TEE-based security proxy re-encryption method
A security proxy and re-encryption technology, applied in the field of computer security and cryptography, can solve the problems of loss of cloud data sharing, trouble for data owners, etc., to ensure that it will not be stolen, reduce the possibility of being attacked, and reduce computing costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
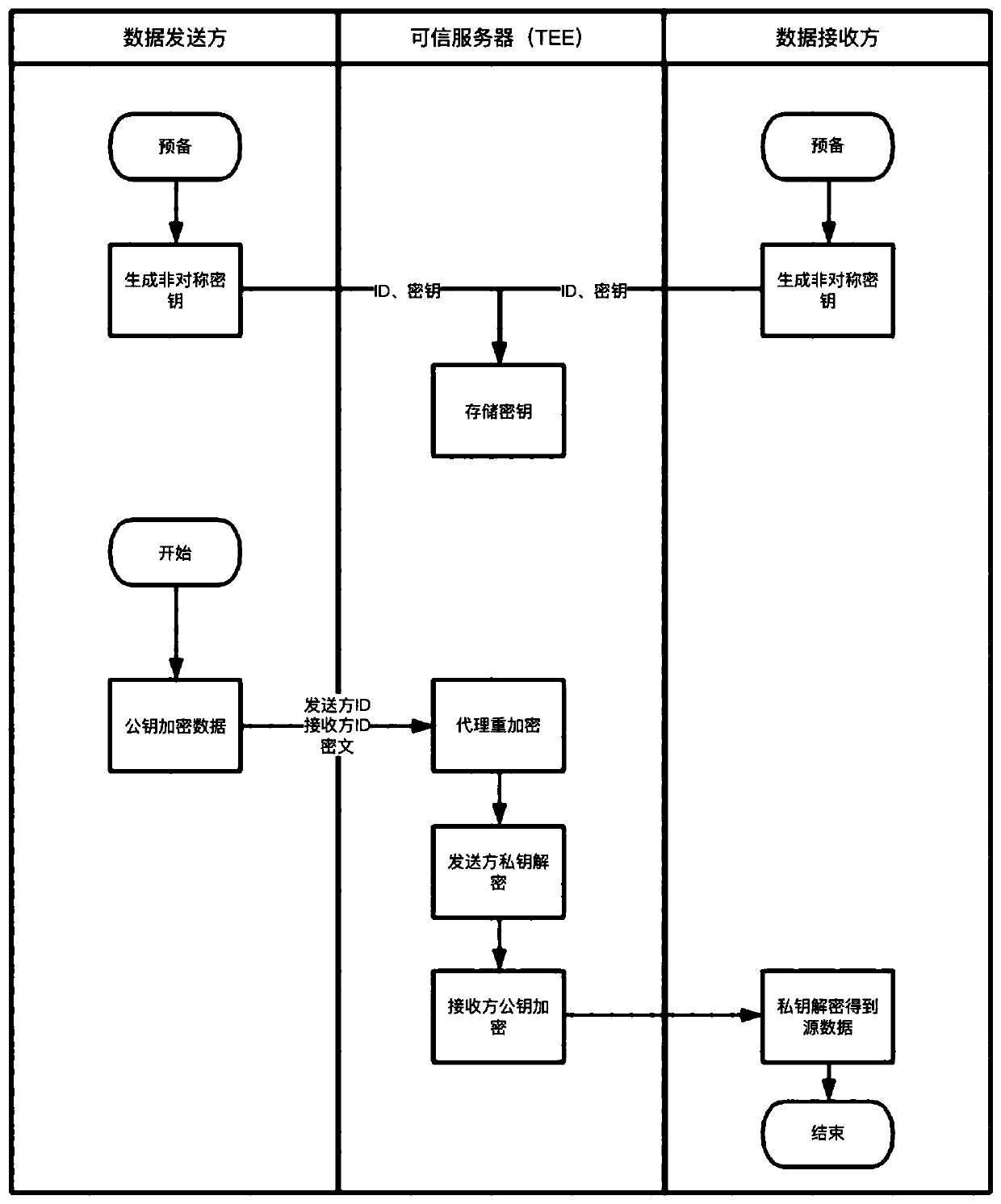
[0013] Such as figure 1 It is a flowchart of the security agent re-encryption method of the present invention, and the security agent re-encryption method specifically includes the following steps:
[0014] (1) The data sender and the data receiver each generate an asymmetric key pair, and upload the data sender ID, the data sender's asymmetric key pair, the data receiver ID, and the data receiver's asymmetric key pair to a trusted server for secure storage; the asymmetric key pair includes a public key and a private key. At this point, the trusted server has the ID and key pairs of all parties, and can perform trusted encryption and decryption operations on behalf of all parties, acting as a trusted agent.
[0015] (2) After the data sender encrypts the data with the public key in its asymmetric key pair, together with the data sender ID and the data receiver ID as parameters, send a proxy re-encryption request based on HTTP or RPC protocol to the trusted server, Call the p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com