Login authentication method and device
A technology for login authentication and login location, applied in the computer field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
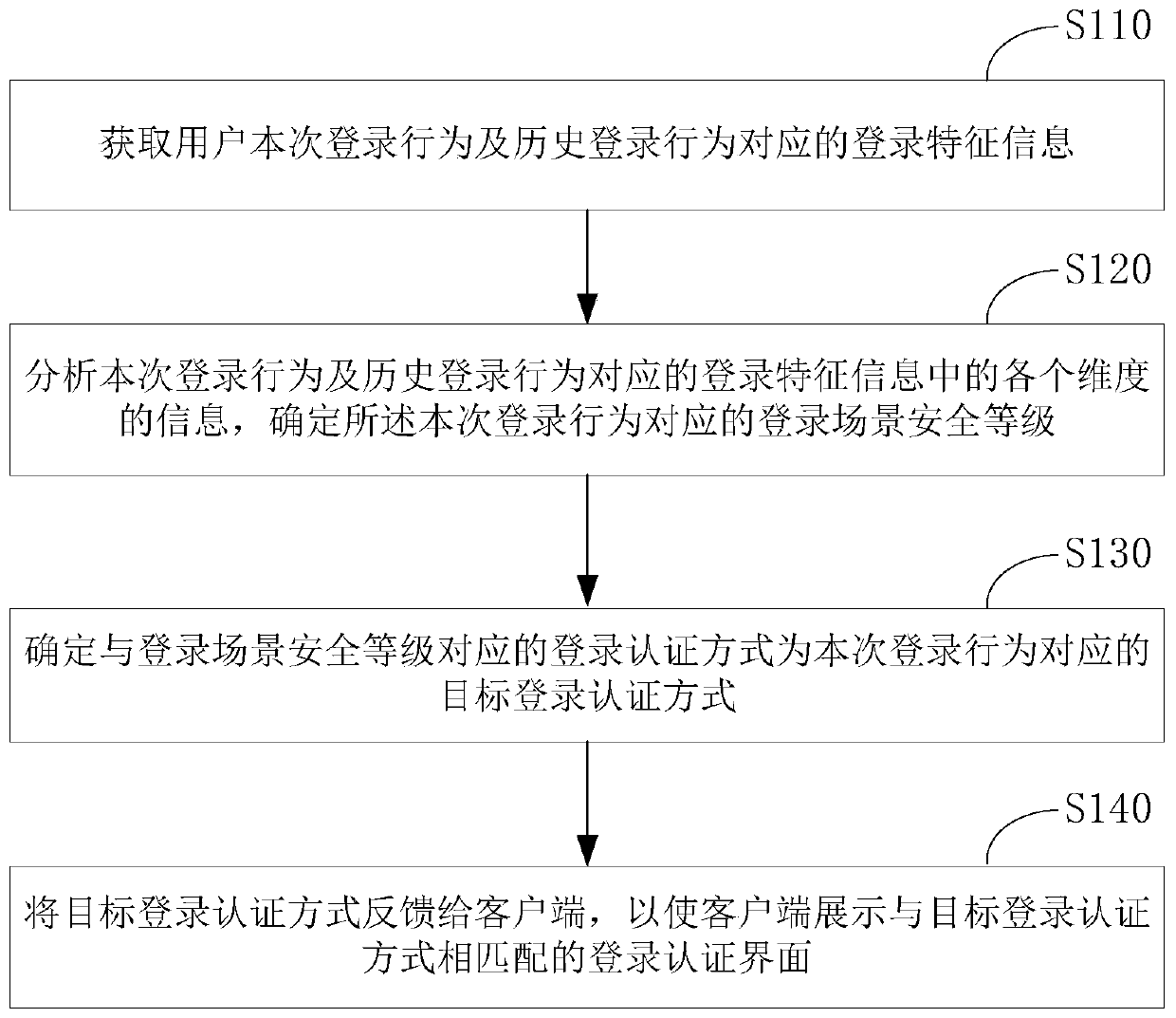
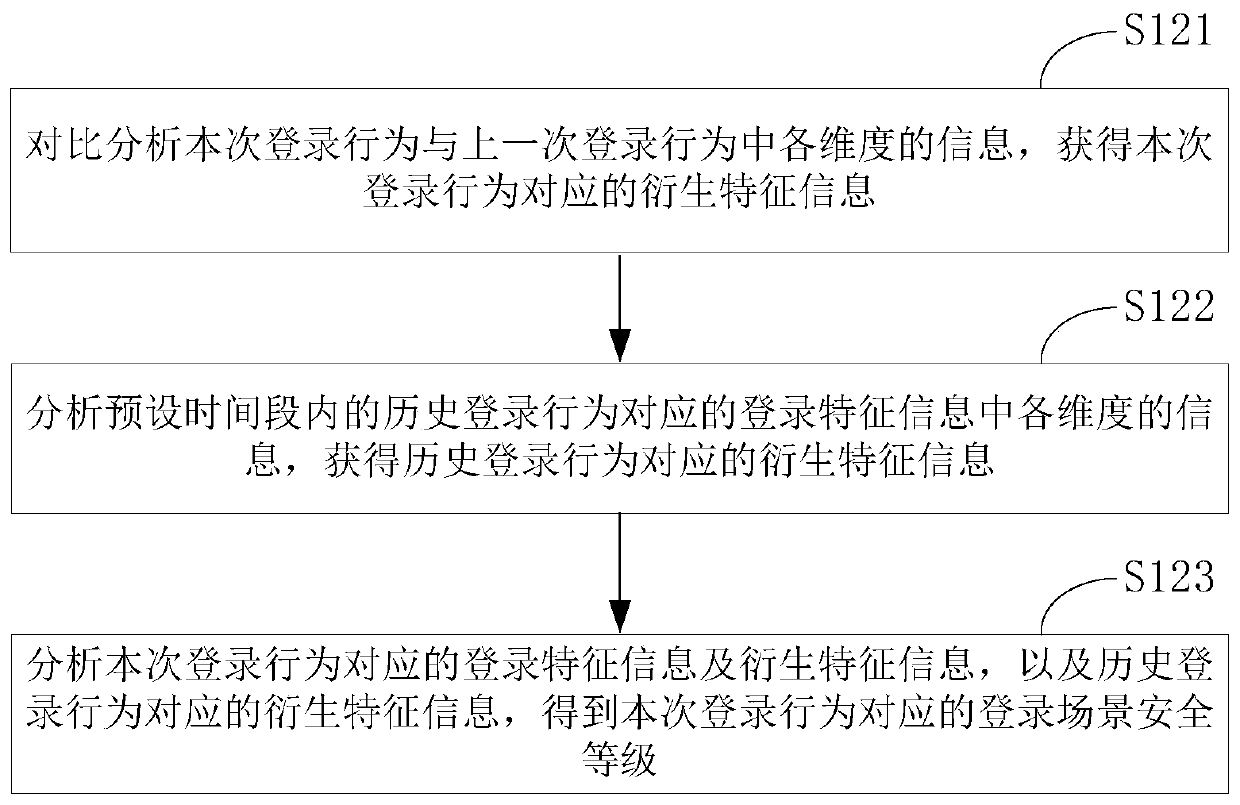
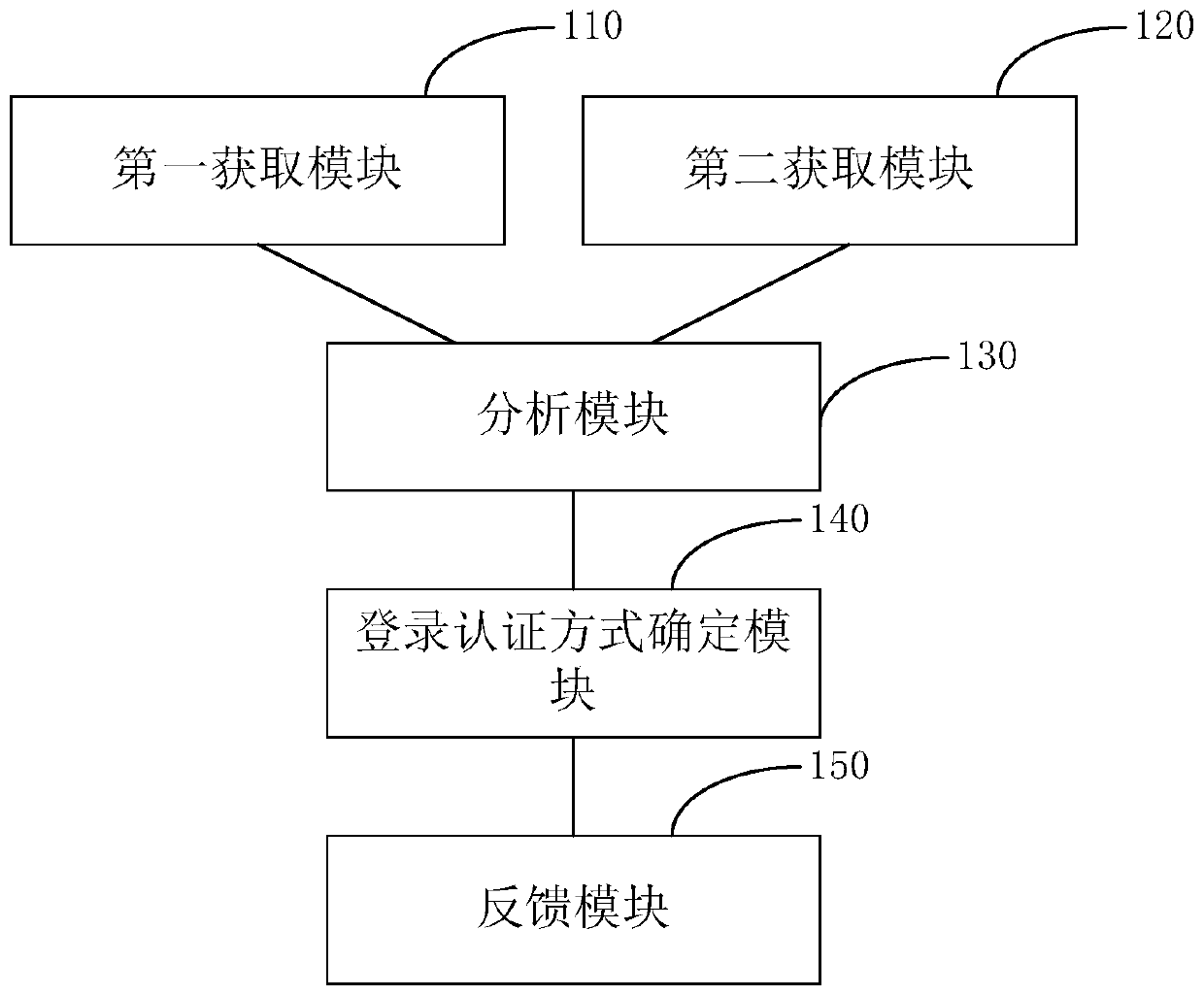
[0057] The traditional login authentication method always uses the login authentication method selected by the user for login authentication. However, in different scenarios, the potential risks brought by different login methods are different. For example, when the user is sleeping at night, the fingerprint login method has Great potential risk. For another example, in the case of the user's mobile phone being lost, there is a great potential risk in the SMS verification code login method. In order to solve this technical problem, the present invention provides a login authentication method, which obtains the login feature information corresponding to the current login behavior and historical login behavior of the user; analyzes the obtained login feature information to determine the login scenario security level corresponding to the current login behavior . Then determine the login authentication method that matches the security level of the login scenario corresponding to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com