Password authentication method with high security
A password authentication and high-security technology, applied in the fields of information security and cryptography, can solve problems such as complex algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The specific embodiment of the present invention will be further described in detail in conjunction with the accompanying drawings.
[0064] The goal that the present invention will realize is:
[0065] (1) The user password can be modified or deleted by the user.
[0066] (2) The user name and password are transmitted in cipher text.
[0067] (3) No one can log in as a certain user.
[0068] (4) The plaintext form of the user name and password cannot be obtained by the server-side personnel.
[0069] (5) The authentication system can resist attacks such as replay attack, password guessing attack and masquerading attack.
[0070] (6) The authentication system has high efficiency.
[0071] (7) If the smart card is lost, the attacker holding the smart card cannot log in to the system by guessing the password.
[0072] The present invention comprises following four steps:
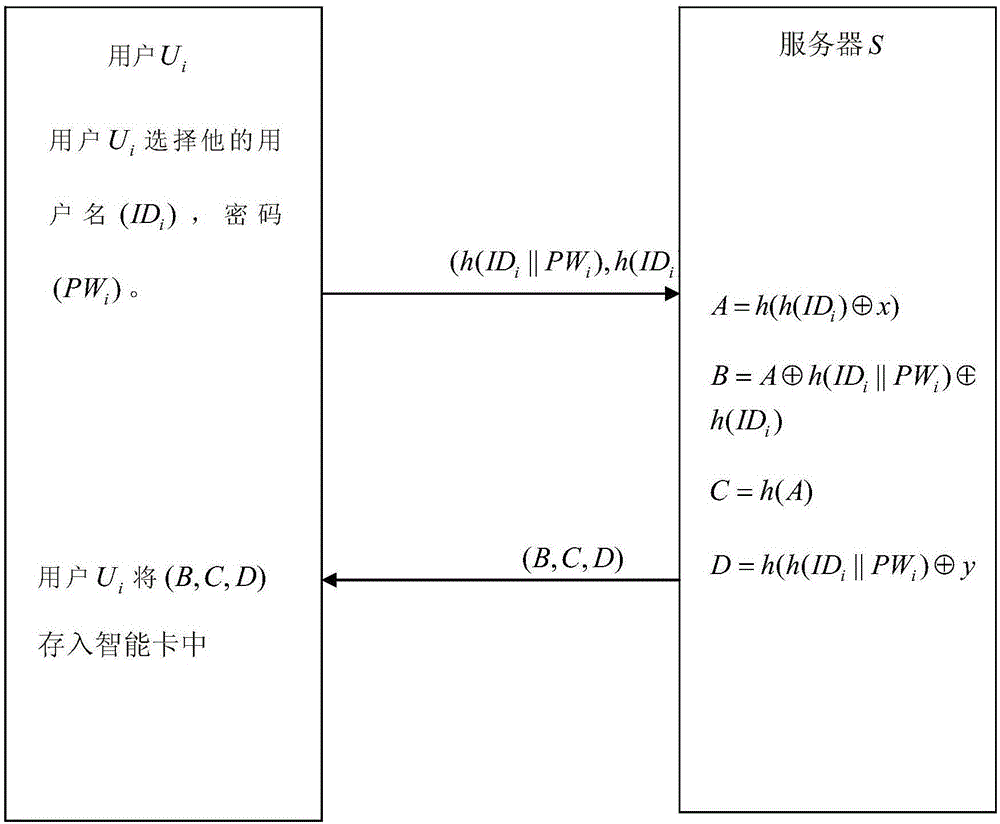
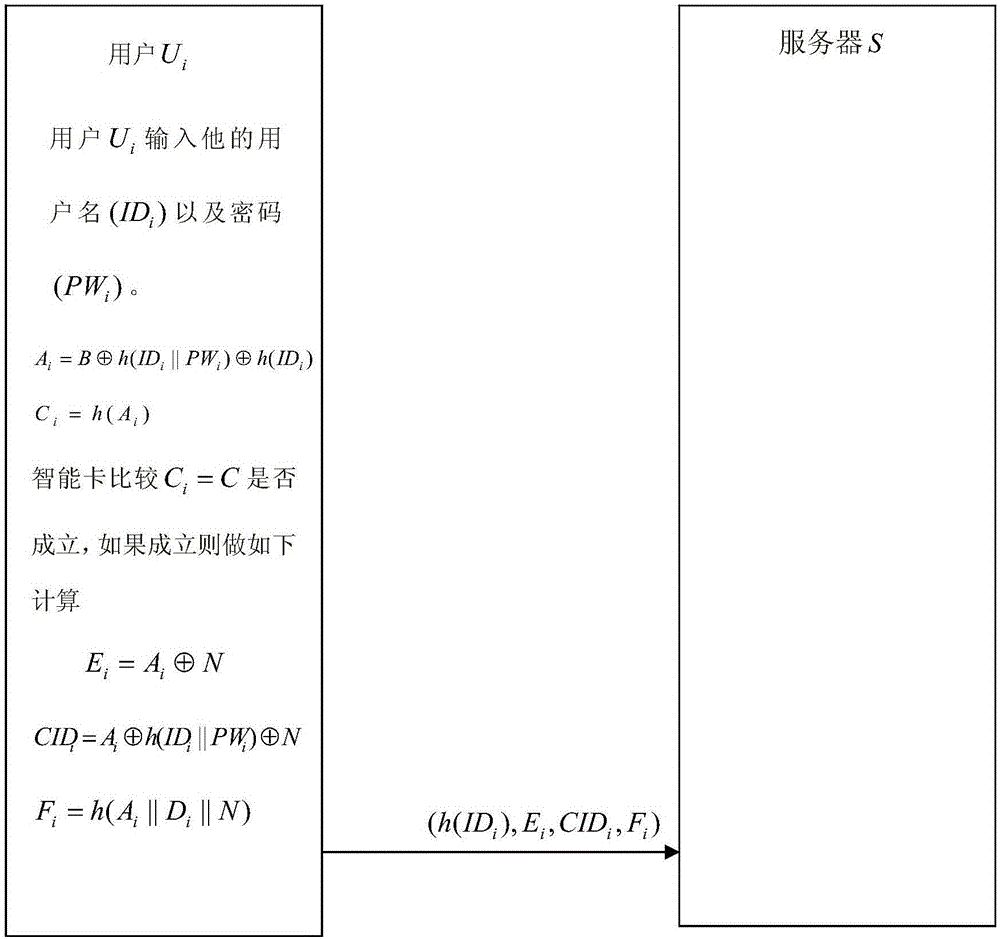
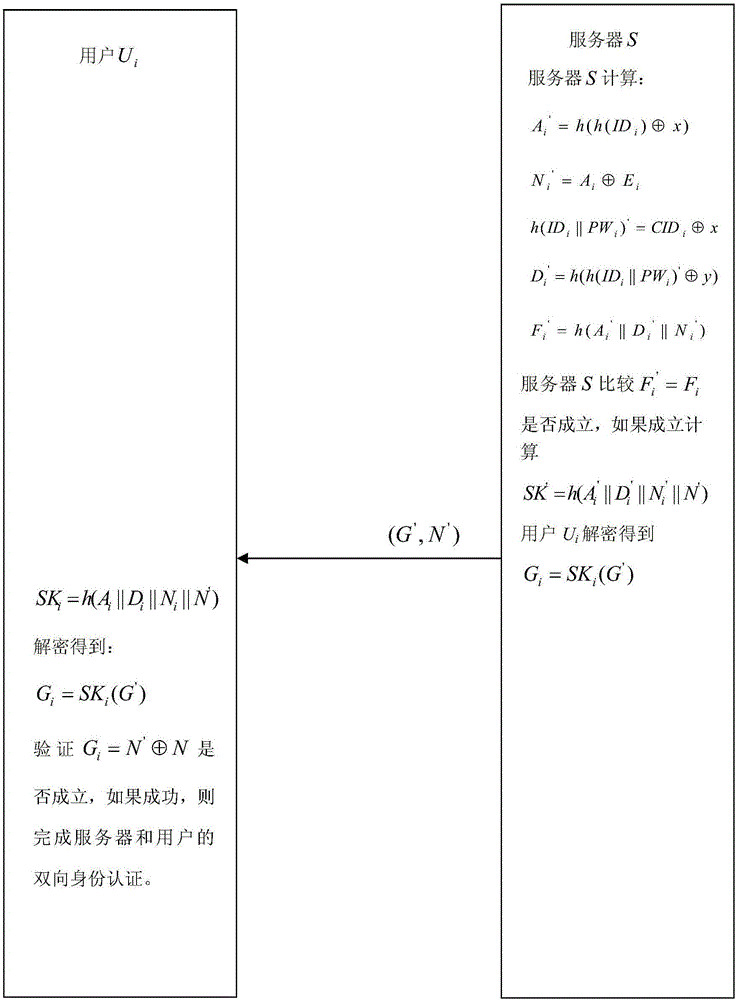
[0073] Step 1, user registration stage. Such as figure 1 As shown, the user chooses a user n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com