Physical layer security methods based on non-optimal user cascading scheme in heterogeneous network
A physical layer security and heterogeneous network technology, which is applied in the field of physical layer security and multi-layer heterogeneous networks, can solve the problems of difficulty in connecting to the best base station for users and high computational complexity, so as to ensure reliable transmission, alleviate channel congestion, Guaranteed efficient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] A physical layer security method based on a non-optimal user cascade scheme in a heterogeneous network, including the following steps:
[0066] S1. The described network model according to the homogeneous Poisson point process of spatial nodes is analyzed using random geometric mathematical tools. For all network nodes (base stations, user equipment, eavesdroppers), their spatial positions obey the intensity λ The homogeneous Poisson point process Φ;
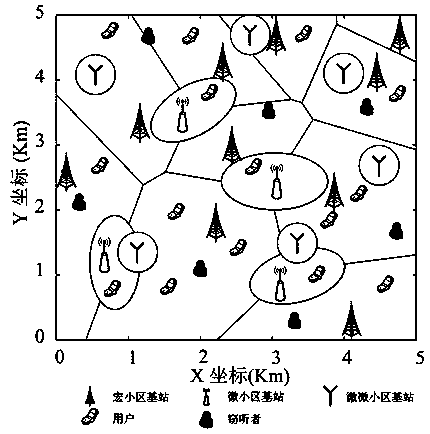
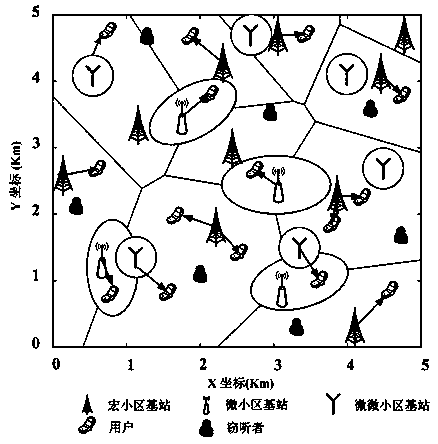
[0067] S2, we consider a K-layer heterogeneous network, such as figure 1 As shown, analyze the heterogeneous network structure composed of macrocell, microcell and picocell when K=3. The spatial position of the k-th layer base station satisfies the intensity λ k Homogeneous Poisson point process Φ k , And k=1, 2,...,K. In addition, the obedience intensity of the cell user location is λ U Homogeneous Poisson point process Φ U . We assume that all cellular communication links are passive and vulnerable to eavesdropping by mal...
Embodiment 2
[0117] Example 2: Based on Example 1 but with a difference;
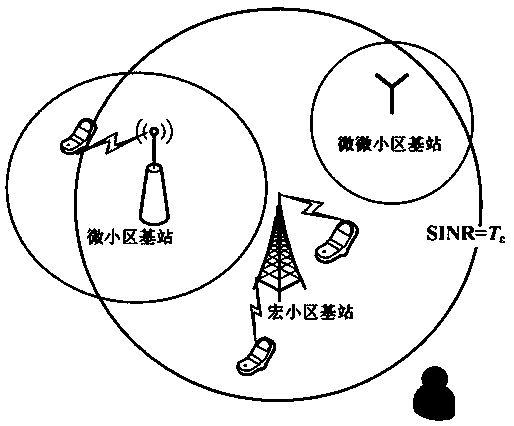
[0118] The security mentioned in the present invention is based on a physical layer security algorithm. Due to the broadcast nature of wireless transmission, it is prone to security problems such as interference and eavesdropping, which will endanger communication privacy in the wireless network. Specific performance as Figure 5 As shown, user A, user B, and eavesdroppers share the same wireless network communication system, where user A and user B are legal users, and the channel between them is called a legal channel. The eavesdropper is a potential threat in the communication system, and the channel it occupies is called the eavesdropping channel. When the signal-to-interference plus noise ratio received by the eavesdropper is less than the security threshold, user A and user B can achieve secure communication. Therefore, the random characteristics of channel noise or the security threshold can be used to safely tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com