Terminal implicit identity authentication method based on Sudoku password
An identity authentication and grid password technology, applied in the field of terminal implicit identity authentication based on Jiugong grid password, can solve the problem of not being able to apply Jiugong grid graphic password well, and achieve the effect of improving the accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
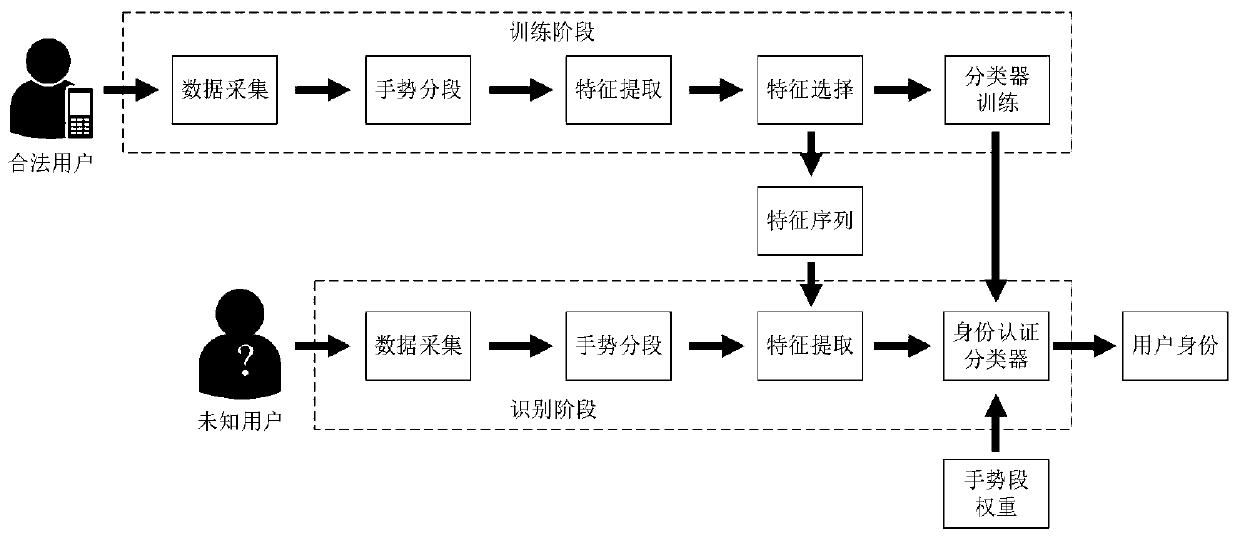
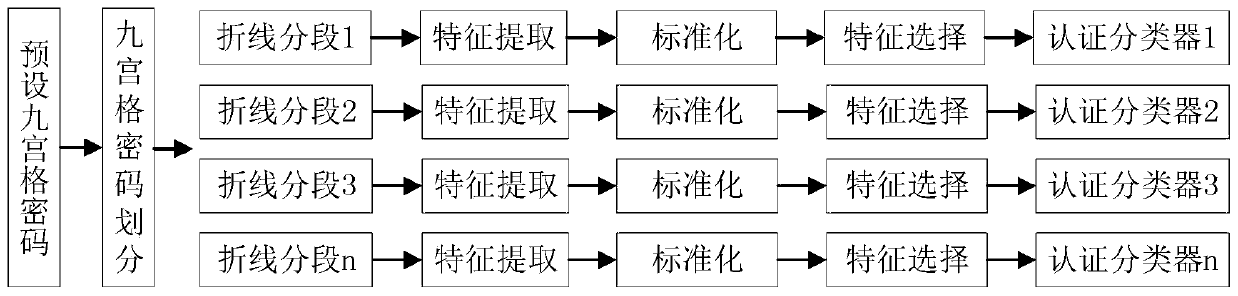
[0047] like figure 1 As shown, the embodiment of the present invention provides a mobile phone terminal implicit identity authentication method based on Jiugongge password, from figure 1 It can be seen that the method includes two stages: the training of the identity authentication classifier and the identity authentication of the user to be authenticated. In the training phase, the data of the preset Jiugongge password of legitimate users is collected to train the authentication model. In the authentication stage, the behavior data of the Jiugongge password to be authenticated is used for authentication by the trained authentication model to determine the legitimacy of the user.
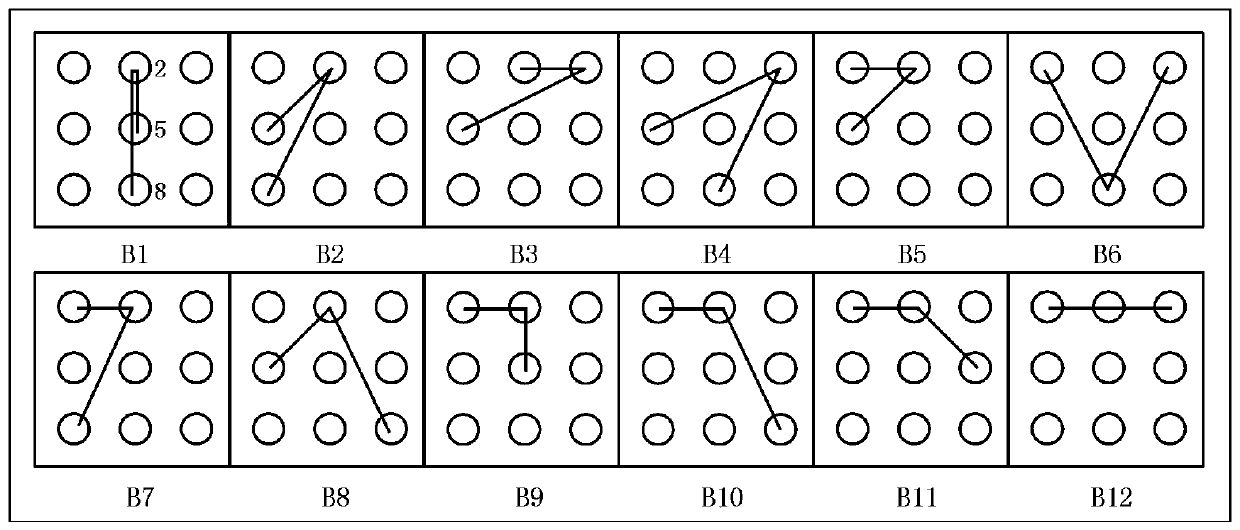
[0048] The determination of the basic unit of the broken line of the Jiugongge password is independent of the training phase and the certification phase, as follows:
[0049] In the establishment of the basic unit of the broken line, according to the drawing rules of the Jiugongge cipher, exhaustiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com