Data processing method and device, electronic equipment and readable storage medium
A data processing and processor technology, which is applied in the field of data security and can solve problems such as user information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
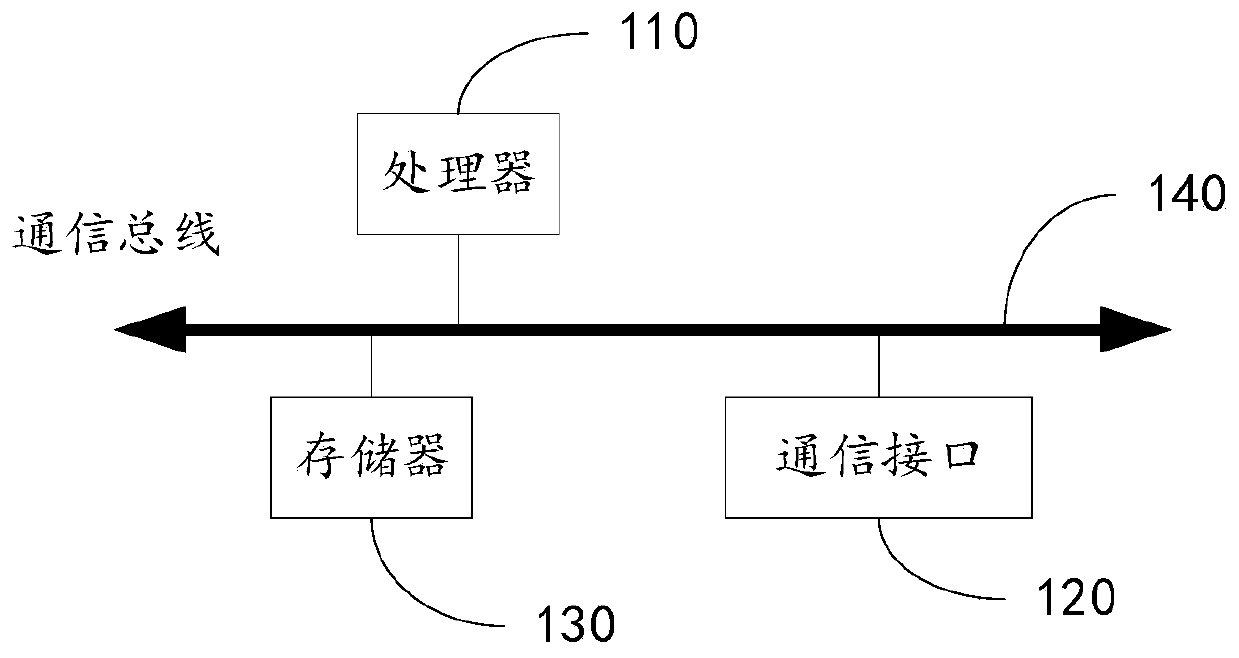
[0066] The following will clearly and completely describe the technical solutions in the embodiments of the present application with reference to the drawings in the embodiments of the present application.
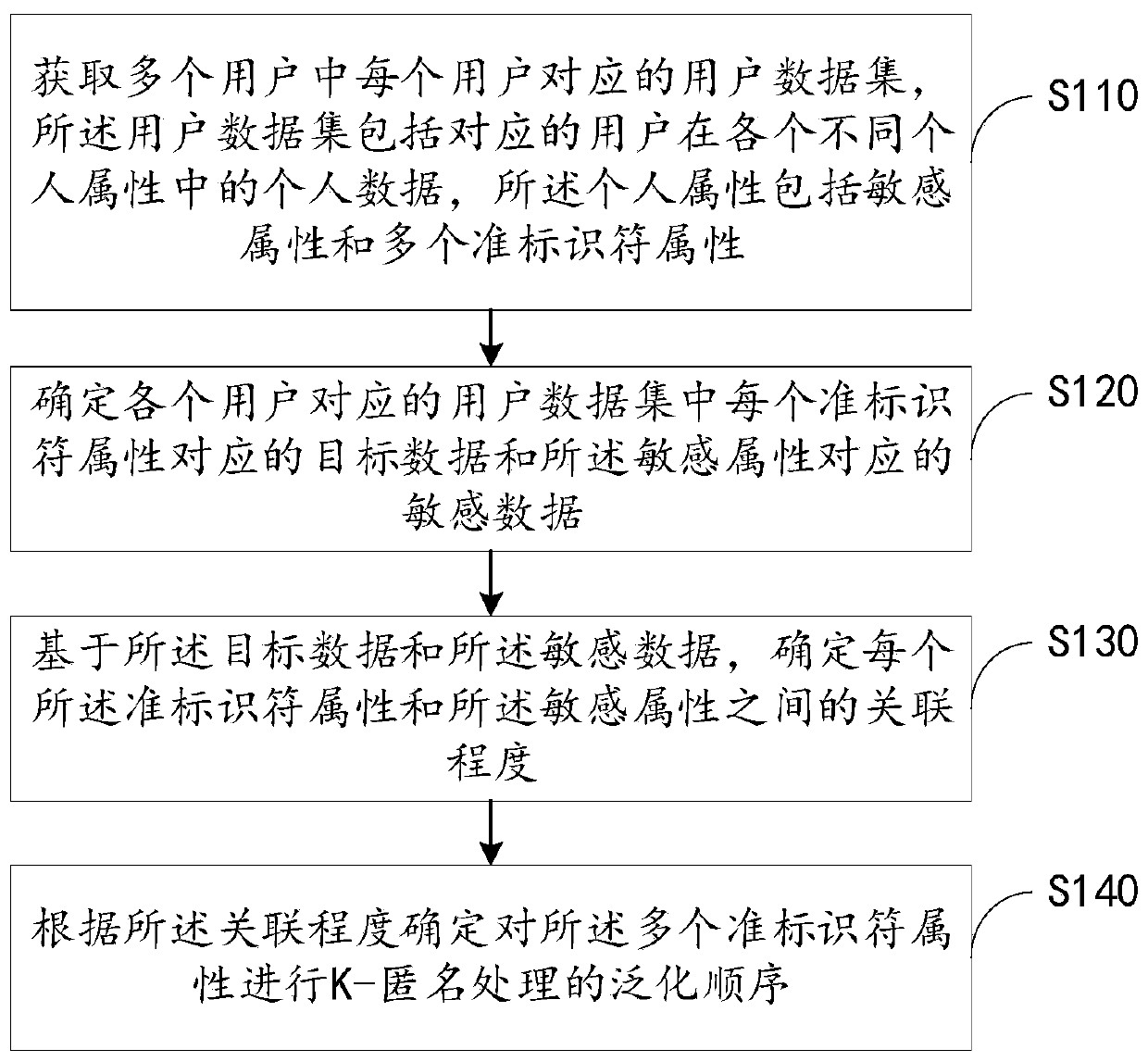
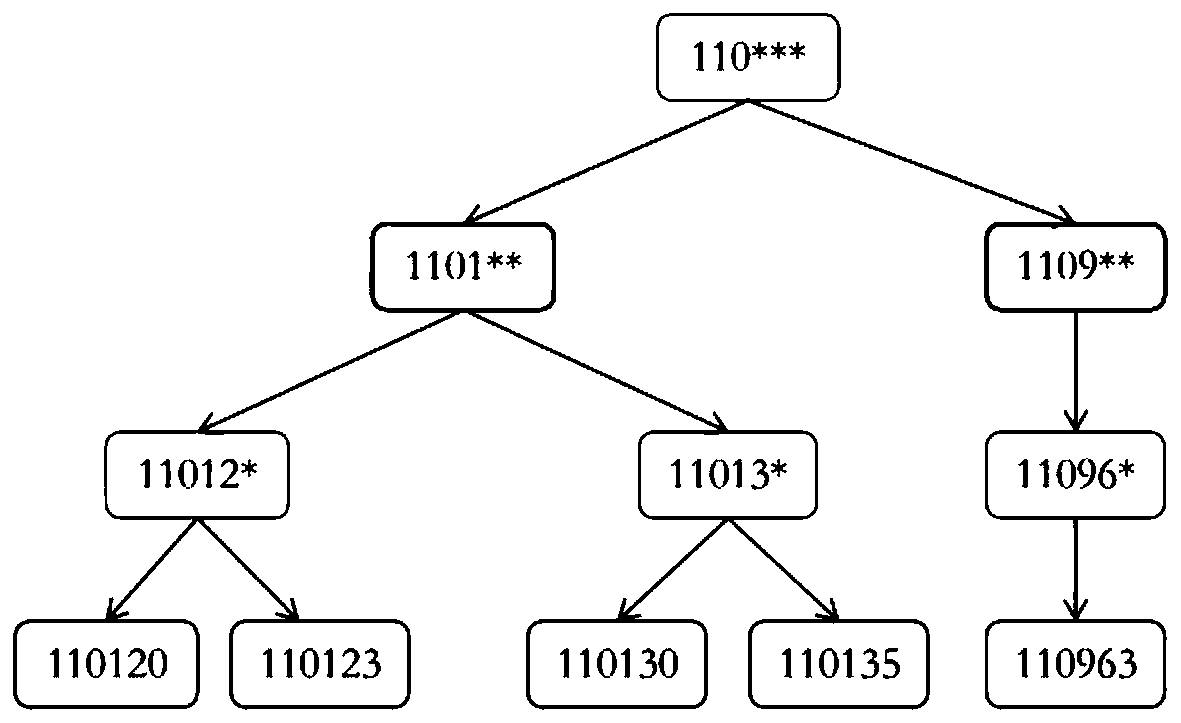
[0067] The embodiment of the present application provides a data processing method, which determines the generalization order for multiple quasi-identification attributes by obtaining the degree of association between the quasi-identifier attribute and the sensitive attribute. Generalization, so that quasi-identifiers related to sensitive attributes can be generalized, and attackers will not easily locate users, avoiding the problem that users' private information is easily leaked.
[0068] In order to facilitate the understanding of the embodiments of the present application, the related concepts involved in the embodiments of the present application are firstly explained below.
[0069] Identifier: It can uniquely determine the identity of a user, such as ID, name and ot...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com