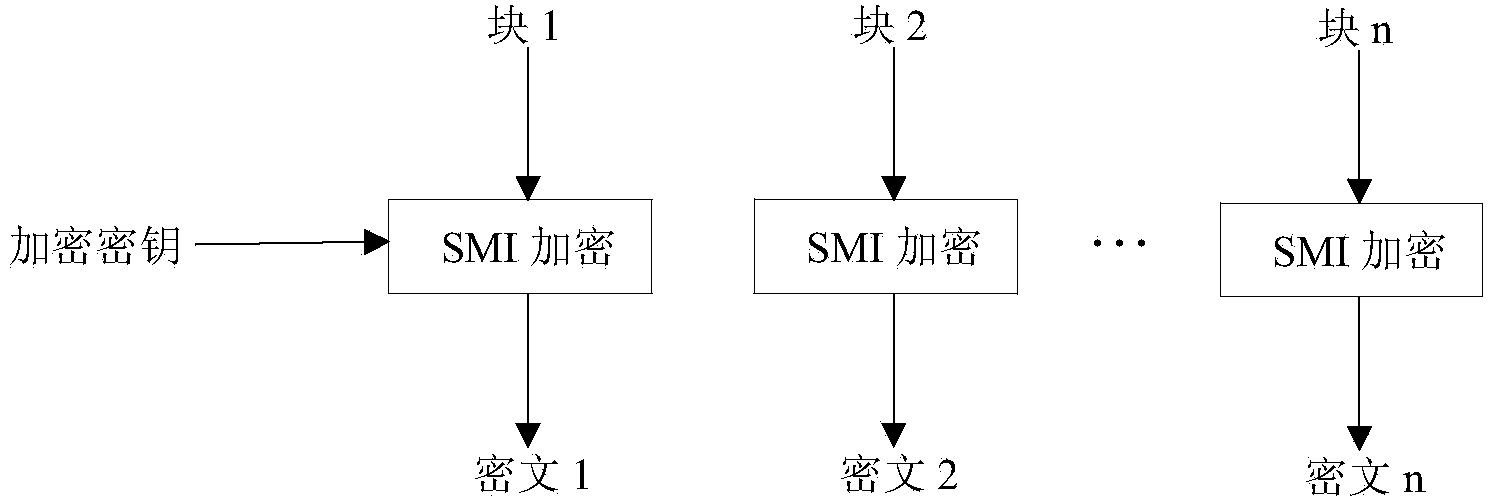
Touch keyword using national cipher SM1 encryption chip and encryption method thereof
InactiveCN103853340ADefense against replay attacksWon't stealInput/output for user-computer interactionUser identity/authority verificationTransfer procedureNetwork packet
The invention discloses a touch keyword using a national cipher SM1 encryption chip and an encryption method thereof. The touch keyword using the national cipher SM1 encryption chip comprises a touch chip, a master control MCU (Microprogrammed Control Unit) and a data guide wire which is used for connecting the master control MCU and the touch chip; the data guide wire is an I2C bus of a two-wire serial bus; and the I2C bus is also connected with the national cipher SM1 encryption chip. By using a hardcore type national cipher SM1 encryption chip, a collection data packet collected by the touch chip is encrypted, transmitted to the master control MCU and then decrypted again, so that the touch keyword using the national cipher SM1 encryption chip is capable of ensuring that touch sensing information is not stolen in the transmission process and guaranteeing safety of data application; and the touch keyword using the national cipher SM1 encryption chip is especially applicable to a payment terminal of financial products.
Owner:GUANGDONG HUADA INTERNET CO LTD
Reminding method, device and terminal
ActiveCN106803928AImprove experienceWon't stealCharacter and pattern recognitionClosed circuit television systemsPublic placeComputer science
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Secure communication method and device based on identity authentication
ActiveCN110881048AWon't stealIncrease flexibilityUser identity/authority verificationSecure communicationCiphertext
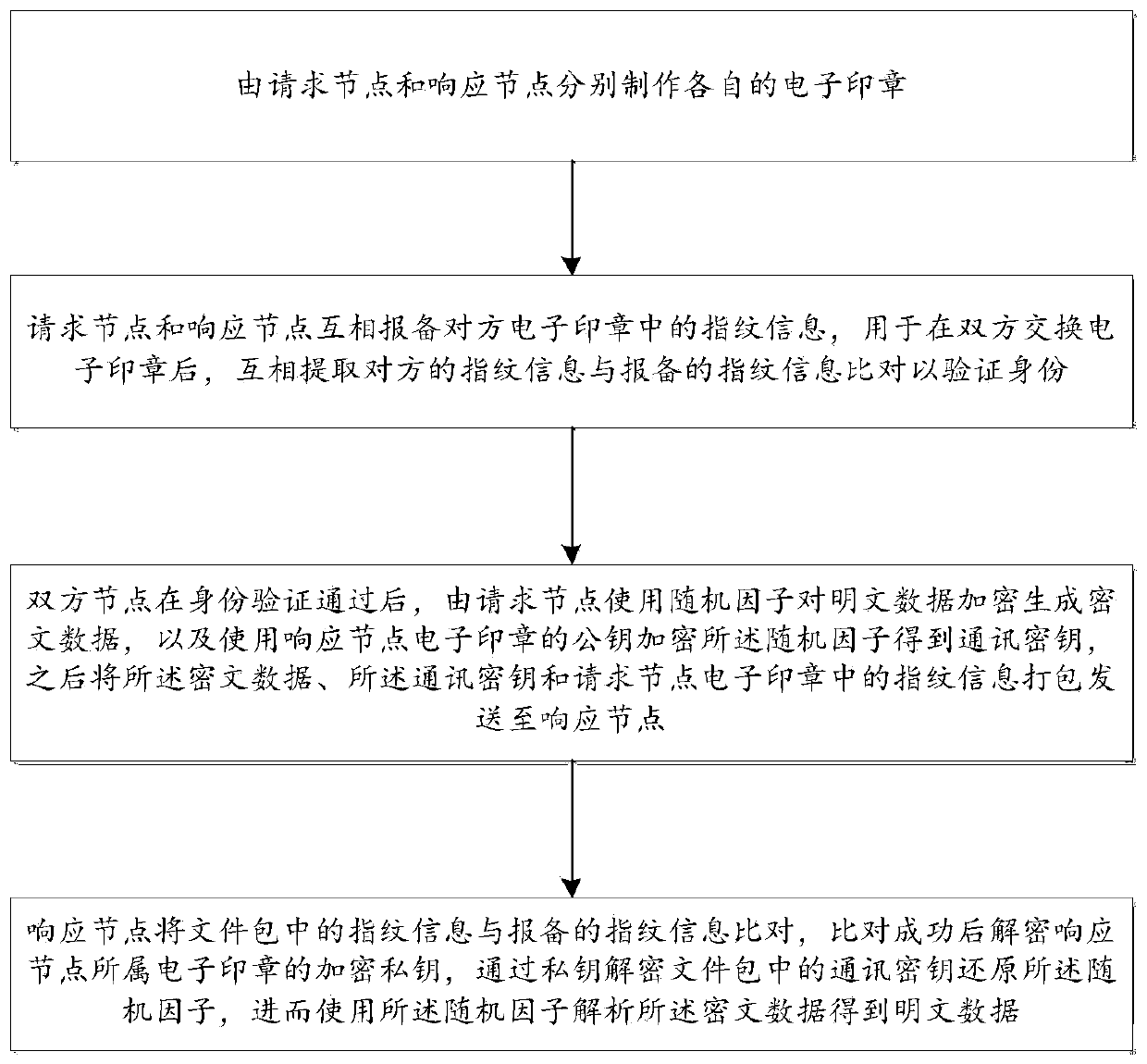
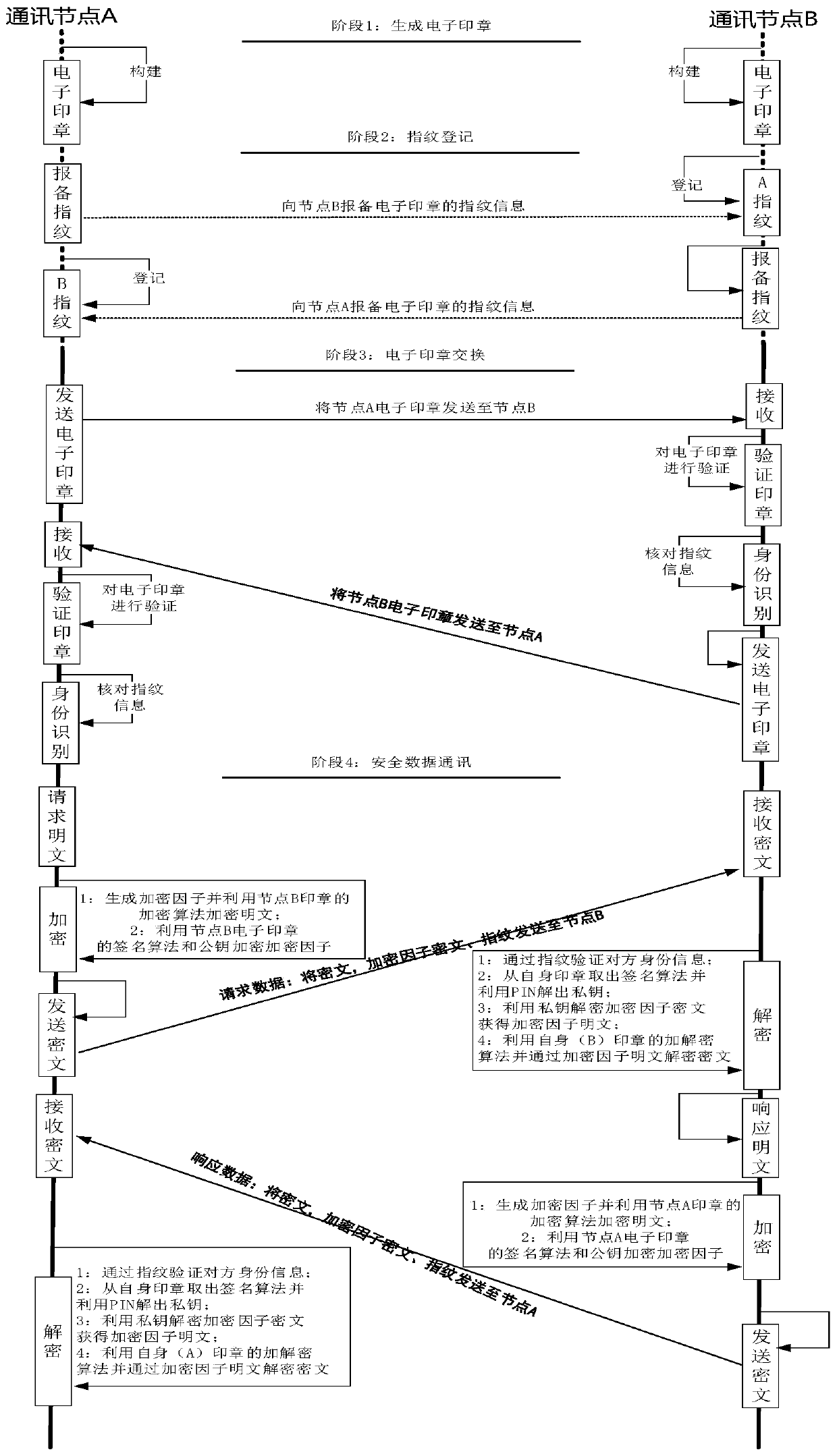
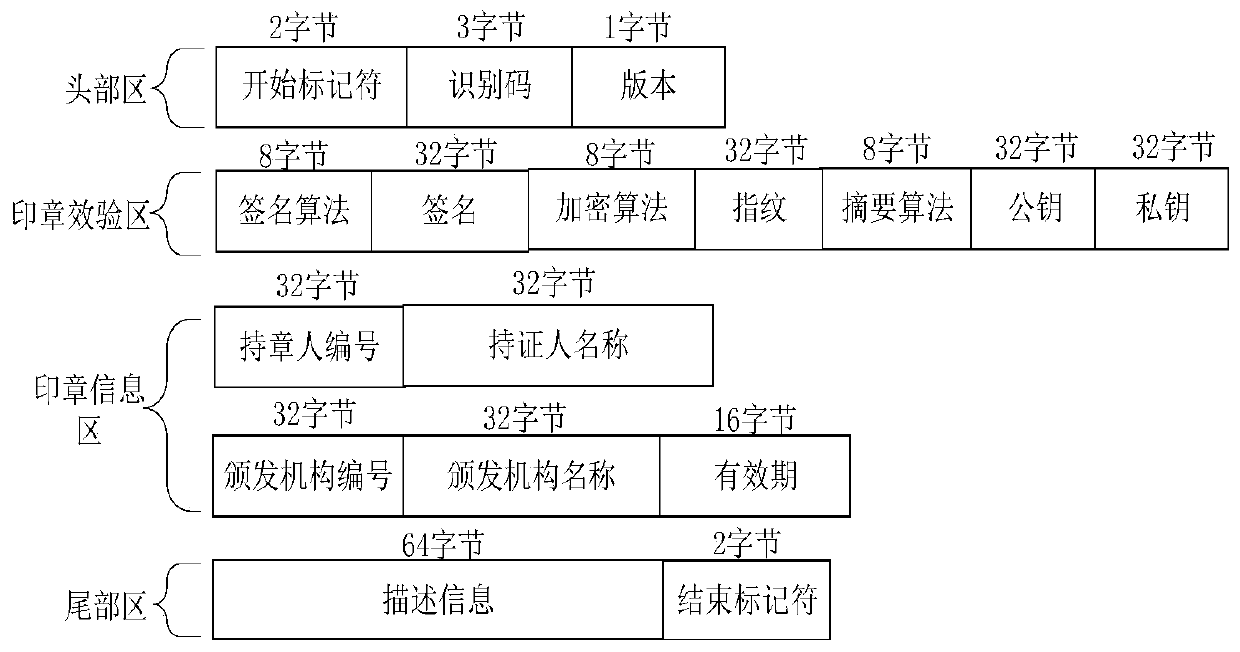
The invention discloses a secure communication method and device based on identity authentication, and the method and device can achieve the flexible and efficient verification of identity informationof two communication sides through electronic seals of two forced authentication sides under the condition that there is no need to apply for a digital certificate from a CA mechanism, and guaranteesthe safety of communication data. The method comprises the following steps that: a request node and a response node respectively manufacture respective electronic seals; the request node and a response node report fingerprint information in electronic seals of the opposite side; the request node encrypts plaintext data by using a random factor to generate ciphertext data, encrypts the random factor by using a public key of the electronic seals of an opposite side to obtain a communication key, and then packages and sends the ciphertext data, the communication key and the fingerprint information to the response node; and the response node compares the fingerprint information in the file package with the reported fingerprint information, decrypts the encrypted private key of the electronicseals to which the response node belongs after successful comparison, decrypts the communication key through the private key to restore the random factor, and analyzes the ciphertext data to obtain plaintext data.
Owner:SUNING CLOUD COMPUTING CO LTD
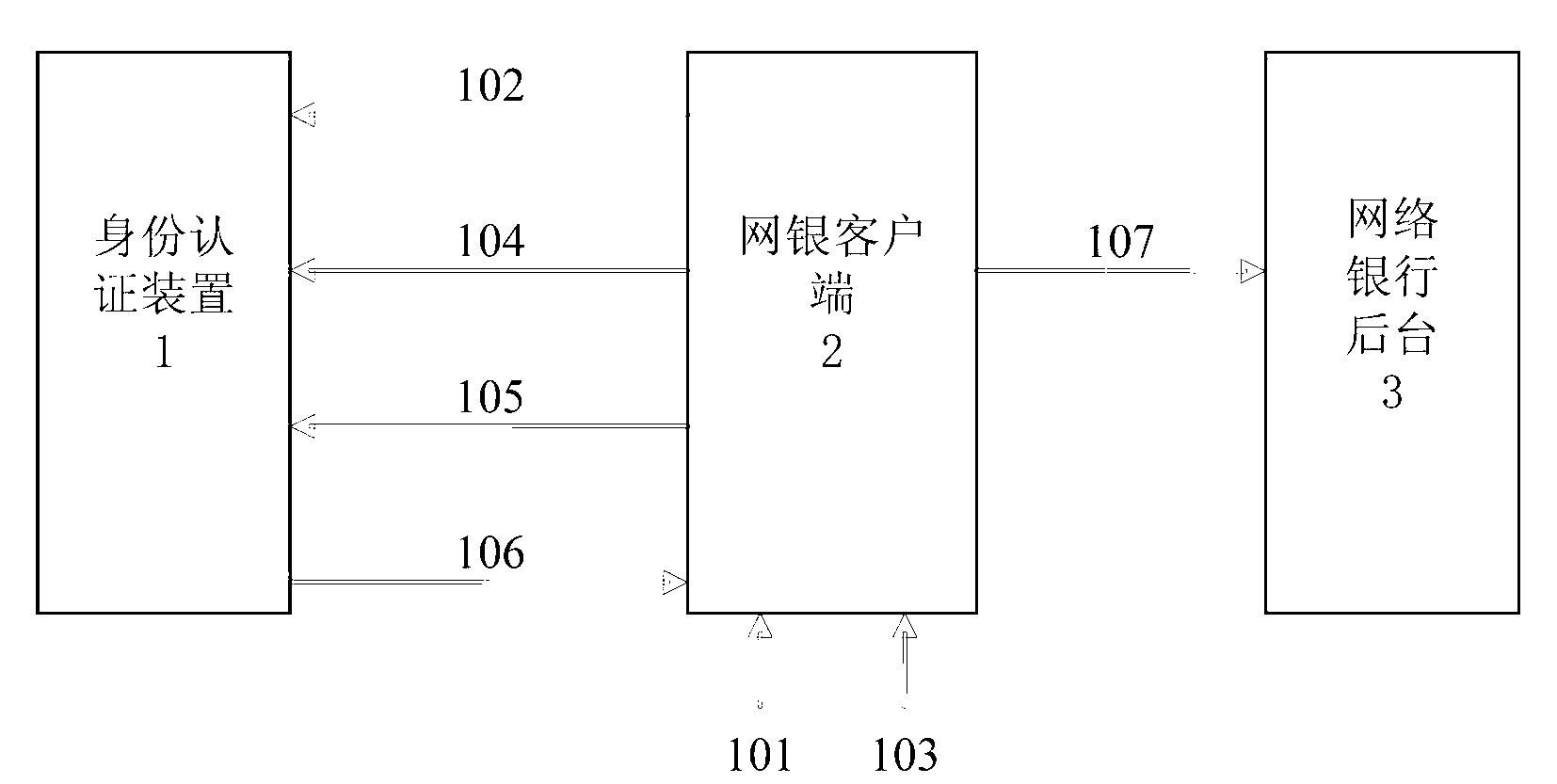
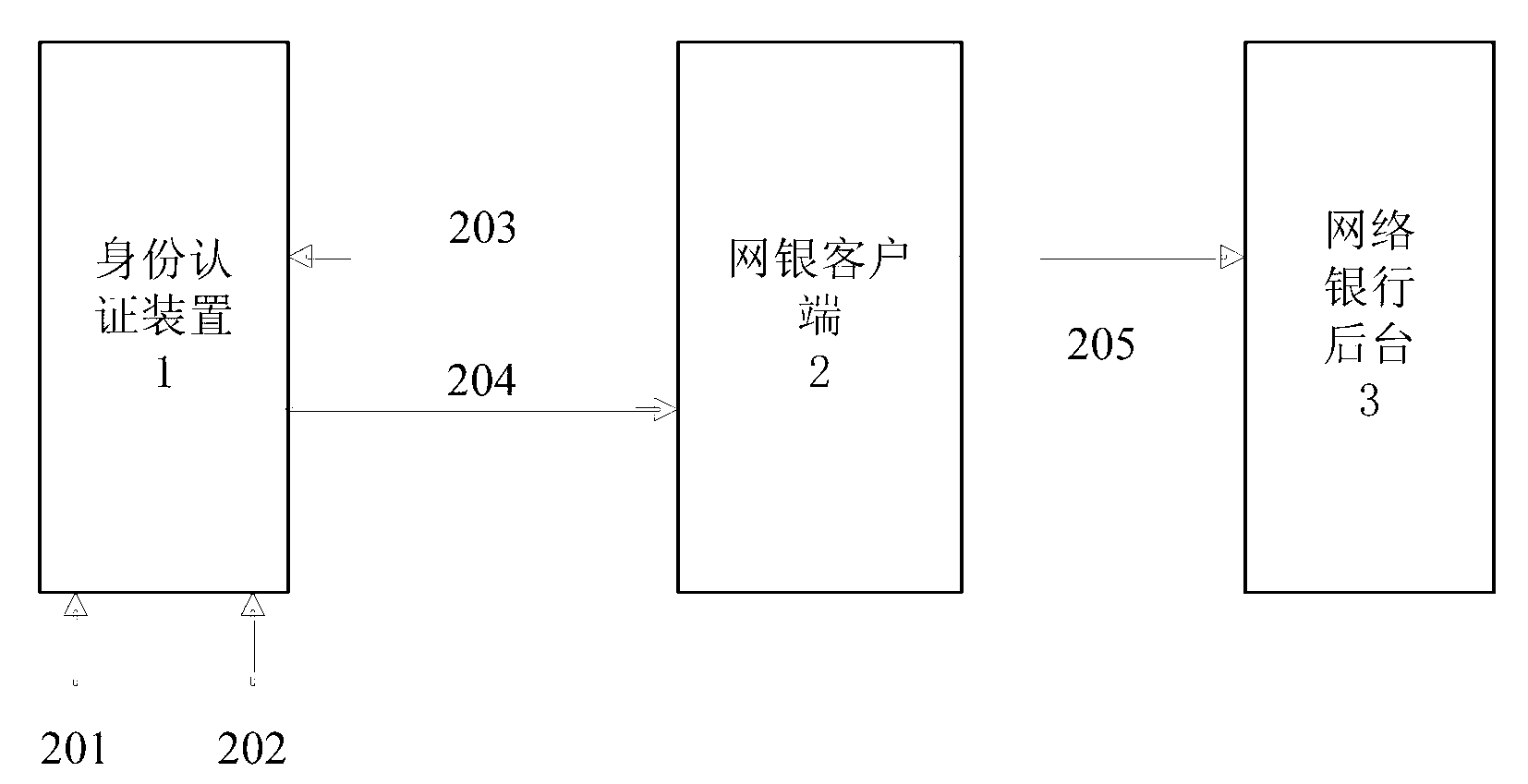
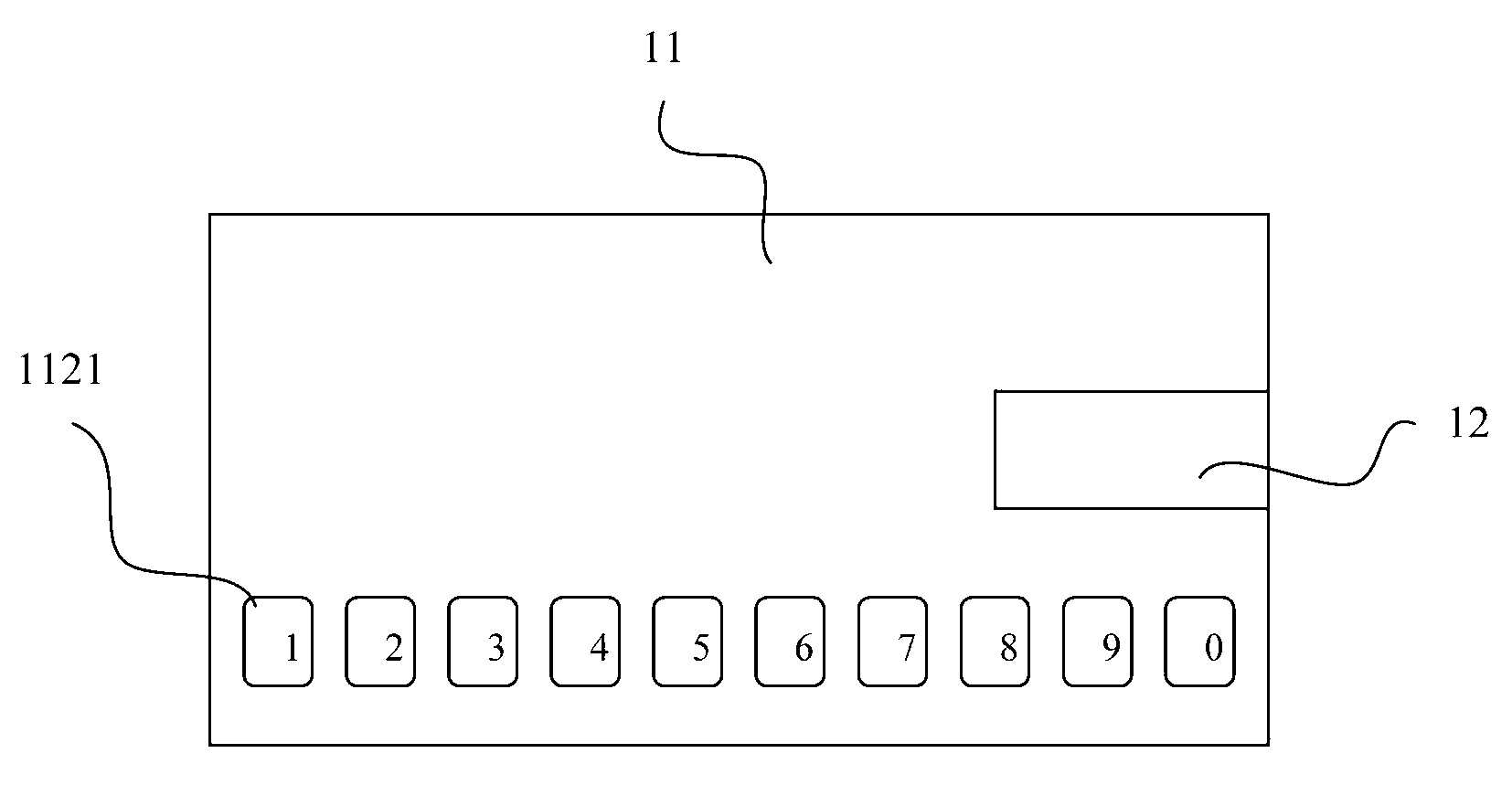
Online bank identity authentication method and apparatus thereof
An online bank identity authentication method and an apparatus thereof are disclosed. The method comprises the following steps: setting an apparatus, wherein the apparatus comprises a processor, an interface connected with the processor and a keyboard; inputting an authorization code via the keyboard, wherein after the authorization code is verified to be qualified, the processor carries out digital signature processing on external equipment via data provided by the interface and the processed data is returned to the external equipment via the interface. Through inputting the authorization code and an account password on the apparatus which is independent of an online bank client, the authorization code and the account password can be ensured not to be stolen so as to effectively guarantee safety of an identity authentication process.
Owner:SHENZHEN ZHENGTONG ELECTRONICS
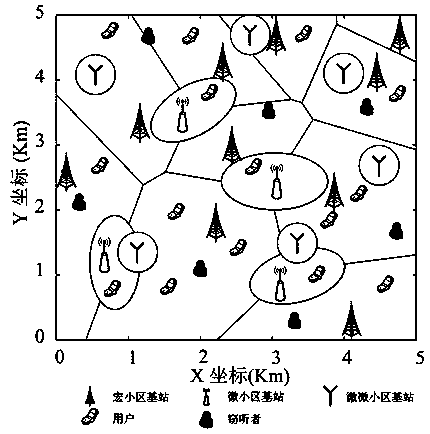
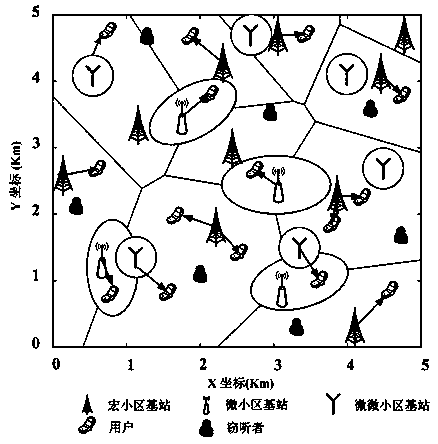
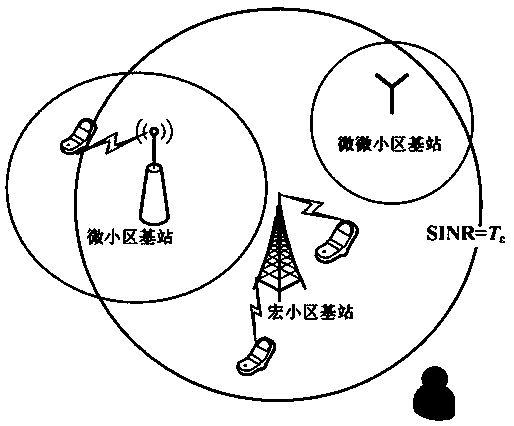
Physical layer security methods based on non-optimal user cascading scheme in heterogeneous network
ActiveCN109302703AImprove throughputImprove spectral efficiencyPower managementSecret communicationPathPingSpectral efficiency
The invention discloses physical layer security methods based on a non-optimal user cascading scheme in a multilayer heterogeneous network and belongs to the technical field of wireless communication.According to the methods, a multilayer heterogeneous network model in a passive eavesdropping scene is analyzed through description of node distribution density, a base station transmitting power, path loss indexes and a bias factor of each layer. The problem that the optimal base stations are difficult to connect is solved by the provided method based on the non-optimal user cascading scheme. According to the scheme, network nodes are modeled into a homogeneous Poisson point process through utilization of stochastic geometry. On the basis of a stochastic geometry mathematical tool, a physical layer security probability expression of the multilayer cellular heterogeneous network is inferred. Influence of the transmitting powers, security thresholds and eavesdropper density on a system security probability is compared and analyzed according to obtained security probabilities. The method has obvious advantages in the aspect of improving physical layer security of the system. A network coverage probability and average user capacity are improved. Throughput and spectral efficiency of the network are also improved.
Owner:NORTHWEST NORMAL UNIVERSITY
Wheat drying device and operation method thereof
InactiveCN109405456AQuick drying jobWon't stealBatteries circuit arrangementsElectric powerScrew threadTimer
The invention discloses a wheat drying device and an operation method thereof. The wheat drying device comprises an airing plate. The top of the airing plate is fixedly connected with a baffle plate.The front end and the rear end of the two sides of the inner cavity of the baffle are fixedly connected with threaded rods through bearings, and the left side of the inner cavity of the baffle plate is in threaded connection with a material turning plate. According to the wheat drying device and the operation method thereof, the airing plate, the baffle plate, the threaded rod, a material turningplate, a belt disc, a belt, a first motor, a yarn net rack, a spring, supporting legs, a supporting rod, a bottom plate, a supporting plate, a crank connecting rod mechanism, a second motor, a drivingbevel gear, a driven bevel gear, a mounting rod, a solar panel, a storage battery, a protection box, a photovoltaic converter, a processor, a storage module and a timer are arranged and matched witheach other to use, the wheat can be quickly aired, and time and labor are saved, so that the airing efficiency is greatly improved; moreover, birds cannot be eaten and cannot be mixed with the silt,so that great convenience is brought to later collecting and assembling.
Owner:许昌泰禾农业科技发展有限公司
Mechanical anti-theft charging bin
PendingCN108258759AStrong reliabilityReduce energy consumptionElectric powerSafety/protection circuitsElectromagnetic lockTorsion spring
The invention discloses a mechanical anti-theft charging bin. The charging bin comprises a strip-shaped base, a buckle mechanism and an electromagnetic lock mechanism; insertion slots are formed in the upper side face of the strip-shaped base at intervals; the buckle mechanism comprises buckle units the number of which correspond to that of the insertion slots; each buckle unit comprises a lock hook swing arm, a torsion spring, a tension spring, a thrust jacking plate, a fixing shaft and a mounting base; the electromagnetic lock mechanism is mounted on the strip-shaped base, and each telescopic lock lever conducts blocking and limiting on a locking position of the corresponding lock hook swing arm. According to the mechanical anti-theft charging bin, the lock hook swing arms, the torsion springs, the tension springs, the thrust jacking plates, the fixing shafts and the mounting bases are adopted for constituting all the buckle units; by means of a pure mechanical structure, insertion locking and automatic ejection of a charging pal are achieved. The mechanical anti-theft charging bin has excellent reliability, and the power consumption of a power supply can be reduced.
Owner:海南小魔科技有限公司
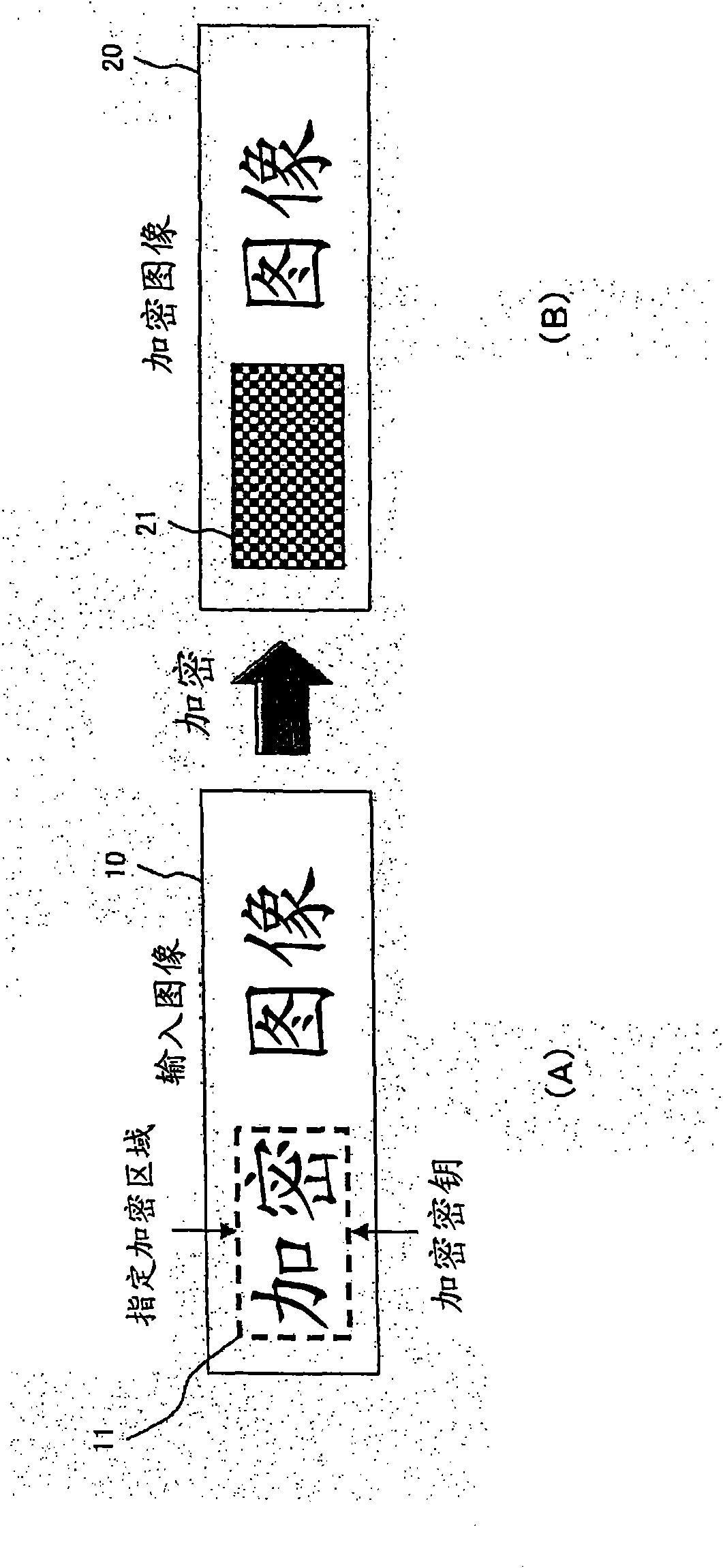
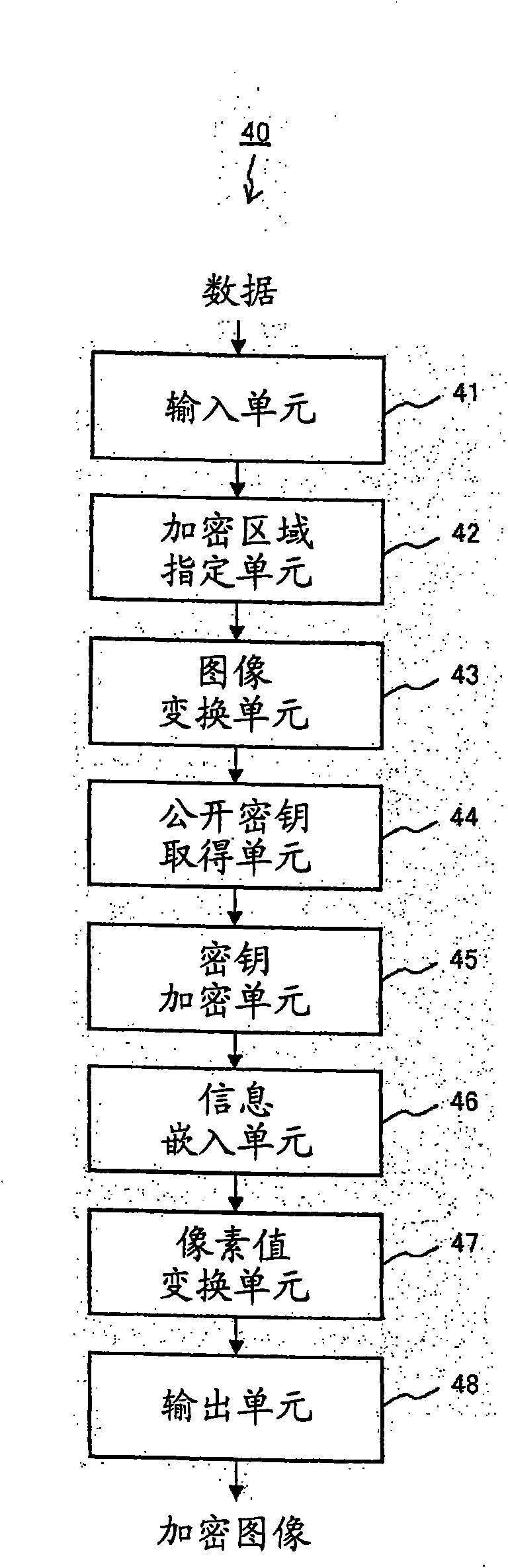
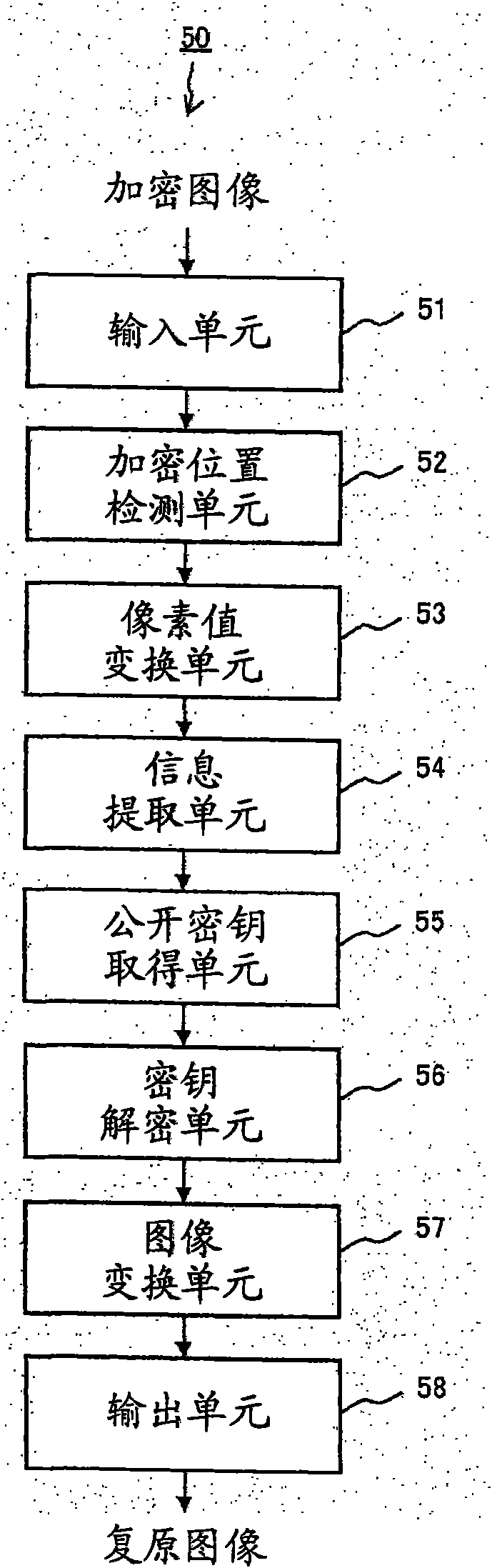
Image encrypting device, image decrypting device, method and program
InactiveCN101682503AWon't stealKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareImaging data
An image encrypting device according to the present invention generates a finally encrypted image sequentially by converting an image of a specified region in an input image with an encryption key, byembedding information obtained by encrypting the encryption key with a public key pairing with the private key of a transmission destination, and by performing pixel value conversion. Then, the encrypted image is transmitted to the transmission destination as a printed matter or via a network. An image decrypting device according to the present invention converts the encrypted image in the form of print data or electronic data into an image, and inputs the image. Next, the image decrypting device extracts a decryption key (the encryption key) from the image of the encryption region by executing a process reverse to the process of the image encrypting device according to the present invention for the encryption region of the encrypted image converted into the image data. Then, the image decrypting device decrypts the original image of the encrypted region by using the decryption key, and restores the entire encrypted image.
Owner:FUJITSU LTD
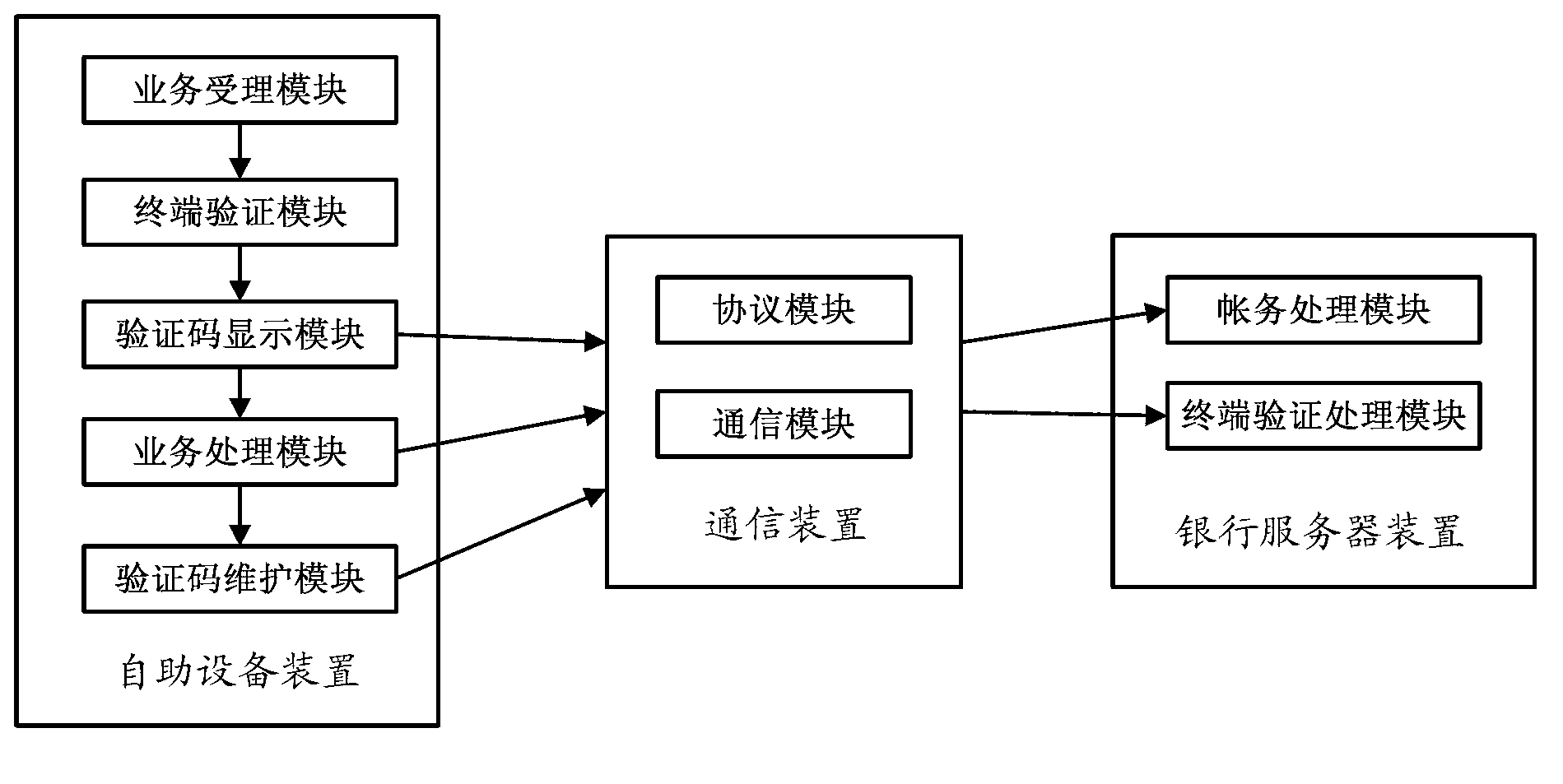
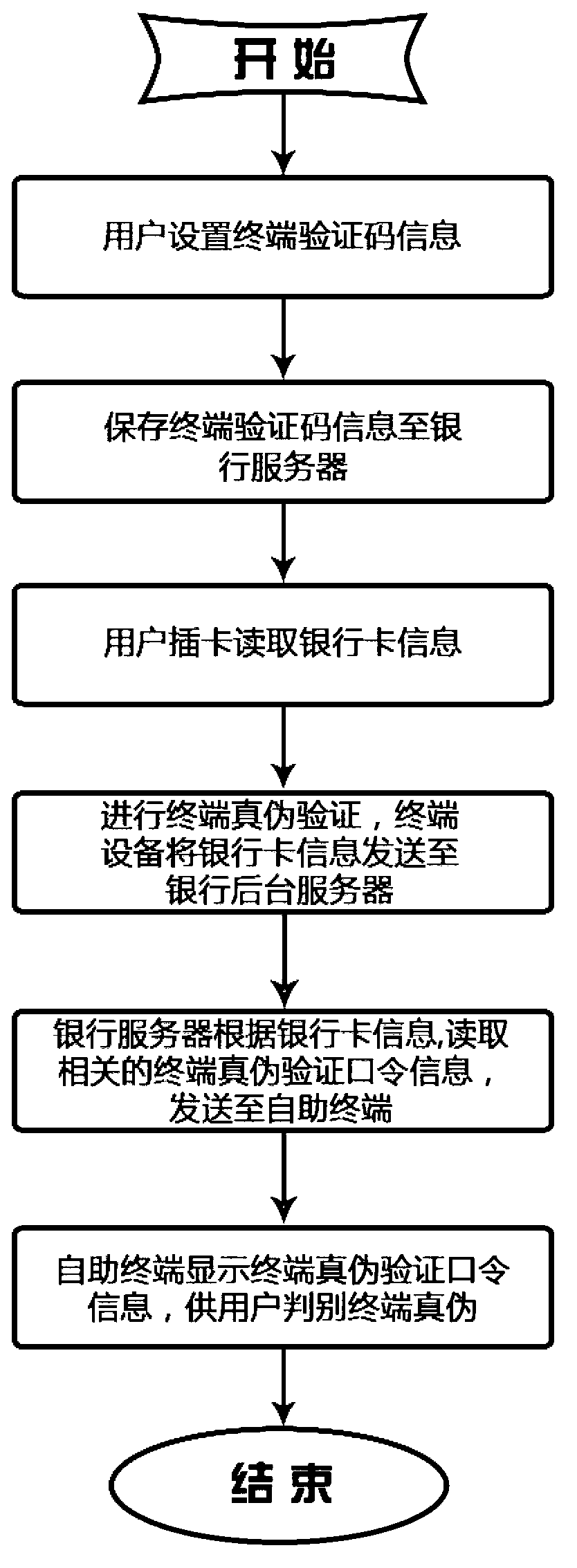
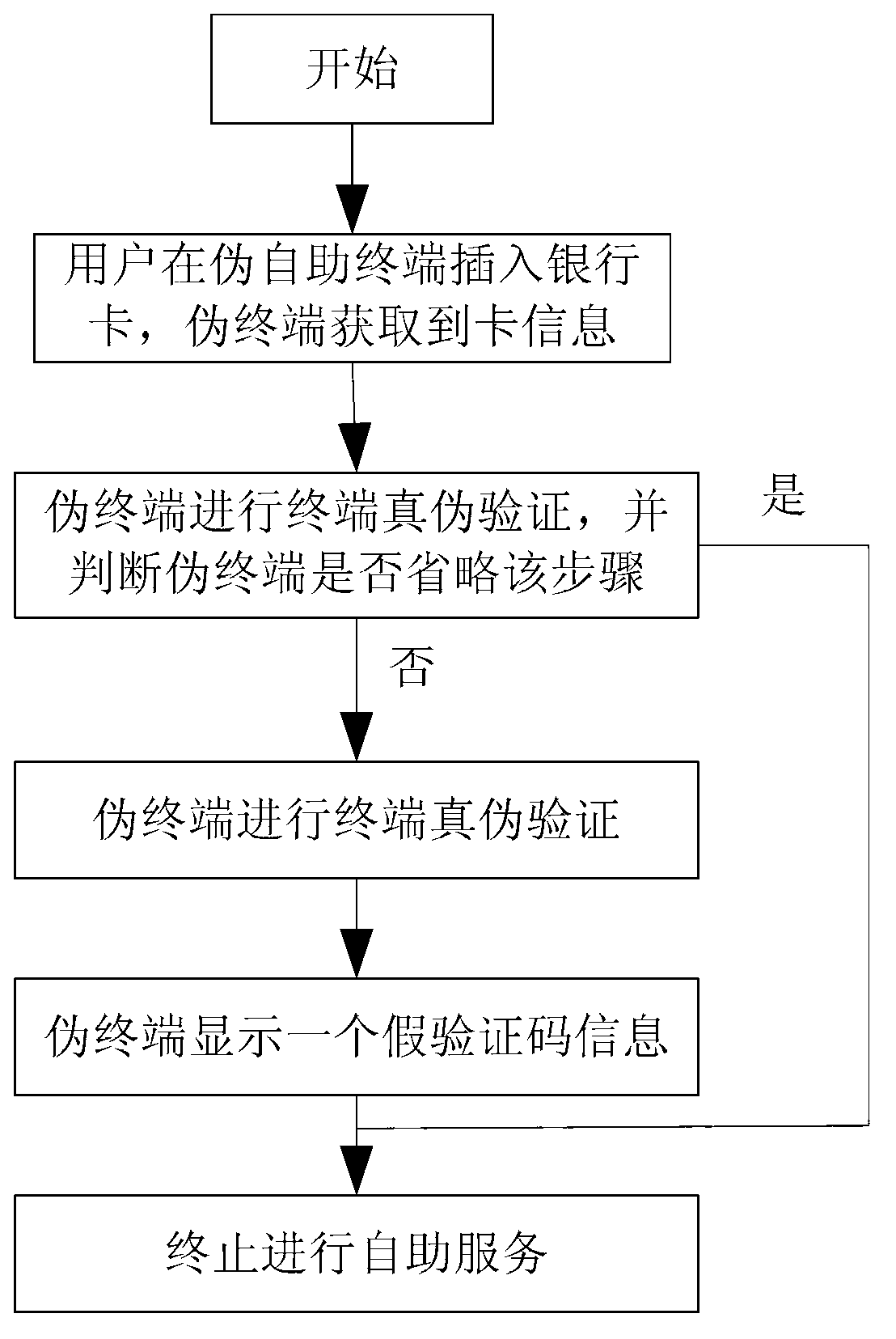
System and method for verifying authenticity of financial self-service terminal
InactiveCN103268676AWon't stealEliminate the disadvantages of unreliabilityComplete banking machinesTelecommunications linkPassword
The invention discloses a system and a method for verifying the authenticity of a financial self-service terminal. The system comprises a self-service apparatus, a communication device and a bank server device; the self-service apparatus can be financial self-service terminal equipment capable of providing deposit, withdrawal deposit or account transfer service for users, or terminal equipment capable of providing financial services by requiring password entry and card insertion operation; the communication device can be communicated with a bank host instantly to finish the financial self-service for users, and the communication device is used for connecting a customer and the communication links of a bank service host; and the bank server device is a service system capable of managing user account information and deposit of the user. According to the system and the method for verifying the authenticity of the financial self-service terminal, the operation is simple, the verification is convenient, no extra communication channels are needed, the cost is lower, the verification can be realized only by utilizing the existing communication links of the self-service terminal and the bank host, more importantly, the defects caused by the second communication link such as a mobile device and unreliable information source are completely eradicated.
Owner:GUANGZHOU KINGTELLER TECHNOLOGY CO LTD
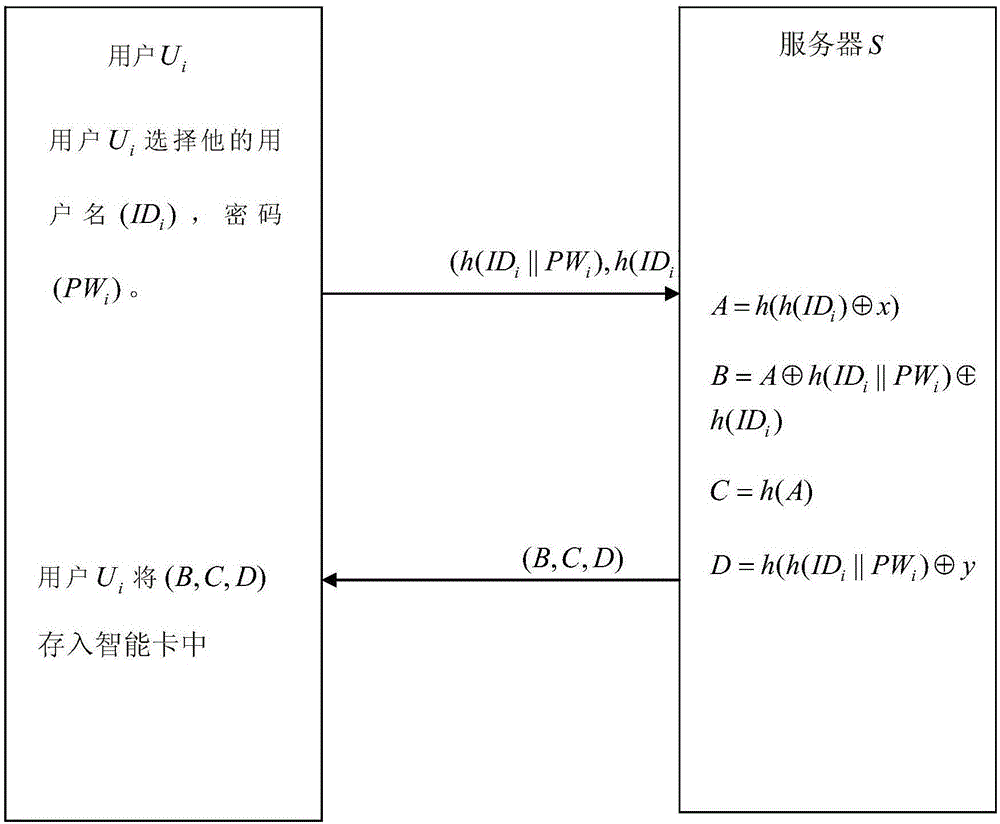
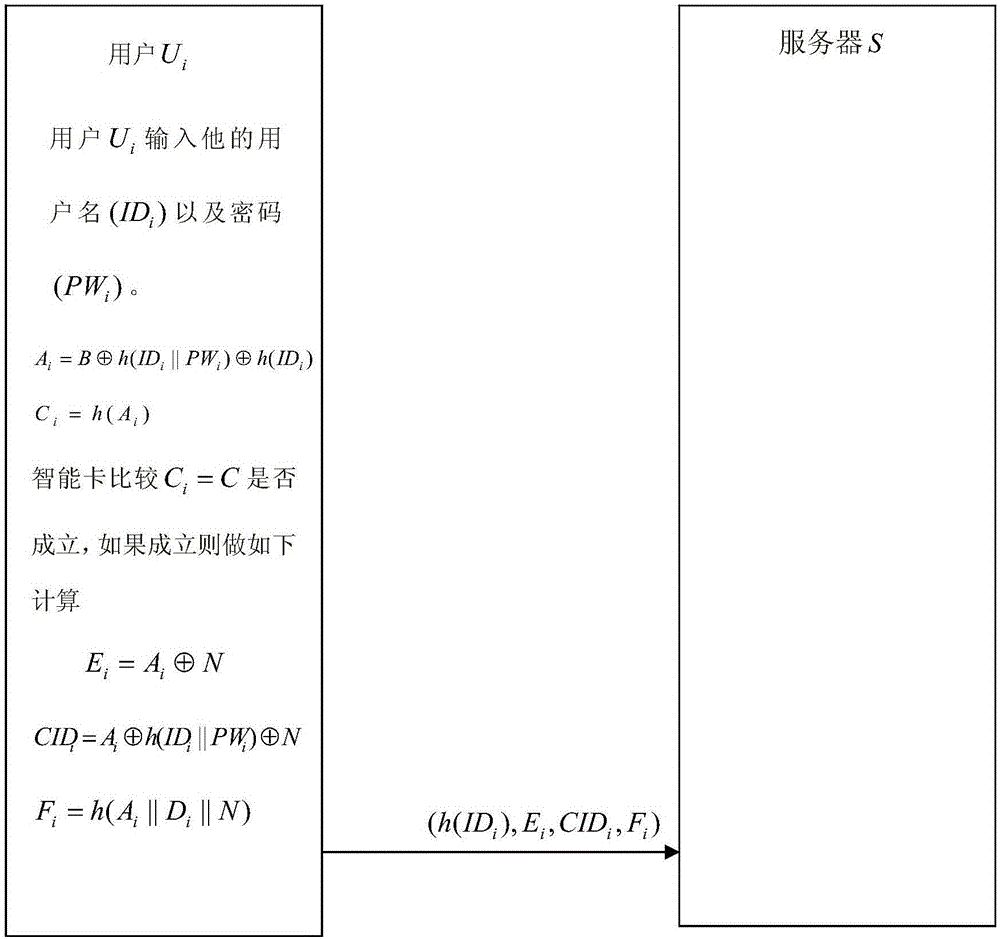
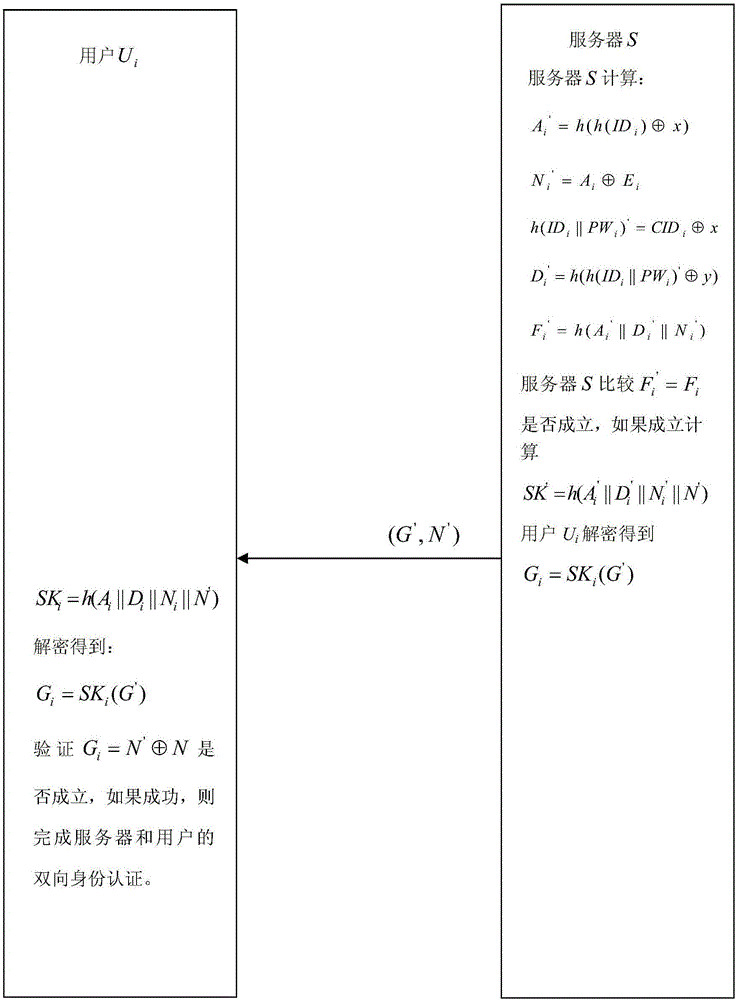
Password authentication method with high security
ActiveCN106230840ARelieve pressureProtect user informationTransmissionHash functionInformation transmission
The invention discloses a password authentication method with high security. By employing the mode of combining smart card hardware with a cipher algorithm, the method can be applied to the security mechanism of a series of network services such as finance, online shopping, social activities, and security. According to the method, the combination of a smart card and password authentication is focused, four stages of user registration, login, mutual authentication of a server and a user, and user password change are included, lightweight, high-efficiency and secure cipher protocols and methods such as Hash function, XOR operation, and symmetric keys are mainly applied, the security is high, special security processing of usernames and passwords is performed in an information transmission process, the stolen risk for the usernames and the passwords is reduced, replay attacks and information block attacks can be effectively prevented, and the users can freely change the passwords without the server.
Owner:NANJING UNIV OF POSTS & TELECOMM
Key management-based access control method suitable for pay television system
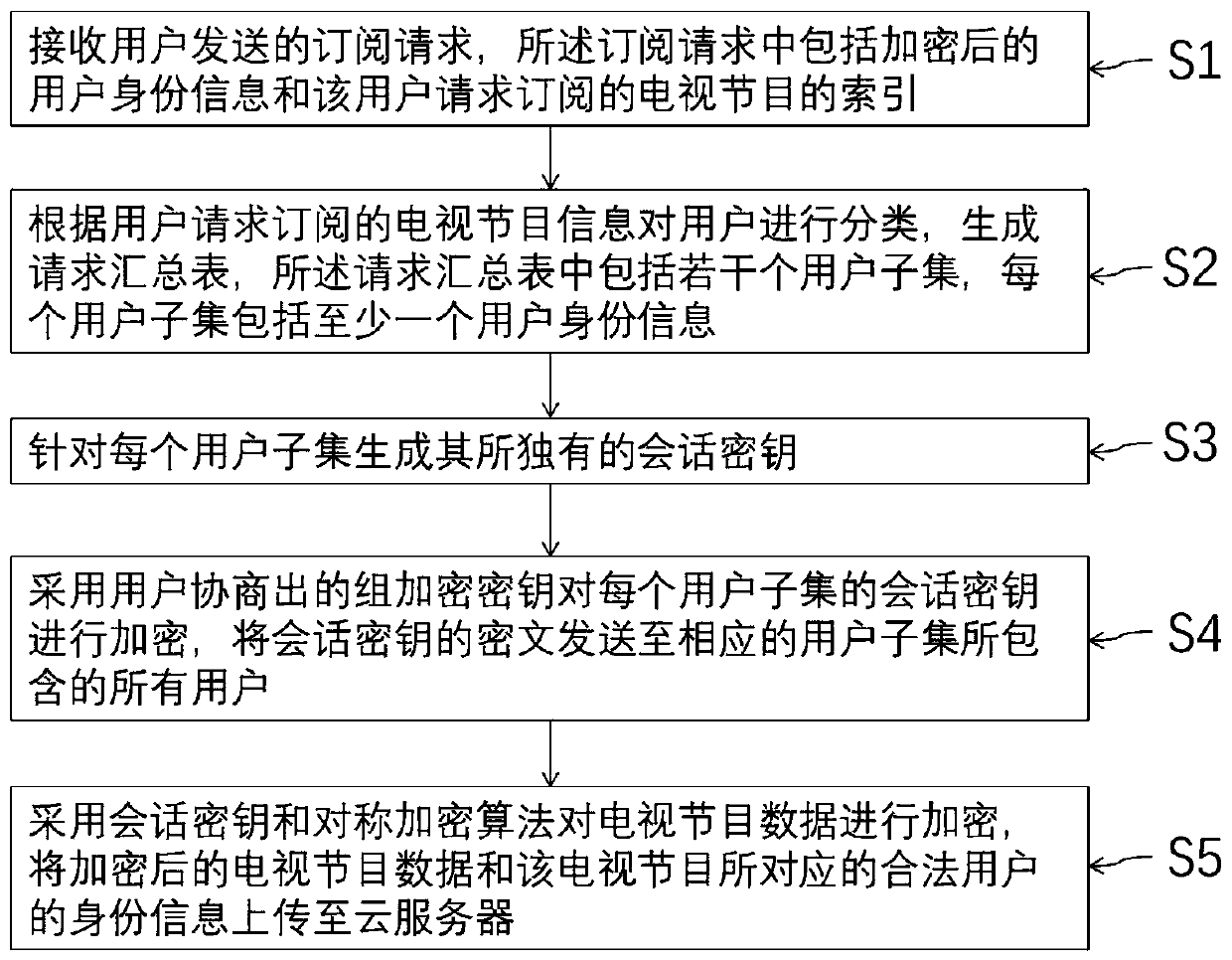
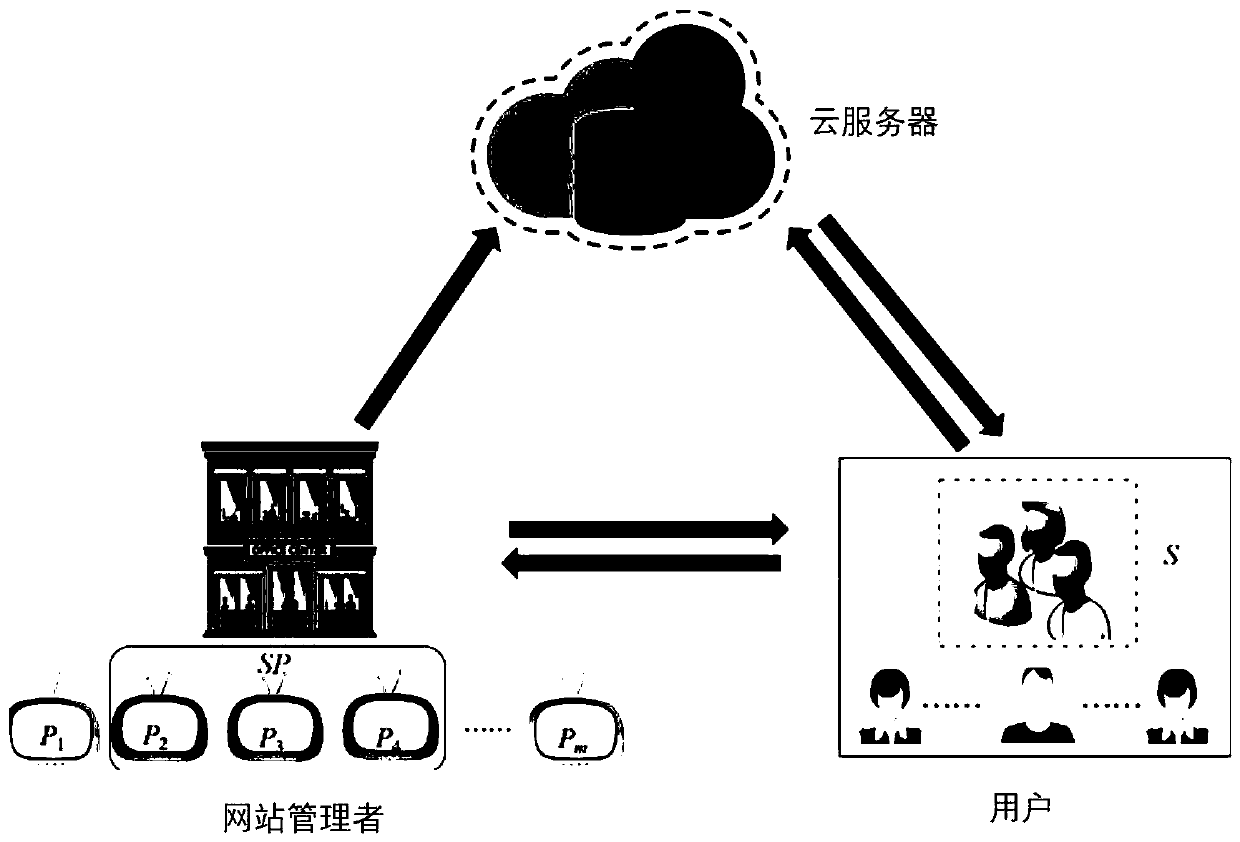
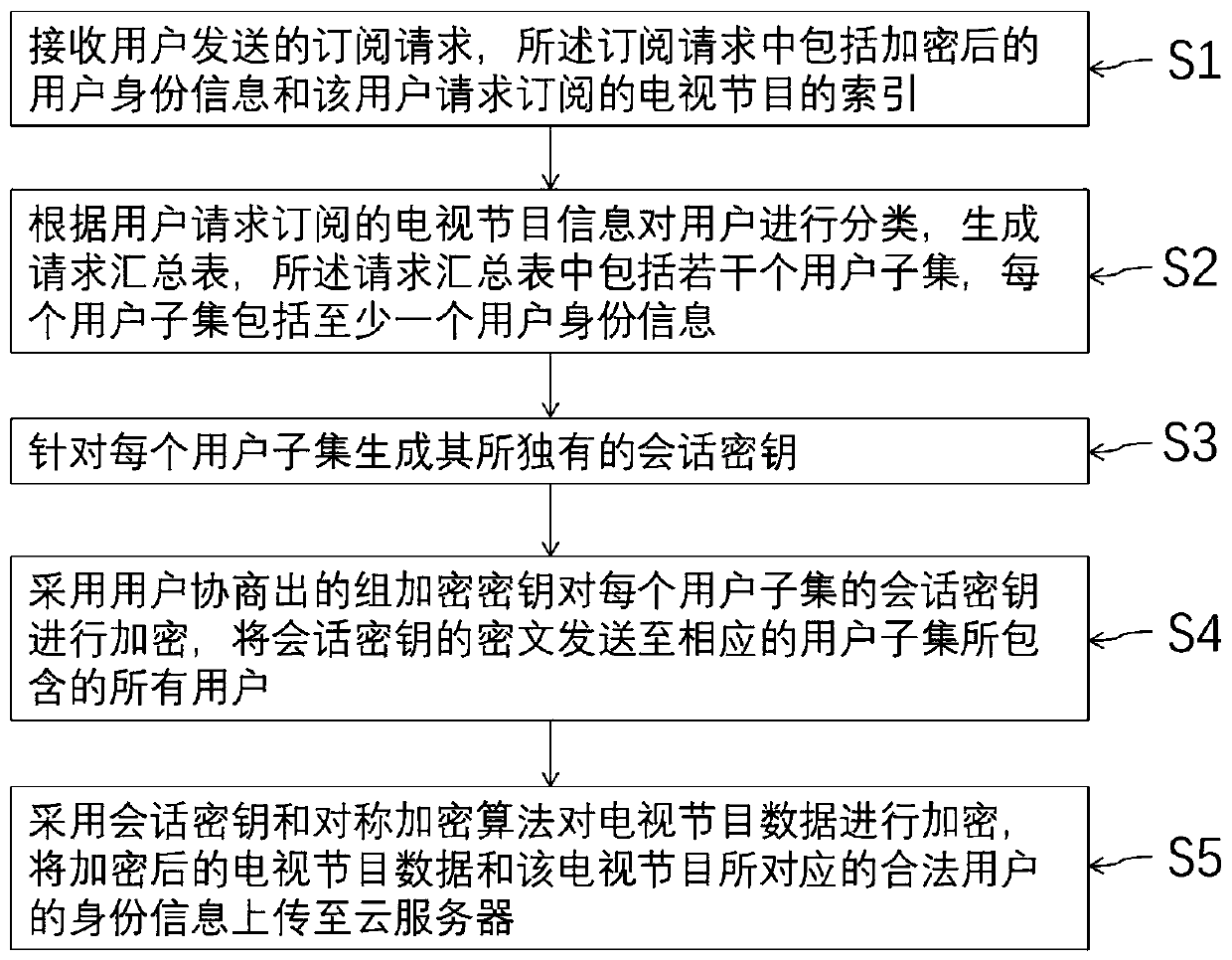
ActiveCN110012312AWon't stealSupport dynamic operationSelective content distributionPlaintextTelevision system
The invention discloses a key management-based access control method suitable for a pay television system, which comprises the following steps of: forming a group by all users of the same video website, dividing the users into different user subsets according to the preferences of the users, wherein television programs subscribed by the users in the same user subset are the same. And the website manager encrypts the television program and the session key, and sends the ciphertext of the program and the ciphertext of the session key to the cloud server and the corresponding user respectively. And the cloud server updates the data storage table according to the data uploaded by the website manager and judges whether the request of the user is legal or not according to the data storage table.Only legal users can obtain the session key and the ciphertext of the television program at the same time, and the plaintext of the television program is further obtained through decryption. According to the invention, the privacy data of the user can be ensured not to be stolen, and the dynamic operation of the user and the service provider on the television program is supported; and computing and communication overheads of the user and the service provider are saved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
An anti-virus system for internet information security based on big data analysis
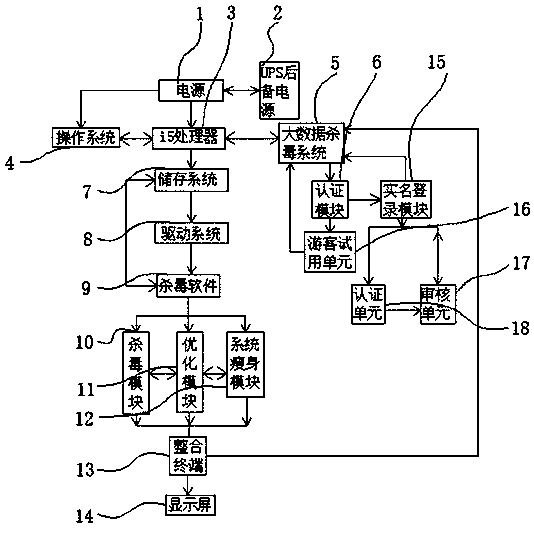
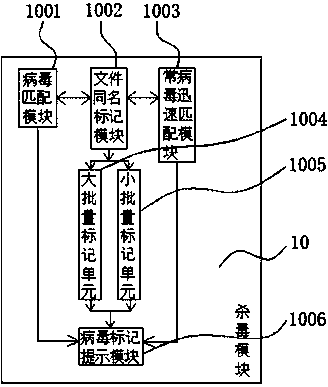
PendingCN109543412AImprove storage effectEasy to operatePlatform integrity maintainanceAnti virusOperational system
The invention relates to an anti-virus system for Internet information security based on big data analysis, including a power supply and a certification module; the power supply is electrically connected with a UPS backup power supply through a conductor, and the power supply is electrically connected to an i5 processor input through a wire, The i5 processor is electrically connected with the operating system through a wire, the i5 processor is electrically connected with the big data antivirus system through a wire, the authentication module is electrically connected with the big data antivirus system output through a wire, and the i5 processor is electrically connected with the storage system input through a wire. The invention uses the antivirus module, the optimization module and the setting of the system slimming module, the antivirus module, the optimization module and the system slimming module as the three functions of the antivirus software through the electric parallel connection of wires, the antivirus module, the optimization module and the system slimming module, and can carry out multi-scheme response according to different situations of users.
Owner:何小钟
Water grate
InactiveCN102080412AImprove carrying capacityUnique structureSewerage structuresClimate change adaptationWater flowStringer
The invention relates to a water grate, which comprises a grate body, wherein the grate body consists of 4 to 20 square grids formed by crossly encircling 3 to 5 longitudinal beams and 3 to 6 cross beams; a group of patterns is engraved in each square grid; and the longitudinal beams, the cross beams and the patterns are molded integrally. The water grate is suitable for sealing entrances of underground box culverts, pipelines and blind ditches into which sewage and rainwater flow, allows water to pass through, intercepts impurities, bears loads of pedestrians and vehicles and can be opened. Compared with the conventional water grate, the water grate has a unique structural form and has high bearing capability; and the water grate has an exquisite structure and a larger water flow cross section compared with the conventional water grate which has an ordinary structure and is made of a cement-based material or a resin-based material. Moreover, the grate body is made of a cement-based composite material, so that the grate body does not have any recycling value and is theft-proof.
Owner:吕云南
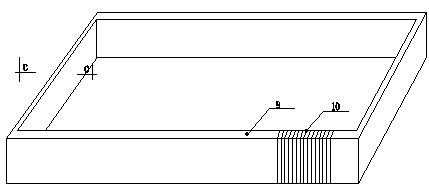
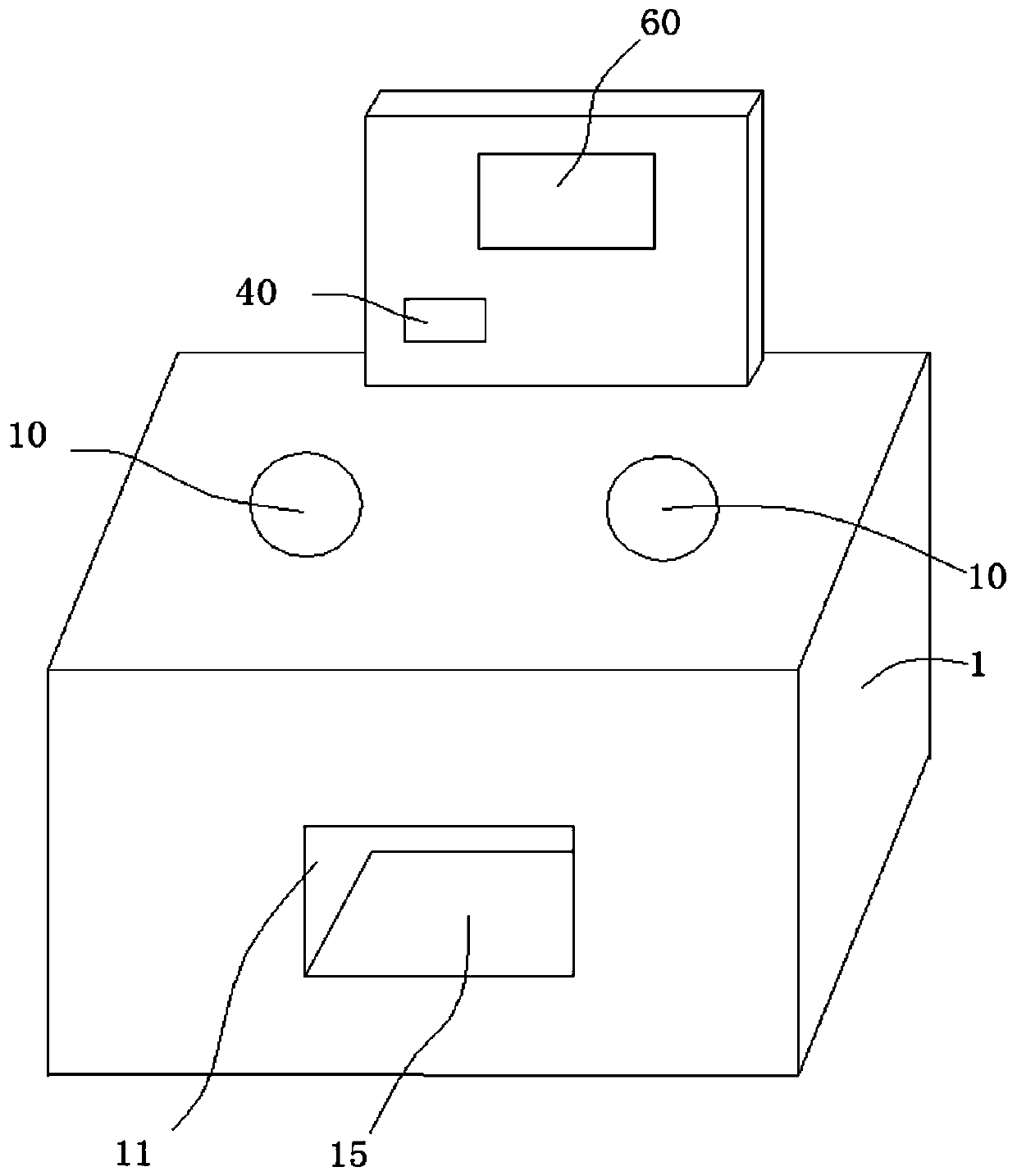
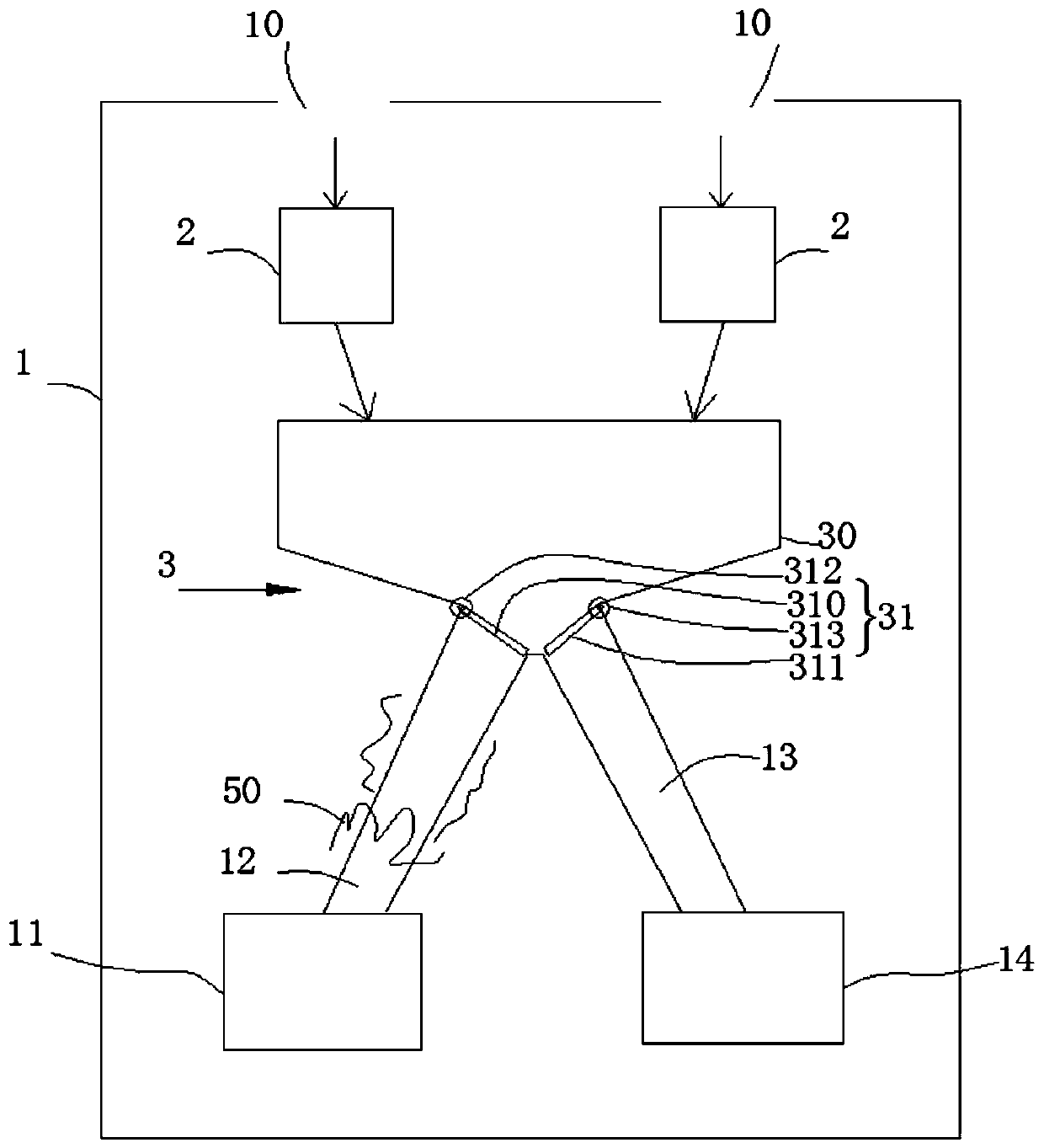
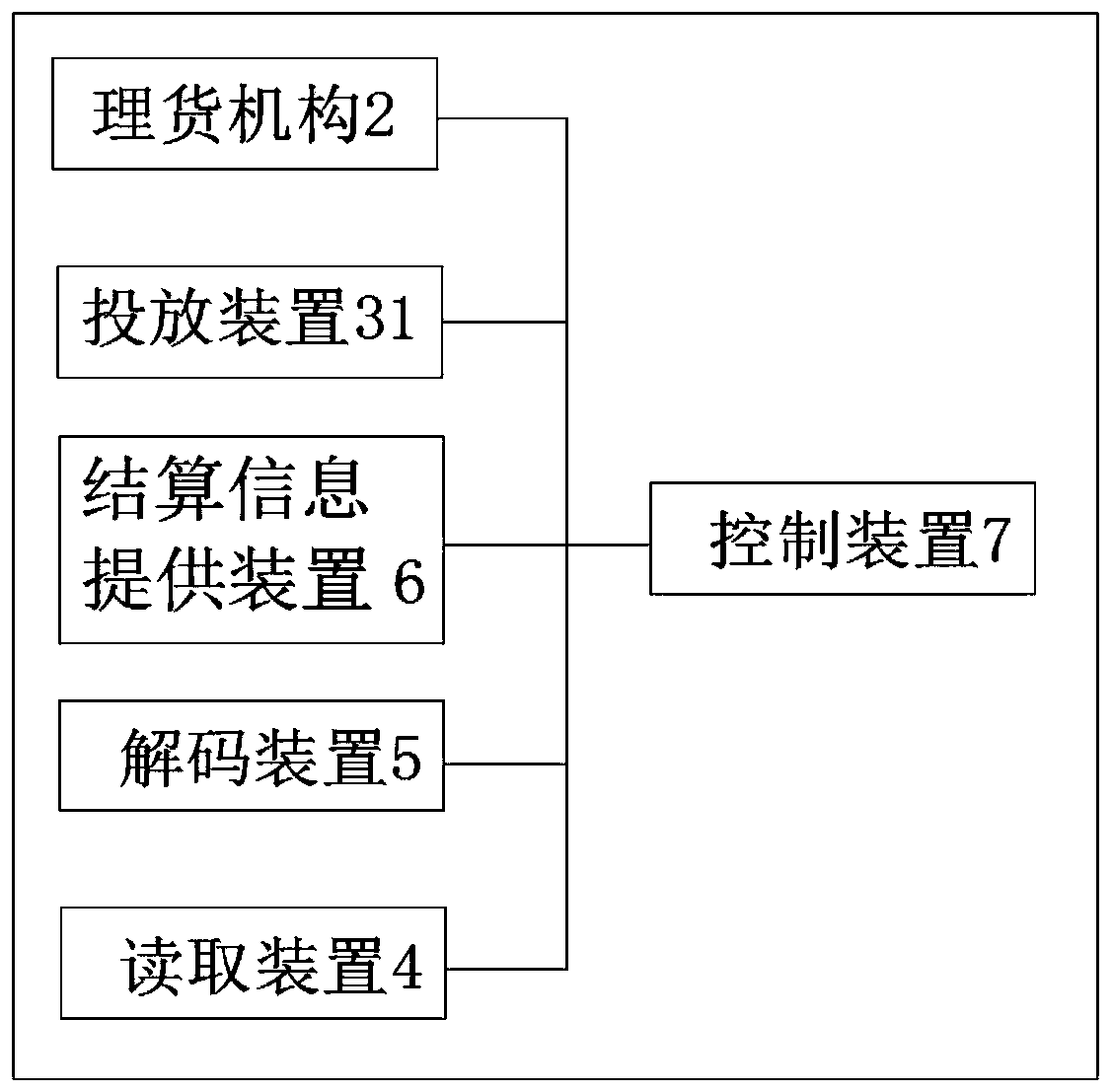
Self-service cash register device and method for goods with anti-theft tags
The invention discloses a self-service cash register device and method for goods with anti-theft tags, and the self-service cash register device is characterized by comprising a housing, a tally mechanism, a temporary storage container, a decoding device, a control device and the like, wherein the tally mechanism can count the number of products input from the product input port of the casing eachtime, and temporarily stores the input products in the temporary storage container if the customer does not pay; after the payment of the input products is completed by the customer, the control device confirms the payment operation of the customer and allows the decoding device to decode the products in the casing after the confirmation is successful; and finally, the customer can take out the paid and decoded products through the product take-out port. In this way, the situation where the number of decoded products taken by the customer is greater than the number of paid products is avoided, and the products in the unmanned sales place will not be stolen by customers, thereby making the anti-theft technology of the products in the unmanned sales place more complete.
Owner:NINGBO XUNQIANG ELECTRONICS TECH
Adjustable vehicle spare tire frame
ActiveCN103950476AQuick disassembly and installationWon't stealSpare wheel arrangementsEngineeringSpare tire
The invention provides an adjustable vehicle spare tire frame which comprises a main body, two fixing bases, two vertical boards, a main shaft, a pressing board, a locking nut, two tire pressing boards, two first supports, two second supports, two first adjusting nuts, two second adjusting nuts and two adjusting screw rods, wherein the main body is disc-shaped, the fixing bases and the vertical boards are respectively and fixedly installed at the left side and the right side of the main body, the main shaft is installed in the center of the main body, the pressing board and the locking nut are concentrically fixed, the first supports and the second supports are respectively and fixedly installed at the upper part and the lower part of the main body, through holes are formed in the middle positions of the first supports and the second supports, the adjusting screw rods are respectively arranged on the through holes in the first supports and the second supports, and the tire pressing boards are respectively and fixedly installed on the adjusting screw rods. The adjustable vehicle spare tire frame can play the role of dismantling a spare tire fast and conveniently, and effectively guarding against theft and loss.
Owner:山东祥弘环保科技股份有限公司
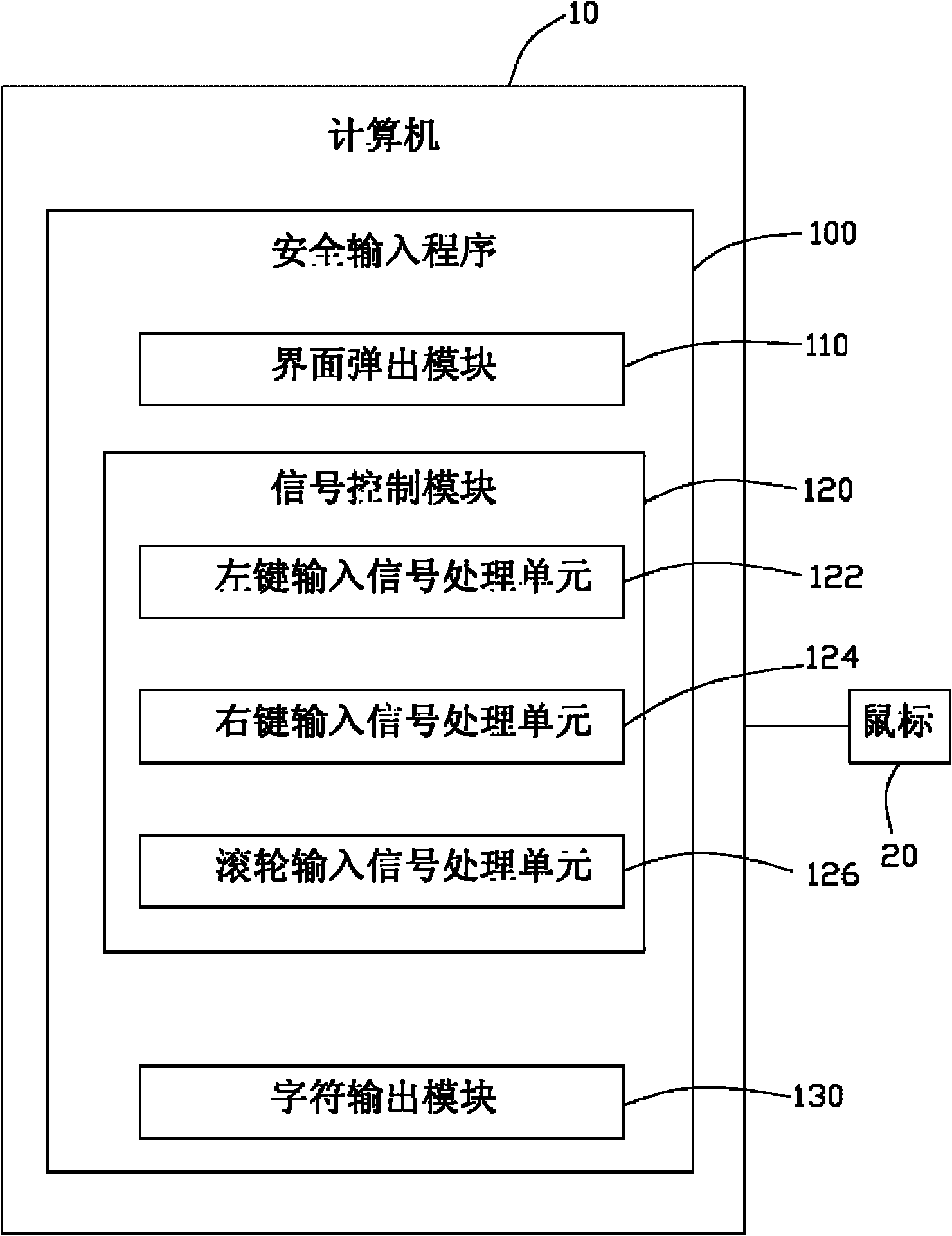
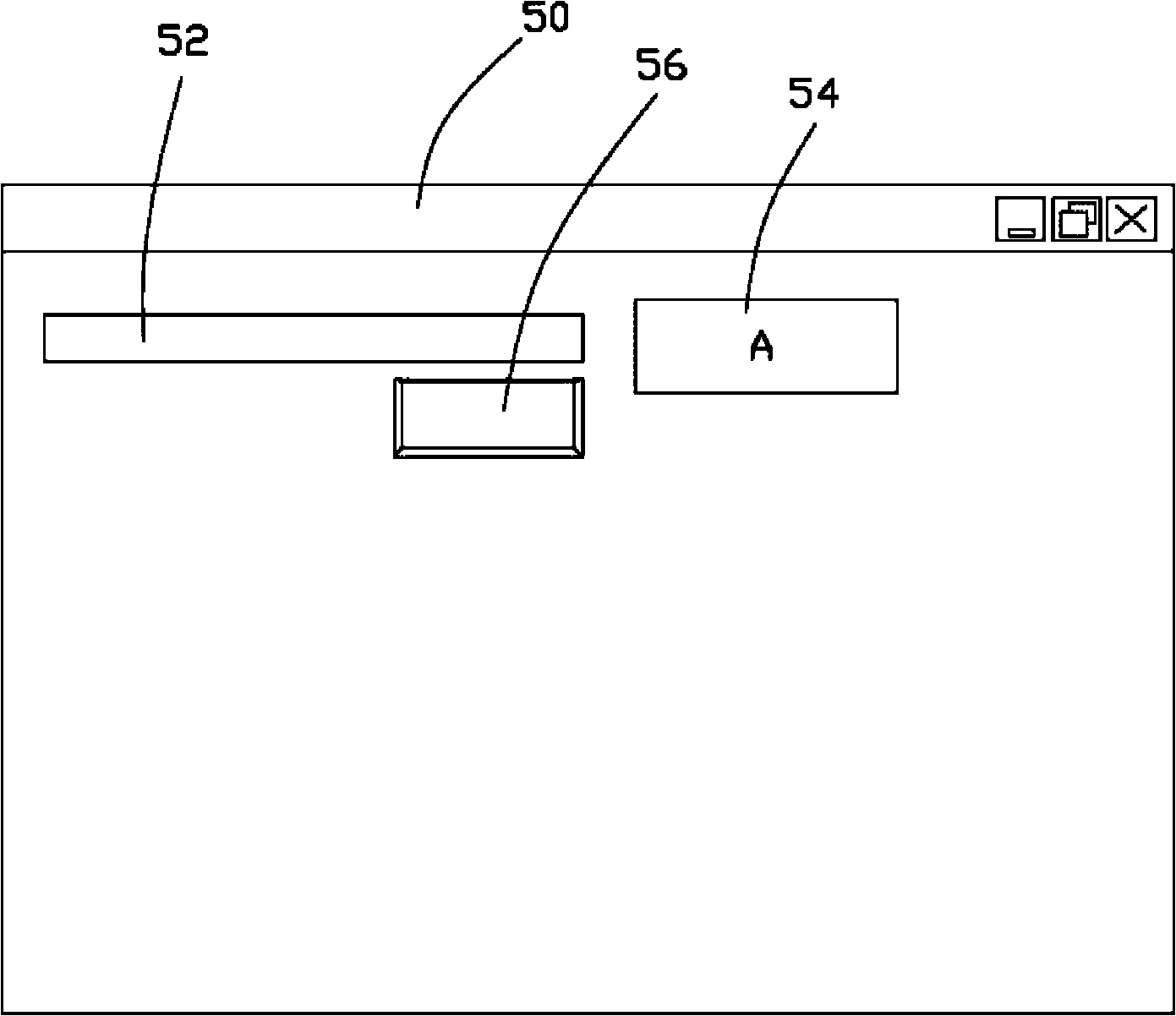
Safe input system and safe input method
InactiveCN101833412AImprove convenienceWon't stealInternal/peripheral component protectionInput/output processes for data processingComputer hardwareSoftware engineering
The invention relates to a safe input system comprising a computer and a mouse, wherein the computer is provided with a safe input program; the mouse is connected with the computer; the safe input program comprises an interface ejection module, a signal control module and a character output module; the interface ejection module is used for ejecting an input interface after the safe input program is started; the signal control module is used for processing signals which are input into a character display frame of the input interface by the mouse and inputting characters wanted to input into a character input field of the input interface; the character output module is used for outputting all the characters displayed in the character input field to an input window of an application program. A user can use the safe input system in any time according to actual requirements, thereby improving user use convenience; and information input by the safe input system can not be easily stolen by a network hacker, thereby increasing information input safety.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
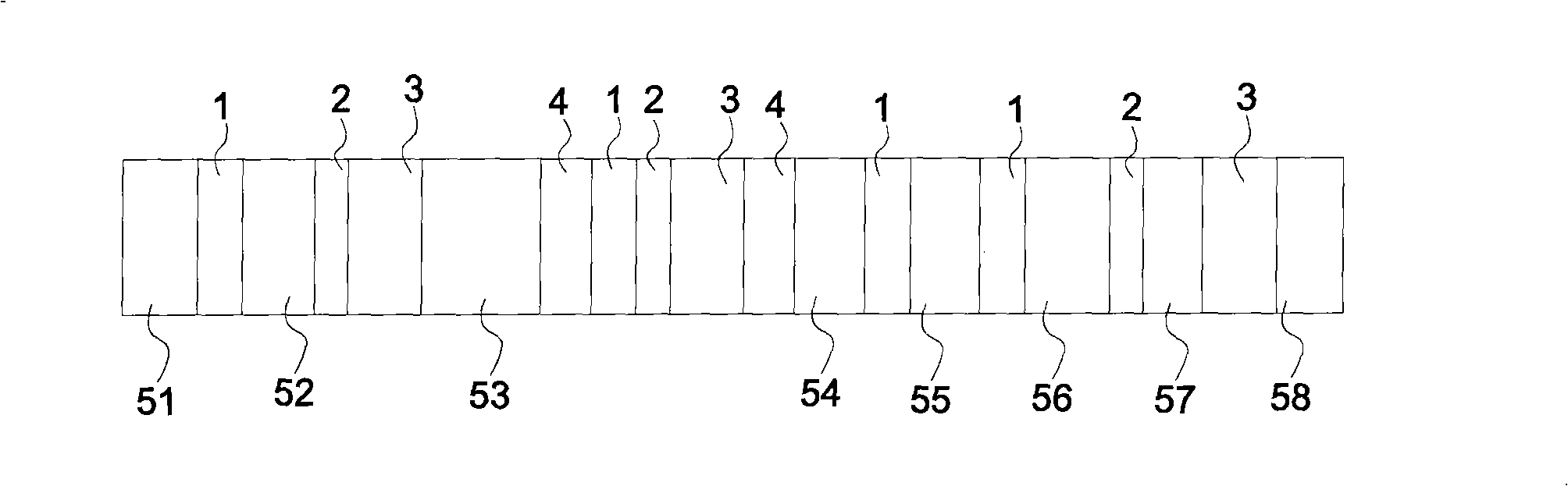
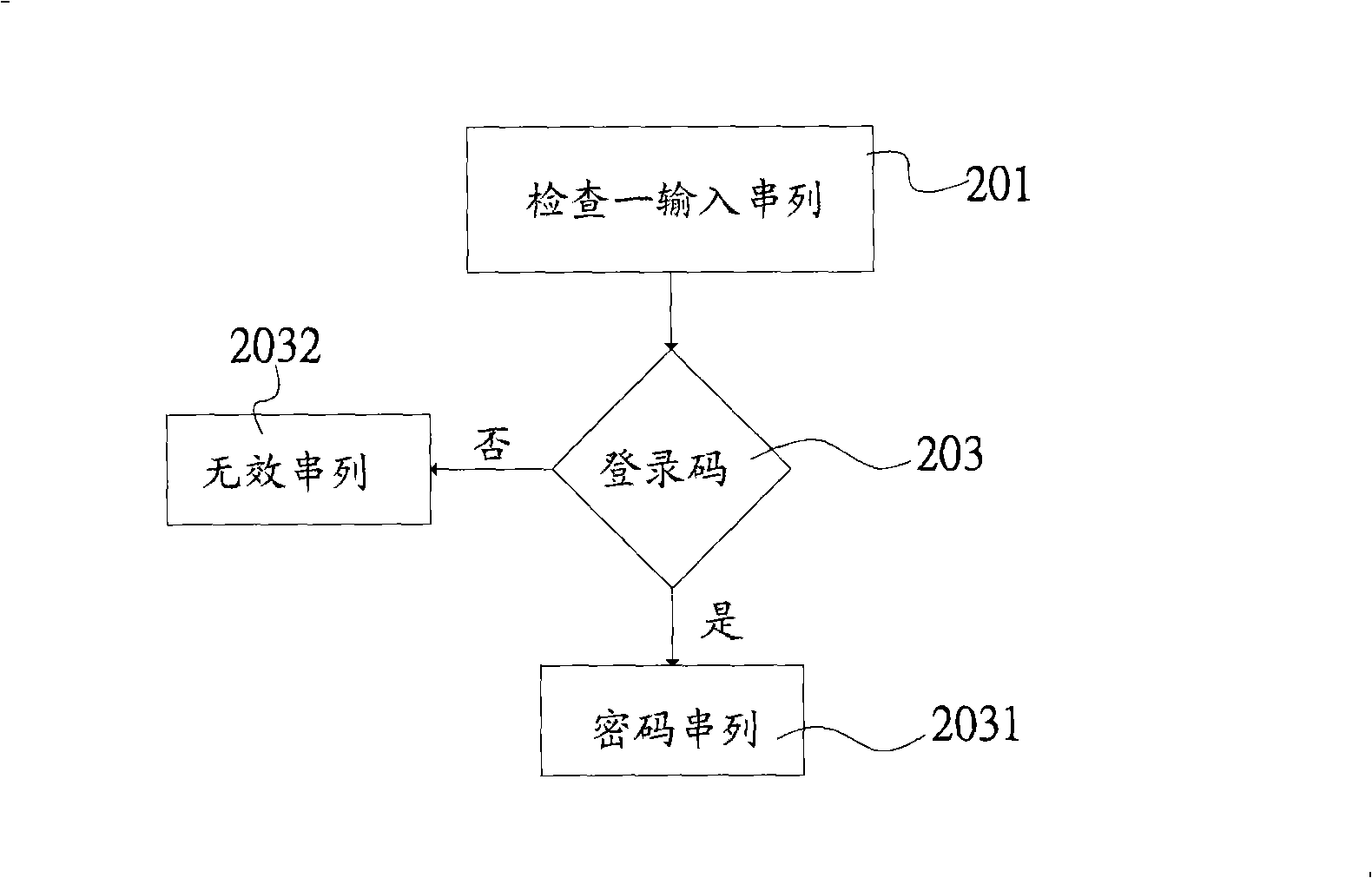
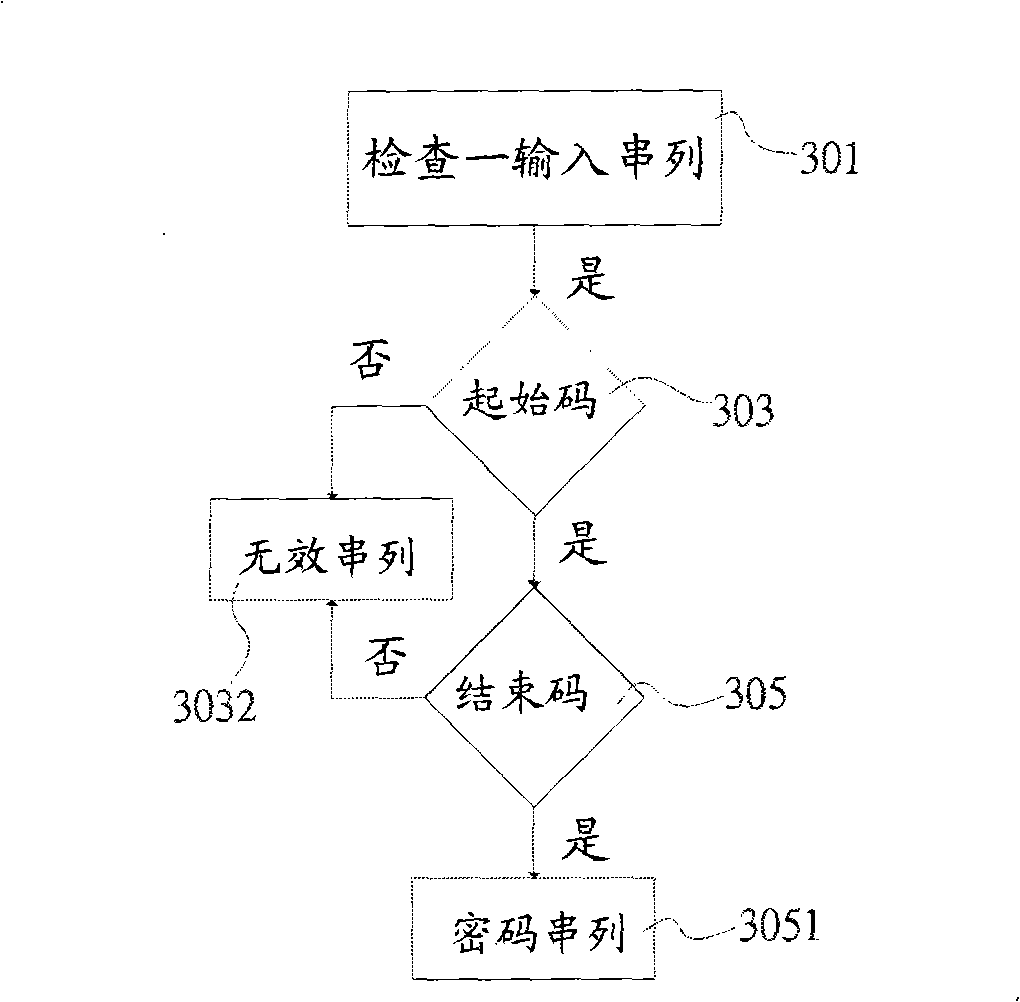
Method for enacting and acknowledging irregularity code
InactiveCN101277188AWon't stealUser identity/authority verificationDigital data authenticationRandom combinationPassword
The invention provides a method for setting anomalous password and a confirmation method. An anomalous character set composed of a string of character, number or symbol, is input into a host computer, generates a password serial list and is displayed on a display; the password serial list includes at least one login code and at least one random combination unit composed of character, number or symbol, the login code is hid in the random combination unit and is not easy being stealing.
Owner:WISTRON CORP +1
Single sign-on tamper-proofing method and device, computer equipment and storage medium
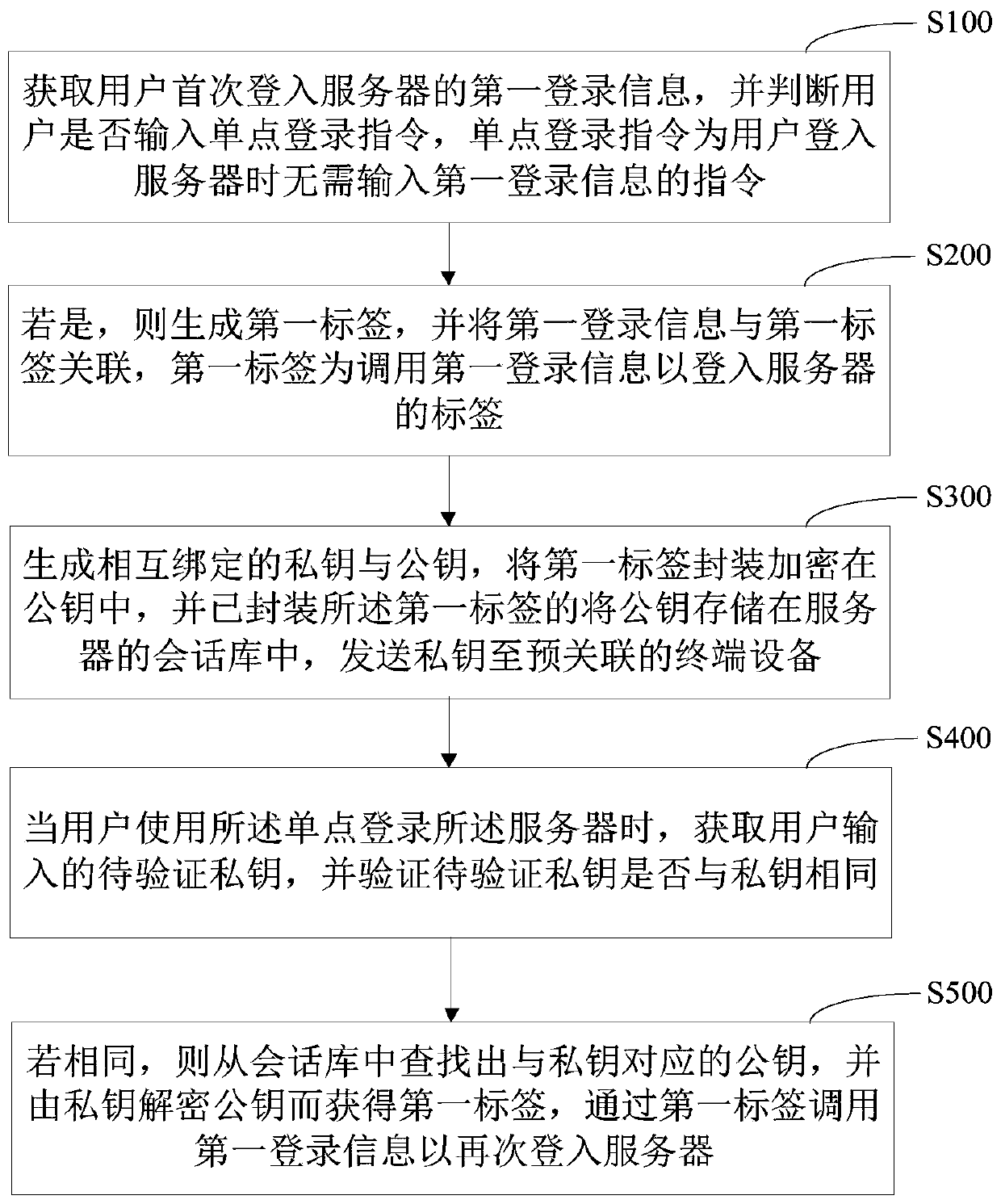
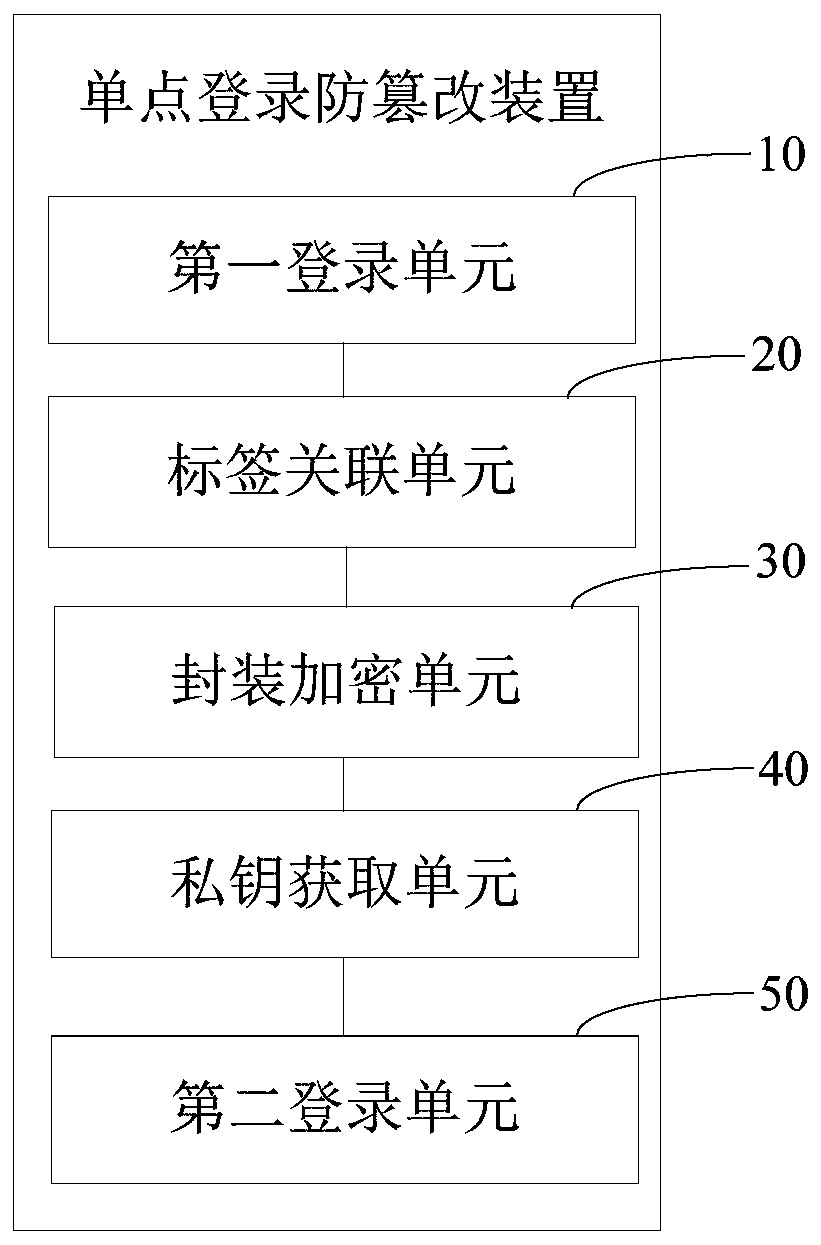
ActiveCN110266640AImplement single sign-onImplement encryptionTransmissionTamper resistanceTerminal equipment
The invention provides a single sign-on tamper-proofing method and device, computer equipment and a storage medium. The method comprises the following steps: obtaining first login information of a user logging in a server, associating the first login information with a first tag, generating a private key and a public key which are bound with each other, packaging and encrypting the first tag in the public key, and storing the public key in a session library of the server, thereby realizing the encryption of the tag, and preventing an illegal person from inputting the tag into the session library and directly entering the server; sending the private key to a pre-associated terminal device; obtaining a to-be-verified private key input by the user through the terminal equipment; judging whether the to-be-verified private key is the same as a private key or not, if yes, searching whether a public key corresponding to the private key exists in a session library, if yes, decrypting the public key by the private key to obtain a first label, and obtaining first login information corresponding to the first label to log in a server again through the first login information, thereby realizing single sign-on of a user.
Owner:PING AN TECH (SHENZHEN) CO LTD
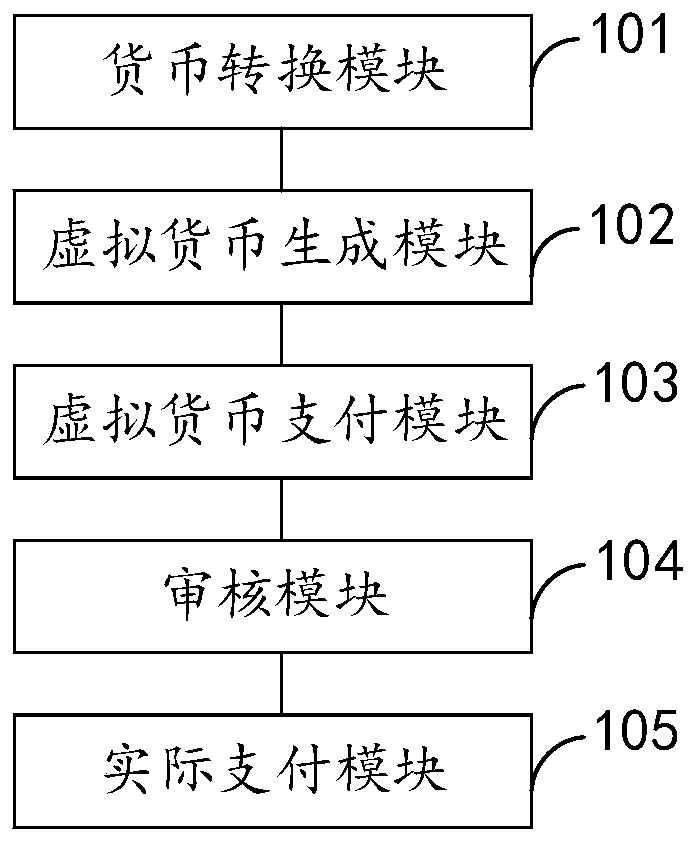
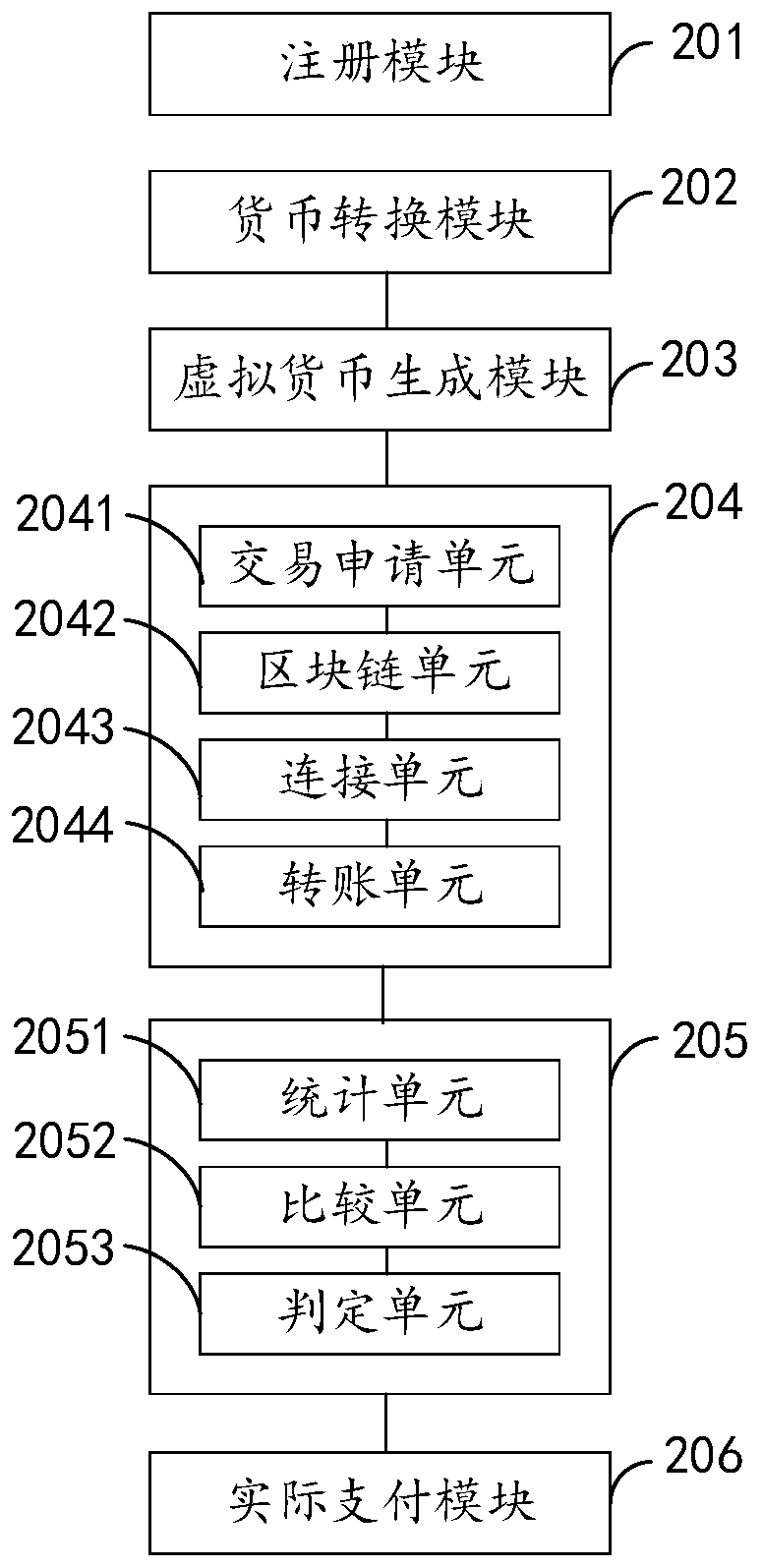
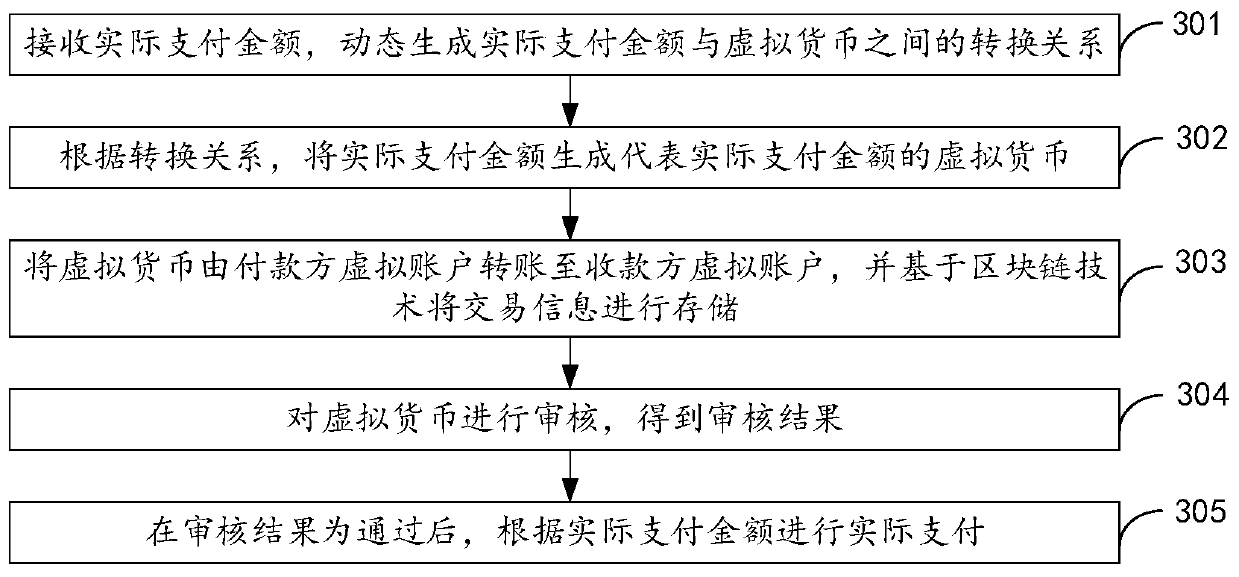
Electronic payment system and method, intelligent terminal and storage medium
InactiveCN109754235AImprove safety performanceWon't leakPayment protocolsPayment circuitsBlockchainOperating system
The invention relates to an electronic payment system and method, an intelligent terminal and a storage medium, and is applied to the technical field of electronic payment, and the electronic paymentsystem comprises a currency conversion module which is used for dynamically generating a conversion relation between an actual payment amount and virtual currency; a virtual currency generation moduleused for generating virtual currency representing the actual payment amount from the actual payment amount according to the conversion relation; a virtual currency payment module used for transferring the virtual currency from a payer virtual account to a payee virtual account and storing transaction information based on a block chain technology; an auditing module used for auditing the virtual currency to obtain an auditing result; and an actual payment module used for carrying out actual payment according to the actual payment amount after the audit result is passed.
Owner:篱笆墙科技集团有限公司
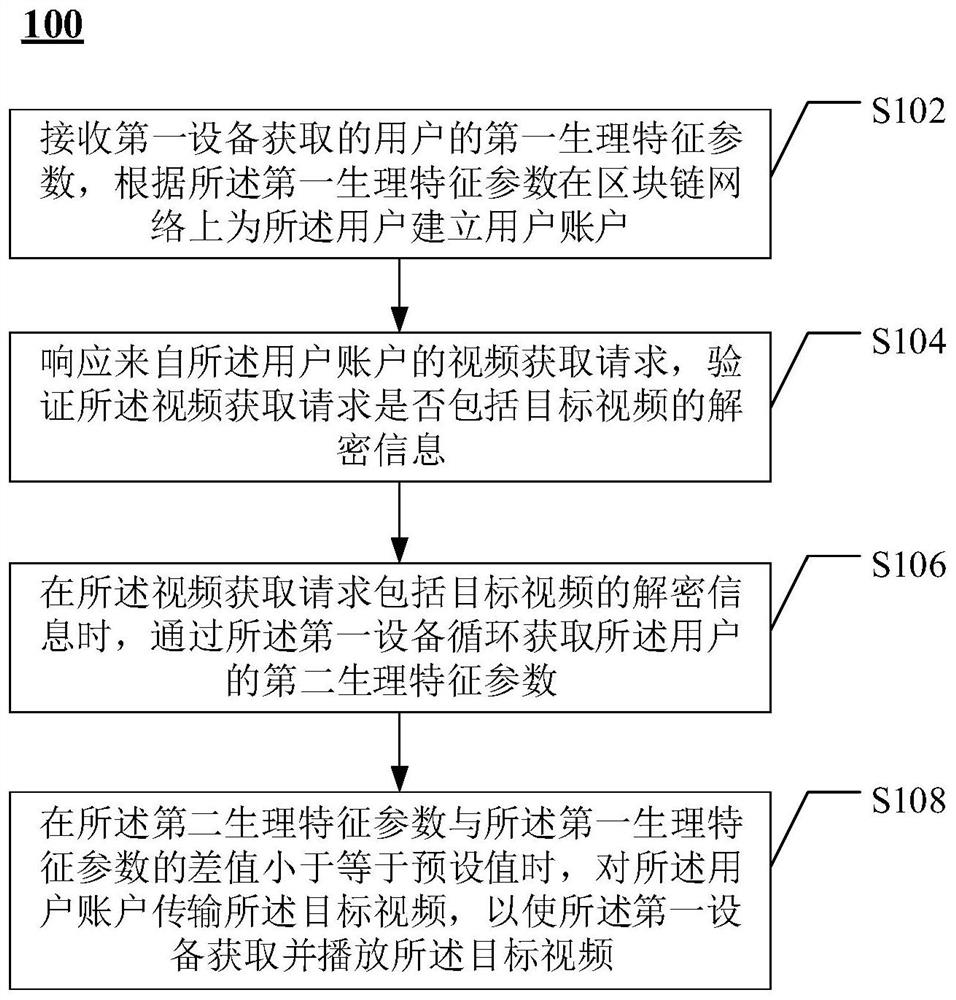
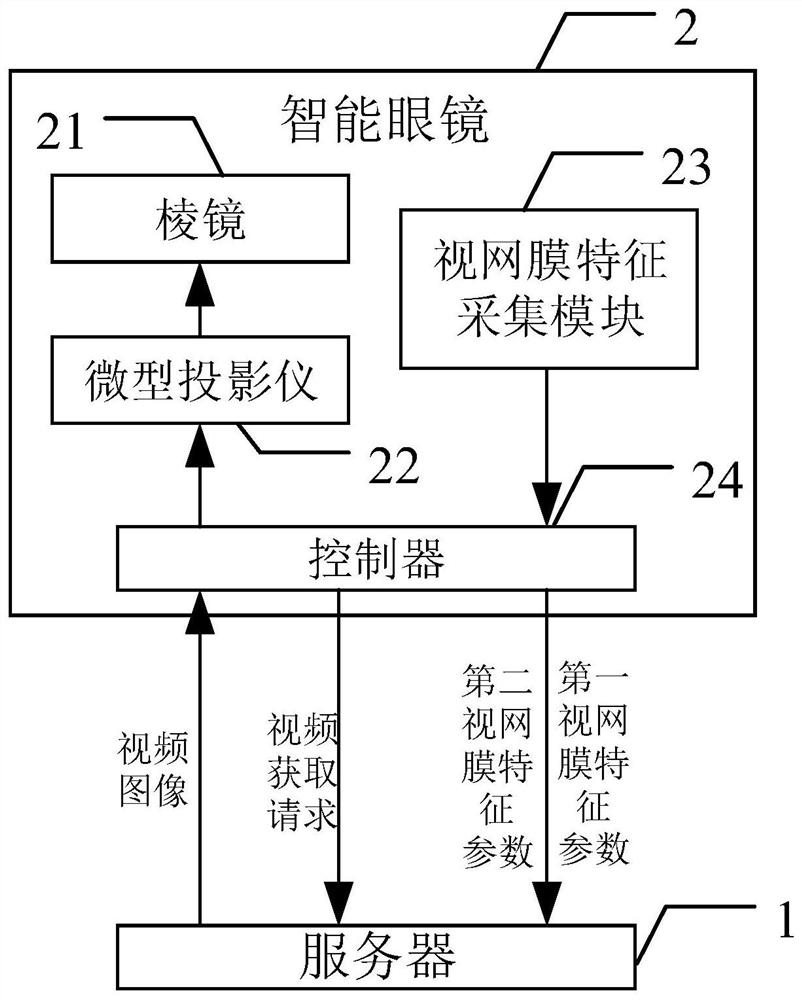
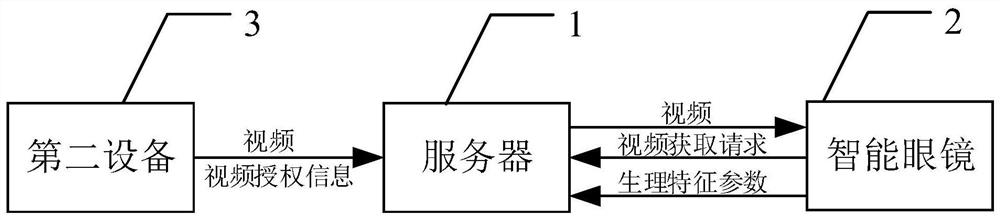
Video transmission control method and device, electronic equipment and intelligent glasses
PendingCN112995717AImprove securityWon't stealUser identity/authority verificationSelective content distributionComputer hardwareSmartglasses
The invention provides a video transmission control method and intelligent glasses. The video transmission control method comprises the following steps: receiving a first physiological feature parameter of a user acquired by first equipment, and establishing a user account for the user on a block chain network according to the first physiological feature parameter; in response to a video acquisition request from the user account, verifying whether the video acquisition request comprises decryption information of a target video; when the video acquisition request comprises decryption information of a target video, circularly acquiring a second physiological feature parameter of the user through the first equipment; and when a difference value between the second physiological feature parameter and the first physiological feature parameter is smaller than or equal to a preset value, transmitting the target video to the user account, so that the first device acquires and plays the target video. According to the video transmission control method provided by the invention, the security of the video file in the transmission process can be improved.
Owner:BEIJING WODONG TIANJUN INFORMATION TECH CO LTD +1
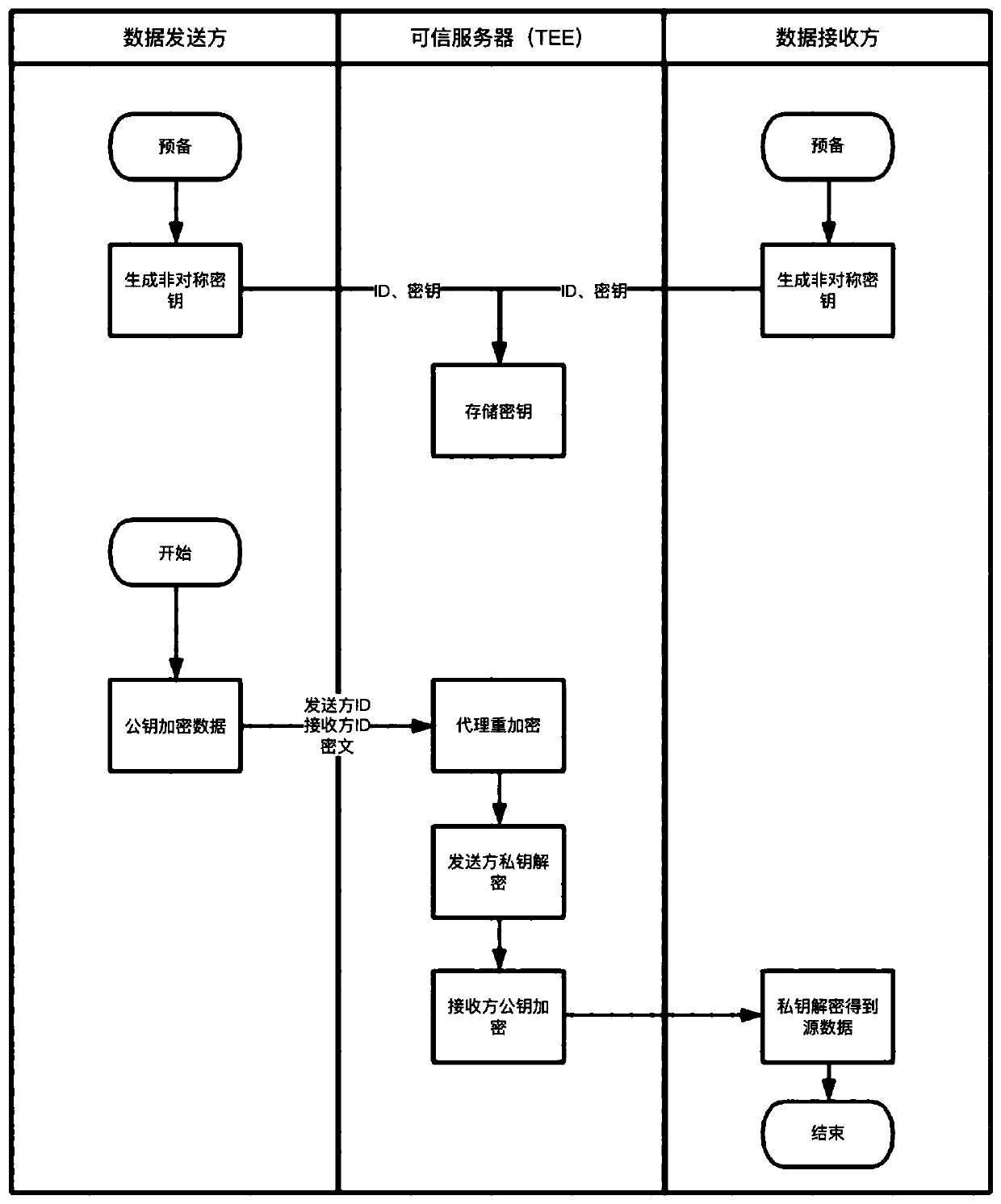
TEE-based security proxy re-encryption method
InactiveCN111262694AReduce consumptionKeep keys safeKey distribution for secure communicationKey (cryptography)Information transmission
The invention discloses a TEE-based security proxy re-encryption method, which belongs to the technical field of computer security and cryptography, and specifically comprises the following steps that: two information transmission parties respectively generate asymmetric key pairs, and upload the respective key pairs to a trusted server loaded with a trusted execution environment; an information sender encrypts information by using a public key of the information sender and then sends the information to the trusted server; the trusted server decrypts the information by using the private key ofthe sender, encrypts the information by using the public key of the receiver, and sends the encrypted information to the receiver; after receiving the decrypted information, the receiver decrypts thedecrypted information by using a private key of the receiver. In the method, a trusted server loaded with TEE serves as a proxy. The method has the characteristics of low resource consumption and lowcost.
Owner:HANGZHOU QULIAN TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com