An Endogenous Secure Communication Method Based on Wireless Channel Characteristics
A secure communication and wireless channel technology, applied in the field of endogenous secure communication based on wireless channel characteristics, can solve problems such as low implementation efficiency, inability to achieve comprehensive protection, and insufficient protection, so as to improve security performance and improve information security processing efficiency , Enhance the effect of defense effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
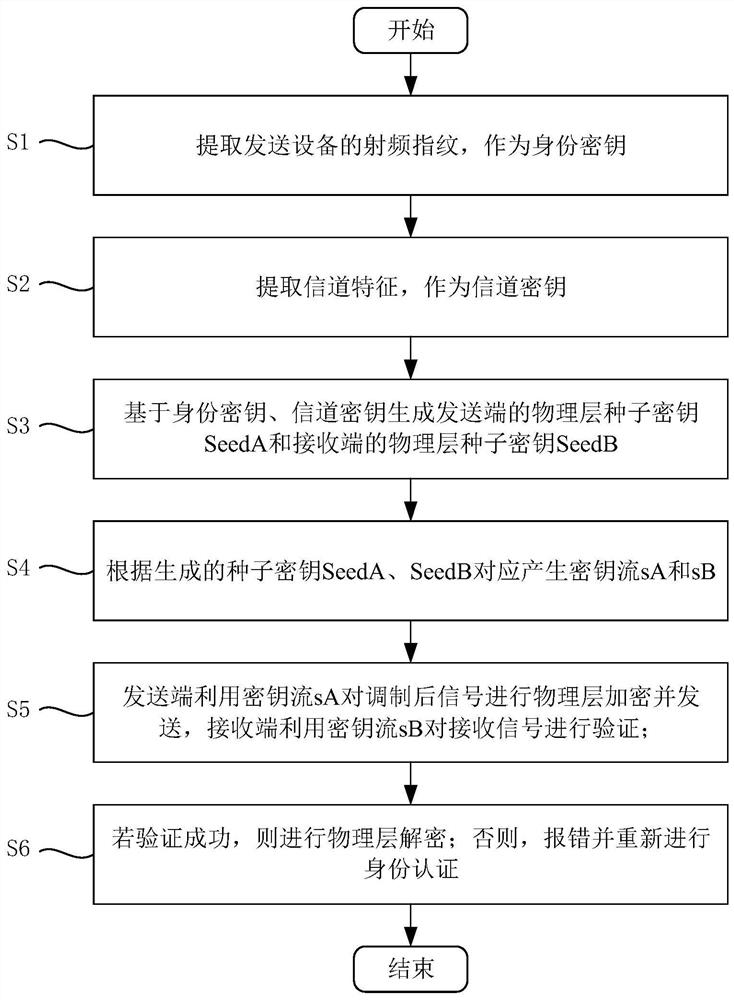
[0071] Such as figure 1 As shown, an endogenous secure communication method based on wireless channel characteristics includes the following steps:
[0072] S1: Extract the RF fingerprint of the sending device as the identity key K;
[0073] S2: Extract channel features as channel key K z ;
[0074] S3: Based on identity key K and channel key K z Generate the physical layer seed key SeedA of the sending end and the physical layer seed key SeedB of the receiving end;
[0075] S4: According to the generated seed keys SeedA and SeedB, correspondingly generate key streams sA and sB;
[0076] S5: The sending end uses the key stream sA to encrypt the modulated signal at the physical layer and sends it, and the receiving end uses the key stream sB to verify the received signal;
[0077] S6: If the verification is successful, perform physical layer decryption; otherwise, report an error and perform identity authentication again.
[0078] In the specific implementation process, t...
Embodiment 2
[0080] More specifically, on the basis of Example 1, the step S1 specifically includes the following steps:
[0081] S11: Receive signals through the receiver antenna array, and perform channel estimation on the received signals, setting k=1;
[0082] S12: Calculate the autocorrelation matrix R(k) for the channel estimation result of the k-th carrier, and perform rank-increasing processing on the autocorrelation matrix R(k), to obtain the rank-increasing autocorrelation matrix R(k) of the k-th carrier;
[0083] S13: yes Calculate the multipath signal amplitude;
[0084] S14: judge whether k is equal to N, and N is the total number of carriers; if it is equal, proceed to step S15; if not, set k=k+1, and return to step S12;
[0085] S15: Sort the multipath signal amplitudes of each carrier, select a path, obtain a radio frequency fingerprint, and use the radio frequency fingerprint as an identity key K.
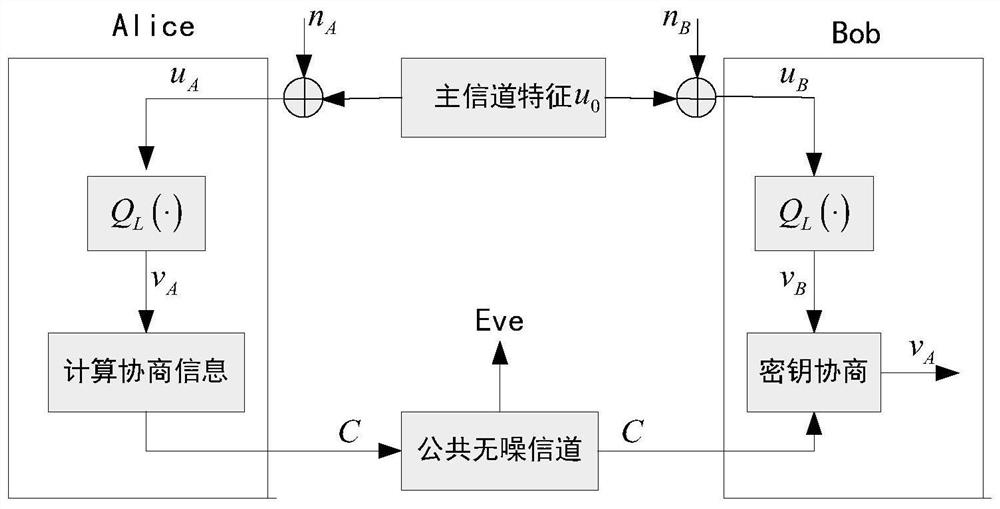
[0086] More specifically, such as figure 2 As shown, in the step S2,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com