Secure communication method and device based on identity authentication
An identity authentication and security technology, applied in the field of communication security, can solve problems such as cumbersomeness, inapplicability, and inconvenient security data communication, and achieve the effects of improving security, increasing convenience, and increasing flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
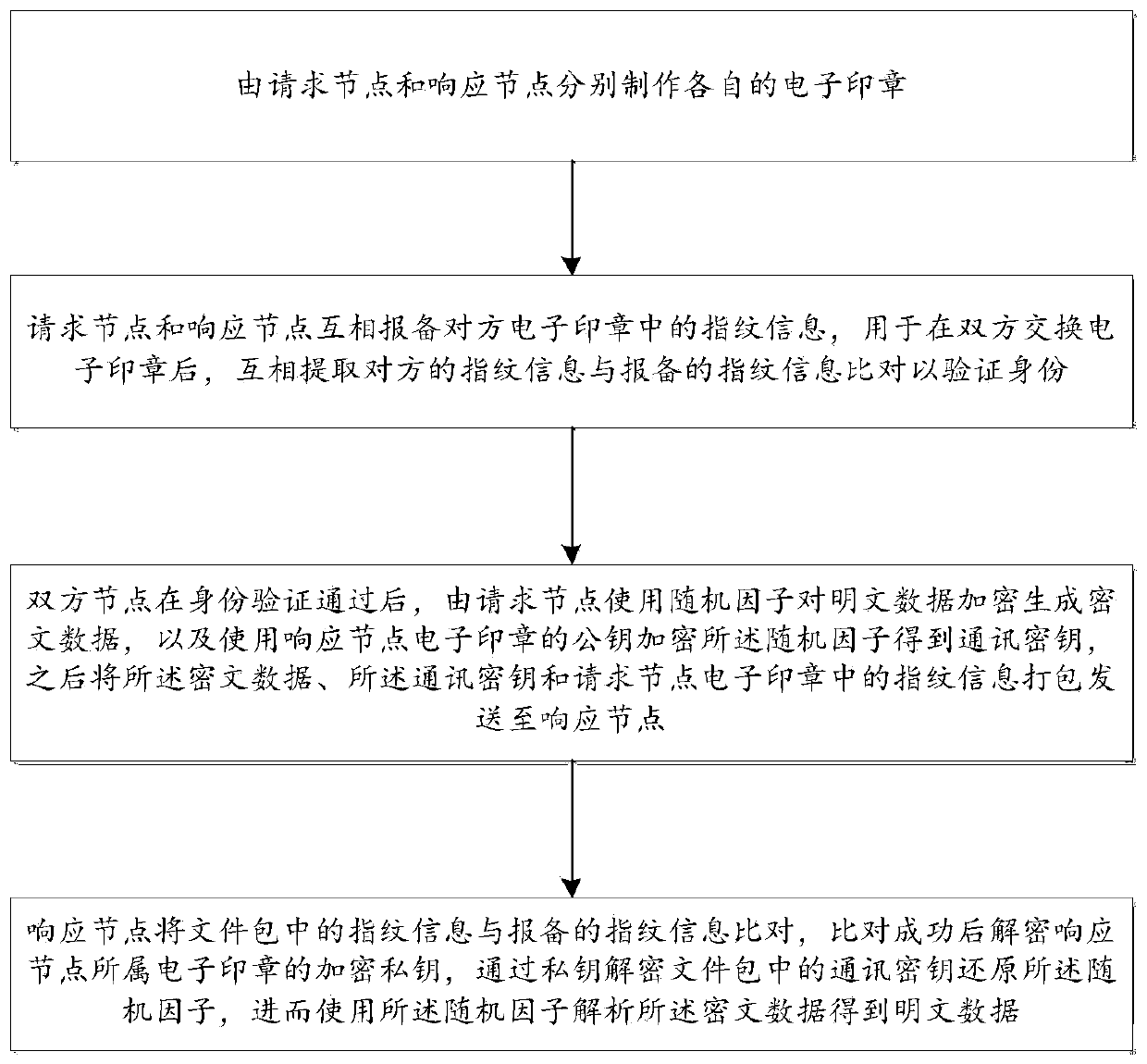
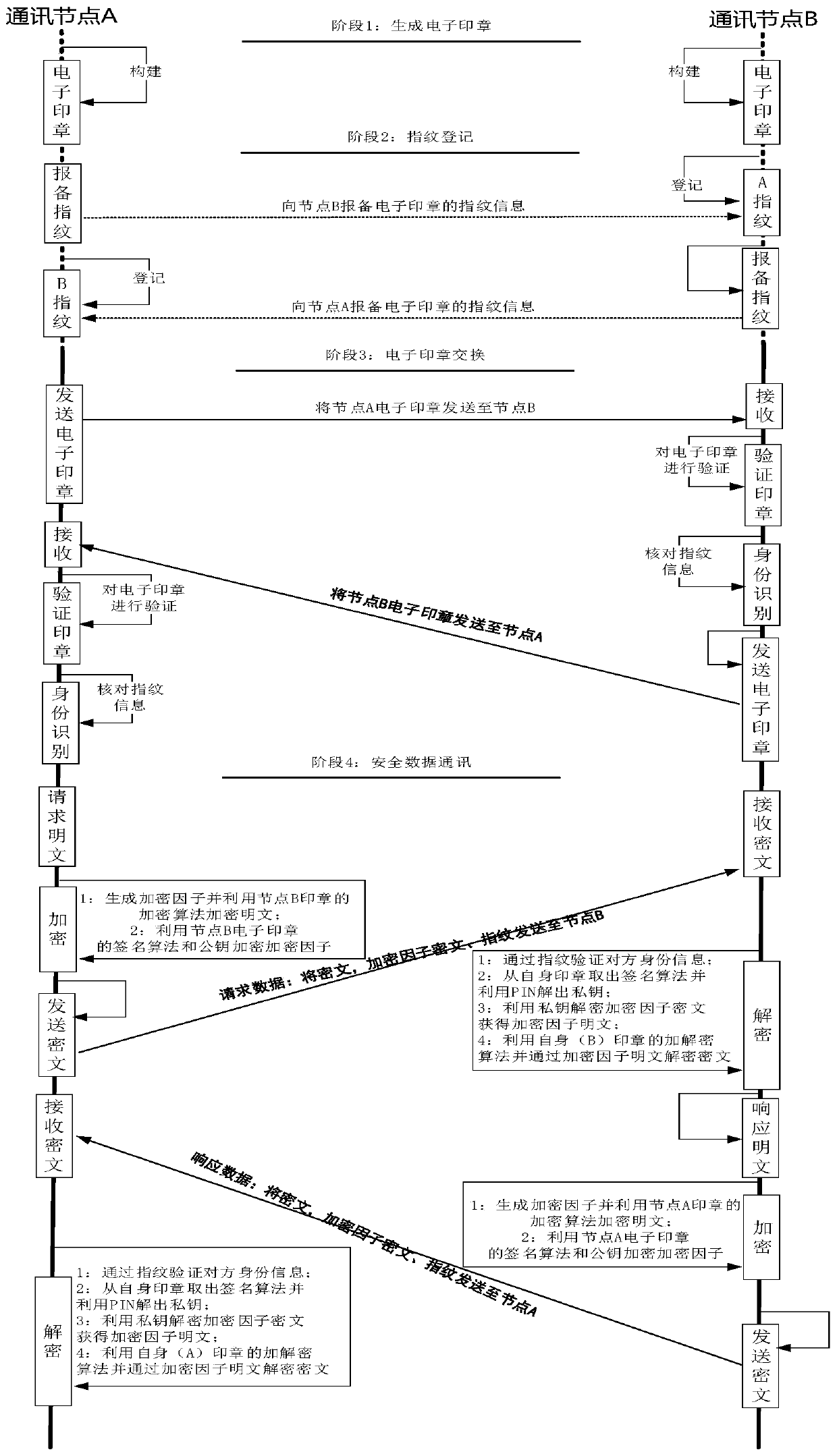
[0057] see Figure 1-Figure 3 , this embodiment provides a secure communication method based on identity authentication, including:
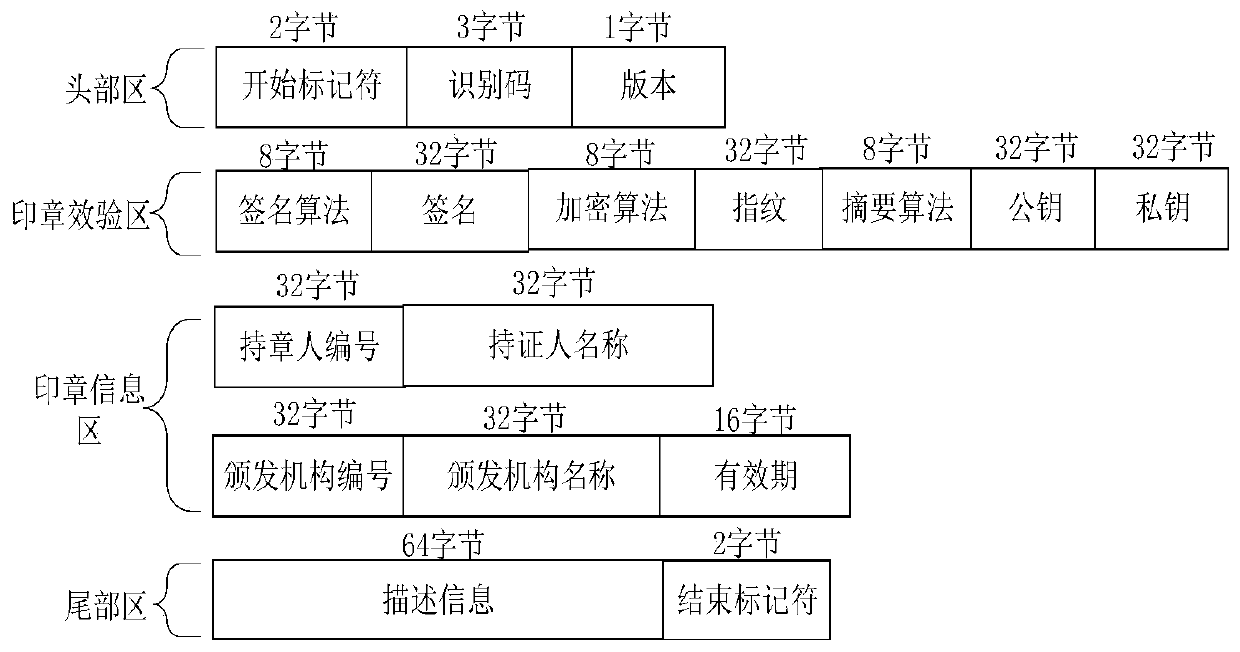
[0058] The requesting node and the responding node make their own electronic seals, and the electronic seal includes a verification area composed of signature algorithm, signature information, encryption algorithm, fingerprint information, digest algorithm, public key and encrypted private key; the requesting node and the responding node Report the fingerprint information in each other's electronic seals to each other, and after the two parties exchange electronic seals, extract each other's fingerprint information and compare them with the reported fingerprint information to verify their identities; after the two nodes pass the identity verification, the requesting node uses it The random factor encrypts the plaintext data to generate ciphertext data, and uses the public key of the responding node's electronic seal to encrypt the random factor ...
Embodiment 2
[0093] This embodiment provides a secure communication device based on identity authentication, including:
[0094] The seal making unit is used to make their own electronic seals by the requesting node and the responding node, and the electronic seal includes a verification algorithm composed of signature algorithm, signature information, encryption algorithm, fingerprint information, digest algorithm, public key and encrypted private key. test area;
[0095] The fingerprint registration unit is used for the requesting node and the responding node to report the fingerprint information in the electronic seal of the other party to each other, and is used to extract the fingerprint information of the other party and compare it with the reported fingerprint information to verify the identity after the two parties exchange the electronic seal;
[0096] A file encryption unit, configured to save the compressed logistics box code message in the storage system, and complete the archi...
Embodiment 3
[0100] This embodiment provides a computer-readable storage medium. A computer program is stored on the computer-readable storage medium. When the computer program is run by a processor, the steps of the above-mentioned secure communication method based on identity authentication are executed.
[0101] Compared with the prior art, the beneficial effect of the computer-readable storage medium provided by this embodiment is the same as the beneficial effect of the identity authentication-based secure communication method provided by the above technical solution, and will not be repeated here.
[0102] Those of ordinary skill in the art can understand that all or part of the steps in the above-mentioned inventive method can be completed by instructing related hardware through a program. The above-mentioned program can be stored in a computer-readable storage medium. When the program is executed, it includes: For each step of the method in the foregoing embodiments, the foregoing s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com