Key management-based access control method suitable for pay television system
An access control and key management technology, applied in the field of access control based on key management, can solve problems such as not supporting subscription behavior well
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] In order to better understand the technical content of the present invention, specific embodiments are given together with the attached drawings for description as follows.
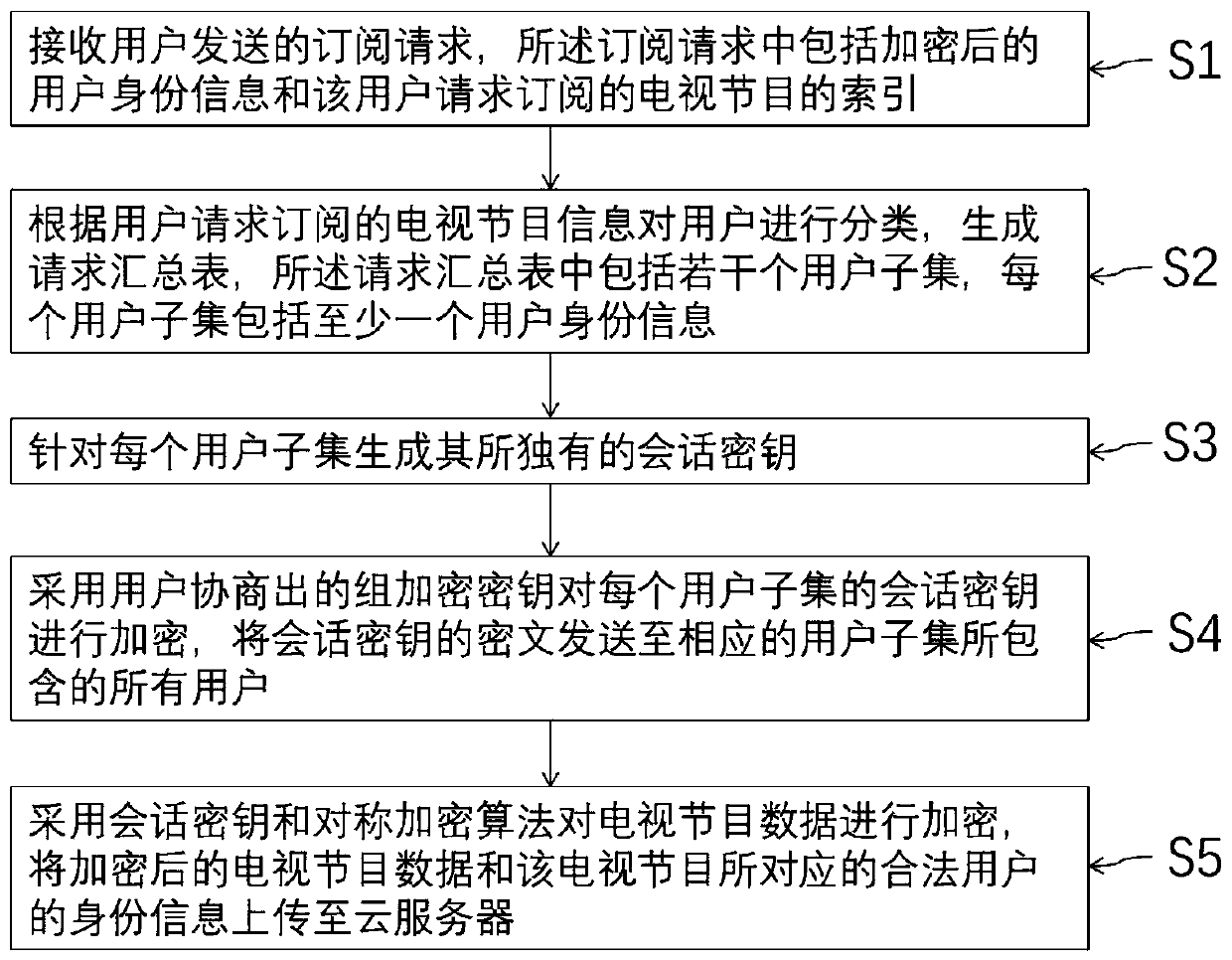
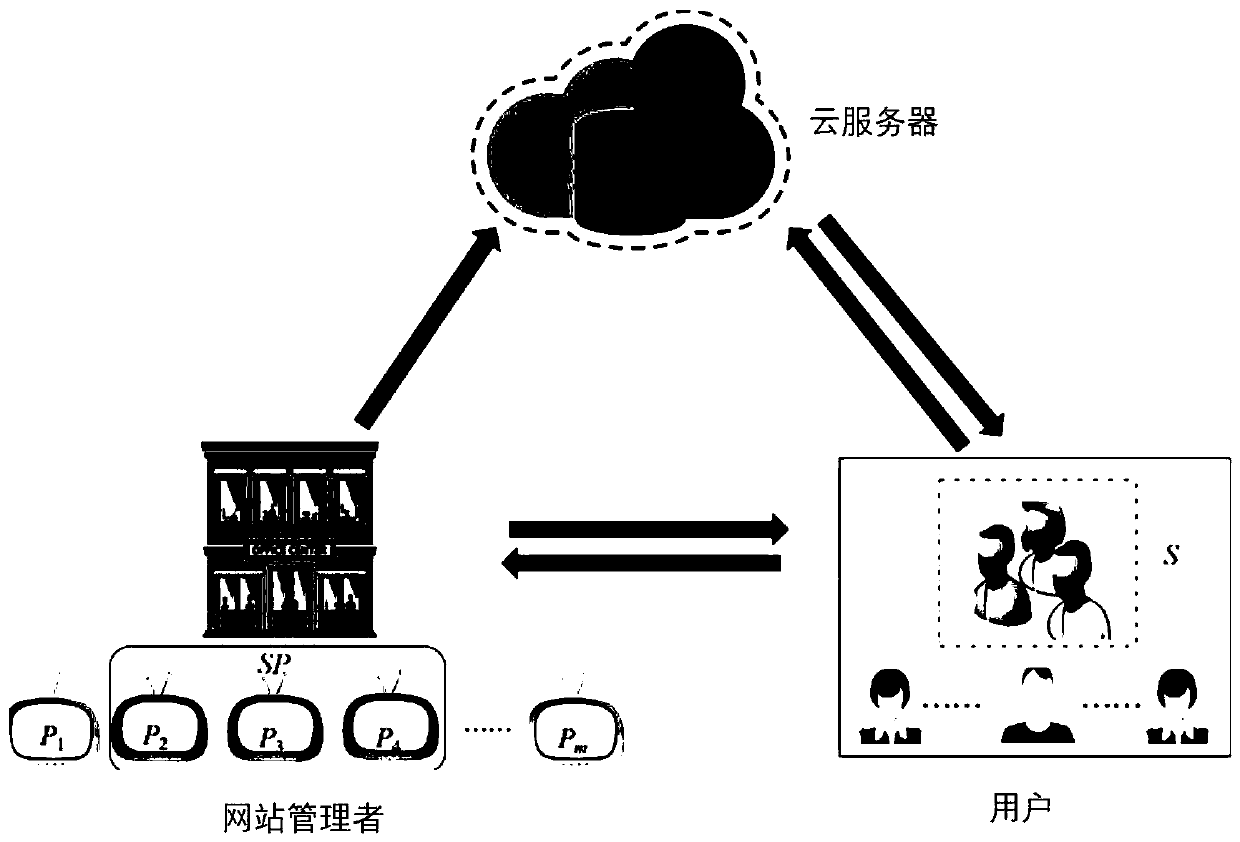
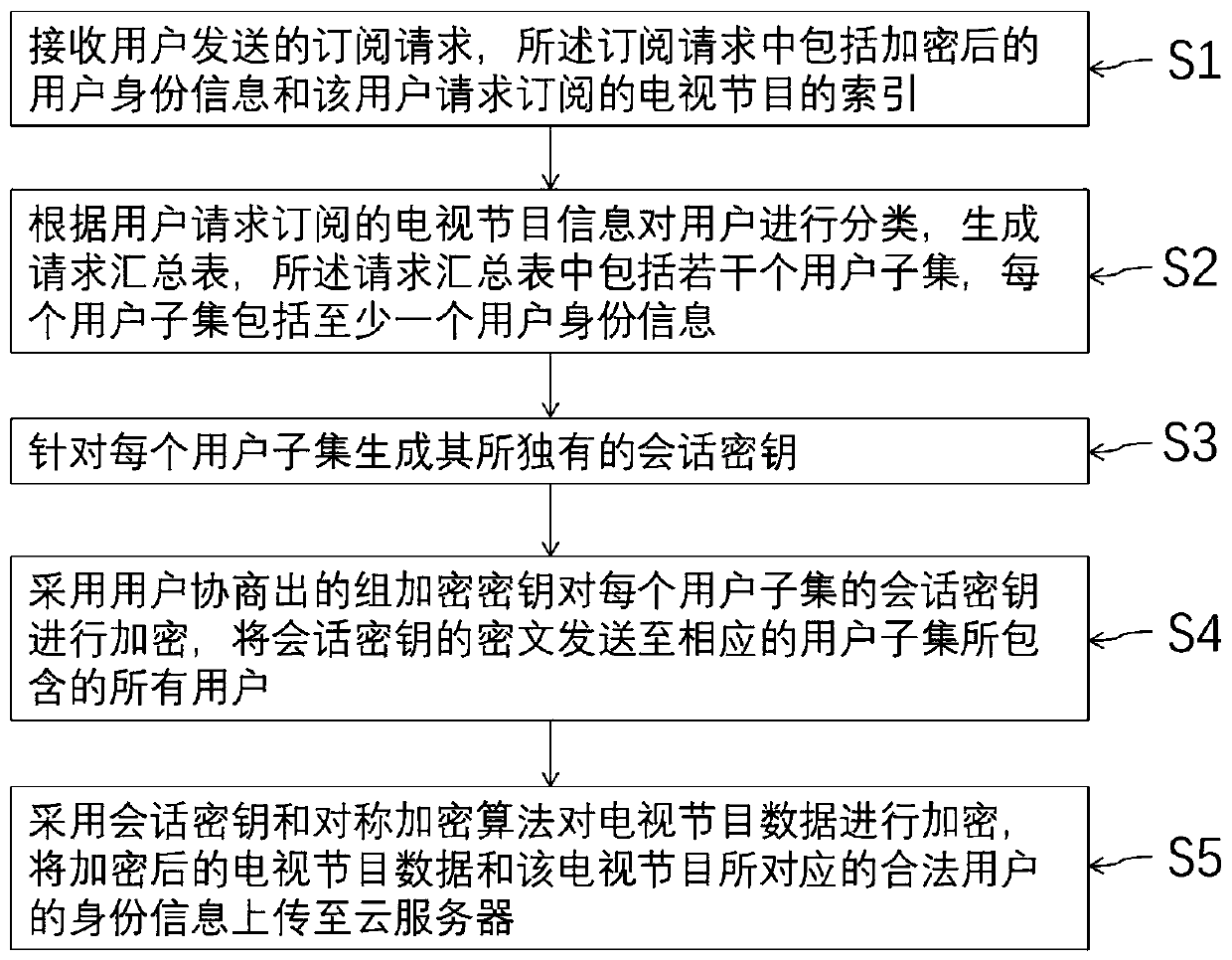
[0061] The present invention refers to an access control method based on key management suitable for a pay television system, and the access control method includes:
[0062] S1: Receive a subscription request sent by a user, where the subscription request includes encrypted user identity information and an index of the TV program that the user requests to subscribe to.
[0063] S2: Classify the users according to the TV program information requested by the users to subscribe, and generate a request summary table. The request summary table includes several user subsets, and each user subset includes at least one user identity information.
[0064] S3: Generate a unique session key for each user subset.
[0065] S4: Use the group encryption key negotiated by the users to encrypt the session key of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com