Data processing method and device based on block chain, equipment and medium
A data processing and block chain technology, applied in the field of block chain technology, can solve problems such as limiting block chain network business processing capabilities and inability to access external resources, and achieve rich and flexible data processing capabilities, ensuring security and reliability performance, taking into account the effect of safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example
[0115] First embodiment
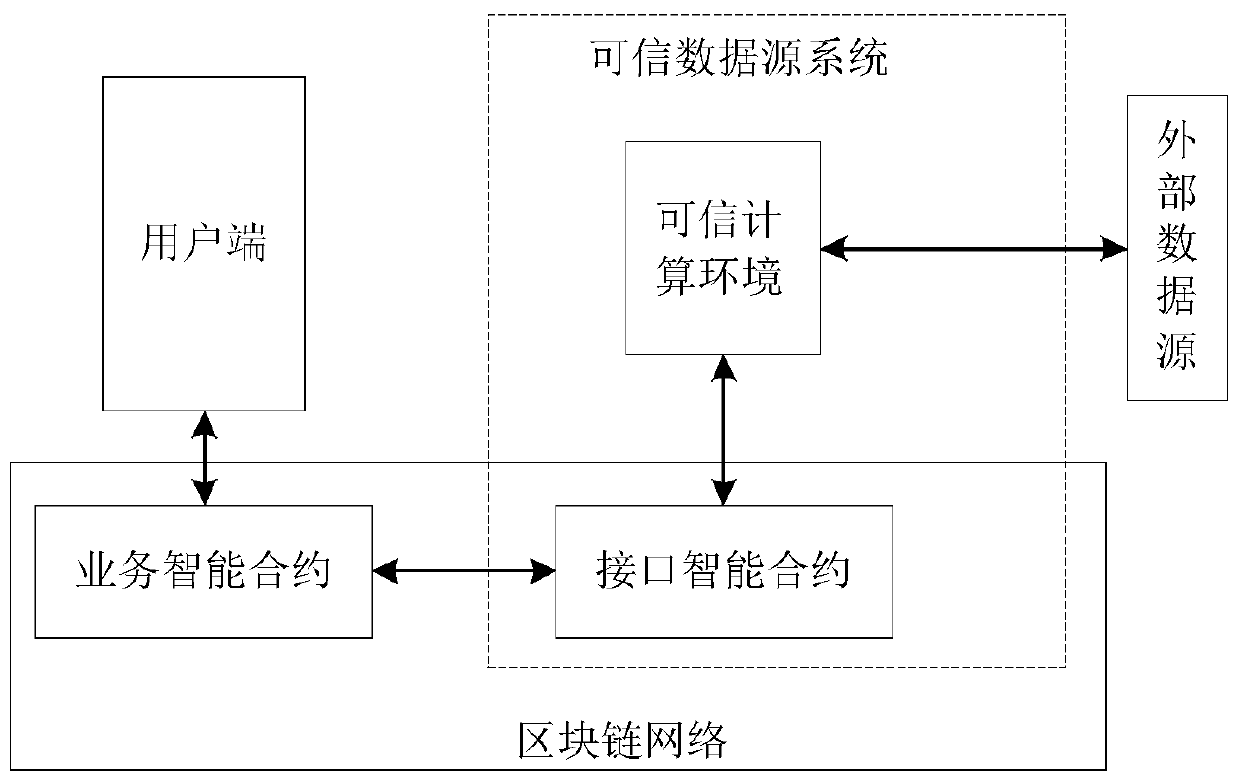
[0116] Before introducing the embodiments of this application, firstly, each device end of this application that executes the blockchain-based data processing method will be explained. Figure 1A Shown is a system architecture for implementing the blockchain data processing method of the embodiment of the present application, and the architecture includes: a user terminal, a blockchain network, and a trusted data source system (ie Figure 1A Dashed box in) and external data sources.
[0117] Among them, the user end is the device end for users to access the blockchain network and invoke the business smart contract in it to initiate related business transaction requests. It can be a node device of the blockchain network, such as a lightweight node device of the blockchain network. , It can also be a software platform (such as a SaaS platform) that the service provider provides for users to access the blockchain network.
[0118] A business smart contract is dep...
Example
[0137] Second embodiment
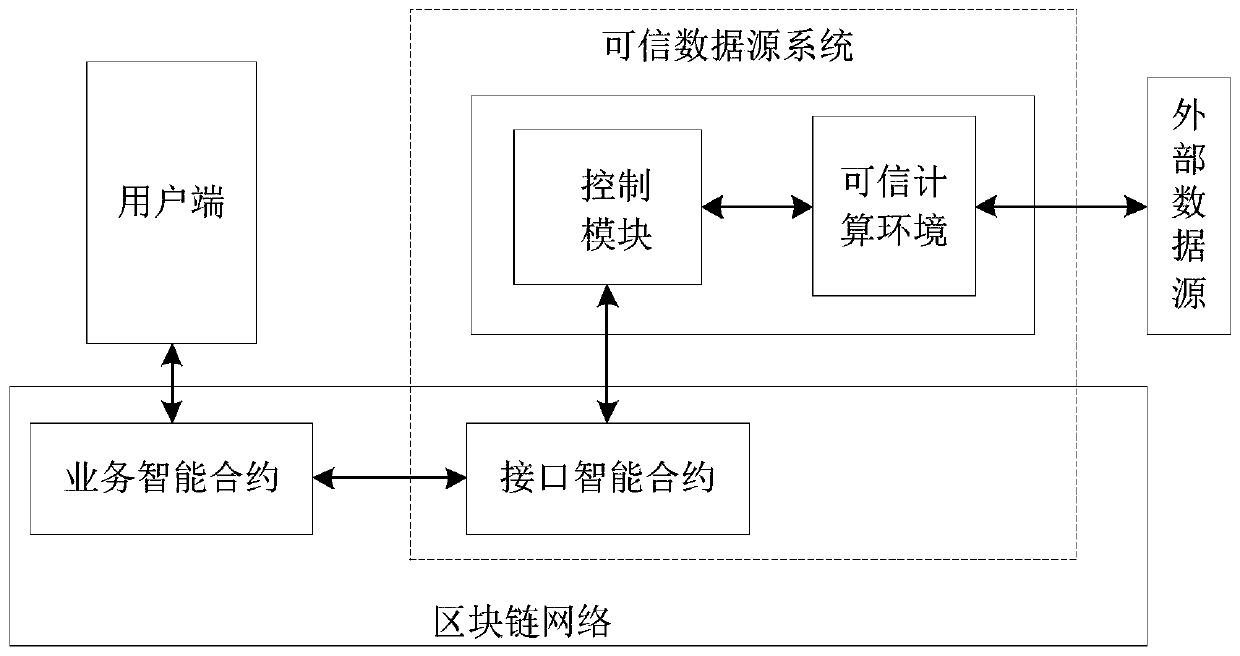
[0138] Figure 2A Is another architecture diagram of the data processing method for executing the blockchain provided by the embodiment of the application; the architecture diagram is in Figure 1A On the basis of the illustrated architecture, a control module (ie Relay module) is added to the trusted data source system. The control module can be an intermediate module connecting the interface smart contract and the trusted computing environment in the trusted data source system. The control module mainly plays a role of service management in the trusted data source system. For example, the control module can deploy interface smart contracts in the blockchain network, and obtain off-chain processing requests from the interface smart contracts and transmit them to the trusted computing environment. And the processing result of the off-chain processing request obtained from the trusted computing environment is fed back to the interface smart contract. Its ...
Example
[0164] The third embodiment
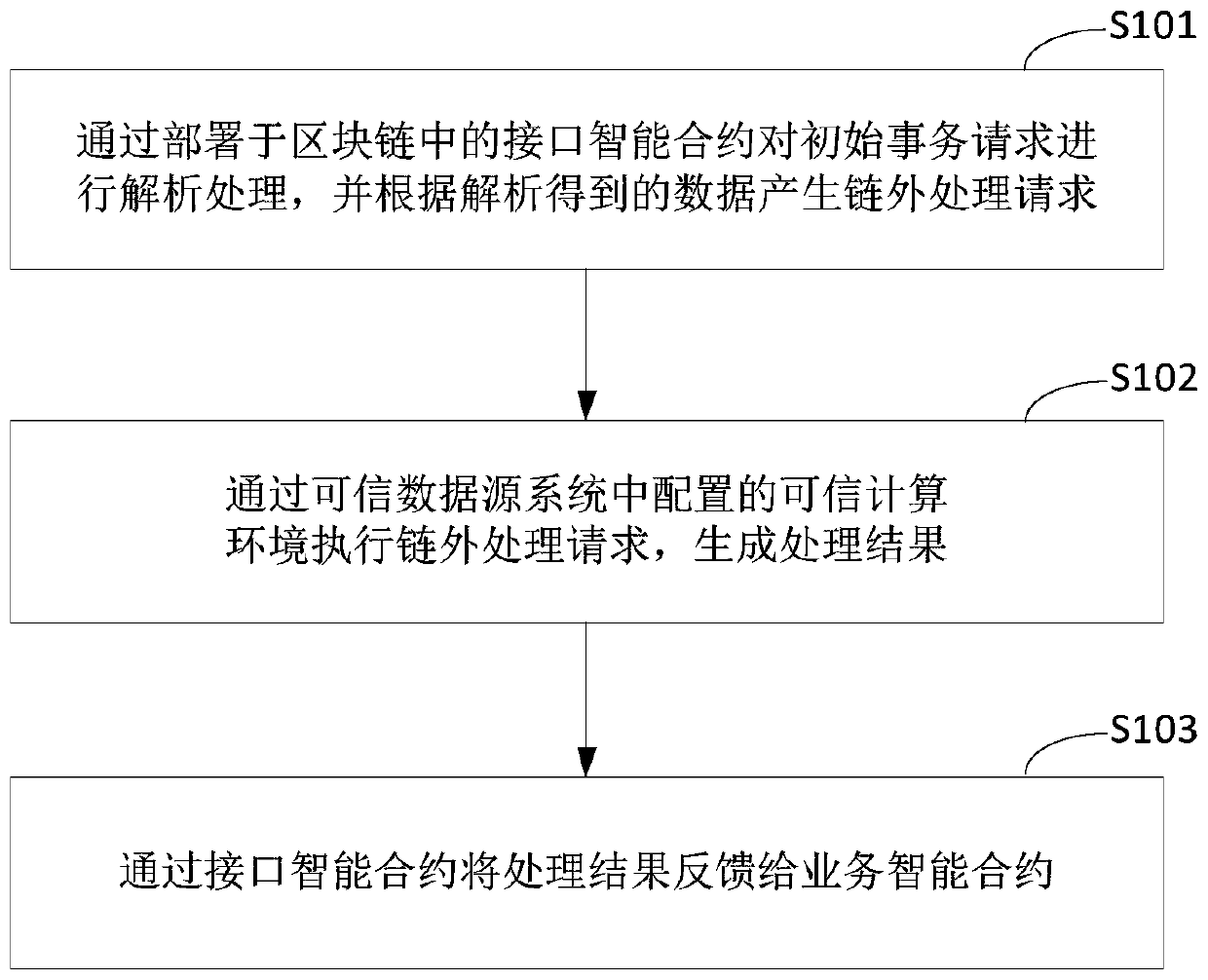
[0165] image 3 It is a flowchart of a blockchain-based data processing method according to the third embodiment of the present application. This embodiment is optimized on the basis of the above-mentioned embodiments, and specifically gives the detailed process introduction of the control module to obtain the off-chain processing request and transmit it to the trusted computing environment, and the trusted computing environment to execute the off-chain processing request to generate the processing result. .
[0166] Optionally, in this embodiment of the present application, at least one secure container instance (Enclave) is configured in the trusted computing environment configured by the trusted data source system for performing data processing operations of the set function. The secure container instance may be a collection of codes that implement a certain computing function, and is used to perform data processing tasks of the set function. In t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com