Method for enacting and acknowledging irregularity code
A setting method and irregular technology, applied in digital data authentication, user identity/authority verification, instruments, etc., can solve problems such as usage restrictions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
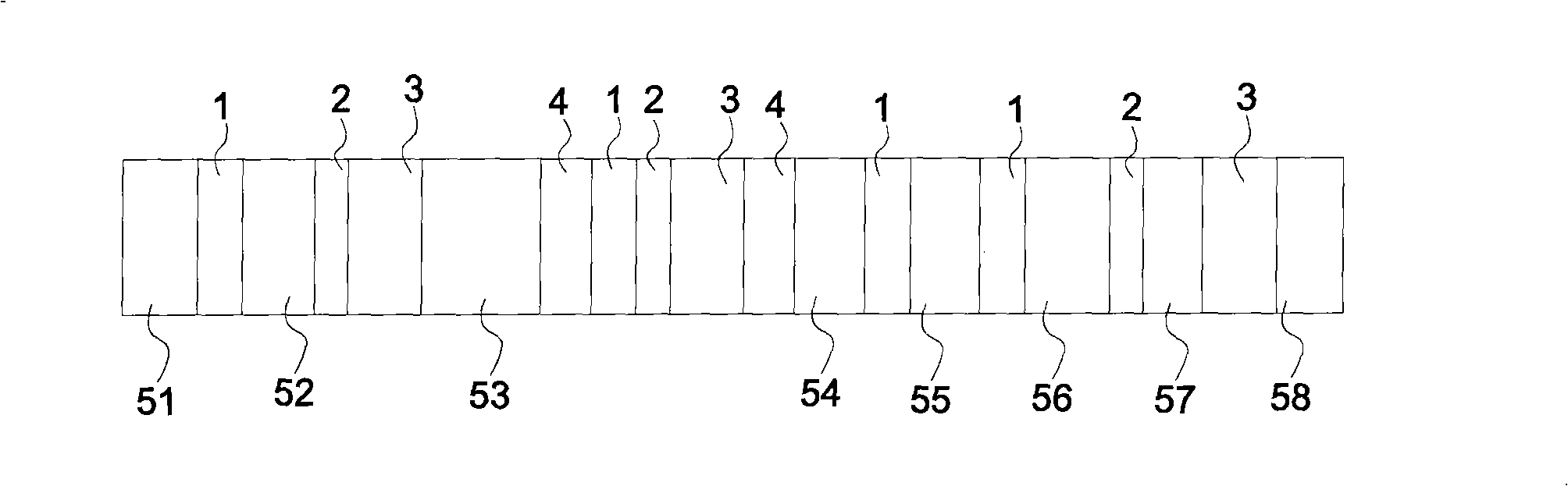
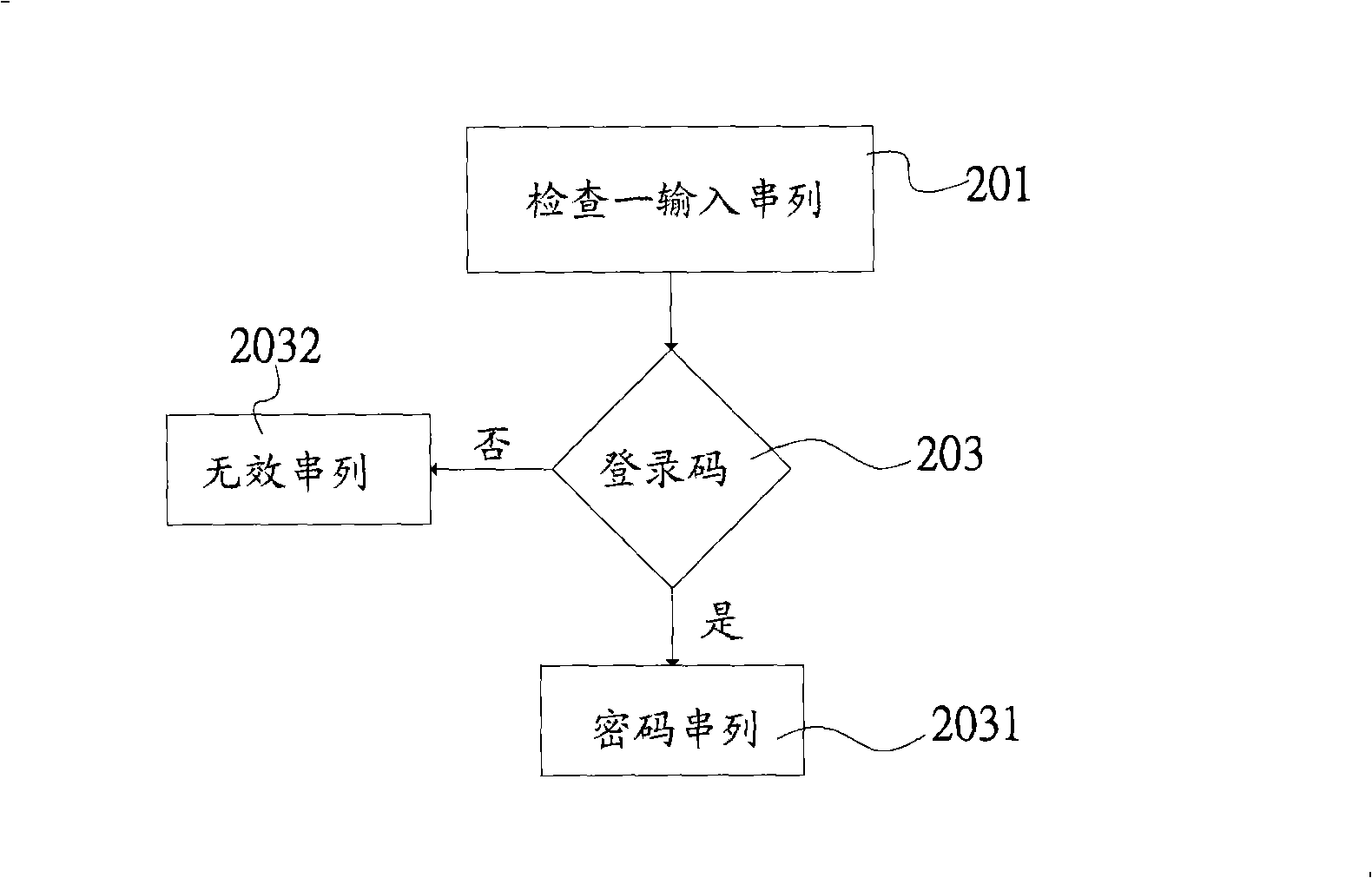
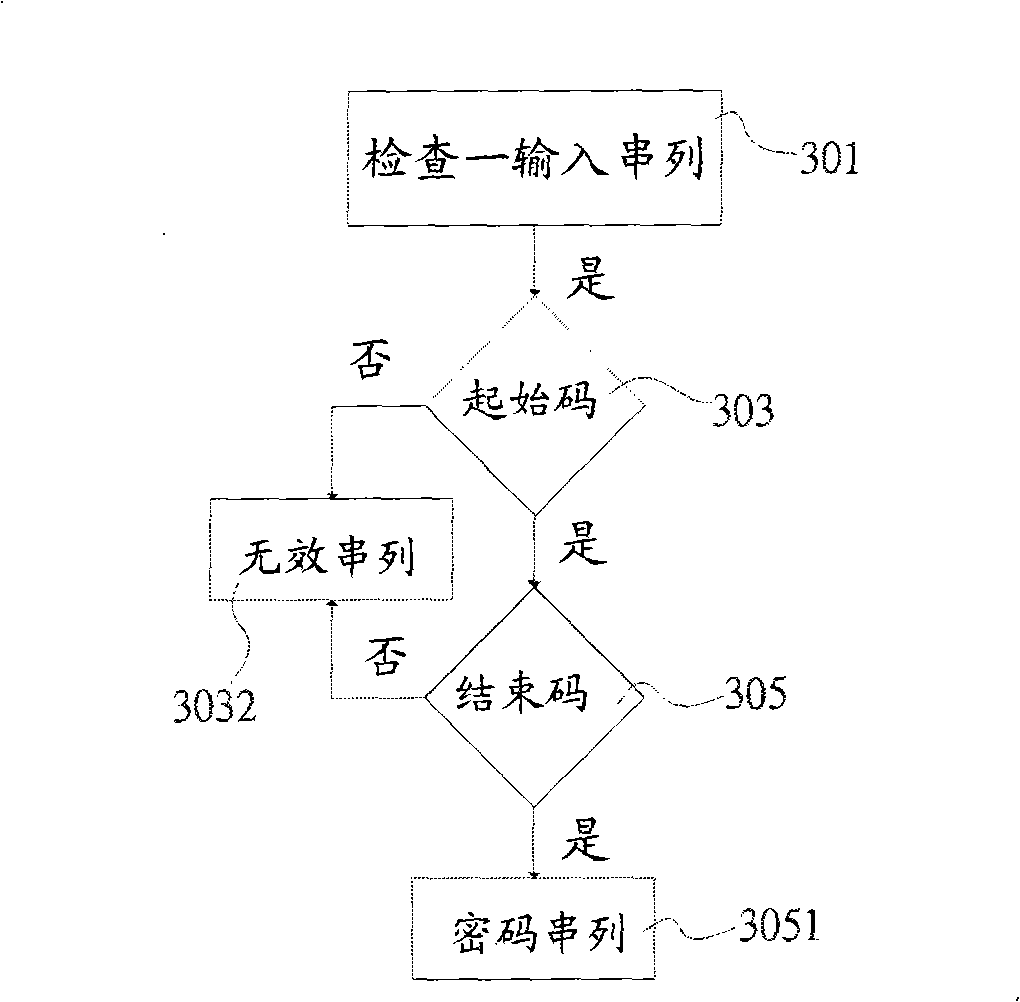
[0030] see figure 1 shown. The method for setting irregular passwords of the present invention is used for a user to set a password string to log in to electronic devices such as servers provided by computers, financial card cash machines, Internet sites, or hosts of wireless communication networks. The operator of the device. The method for setting irregular passwords of the present invention includes inputting an irregular character set composed of a string of characters, numbers or symbols into a host, such as a computer host, a portable communication device, etc., to generate a password string, and display In a display unit such as a liquid crystal display; the password string includes a login code and at least one component unit 51-58. The login code and the constituent elements 51-58 each include at least one character. The character is one or both of a letter, number, or symbol. The entry code may further include a start code 1, an intermediate code 2 and an end cod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com